Agent Tesla Delivered via Fake Canon EOS Notification on Free OwnCloud Account
For a few days, there are new waves of Agent Tesla[1] landing in our mailboxes. I found one that uses two new "channels" to deliver the trojan. Today, we can potentially receive notifications and files from many types of systems or devices. I found a phishing sample that tries to hide behind a Canon EOS camera notification. Not very well designed but it’s uncommon to see this. It started with a simple email:
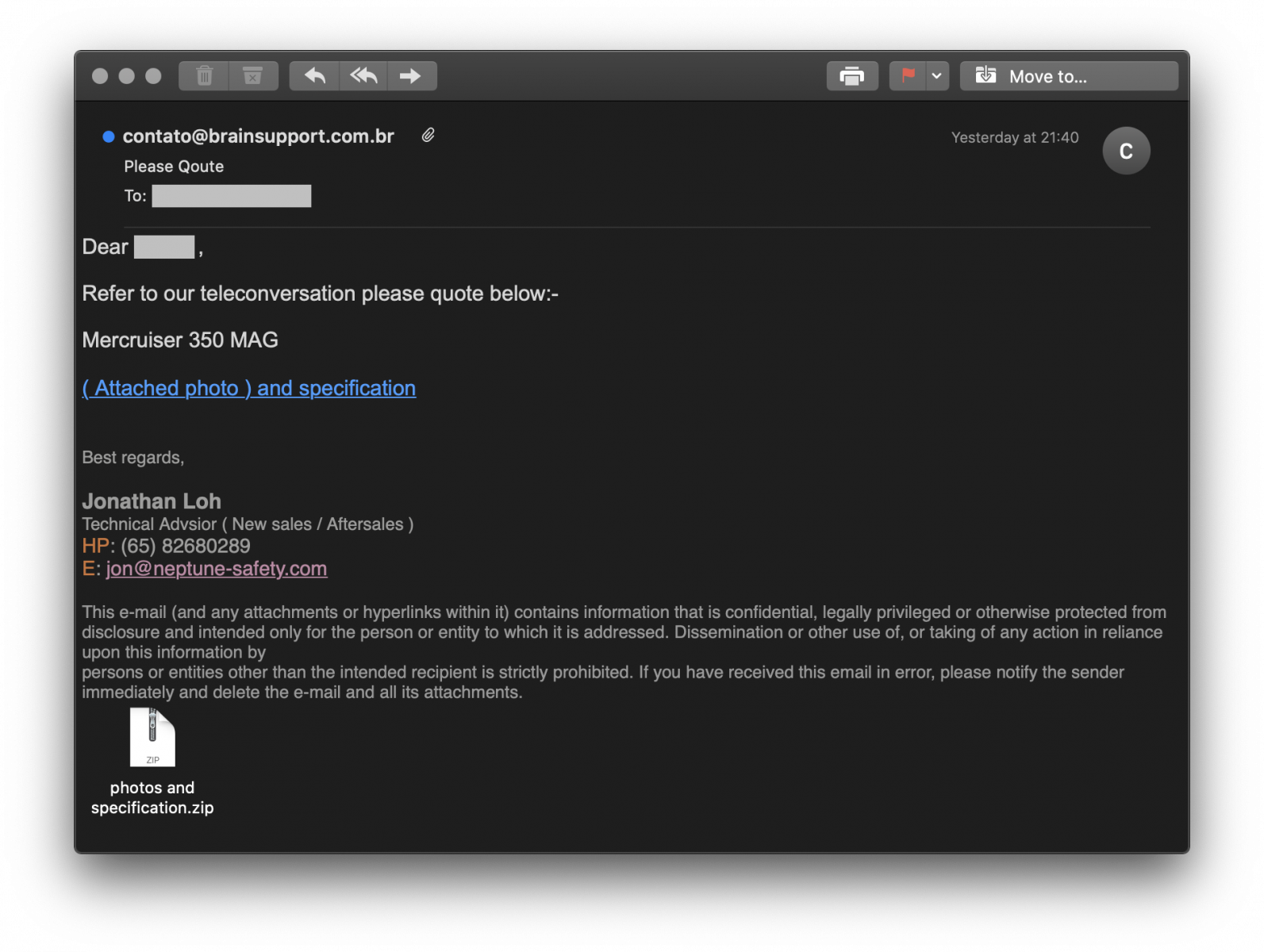
Note the beautiful typo in the mail subject! ("Qoute")
The malicious payload is delivered via the following path:
A ZIP archive is attached to the mail:
Photos and specification.zip (SHA256:0875804511b077f7e8b4d5f4dd11b61f2334b9b61da1018f6246739a348a6d19)
The archive contains an HTML file (Unicode):
photos and specification.html (SHA256:ab6b5faa826f5f503d9b9c8c5de0e3b0d65bf88812a9f7b83bf97901c39d6ebe)
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR/html4/loose.dtd"> <HTML><HEAD> <META name=GENERATOR content="MSHTML 11.00.9600.19626"></HEAD> <BODY style="MARGIN: 0.5em"> <P><A href="hxxps://nuesterish742[.]owncloud[.]online/index.php/s/rEbK2f0fHiMTy2k"><IMG style="HEIGHT: 368px; WIDTH: 661px" border=0 hspace=0 alt="" src="hxxps://www[.]mirrorlessrumors[.]com/wp-content/uploads/2018/09/Bildschirmfoto-2018-09-02-um-07.29.06-700x368.png" width=699 align=baseline height=368></A><BR><BR><BR><FONT size=7><A href="hxxps://nuesterish742[.]owncloud[.]online/index.php/s/rEbK2f0fHiMTy2k"><STRONG>DOWNLOAD</STRONG></A><STRONG> </STRONG> <A href="hxxps://nuesterish742[.]owncloud[.]online/index.php/s/rEbK2f0fHiMTy2k"><STRONG>VIEW</STRONG></A><BR><A href="hxxps://nuesterish742[.]owncloud[.]online/index.php/s/rEbK2f0fHiMTy2k"><FONT size=3>hxxps://nuesterish742[.]owncloud[.]online/index.php/s/rEbK2f0fHiMTy2k</FONT></A><BR><BR></FONT></P></BODY></HTML>
Here is the page rendered in a browser:
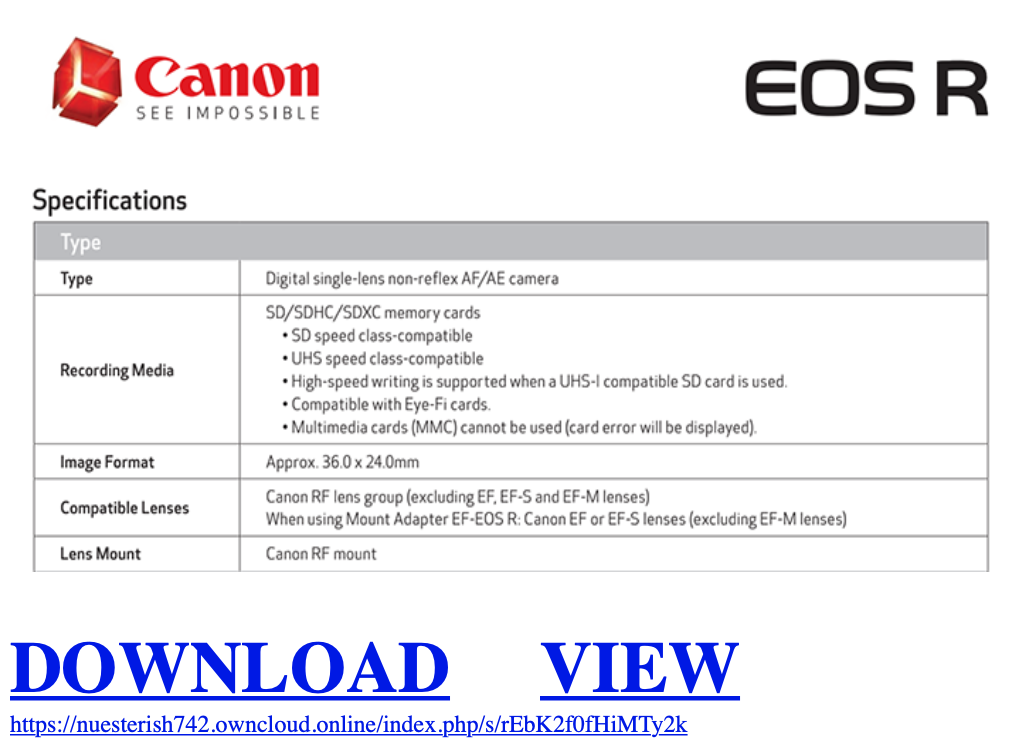
The next stage payload is hosted on a public OwnCloud account. OwnCloud is a very popular cloud storage solution. You can run your private cloud on-premises but they also offer a “cloud” solution and a free trial:

A file is shared via this trial account: “Photos and specification.cab” (SHA256:d6404503a8257ebf3d153e91d0b92c9ae8da7c710124781ae27e6a55c40b887f). It contains the final payload:
Photos and specification.exe (SHA256:5254a36f51199786127851940e49c50ffe04aafa091ba6518118125bd68a4c31) with a current VT score of 24/72[2]. This is the Agent Tesla itself.
It copies itself into C:\Users\admin\AppData\Roaming\ and implements persistence via a scheduled task:
C:\Windows\System32\schtasks.exe" /Create /TN "Updates\PHIvtqf" /XML "C:\Users\user\AppData\Local\Temp\tmp6CEB.tmp
The scheduled task configuration is also dumped on disk:
<?xml version="1.0" encoding="UTF-16"?>
<Task version="1.2" xmlns="http://schemas.microsoft.com/windows/2004/02/mit/task">
<RegistrationInfo>
<Date>2014-10-25T14:27:44.8929027</Date>
<Author>SANDBOX\user</Author>
</RegistrationInfo>
<Triggers>
<LogonTrigger>
<Enabled>true</Enabled>
<UserId>SANDBOX\user</UserId>
</LogonTrigger>
<RegistrationTrigger>
<Enabled>false</Enabled>
</RegistrationTrigger>
</Triggers>
<Principals>
<Principal id="Author">
<UserId>SANDBOX\user</UserId>
<LogonType>InteractiveToken</LogonType>
<RunLevel>LeastPrivilege</RunLevel>
</Principal>
</Principals>
<Settings>
<MultipleInstancesPolicy>StopExisting</MultipleInstancesPolicy>
<DisallowStartIfOnBatteries>false</DisallowStartIfOnBatteries>
<StopIfGoingOnBatteries>true</StopIfGoingOnBatteries>
<AllowHardTerminate>false</AllowHardTerminate>
<StartWhenAvailable>true</StartWhenAvailable>
<RunOnlyIfNetworkAvailable>false</RunOnlyIfNetworkAvailable>
<IdleSettings>
<StopOnIdleEnd>true</StopOnIdleEnd>
<RestartOnIdle>false</RestartOnIdle>
</IdleSettings>
<AllowStartOnDemand>true</AllowStartOnDemand>
<Enabled>true</Enabled>
<Hidden>false</Hidden>
<RunOnlyIfIdle>false</RunOnlyIfIdle>
<WakeToRun>false</WakeToRun>
<ExecutionTimeLimit>PT0S</ExecutionTimeLimit>
<Priority>7</Priority>
</Settings>
<Actions Context="Author">
<Exec>
<Command>C:\Users\user\AppData\Roaming\PHIvtqf.exe</Command>
</Exec>
</Actions>
</Task>
You can detect hosts infected by Agent Tesla by checking connections over TCP/587 (SMTP submissions) which is usually permitted compared to TCP/25. In this case, it used the IP address %%ip:78.142.19.101% to exfiltrate data.
I also found other suspicious OwnCloud accounts:
nuesterish742.owncloud.online
wighteredd264.owncloud.online
ntyclighta026.owncloud.online
idompoomel467.owncloud.online
titiollaug517.owncloud.online
Probably there are many more...
[1] https://any.run/malware-trends/agenttesla
[2] https://www.virustotal.com/gui/file/5254a36f51199786127851940e49c50ffe04aafa091ba6518118125bd68a4c31/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | Greenwich Mean Time | Oct 27th - Oct 31st 2025 |


Comments