Emptying the Phishtank: Are WordPress sites the Mosquitoes of the Internet?
[This post was created with help from Jesse La Grew, one of our SANS.edu undergraduate student interns]
In November, an accountant working for a construction company received an innocent enough-looking email: An update on the terms to submit bills to a local county. Seeing the email, the accountant clicked on the link and quickly downloaded the new document after entering their Outlook 365 credentials. The PDF looked all right but was something the accountant had already downloaded a couple of weeks ago from the county’s official website.
A few weeks later, the accountant noticed that a payment from the county was overdue. They picked up the phone and called their contact. The county had paid the bill, and the connection noted that they sent the money to the new bank account provided by the company.
This, turns out, was a typical case of “business email compromise.” An excellent, old phishing scam initiated it. From the “kid living in mom’s basement,” “organized crime,” to “state actors,” phishing is the arrow in the attacker’s quiver that doesn’t seem to get dull. Phishing attacks usually come in three stages:
1. The Email
Attempting to distinguish yourself as a red teamer or trying to get promoted quickly by the criminal gang you are working for? This is where you show your skill. Most phishing emails are a game of “Numbers” in playing the odds of finding a few users who haven’t seen that phishing email yet. Better emails target specific groups or individuals, and even some of the initial “conversations” can be scripted to establish a rapport with the victim.
2. The Landing Page
This is where we will be focusing. The attacker needs a reliable way to host a landing page. The landing page will usually mimic a common login form or link to another resource to make attribution and filtering more challenging. In some cases, these landing pages will adapt themselves to the victim by prefilling logos or form content. Code to block specific known security companies from discovering the page is very standard.
3. The Execution
Sometimes automated and immediate, but often delayed by months, the attacker will attempt to use harvested credentials. Specific groups have also specialized in collecting credentials to sell them to other groups.
Our work here looked explicitly at the landing pages: Where are they hosted, and what can be done to dry up the supply of hosting opportunities for phishing landing pages.
Methodology
We used Phishtank [phishtank] and its verified phishing page URLs repository. After downloading the daily list of phishing URLs, we used a script to categorize them. First, the page was downloaded to look for evidence of specific content management platforms. We also looked at the IP the page is hosted at and consulted URLScan [urlscan], which indexes pages and identifies hosting platforms and other frameworks used.
Results
We ran into a classic 80/20 principal problem. 4 Platforms make up 97% of the phishing problem: WordPress, Google Sites, Adobe Experience Manager, and Weebly (the last one contributing only 7%).
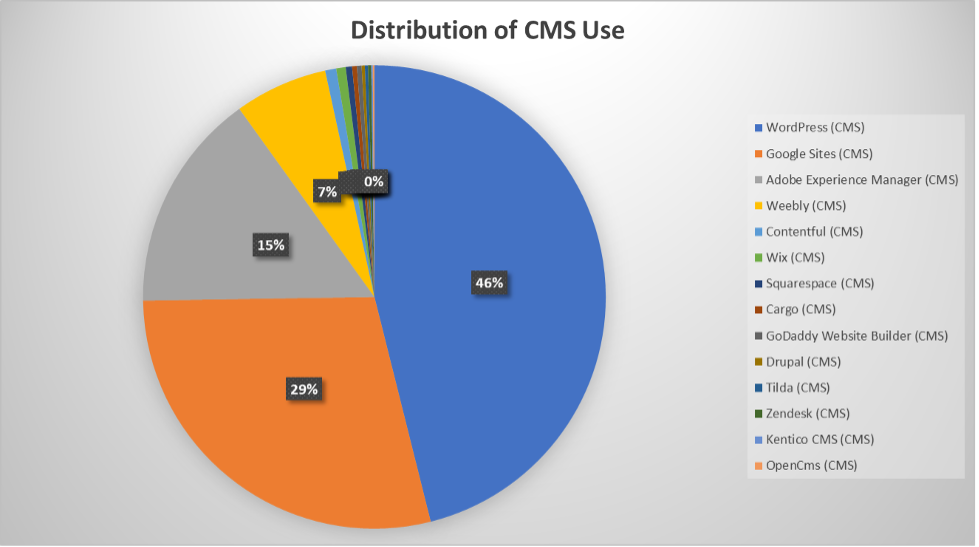
Distribution of Phishing Sites by CMS
According to w3Techs, WordPress is used by about 43% of all websites [w3techs]. Of the phishing sites that used a CMS, 46% of those used WordPress. WordPress may be used as a self-hosted and managed platform for free or as part of the commercial WordPress.com service. From the data collected, most sites were using third-party hosting and had customized domain names. Less than 1% of sites were affiliated with networks hosting WordPress.com content. We assume that the vast majority of compromised WordPress sites are self-hosted.
The WordPress platform and plugins used have a well-documented history of vulnerabilities. Many of the plugin vulnerabilities are never patched. Even if a patch is available, these sites can be challenging to update. One of WordPress’s selling points is its ease of use. WordPress sites are often used by small businesses and hobbyists who cannot maintain them properly. Even the hosted platform has its issues. While the sites are patched, and the platform is maintained and protected by WordPress.com, users still often use weak passwords or are falling for phishing themselves.
It is more challenging to get good market share numbers for Google Sites and Adobe Experience Manager. Google sites do not require a “compromise” to be used as a phishing site, but a user may just set up a site and install a phishing package. Google has been rather sluggish in removing these sites (more about that in a later post).
Lessons / Defenses
The prominence of WordPress was not unexpected. WordPress has been an ongoing threat to the Internet. Just this week, a large DDoS attack against sites in Ukraine was launched by injecting JavaScript into compromised WordPress sites [BleepingComputer]. Removing compromised code or shutting down compromised sites is almost impossible. WordPress is some ways is like a Mosquito. By itself, it is annoying and more than a nuisance, but due to their large numbers, these sites are a killer and a threat to the Internet’s infrastructure.
For cloud providers offering free content hosting, effective mechanisms are needed to proactively identify and eliminate content used for phishing sites.
If you are not willing or able to maintain and secure WordPress: Discontinue its use now or migrate to a hosted solution like for example WordPress.com. This isn’t limited to WordPress, but to any plugin that may be used within the platform.
Phishing sites are hosted on popular free or low-cost hosting platforms. They will often exploit vulnerabilities to compromise existing sites. Compromising an existing site will allow flying under the radar for site reputation services. Even if the possibility were removed to compromise an existing site, there are still readily available free services available to bad actors.
Blocking WordPress or Google Sites entirely is not an option. Too many valid sites are hosted using these services and software. Sending takedown notices beyond reporting the sites to PhishTank, is ineffective [Susan Ramsey]. But awareness of the large number of phishing sites hosted on these services, and pressure on these services to reduce the phishing sites, is needed. Rethinking how these services are maintained and how their customers are validated can help to address many of these challenges. There is a lot of damage that can occur in a short period of time and efficient phishing website takedowns may not address all risks.
A variety of mitigations are needed since there is always a limit to the technical controls that can be put in place. This is especially true when many resources are out of the direct control of an organization. Education and awareness programs can help end-users better identify suspicious emails and report them appropriately. Where phishing emails are concerned, the most flexible solution is also the location where the compromise often occurs. A phishing URL is no help to a bad actor if the site is not navigated. In addition, email controls can also help to identify and remove suspicious emails before it gets to an end-user.
[phishtank] https://www.phishtank.com
[urlscan] https://urlscan.io
[w3techs] https://w3techs.com/technologies/overview/content_management
[Susan Ramsey] https://www.sans.edu/cyber-research/can-we-move-past-blocklists-to-automated-takedowns/
[BleepingComputer] https://www.bleepingcomputer.com/news/security/hacked-wordpress-sites-force-visitors-to-ddos-ukrainian-targets/#.YkMRYcj5wFQ.twitter
| Application Security: Securing Web Apps, APIs, and Microservices | Las Vegas | Sep 22nd - Sep 27th 2025 |


Comments