Scanning s3 buckets
by Manuel Humberto Santander Pelaez (Version: 1)
We frequently see news of information leaks that occur in different companies due to having information in the cloud with the wrong permissions, allowing anyone access to potentially confidential information.
Why do people remove restrictions and allow a bucket to be public? Regardless of its intention, on many occasions it corresponds to inappropriate devops practices where objects are created from development without security measures and make their transition to production in the same way.
In this diary we will look at how to scan S3 buckets on AWS with incorrect public access permissions. For this we will use the s3scanner tool, which you can get from https://github.com/sa7mon/S3Scanner It requires the creation of a file containing the names of all buckets to be enumerated. For this case, I proceeded to create a bucket with a hackable name and it will be the only name that contains the file:
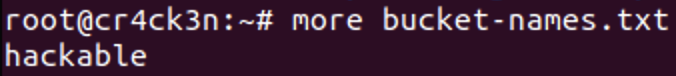
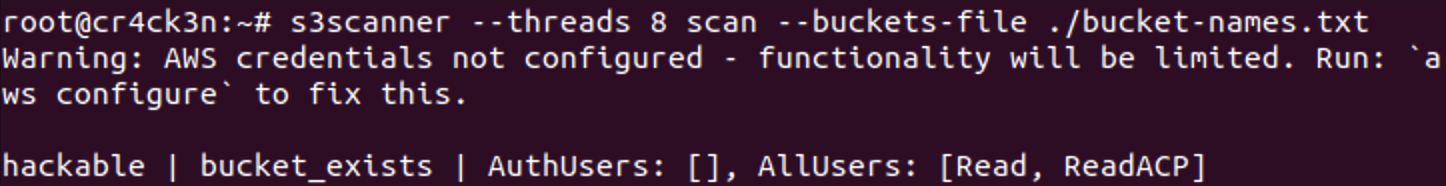
After this, we proceed with the execution of the tool. It is important to note that we are doing an enumeration exercise that does not involve configuring AWS credentials, which is why we will get a warning that still does not interfere with the result we seek to obtain:
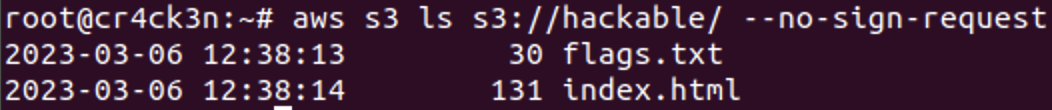
Let's see what files are present using AWS Cli:
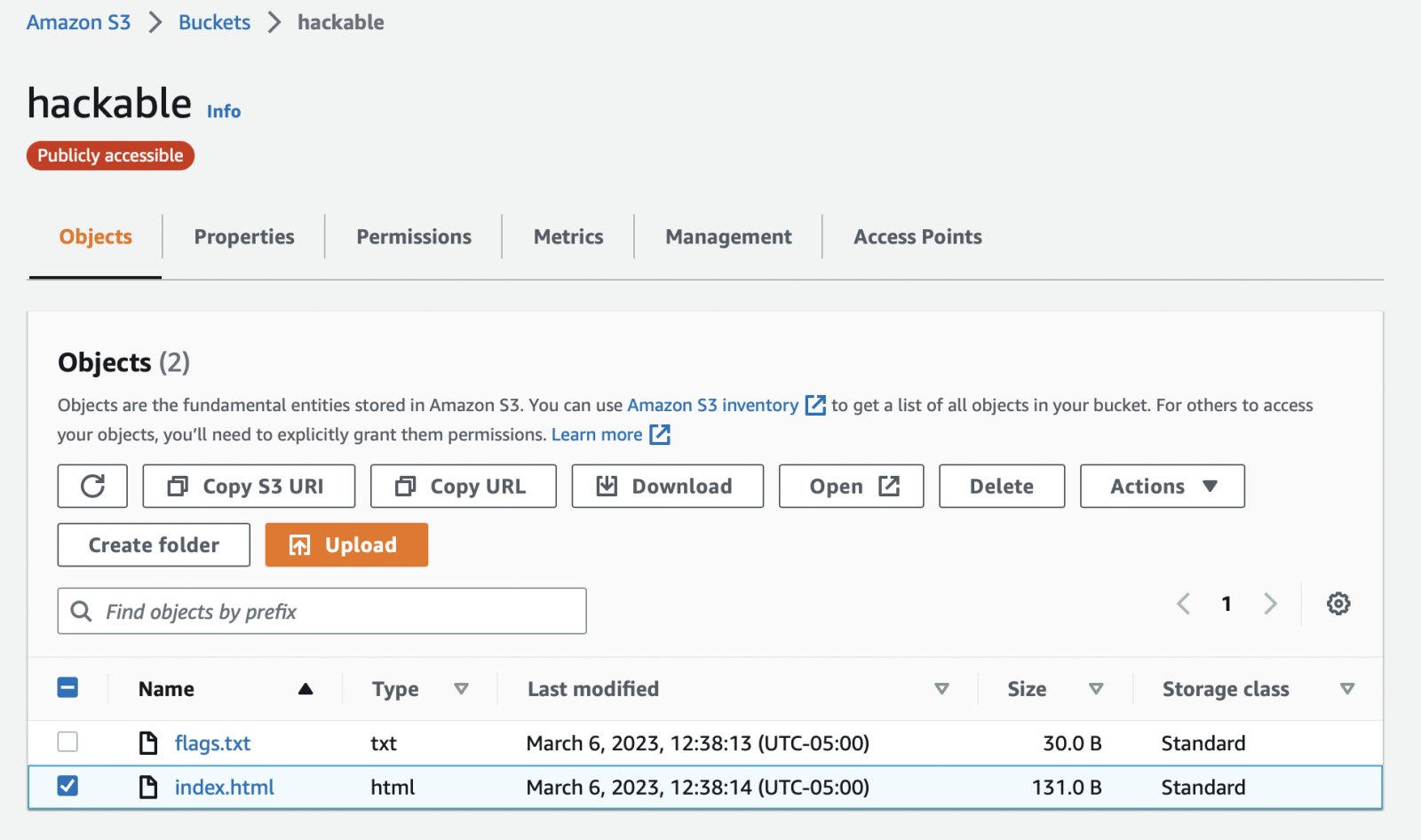
And, of course, AWS console shows a mayor warning as publicly accesible with this bucket:
Changing permissions on cloud artifacts can easily go unnoticed. To manage problems like these, it is necessary to have a control that performs the automated review of the security posture in the cloud, in such a way that it alerts when this kind of permission change occurs and thus the corresponding actions can be taken. We will review this in a future diary.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Mastodon:manuelsantander@infosec.exchange
email:msantand@isc.sans.org



Comments