Intersting Facebook SPAM
Facebook is kind of training its user base that it is OK to click on links in emails, as long as they look like pretty buttons. When there is a friend request, or a comment has been added, in the interest of making sure that you get the message it is emailed. It was probably only a matter of time before Facebook like SPAM/PHISH email started arriving.
When I received the following, I must confess I nearly clicked it automatically, before I noticed the actual link.
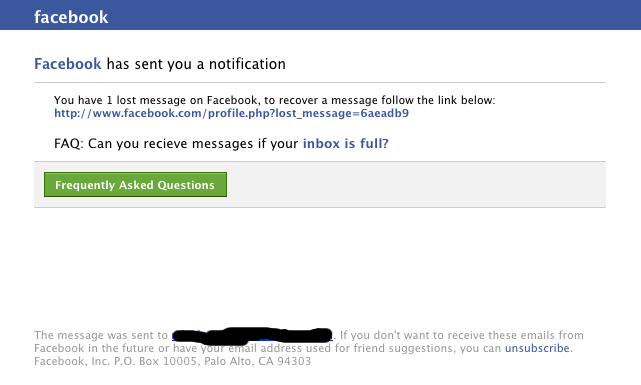
When I did click the link, I got a second surprise. To be honest I was expecting a facebook login page, failing that I was expecting malware, but what I ended up with was this. Plain old SPAM
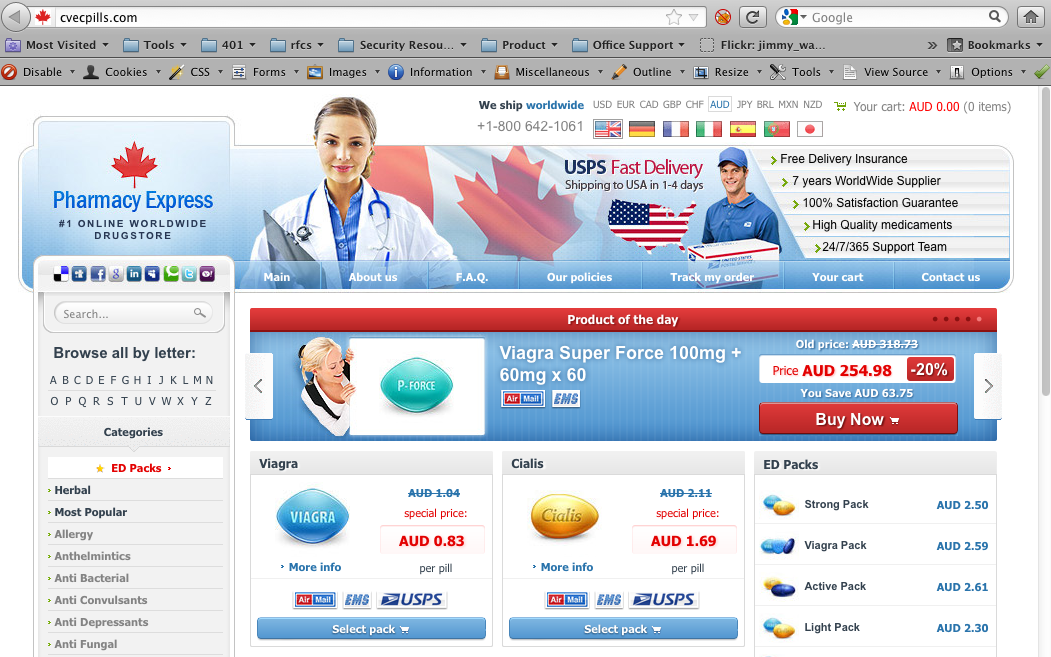
Not terribly exciting I agree. What caught my eye however was that the SPAM email looked darn close to the real thing, the emails Facebook users get every day.
If you have a user base that uses Facebook, you may wish to bring this to their attention. At the moment it is only SPAM, but it doesn't have to be.
If you are into blocking, this particular SPAM run ends up on 115.145.129.35 (South Korea), loads medicalaf.ru (In China) which redirects to cvecpills.com (In Romania). Not a bad method to get some distance between the emil and the eventual landing page. Allows them to switch targets easily.
Mark H - Shearwater


Comments
Mr.Clarke
Feb 17th 2012
1 decade ago
Spammers are getting better at using spell checkers, but apparently they are still not standard equipment in the spammer's toolkit!
Paul
Feb 17th 2012
1 decade ago
Al of Your Data Center
Feb 17th 2012
1 decade ago
MiKaVienna DeepSec
Feb 22nd 2012
1 decade ago
Travis
Feb 22nd 2012
1 decade ago