The Side Effect of GeoIP Filters
IP location, GeoIP or Geolocalization are terms used to describe techniques to assign geographic locations to IP addresses. Databases are built and maintained to link the following details to IP addresses:
- Country
- Region
- City
- Postal code
- Internet Service Provider
- Coordinates (Longitude, Latitude)
- Autonomous system (BGP)
There are many IP location service providers like Maxmind or DB-IP. Some are free, other are paying. How and when IP location can be useful? Usually, to give more visibility to reporting. The map below represented the geographic location of hosts that connected to my honeypots for the last 24 hours:
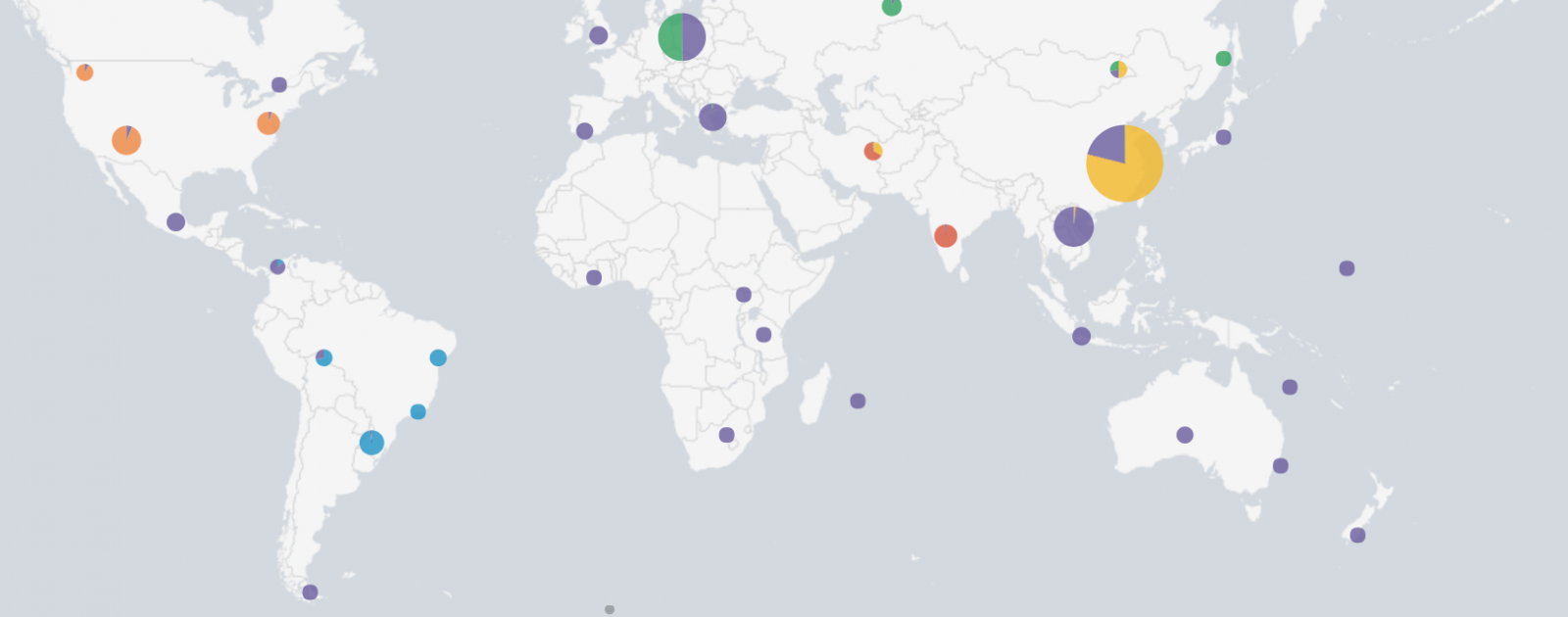
IP location can be used to enrich your data and improve visibility in security dashboards:
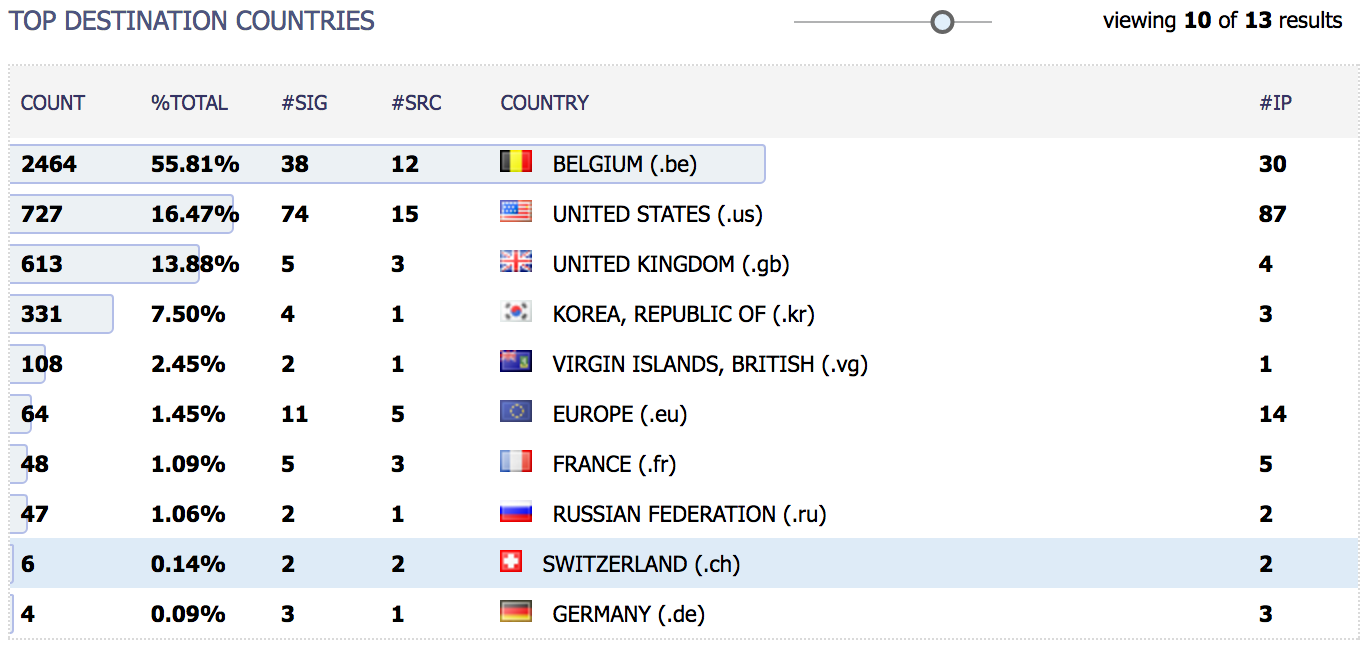
If increasing visibility is a nice feature, why not use IP databases also for defensive purposes? Some security products propose this feature. You can block traffic coming from certain regions:
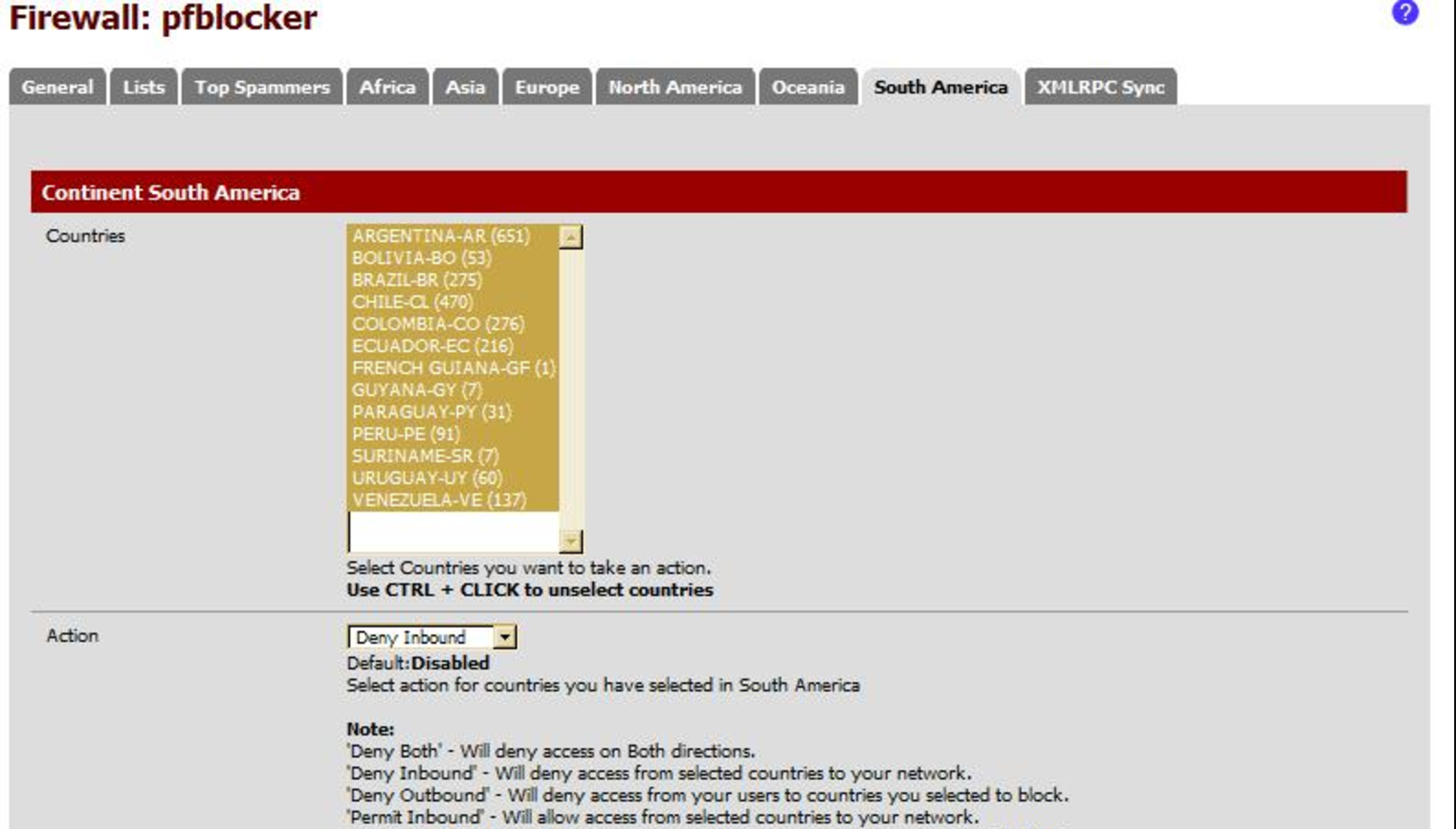
If this looks very “aggressive”, in some cases, it can be useful if you want to protect online services used only by local people (from your country). If you don’t make business with China, you should not receive connections from Chinese IP addresses. This sounds legit. However, this control may have nasty effects. The IPv4 address space being fully assigned[1], organisations which need more IP addresses are looking to buy some subnets from other organisations which have unused allocations. A new business is born!
One of our readers, based in the US, contacted us about an issue with a /19 subnet they bought from an ISP in another country. They started to allocate IP addresses from this /19 to their customers and some of them were not able to connect to 3rd-party websites. After some investigations, the affected websites used IP location databases to restrict access from “trusted” countries (note the quotes!). Their IP location databases being too old, the IP addresses were still referenced as assigned to their old country and… blocked!
How are those databases updated? The Internet topology is changing daily and IP ranges are (re-)assigned all the time. Most of the GeoIP database providers use whois records to track changes and update their database as fast as possible. Maxmind is transparent about the accuracy of their data[2]. They also propose a form to submit changes. Here is an example of the database accuracy for Belgium:
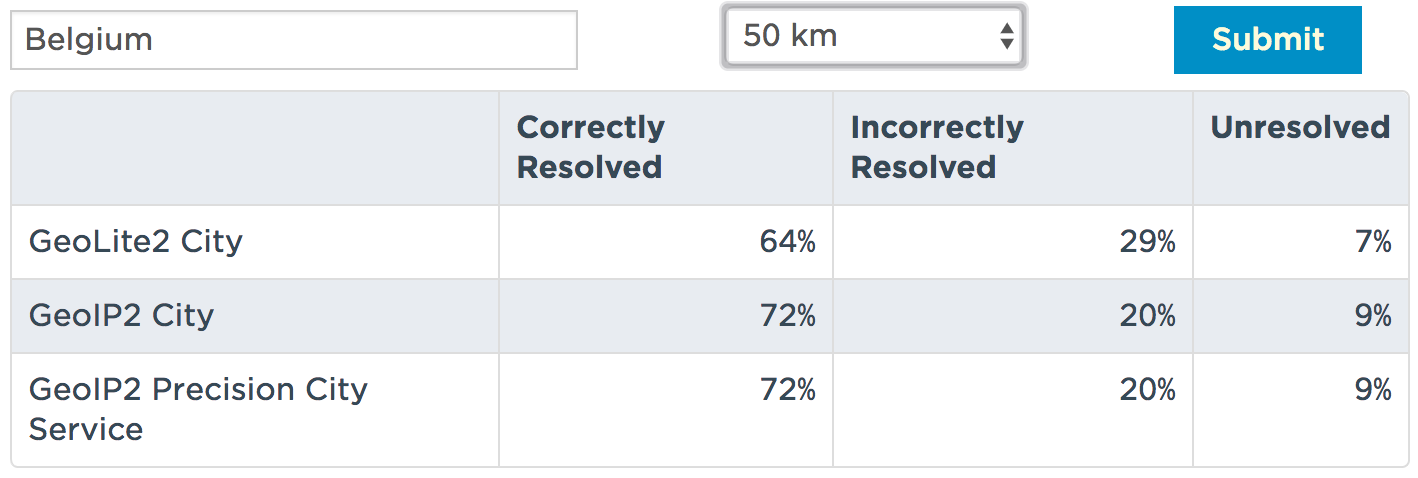
Even if databases are constantly updated (the update rate may also depend on your subscription - free or paying), it’s the responsibility of the end-user or the security solution provider to implement a process to automatically update databases. It’s possible to check the version using the command line. Here is an example with Linux and the GeoIP tools:
root@so:/# geoiplookup -v 8.8.8.8 GeoIP Country Edition: GEO-106FREE 20170307 Build 1 Copyright (c) 2017 MaxMind GeoIP City Edition, Rev 1: GEO-533LITE 20151201 Build 1 Copyright (c) 2015 MaxMind Inc All Rights Reserved GeoIP ASNum Edition: GEO-117 20170306 Build 1 Copyright (c) 2017 MaxMind Inc All Rights Reser GeoIP Country V6 Edition: GEO-106FREE 20170307 Build 1 Copy GeoIP ASNum V6 Edition: GEO-117 20170306 Build 1 Copyright (c) 2017 MaxMind Inc All Rights Re GeoIP City Edition V6, Rev 1: GEO-536LITE 20151201 Build 1 Copyright (c) 2015 MaxMind Inc All Rights Reserved
I checked the new IP addresses of our readers against several online services and all of them reported an accurate location (USA). Conclusion: the blocking service was for sure using an outdated version of an IP location database. The only solution is to contact them to report the problem and ask them to upgrade.
Personally, I won’t recommend blocking traffic based on IP location. Why? The Internet has no border and you never know from where your visitors will reach you. The following Tweet is the best example:
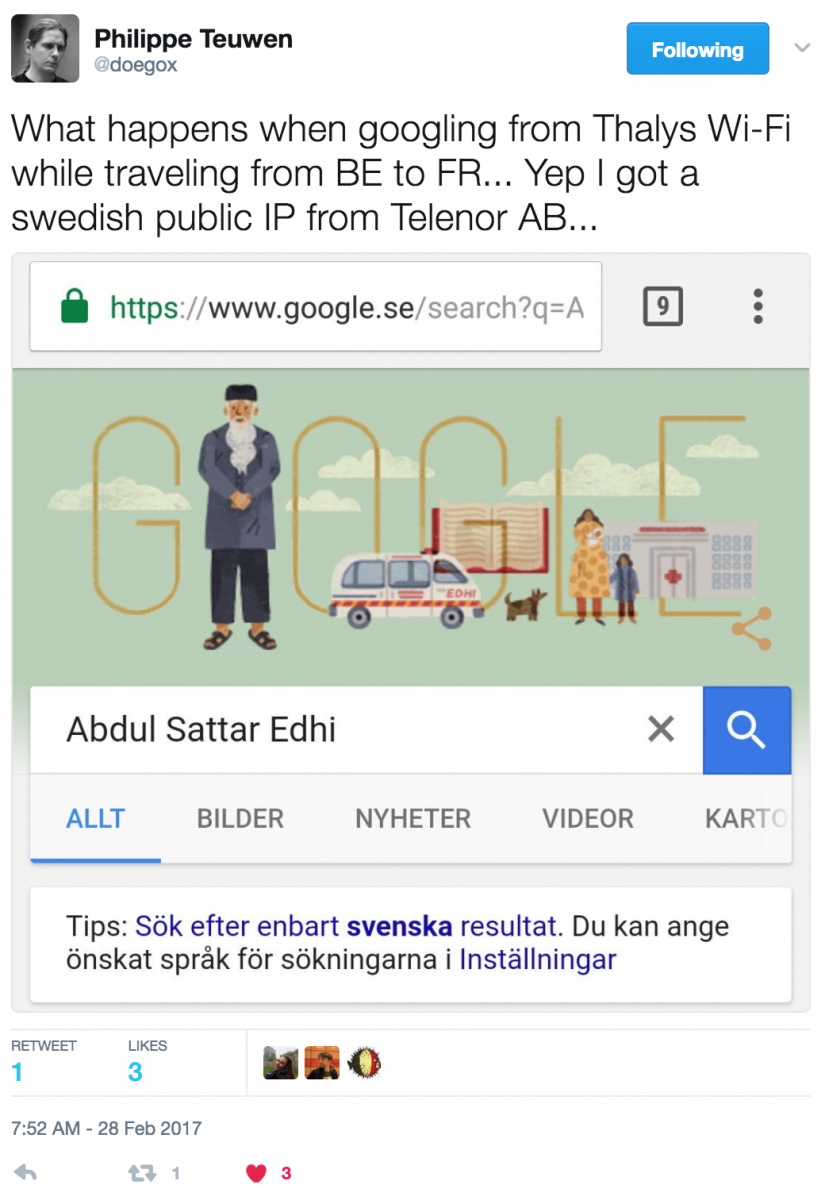
[1] https://blog.apnic.net/wp-content/uploads/2016/01/afig1.jpg
[2] https://www.maxmind.com/en/geoip2-city-database-accuracy
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | Greenwich Mean Time | Oct 27th - Oct 31st 2025 |


Comments
The Luxembourg CERT (CIRCL) proposes a nice tool called BGP Ranking: http://bgpranking.circl.lu/ which helps in detecting suspicious autonomous systems.
Anonymous
Mar 10th 2017
8 years ago
Anonymous
Mar 10th 2017
8 years ago
edit: can i further add that i have never not once run into a problem with geoip tables that i use which are retrieved from maxmind with xt_geoip_dl and created with xt_geoip_build. then again i dont have swarms of traffic.
Anonymous
Mar 10th 2017
8 years ago
MaxMind renew their databases on Tuesday either weekly or monthly (https://support.maxmind.com/geoip-faq/geoip2-and-geoip-legacy-databases/how-often-are-the-geoip2-and-geoip-legacy-databases-updated/), and they have an update program (https://dev.maxmind.com/geoip/geoipupdate/#Using_GeoIP_Update) to automate this process. Implemented auto-update properly and we had zero customer complaints.
Anonymous
Mar 11th 2017
8 years ago
Anonymous
Mar 11th 2017
8 years ago
In my personal firewalls, I pretty much shitlist all of APNIC and AfriNIC. Parts of LACNIC too. There's never been any legitimate traffic coming from those blocks. If a service provider can't deal with abuse, whether that's due to a 'I don't care' attitude or an inability to, I will also add whole CIDR ranges.
Anonymous
Mar 13th 2017
8 years ago
We've taken the stance that any country that typically won't respond to abuse@ complaints isn't on our blacklist. Any anti-western country is on our blacklist. Blacklist means no inbound or outbound traffic.
The remaining CCs we then use as a base for a greylist filter. Our greylist filter doesn't allow inbound, but will allow outbound via our secured webproxy and DNS resolvers. To complete this greylist filter, we made a list of countries which we do have contracts with and deleted them from the remaining CCs (this list of CCs is basically a whitelist), and anything left is now greylisted.
This alone has cut down on 99% of our spam. Yes, we still get spam, and yes we still have commercial spamfilter products, but the noise floor was lowered substantially. Additionally, the spam that does get through and is malicious, we follow-up on and report, both to our commercial spamfilter company, to the netblock-owning ISP, and to the company assigned the IP netblock. Guess what, the majority of the time the ISP responds and starts an investigation, and sometimes the company even responds.
Do we have struggles with this from time to time? Sure, we've needed to add some countries to our whitelist. Do employees traveling to Russia or China on personal time not have the ability to VPN or check email? Absolutely! And we don't want them to, and we force them to change their passwords immediately when they return from out of country.
Clearly this isn't a one-size-fits-all use, but it works for us. We are a local utilities business, and other than contractors or vendors we purchase from, all of our business dealings are local or at least US-based. We have an issue perhaps 1-2 times per year, but we have a process in place to troubleshoot and resolve.
Anonymous
Mar 14th 2017
8 years ago
There are several vendors in the industry and applying different approaches such as network routing in determining the location.
Below is another vendor that is showing better accuracy but I agree it is not ideal yet.
https://www.ip2location.com/data-accuracy
In conclusion, system admin should not shy away from geolocation. It is a powerful tool in preventing attacks.
Anonymous
Apr 20th 2017
8 years ago