Investigating Sites After They are Gone; And a Case of Uber Phishing With SSL
A reader sent us an interesting find of a phishing site that is going after Uber credentials. Uber credentials are often stolen and resold to obtain free rides. One method the credentials are stolen is phishing. The latest example is using convincing looking Uber receipt emails. These emails feature a prominent link to "uberdisputes.com".
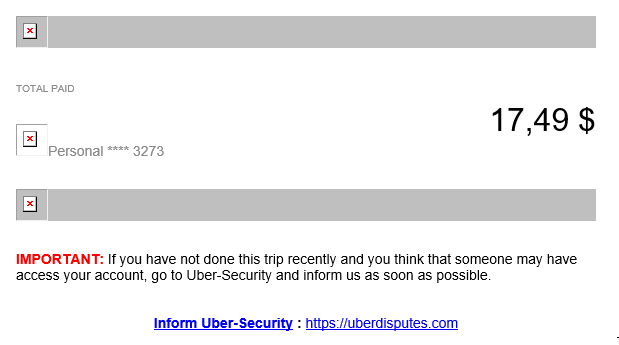
Uberdisputes.com then requests the user's Uber credentials to log in. Overall, the site uses the expected Uber layout. But more: The site uses a valid SSL certificate.
Turns out that the site was hosted behind a Cloudflare proxy. Cloudflare does issue free SSL certificates, and just like most certificate authorities, it only requires proof of domain ownership to obtain this service. This does make it more difficult to distinguish a fake site from the real thing.
Now by the time I started to investigate this, the original site was already taken down. But there was still some evidence left to see what happened. First of all, passive DNS databases did record the IP address of the site, which pointed to Cloudflare. Secondly, when searching certificate transparency logs, it was clear that a certificate for this site was issued to Cloudflare. Like for all Cloudflare certificates, the certificate was valid for a long list of hostnames hosted by Cloudflare. Sadly, it looks like whois history sites like Domaintools have no record of the site, so we do not know when it was exactly registered, but likely just before the domain started to get used.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
STI|Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Las Vegas | Sep 22nd - Sep 27th 2025 |


Comments