Windows Security Blocks UPX Compressed (packed) Binaries
Nothing surprising, but a nice story for the weekend: I was experimenting with compiling some Python scripts to run them as native Windows programs this week. I used "pyinstaller" to convert the Python script into an executable. But I was a bit shocked by the large size of the binaries (ok. I should have expected that). So I attempted to compress them with UPX, which creates nice self-extracting binaries.
Another thing that should not have surprised me: As soon as I compressed ("packed") the binary, Windows Security flagged them as malicious. Windows Security had no problem with the upx binary, only with binaries packed by upx. Part of the reason may have been that I did not sign my packed binary. I still have to see if that will help.
Here are the steps to reproduce:
- Create a one-liner:
print("Hello World")and save as helloworld.py - run pyinstaller --onefile helloworld.py which gets you helloworld.exe
- pack it with upx: upx -ohelloworldsmall.exe helloworld.exe
And wait for the Windows Security popup. You do not have to run the actual binary. Windows Security will also promptly remove it.
I specifically used a script that did not use any external libraries. There are no malicious packages I accidentally include if I do not include anything. I double-checked the UPX tool and downloaded it from various sites to ensure I didn't accidentally download a malicious version. The tool I can't verify is pyinstaller, but I did download it via pip (that doesn't say much)
This issue isn't new. About 15 years ago, Tom Liston created a tiny Windows executable (it may have been the taskbar globe to show the Infocon for Windows XP?). Tom is very proud of writing efficient code, and I am sure his executable was already much smaller than the 9 MBytes my "Hello World" script took. But he made it even smaller with UPX, which led to many anti-malware tools marking it as malicious.
Attackers lover UPX. Not only does it make binaries smaller, but it also makes it more difficult to reverse them. There are also tricks where corrupt UPX files are not analyzed by some sandboxes but will run fine if a user executes them.
But it also shows how lazy some of the signatures deployed by anti-virus vendors are. The UPX binary itself is also considered malicious by a couple of vendors. UPX does have legitimate uses and, by itself, is certainly not malicious. Here are some past reports of Windows Security flagging UPX: https://github.com/upx/upx/issues/337 . And the virus total page for the current Windows UPX binary:
32-Bit Version: https://www.virustotal.com/gui/file/d634cde09d1aa1320a1d4c589d35d306f8350129faf225b2bca394128c2c4442
64-Bit Version: https://www.virustotal.com/gui/file/24624a9d3786d7ba93575383edf694505453af59b39b0463260a75c6344d0ae7
(Interestingly, Palo Alto considers the 32 Bit version malicious, but the 64 Bit Version is ok)
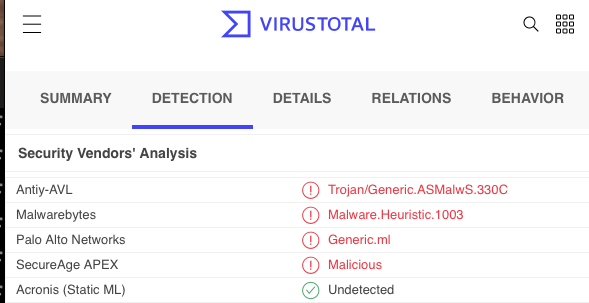
Virustotal detection for the 32-Bit version of UPX
Quick video demo of the experiment: https://youtu.be/DvAqnupF4fQ
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Las Vegas | Sep 22nd - Sep 27th 2025 |


Comments