Building a Live SIFT USB with Persistence
The SIFT Workstation[1] is a well-known Linux distribution oriented to forensics and incident response tasks. It is used in many SANS training as the default platform. This is also my preferred solution for my day-to-day DFIR activities. The distribution is available as a virtual machine but you can install it on top of a classic Ubuntu system. Today, everything is virtualized and most DFIR activities can be performed remotely with the provided VM but... sometimes you still need a way to perform local investigations against a physical computer. That's why I always carry a USB stick with me. Before I was using Kali which provides a standard solution.
But, how to build a live USB SIFT. The key requirement is to implement persistence. For two main reasons;
- Keep your scripts and settings used to expand the default SIFT capabilities
- To save the collected data
Many computers have multiple USB ports, so you can boot a SIFT connected to one port and save your data/images/... on a storage device connected to another port. Except when the computer has only one port available!
To build my live SIFT USB, I followed this process:
Step 1: Install Ubuntu on a USB stick and enable persistence
My best choice to perform this is to use Rufus[2]. The process is pretty straightforward and the most important setting is to define the size of the persistent storage:
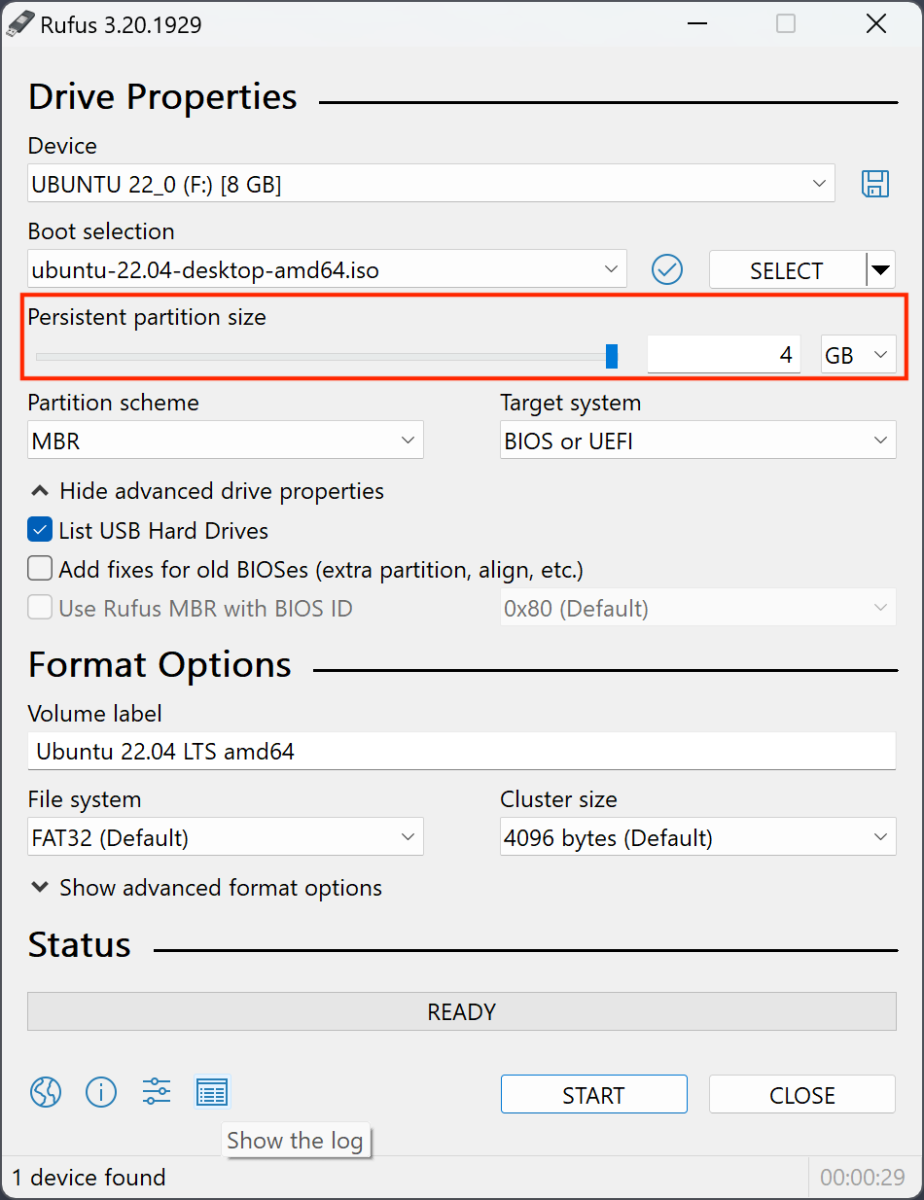
I'm using a 128GB storage and define my persistence partition to 110 GB.
Note: an alternative way to create the disk is to use mkusb[3].
Step 2: Install SIFT
Boot the freshly created USB stick and follow the process described on the SIFT website. Install Cast[4] and run:
sudo cast install teamdfir/sift
Grab some coffee, the installation might take some time depending on your hardware specifications (USB3 is a minimum) and you'll have a classic SIFT environment that you can boot now from any computer.
Step 3: Customize
Because we all have our preferred tools and pieces of scripts, install them on your SIFT as usual.
Now, you can boot it on any computer, perform investigations, and save your pieces of evidence directly on the USB stick!
[1] https://www.sans.org/tools/sift-workstation/
[2] https://rufus.ie/en/
[3] https://help.ubuntu.com/community/mkusb
[4] https://github.com/ekristen/cast/releases/latest
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | Greenwich Mean Time | Oct 27th - Oct 31st 2025 |


Comments