Analyzing Malicious RTF Files Using OfficeMalScanner's RTFScan
Attackers have been using Rich Text Format (RTF) files to carry exploits targeting vulnerabilities in Microsoft Office and other products. We documented one such incident in June 2009 ("details.rtf"). In a more recent example, the CVE-2012-0158 vulnerability was present in Active X controls within MSCOMCTL.OCX, which could be activated using Microsoft Office and other applications. McAfee described one such exploit, which appeared in the wild in April 2012:
"In the malicious RTF, a vulnerable OLE file is embedded with \object and \objocx tags. ... Upon opening a crafted file with the vulnerable application, as in other document exploit files, we see an innocent file posing as bait, while in the background, the Trojan files are installed."
How might you analyze a suspicious RTF file, perhaps delivered to you or your users as an email attachment? RTFScan, now available as part of Frank Boldewin's OfficeMalScanner toolkit, can examine RTF files and assist in extracting embedded artifacts.
Consider the "details.rtf" file, which contained an embedded PE executable without any obfuscation. In an earlier diary we demonstrated a technique for extracting the PE executable from this file with the help of sed, Perl, hexdump and dd. RTFScan makes the task easier:
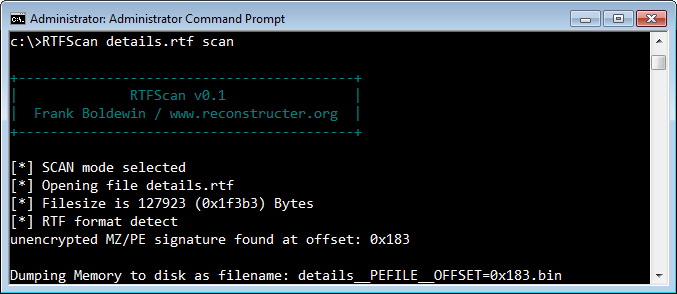
RTFScan automatically located the embedded PE file and extracted it.
Consider the more sophisticated example that took advantage of the CVE-2012-0158 vulnerability mentioned above. In one such incident, a file named "6TH WPCT Action Plan from Environment Group.doc" was delivered to victims by email as part of a targeted attack. Though the file ends with the .doc extension, it is actually an RTF file. RTFScan can scan it and identify malicious artifacts:
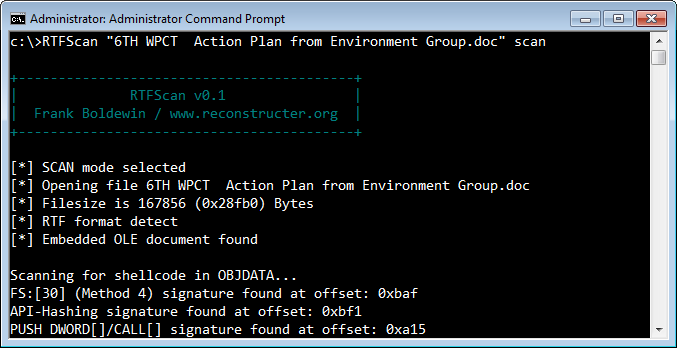
In this case, the malicious executable wasn't directly stored within the RTF file. Instead, the RTF file embedded an OLE object that included the attacker's shellcode. A vulnerable version of Microsoft Word could be tricked into executing the shellcode, which deobfuscated and extracted the malicious PE executable hidden within it.
RTFScan located the embedded OLE object and extracted it. Moreover, it scanned the OLE object for the patterns commonly included in shellcode, such as "FS:[30]" (looking for PEB), API hashing and others. At this point, you could use another tool in the OfficeMalScanner toolkit, called MalHost-Setup, to extract the shellcode and debug it to better understand its functionality. (If you're wondering what the executable embedded into this sample does, see an overview by Byt0r.)
If this is interesting to you, take a look at the article How Malicious Code Can Run in Microsoft Office Documents.
-- Lenny Zeltser
Lenny Zeltser focuses on safeguarding customers' IT operations at NCR Corp. He also teaches how to analyze malware at SANS Institute. Lenny is active on Twitter and Google+. He also writes a security blog.


Comments
Hal
Sep 14th 2012
1 decade ago
Moriah
Sep 15th 2012
1 decade ago
That's why I turn off JavaScript in Adobe Reader - although, I'm not sure if that helps much. Of course, every time Reader gets an update, many settings revert to their defaults and JavaScript is magically re-enabled. (similarly, updating Java seems to switch my desired daily checks for updates to the default weekly/monthly checks)
yvesk
Sep 15th 2012
1 decade ago
https://www.usenix.org/legacy/event/leet10/tech/full_papers/Checkoway.pdf
http://www.reddit.com/r/AskNetsec/comments/23zfck/badbios_infected_text_files/
yvesk
Apr 26th 2014
1 decade ago