Do you have rogue Internet gateways in your network? Check it with nmap
by Manuel Humberto Santander Pelaez (Version: 1)
Many people feels calm when the network perimeter of their companies is secured by solutions like firewalls, Network Access Control (NAC) and VPN. However, mobility has changed the perspective and now the users can find alternate ways to access the internet without restriction while still connected to the corporate network. Examples of this are 3G/4G modems and cellphones sharing internet access to laptop or desktop devices. You can even find small boxes like Raspberry PI that any attacker can plug to the network and get insider access from the outside.
How can you tell if there is a device that is allowing access to the Internet other than your company official internet gateway? You need to find out which devices have IP Forwarding enabled. There is an easy way to perform this task using nmap. the only prerequisite needed is for the analyzed box to accept ICMP requests. The following is an example of the scan:
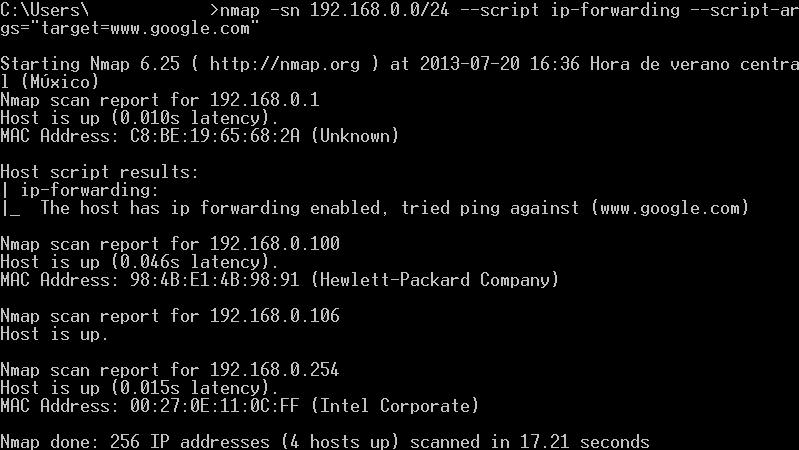
The arguments used are:
- -sn: Tell nmap to perform ping scan and disables portscan.
- 192.168.0.0/24: This is a network range to perform the scan. You can use your own range or single ip address.
- --script ip-forwarding: This script comes with all nmap installations. Sends a special icmp echo-request packet to any external device assuming that it's the default gateway.

This packet is sent to every device that answered previously the ping scan. If any of those devices have IP Forward enabled, will answer the following packet:

- --script-args="target=www.google.com": This is the external target for the echo-request packet.
I will write more about nmap scripts in my next diaries. Feliz día de la independencia para los Colombianos! (Happy independence day to Colombian people!)
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org



Comments
Anonymous
Jul 25th 2013
1 decade ago