Google ads lead to fake software pages pushing IcedID (Bokbot)
Introduction
Fake sites for popular software have occasionally been used by cyber criminal groups to push malware. Campaigns pushing IcedID malware (also known as Bokbot) also use this method as a distribution technique (we also commonly see IcedID sent through email).
This week, a new round of reports appeared about Google Ads leading to a new sites pushing IcedID.
- https://infosec.exchange/@bencrypted/109508166164779496
- https://infosec.exchange/@th3_protoCOL/109513090531163473
Based on these reports, on Wednesday 2022-12-14, I fired up my lab environment and did a Google search for AnyDesk and got a Google ad as my top result. Although the Google ad showed a legitimate AnyDesk URL, it led to a fake site after I clicked the ad.
Today's diary reviews my IcedID infection from this fake AnyDesk site.
Details
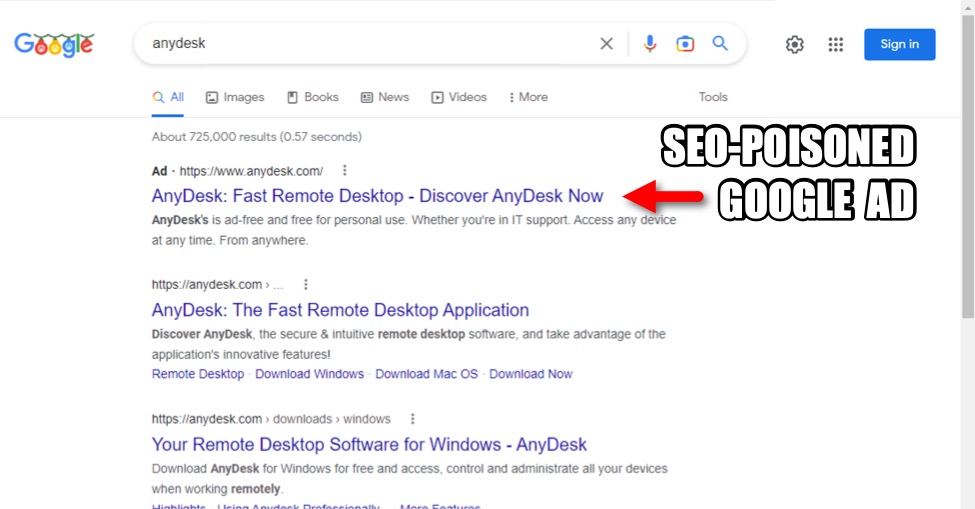
Shown above: Search results when I did a quick Google search for AnyDesk.
Search Engine Optimization (SEO) is a technique that websites use to increase their visibility for search engines like Google. Cyber criminals occasionally use SEO to direct search traffic to malicious advertisement links. These ads redirect users to fake software sites based on specific search terms. I've heard this technique referred to as "SEO poisoning."
The above image shows the top search results after I typed anydesk into Google search. The top result is a Google ad for AnyDesk, which shows a legitimate URL for the official AnyDesk site.
I clicked on the ad, and it generated the following Google Ad Services URL:
hxxps://www.googleadservices[.]com/pagead/aclk?sa=L&ai=DChcSEwjh1bP_3_n7AhXbFdQBHdF9AqwYABAAGgJvYQ&ohost=www.google.com&cid=CAASJeRovgWCSOUdKVM_De2wE7MnzlxJnzH8vREdVT_40LhQhbz-Lks&sig=AOD64_3NZNQWkb8O_B18hKIs9Q3klfDfBw&q&adurl&ved=2ahUKEwjHl6v_3_n7AhVrkmoFHdIpAG4Q0Qx6BAgDEAE&nis=8
That generated the following URL:
hxxps://clickserve.dartsearch[.]net/link/click?&ds_dest_url=https://oferialerkal[.]online/81HqPxz2?https://anydesk.com/en/features/unattended-access&id=4&gclid=EAIaIQobChMI4dWz_9_5-wIV2xXUAR3RfQKsEAAYASAAEgLqA_D_BwE
This led to a URL from a malicious traffic distribution system (TDS) domain oferialerkal[.]online. These malicious TDS domains frequenty change multiple times each day. The above URL generated HTTPS traffic to oferialerkal[.]online, which then led to the following fake AnyDesk URL:
hxxps://wwwanydesk[.]top/en/downloads/windows
This is a fake AnyDesk page, with a button to download a malicious zip archive hosted on a Google Firebase Storage URL at:
hxxps://firebasestorage.googleapis[.]com/v0/b/our-audio-370812.appspot.com/o/wnitFn4RCG%2FSetup_Win_14-12-2022_18-36-29.zip?alt=media&token=3ef517f1-eb72-46bc-ac4b-3fb41f92d373
As I wrote this diary, the above URL still worked, and it delivered a the malicious zip archive.
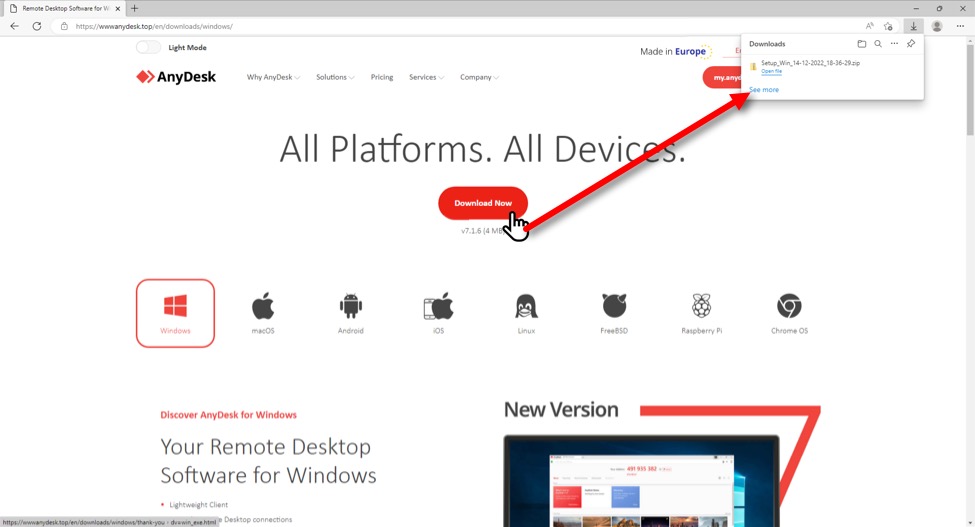
Shown above: Fake AnyDesk site delivering the malicious zip archive.
The zip archive contained a Microsoft Installer (.msi) file. Double-clicking the .msi file on a vulnerable Windows host caused it to drop and run a DLL to install IcedID on the victim's system.
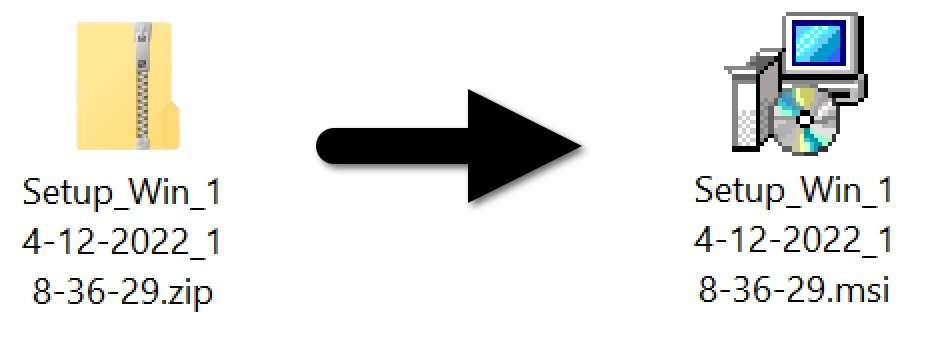
Shown above: Downloaded zip archive and extracted .msi file.
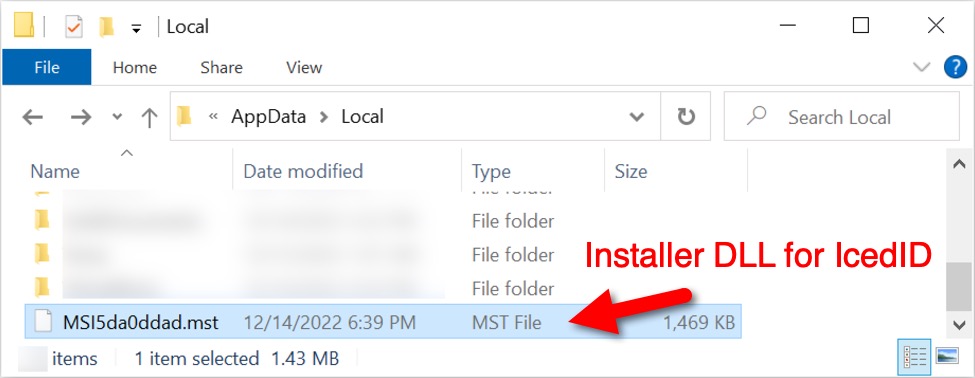
Shown above: The installer DLL for IcedID.
Traffic from the infected Windows host
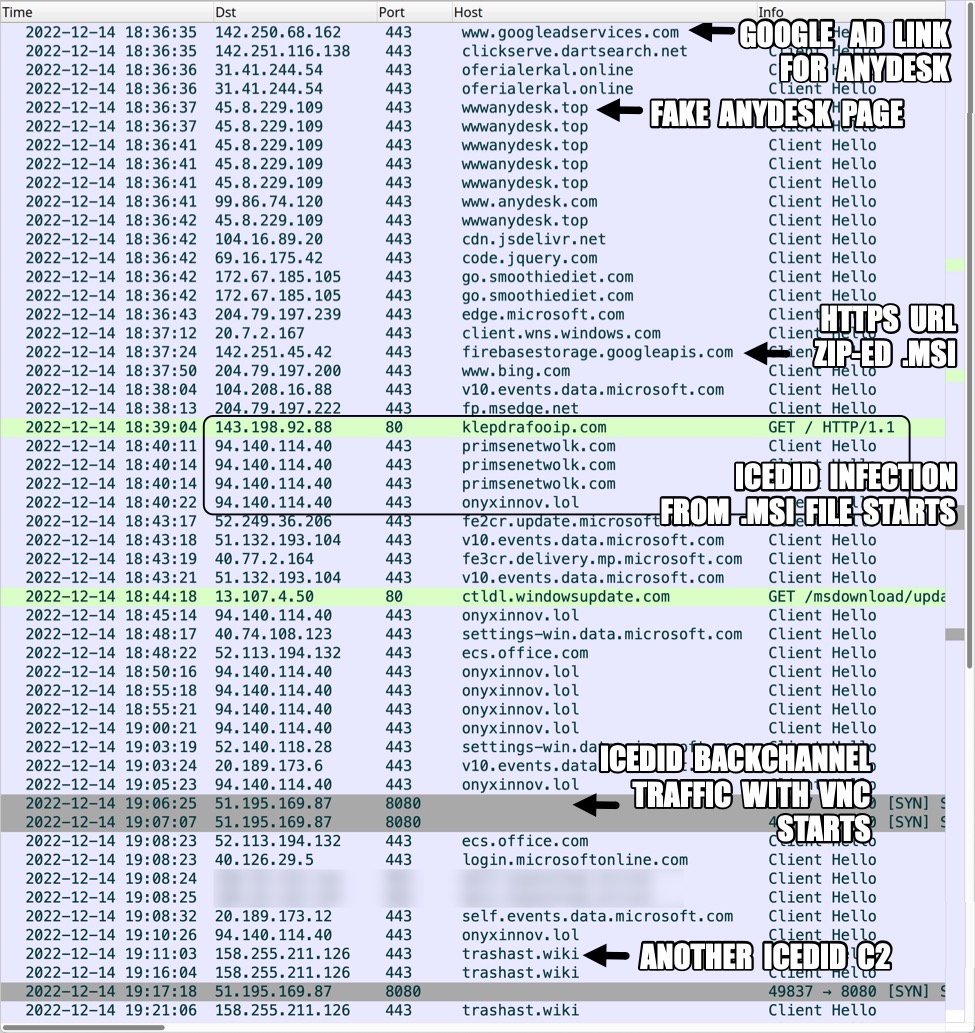
Shown above: Traffic from the infection filtered in Wireshark, part 1.
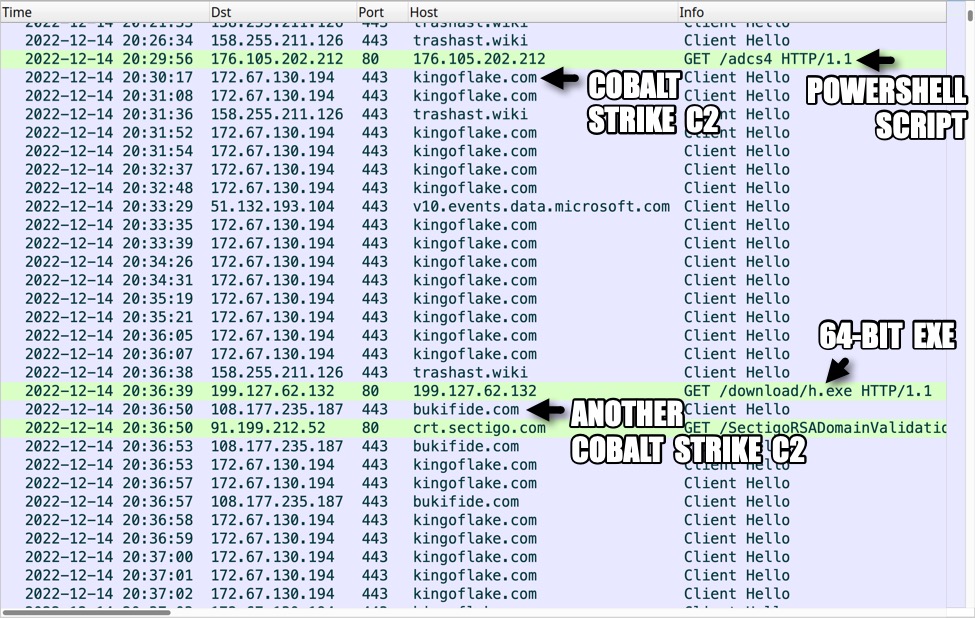
Shown above: Traffic from the infection filtered in Wireshark, part 2.
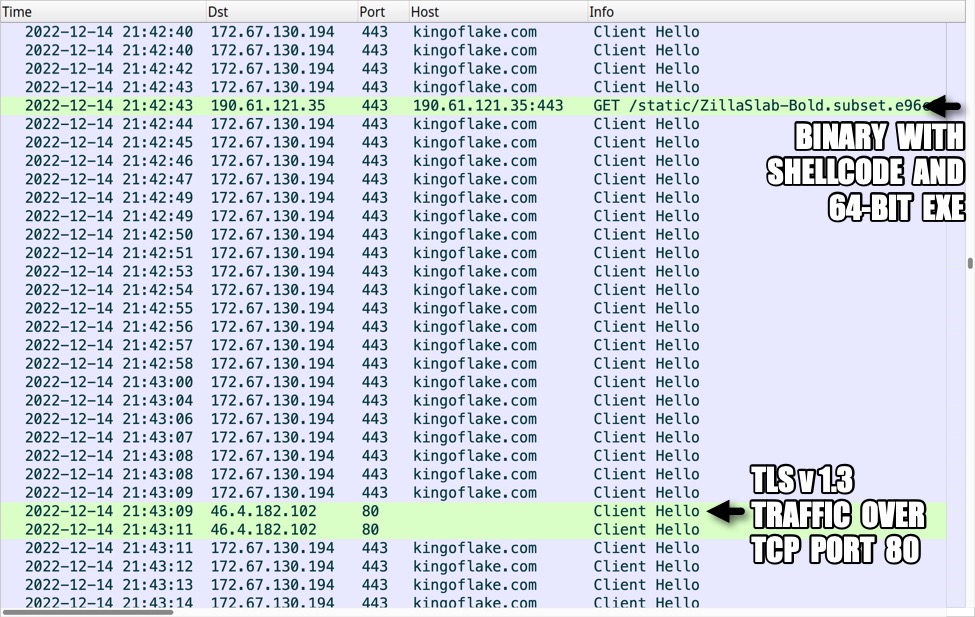
Shown above: Traffic from the infection filtered in Wireshark, part 3.
Indicators of Compromise
Traffic generated by IcedID installer DLL for gzip binary:
- 143.198.92[.]88 port 80 - klepdrafooip[.]com - GET / HTTP/1.1
IcedID post-infection C2 traffic:
- 94.140.114[.]40 port 443 - primsenetwolk[.]com - HTTPS traffic
- 94.140.114[.]40 port 443 - onyxinnov[.]lol - HTTPS traffic
- 158.255.211[.]126 port 443 - trashast[.]wiki - HTTPS traffic
IcedID backchannel traffic with VNC:
- 51.195.169[.]87 port 8080
First Cobalt Strike:
- 176.105.202[.]212 port 80 - 176.105.202[.]212 - GET /adcs4
- 172.67.130[.]194 port 443 - kingoflake[.]com - HTTPS traffic
Second Cobalt Strike:
- 199.127.62[.]132 port 80 - 199.127.62[.]132 - GET /download/h.exe
- 108.177.235[.]187 port 443 - bukifide[.]com - HTTPS traffic
Sliver and/or DonutLoader:
- 190.61.121[.]35 port 443 - 190.61.121[.]35:443 - GET /static/ZillaSlab-Bold.subset.e96c15f68c68.woff/CEx6_0FDJn4RWxBZcsquwwUk57-n7pCuR5k24zUnBepPlxY9gqn968ZXnXAtC2GwTONSpEx3Pnz_lvqz2c2E5B_7n2lMU3wZ7Yeqb9yK9OFsqEQnybJ3THr_uiJpi3X5yQI3puCyecatd8A8KWDsL6euQz1J_U-MxD8EcfWPoPWF8lqYiHLRDP1rKGIpBbW
- 46.4.182[.]102 port 80 - post-infection TLSv1.3 HTTPS traffic
Associated malware:
Downloaded zip and extracted .msi file:
SHA256 hash: 19265aac471f7d72fcddb133e652e04c03a547727b6f98a80760dcbf43f95627
File size: 1,108,416 bytes
File name: Setup_Win_14-12-2022_18-36-29.zip
SHA256 hash: 63a7d98369925d6e98994cdb5937bd896506665be9f80dc55de7eb6df00f7607
File size: 1,966,080 bytes
File name: Setup_Win_14-12-2022_18-36-29.msi
IcedID files from an infected Windows host:
SHA256 hash: 7e5da5fcda0da494da85cdc76384b3b08f135f09f20e582e049486e8ae2f168e
File size: 1,503,408 bytes
File location: C:\Users\[username]\AppData\Local\MSI5da0ddad.mst
File description: 64-bit DLL to install IcedID dropped by above .msi file
Run method: rundll32.exe [filename],init
SHA256 hash: 53639070024366d23c3de5ba1d074cbd1d8b9e78d46f75c32ef02fc20c279fc3
File size: 1,503,408 bytes
File location: hxxp://klepdrafooip[.]com/
File description: gzip binary from klepdrafooip[.]com retrieved by IcedID installer DLL
SHA256 hash: 205fbc52fafd456388d3ef80ff00498c90295791a91811725fea94052dc4fe7a
File size: 364,202 bytes
File location: C:\Users\[username]\AppData\Roaming\GenreAttract\license.dat
File description: Data binary used to run persistent IcedID DLL
Note: First submitted to VirusTotal on 2022-11-08.
SHA256 hash: bfa3eb36beeaa65334abe81cdd870e66b37da3e478d1615697160244fd087b48
File size: 1,499,312 bytes
File location: C:\Users\[username]\AppData\Roaming\{12A3307B-B372-BBC6-7E4B-4992C7C7842B}\{6127EF7F-696C-8BDF-5350-88ECC5774CA5}\uwurtb4.dll
File description: persistent IcedID DLL
Run method: rundll32.exe [filename],init --tu="[path to license.dat]"
Cobalt Strike files:
SHA256 hash: 7486c3585d6aa7c2febd8b4f049a86c72772fda6bd1dc9756e2fb8c5da67bafa
File size: 1,894,758 bytes
File location: htxxp://176.105.202[.]212/adcs4
File description: PowerShell script for first instance of Cobalt Strike activity
SHA256 hash: e8f2c929e1b84a389fede03bff9a4ee951cf563a64809b06f2f76201536fddf7
File size: 1,001,472 bytes
File location: hxxp://199.127.62[.]132/download/h.exe
File location: C:\Users\[username]\AppData\Local\Temp\Dimuak.exe
File description: 64-bit EXE for second instance of Cobalt Strike activity
Sliver and/or DonutLoader:
SHA256 hash: 40194a07a5afa1ef8e0ea4125a62d4ff5b70a14849b154a4694cfd08e40eb22b
File size: 17,085,660 bytes
File location: hxxp://190.61.121[.]35:443/static/ZillaSlab-Bold.subset.e96c15f68c68.woff/CEx6_0FDJn4RWxBZcsquwwUk57-n7pCuR5k24zUnBepPlxY9gqn968ZXnXAtC2GwTONSpEx3Pnz_lvqz2c2E5B_7n2lMU3wZ7Yeqb9yK9OFsqEQnybJ3THr_uiJpi3X5yQI3puCyecatd8A8KWDsL6euQz1J_U-MxD8EcfWPoPWF8lqYiHLRDP1rKGIpBbW
File description: binary with shellcode and 64-bit EXE, for Sliver-based and/or DounutLoader malware
SHA256 hash: 08dd1a4861f4d2b795efb71847386bd141caa0a7ce141798e251db8acd63d3a9
File size: 17,081,991 bytes
File description: above binary with shellcode removed
File type: PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows
Final words
We'll likely continue to see criminal groups abusing Google ads through SEO poisoning and using fake websites to impersonate popular software. This is an effective way for criminals to distribute their malware.
Traffic and malware samples from today's infection are available here.
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments