Maldoc: Once More It's XOR
I was asked for help with malicious Word document MD5 7ea8e50ce884dab89a13803ccebea26e.
Like always, I first run oledump.py on a sample:
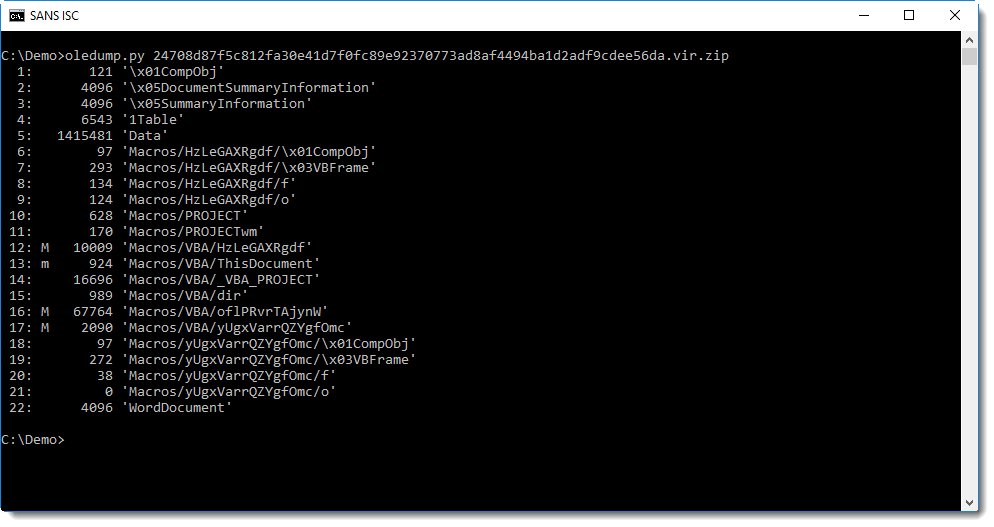
As expected, it contains VBA macros. Then I quickly look at the source code of the VBA code in all macro streams (options -s a -v):
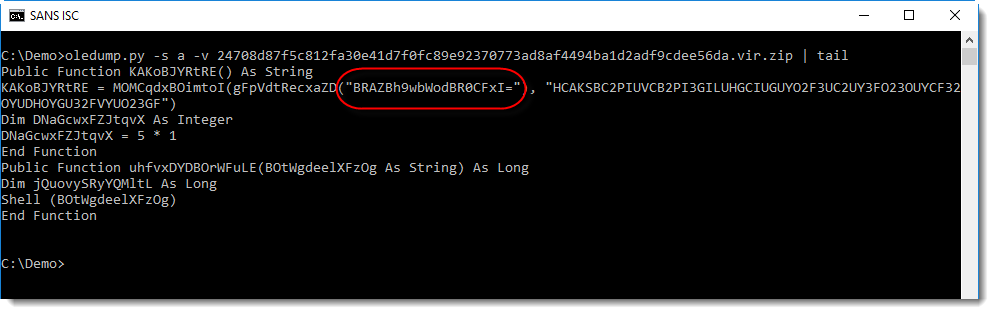
I noticed a string that looks like BASE64 at the end of the VBA source code (that's why I used a tail command in this screenshot). Checking with my tool base64dump.py confirms that this is indeed BASE64:
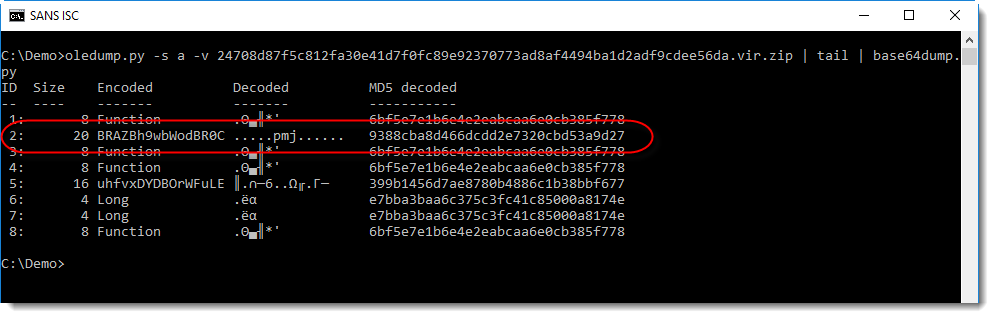
The output confirms that it is BASE64, although I don't recognize the binary data (most bytes are not printable characters).
The string is BASE64, and function gFpVdtRecxaZD is most likely a BASE64 decoder function. The return value of this function is used as first argument to function MOMCqdxBOimtoI. Function MOMCqdxBOimtoI takes 2 arguments, the second argument is a printable string.
I've seen this often before, MOMCqdxBOimtoI is most likely a decoding function, and the second string is the decoding key.
What encoding function? First I try XOR encoding, because it's popular. With my tool cipher-tool.py I check what the result is of XORing the decoded BASE64 string with the key:
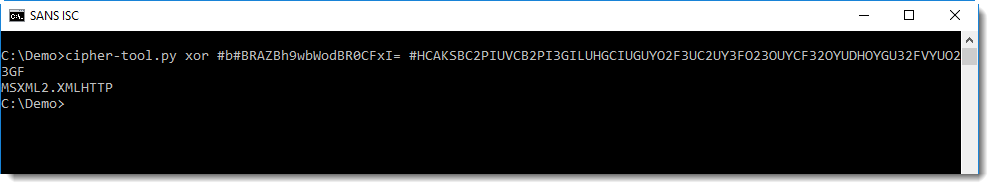
I get a readable, known string: MSXML2.XMLHTTP. This confirms that the encoding is indeed XOR and that the second argument is the key.
Grepping for string MOMCqdxBOimtoI shows me all the lines with encoded strings:
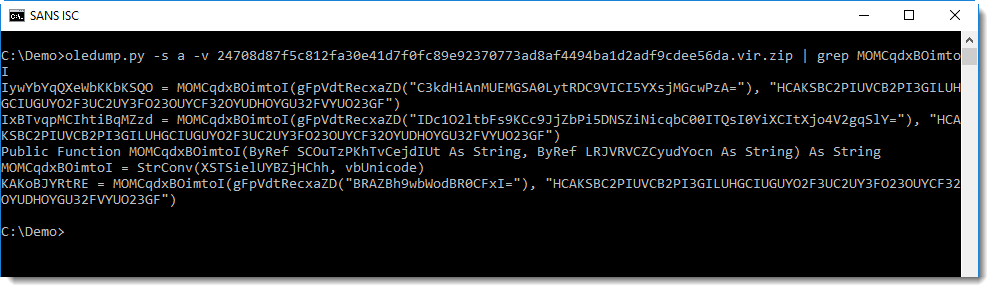
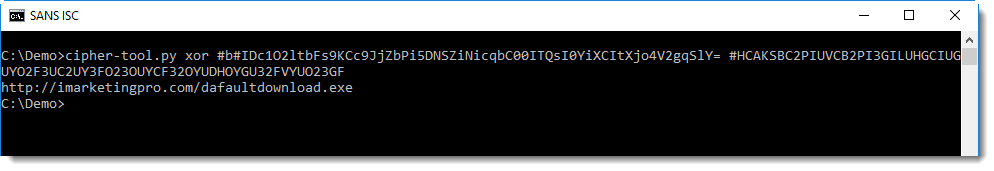
I check the longest string first, because that's most likely the URL:
This analysis can also be automated with plugins.
My oledump plugin plugin_http_heuristics was not able to decode the URL of this sample, until I made a small change:
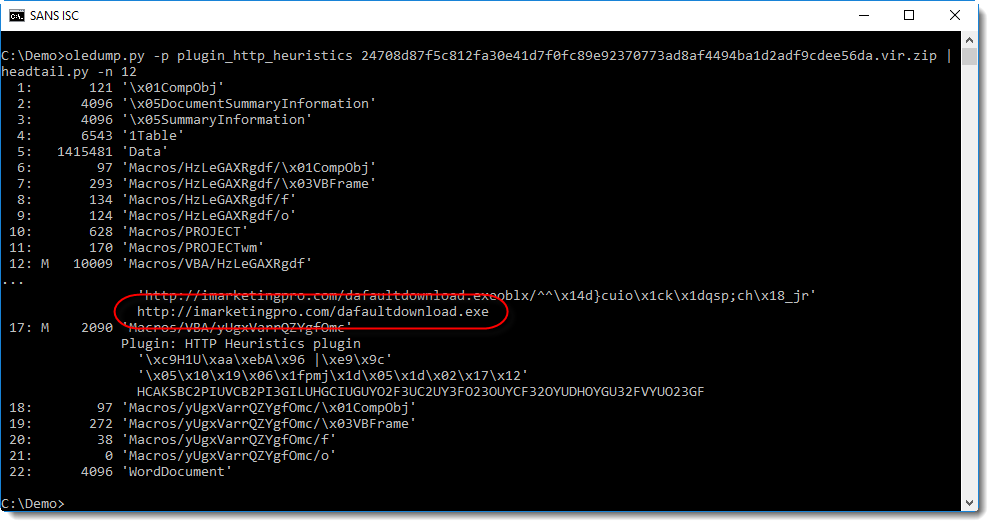
I'll explain the changes to this plugin in the next diary entry.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments
Anonymous
Oct 14th 2018
6 years ago
Anonymous
Oct 15th 2018
6 years ago
Anonymous
Oct 16th 2018
6 years ago