Malware Triage with FLOSS: API Calls Based Behavior
Malware triage is a key component of your hunting process. When you collect suspicious files from multiple sources, you need a tool to automatically process them to extract useful information. To achieve this task, I’m using FAME[1] which means “FAME Automates Malware Evaluation”. This framework is very nice due to the architecture based on plugins that you can enable upon your needs. Here is an overview of my configuration:
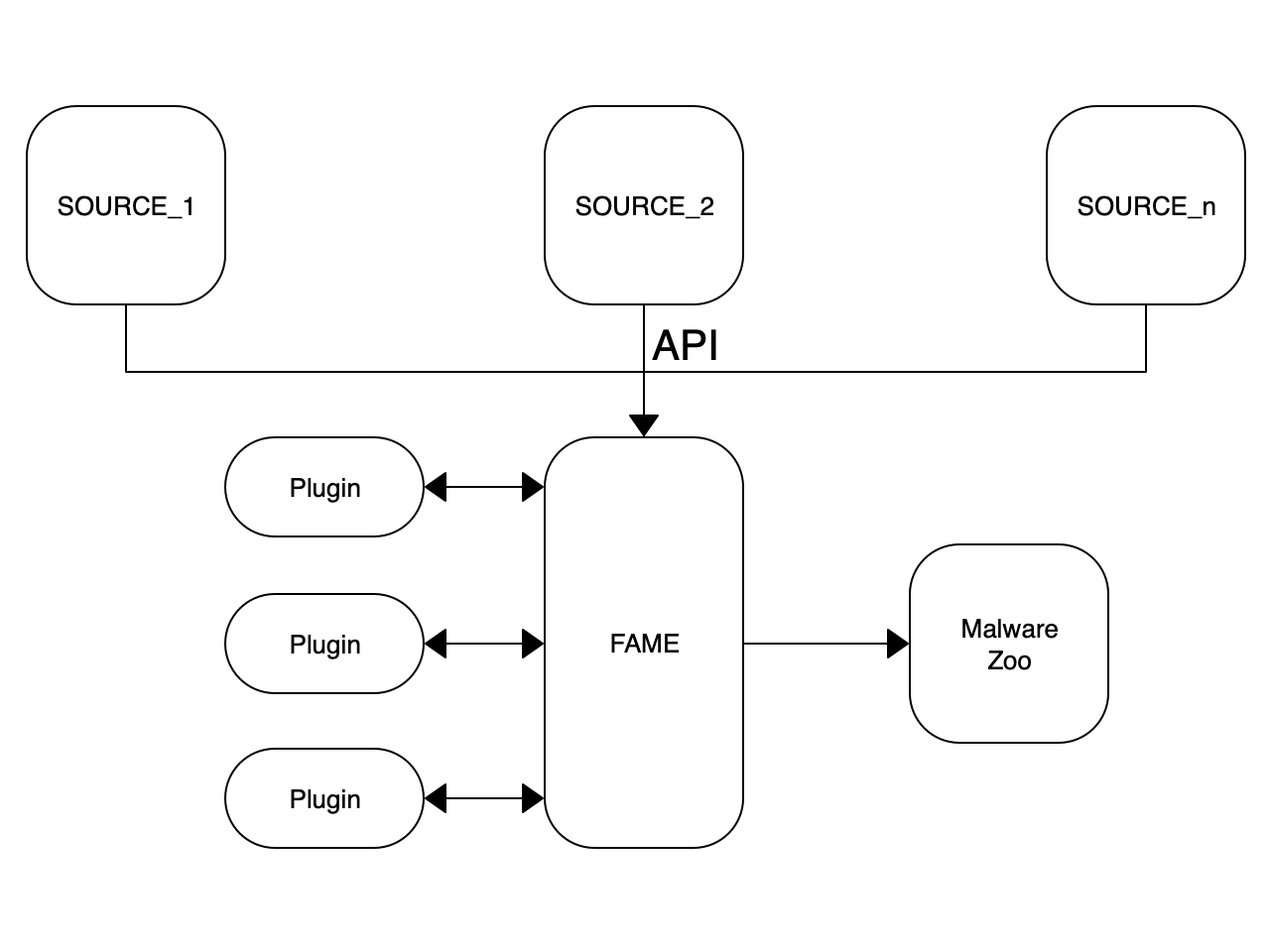
FAME has a REST API that helps to automate the submission of samples. I’ve multiple sources like catch-all email addresses from where I extract malicious attachments. Based on their MIME type, submitted files are processed with the right plugins. Example: PDF are passed to the Peepdf module:

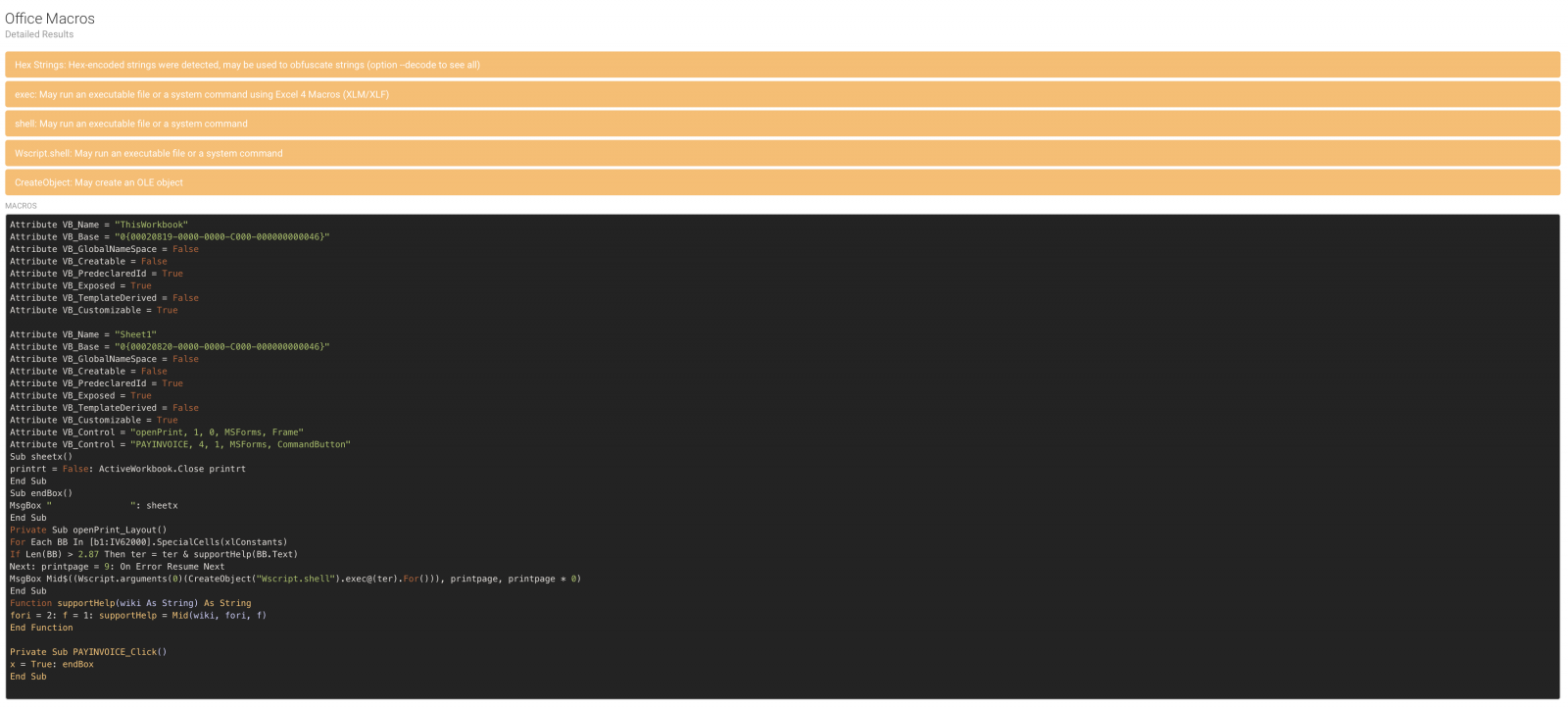
Office documents are passed to the Olevba module:
Executables and scripts are passed to the CAPE module (sandbox analysis):
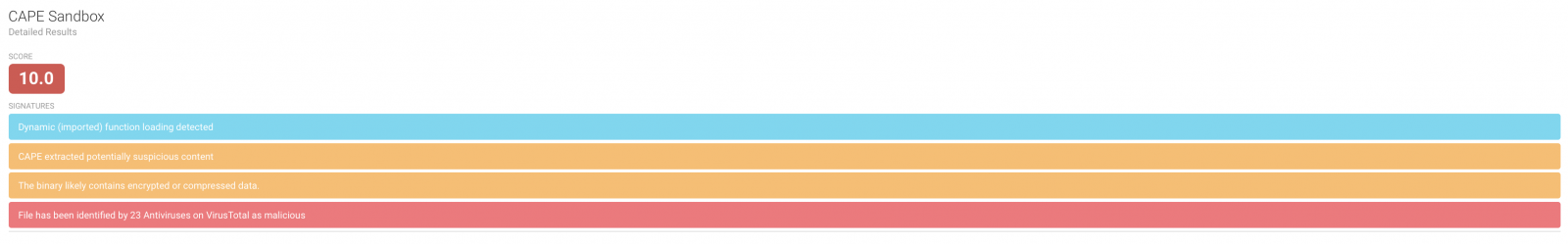
There are many modules available. Analyzing files in a sandbox, like CAPE, is very nice but it consumes a lot of resources. When you submit a bunch of PE files, it could take some time to get results.
A good point about the FAME framework: It’s easy to write your own module (in Python) to process files. To speed up the triage of malicious PE files, I created a module that uses FLOSS to extract files from executables. FLOSS[2], as the acronym says - “FireEye Labs Obfuscated String Solver”, is developed by FireEye. It is a powerful tool that offers a way to automatically deobfuscate concealed strings using common and proprietary algorithms. When you use a command like ‘strings’ against binary files, you will collect only clear-text strings:
root@remnux:/malwarezoo# strings sample.exe |head -10 !This program cannot be run in DOS mode. Richd .text `.data .rsrc @.reloc ntdll.dll KERNEL32.dll USER32.dll OPENGL32.dll
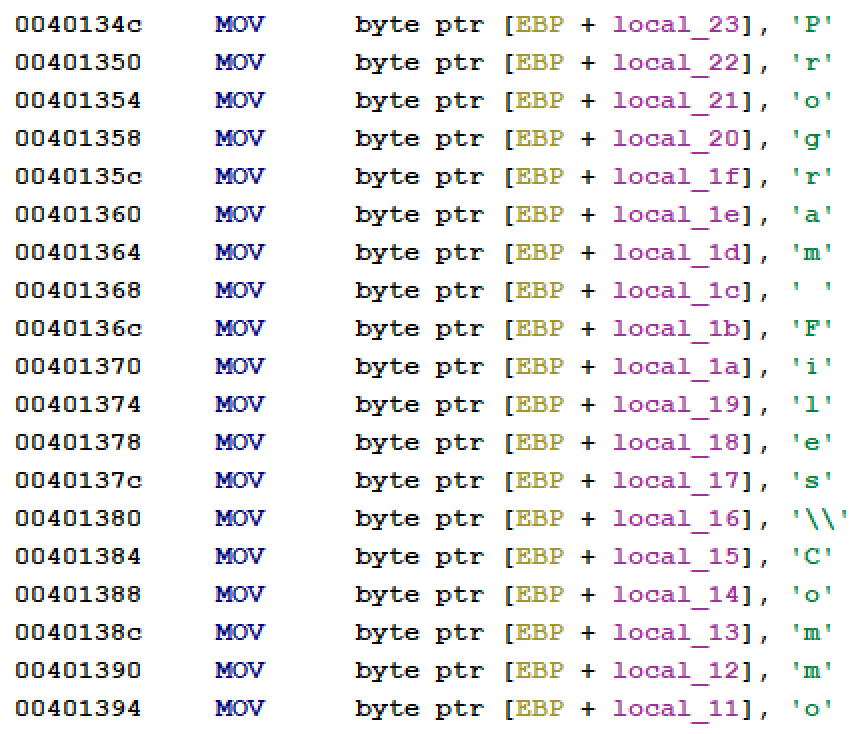
FLOSS emulates the execution of Windows executables to allow it to deobfuscate strings. FLOSS examines the file statically and locates functions that might be capable of decoding strings and emulating their execution to determine what content they are likely to produce. FLOSS can also decode stack strings:
FLOSS is available as a stand-alone binary but, being developed in Python, there is a library available that allows you to integrate FLOSS in your own tools. I wrote a FLOSS plugin that extracts strings from binaries:
- Static strings
- Decoded strings
- Stack strings
Often, just by having a look at the imports on a PE file, you can already get an idea about its behavior. Some of them are more suspicious than others. To facilitate the detection of suspicious behavior, there is a way to search for suspicious strings (a single one) or a group of strings. Indeed, some malicious features are implemented by calling a suite of API calls. A good example is a technique called "process hollowing"[3]. This technique is based on:
- CreateRemoteThreat()
- NtUnmapViewOfSection()
- VirtualAllocEx()
- WriteProcessMemory()
- ResumeThreat()
You can define your own set of suspicious strings. A simple correlation is performed by concatenating them with ‘_AND_’. Here is an example of a configuration file:
root@fame:/# cat /opt/fame/conf/floss_suspicious.txt VirtualAlloc GetLogicalDrives CreateRemoteThread RtlDecompressBuffer NtAllocateVirtualMemory NtResumeProcess SetWindowsHookEx FindWindow CreateToolhelp32Snapshot_AND_Process32First_AND_Process32Next CreateProcess_AND_UnmapViewOfSection_AND_VirtualAllocEx_AND_WriteProcessMemory_AND_ResumeThreat AllocateVirtualMemory_AND_WriteVirtualMemory_AND_ResumeProcess LoadLibrary_AND_GetProcAddress BlockInput GetModuleHandle ProtectVirtualMemory FromBase64String
Another example of correlation is: LoadLibrary() & GetProcAddress(). This combination of API calls, called "dynamic linking", is often used by packed malware.
FLOSS is much faster than a complete analysis in a real sandbox and speeds us the results in FAME. Here are the results of an analyzed file in FAME:
.png)
The script is configurable in FAME like any plugin and allows the following configuration parameters to be defined:
- The minimum / maximum lengths of strings to report
- The maximum amount of strings to report
- A list of strings to ignore (blocklist)
- A list of suspicious strings (like interesting API calls)
If you're interested in this module for FAME or just to see how the FLOSS library is implemented, I published the module on my GitHub account[4]. It's the first version and the script will evolve for sure. If you've any ideas or suggestions, let me know!
[1] https://certsocietegenerale.github.io/fame/
[2] https://github.com/fireeye/flare-floss
[3] https://attack.mitre.org/techniques/T1093/
[4] https://github.com/xme/fame_modules/tree/master/processing/floss_str
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | Greenwich Mean Time | Oct 27th - Oct 31st 2025 |


Comments