Port 51616 - Got Packets?
We're looking for any info or packets that target port 51616. After witnessing a spike yesterday on his network and checking that our port data [1] corroborated his event, Andrew has written in asking what we know.
The most useful snapshot of port activity can be seen in this graph image. I ran the graphs as far back as 2006 and nothing more signifcant was illustrated. The image below highlights yesterdays events as well as a more curious spike back in March. These counts do not seem very significant at first look, but they could clearly be telling us something.
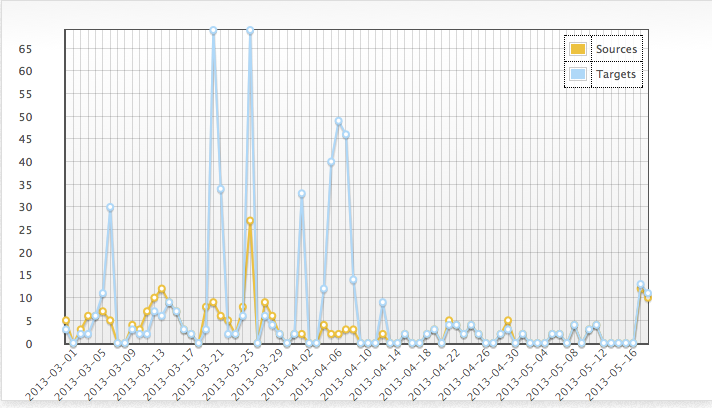
So drop us a comment to share what you know. We're interested to attribute this traffic to something useful.
[1] https://isc.sans.edu/port.html?port=51616
Update 1: ISC reader Jim suggested that port 51616 is Xsan is Apple Inc.'s storage area network (SAN) or clustered file system for Mac OS X. Xsan enables multiple Mac desktop and Xserve systems to access shared block storage over a Fibre Channel network. With the Xsan file system installed, these computers can read and write to the same storage volume at the same time.


Comments
ET SCAN LibSSH Based Frequent SSH Connections Likely BruteForce Attack!
Source port 8089, Dest port 51616
The majority of the IPs are associated with Malware, Proxies, Tor and Bruteforce SSH.
Jason
May 19th 2013
1 decade ago