Sharing Private Data with Webcast Invitations
Last week, at a customer, we received a forwarded email in a shared mailbox. It was somebody from another department that shared an invitation for a webcast “that could be interesting for you, guys!”. This time, no phishing attempt, no malware, just a regular email sent from a well-known security vendor. A colleague was interested in the webcast and clicked on the registration link. He was redirected to a page and was surprised to see all the fields already prefilled with the personal details of the original recipient:
- Name
- Organization
- Direct phone number
The link has this format:
http://go.<redacted>.com/CZL00H0wd04C0hkE140jP06
When you visit this link, based on the URI, it expands to the complete registration URL. Even if invitations are usually nominative, people share often webcast invitations with peers who can be located internally, in restricted groups or... the wild Internet (forums, mailing lists, etc). Just for the story, all communications occurred via HTTP.
It was tempting to search on Google for similar URLs:
intext:"go.<redacted>.com/"
I found 31 hits containing an URL of the same format. Let’s test some of them… The online form for the other webcast session was indeed prefilled but... with the same values (the one of the first colleague). Hmmm… Let’s see if we have some cookies maybe? Yes, we have! Let’s clear them, refresh the page and the URL decodes personal details of the attendee:
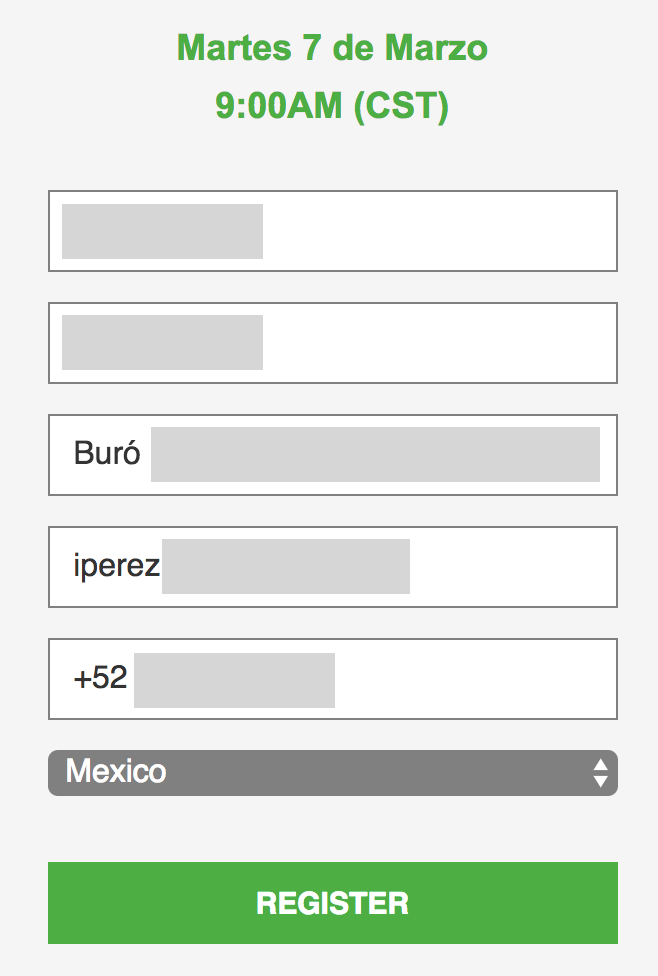
After more investigation, I found some links of the same format posted on Twitter:
Such information are a gold mine to set up a spear phishing attack! The attacker knows your details, your interests in the <vendor> products and that you attended a webinar on a specific date. Keep this in mind when sharing invitations outside a restricted audience!
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | Greenwich Mean Time | Oct 27th - Oct 31st 2025 |


Comments
"original recipient" didn't fully get that, is it the first person who registered ?
Also what could be the logic behind this , info leak from the server side or some type of bad session management ?
Thank you
Anonymous
Jun 1st 2017
8 years ago
Anonymous
Jun 1st 2017
8 years ago