Tool update: mac-robber.py and le-hex-to-ip.py
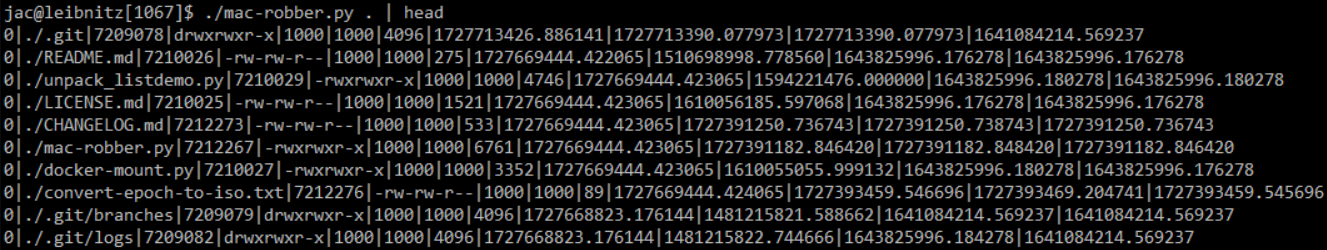
One of the problems I've had since I originally wrote mac-robber.py [1][2][3] seven years ago is that because of the underlying os.stat python library we couldn't get file creation times (B-times). Since the release of GNU coreutils 8.32 (or so), the statx() call has been available on Linux to provide the B-time, but Python out of the box doesn't yet support that call. Recently, though, I did some searches and discovered that for several years there has actually bin a pip package called pystatx that exposes the statx() call and allows us to get the B-time. So, I updated the script. It now tries to import statx and if it succeeds (probably only on relatively recent Linux distros where the pip package has been installed) it can now provide B-times. I also adjusted the formatting so the script will now give microsecond instead of millisecond resolution. I will probably write a python version of mactime at some point so that we can actually take advantage of the additional resolution.
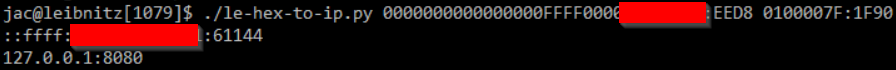
I also did another update to my le-hex-to-ip.py [4][5][6] script, this time allowing the port number to also be passed. It is something I talked about wanting to do the last couple of times I taught FOR577 and so last week when I was TA-ing for Taz, I finally got around to doing it.
If anyone has other suggestions for fixes or improvements, please let me know. Enjoy.
References
[1] https://isc.sans.edu/diary/New%20tool%20macrobberpy/22844/
[2] https://isc.sans.edu/diary/27522
[3] https://github.com/att/docker-forensics/blob/master/mac-robber.py
[4] https://isc.sans.edu/diary/New%20tool%3A%20le-hex-to-ip.py/30284
[5] https://isc.sans.edu/diary/30772
[6] https://github.com/clausing/scripts/blob/master/le-hex-to-ip.py
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
| Reverse-Engineering Malware: Malware Analysis Tools and Techniques | Online | Japan Standard Time | Oct 20th - Oct 25th 2025 |


Comments