Video: Cobalt Strike & DNS - Part 1
One of the Cobalt Strike servers reported by Brad Duncan also communicates over DNS.
This can be tested with a simple DNS TXT query:
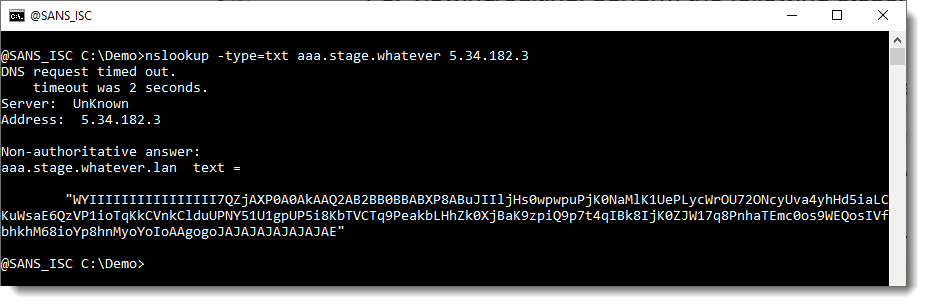
The content of this TXT record contains the start of a Cobalt Strike beacon, encoded with Netbios Name encoding. I recently published an update to my base64dump.py tool to handle this encoding.
In the following video, I show how to use my new, quick & dirty tool to retrieve all DNS TXT records (cs-dns-stager.py) that make up the encoded beacon, and how to decoded this with base64dump and extract the config with my 1768.py tool.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
×
![modal content]()
Diary Archives


Comments