Possible Botnet Scanning
We have received a report from one of our readers that their Cisco IPS are picking up a large amount of scanning traffic across a large number of monitored clients.
He indicates: "These scans started about two or three days ago and have been rolling through our clients. Once we block one source IP address, a new source IP address shows up with the same traffic shortly thereafter. The scans are firing off multiple rapid events for two signatures on our deployed Cisco IPS sensors. "
The sources are both inside and outside the US. Please let us know if you are seeing this type of activity.
Thank you to Ryan for reporting this activity to us.
He reports that the two signatures that are triggering are:
Unix Password File Access Attempt (SigID: 3201) Web Application Security Test/Attack (SigID: 7212)
Updated: We have been receiving information and samples of logs that indicate that there is indeed some activity going on, more than likely is botnet related. The information that we have received indicates that this activity is directed at port 443 and port 80. One of our readers (thanks Erik) indicated that his alerts indicate http://www.snort.org/search/sid/12709?r=1. Looking at the link in this SID it looks like the activity may be directed at Microsoft ASN.1 remote exploit for CVE-2005-1935 with an exploit called kill-bill. ( www.phreedom.org/solar/exploits/msasn1-bitstring/) All of it coincides with when the php get's started occurring. We will keep an eye on the reports and let you know if we see anything developing. Please continue to let us know what you are seeing.
Deb Hale
Firefox 4 Beta 12 released
For those of you who would like to contribute to the future of Firefox, while not quite ready for final release, Firefox 4 Beta 12 is considered "stable and safe to use for daily browsing". There are still some known issues and the Mozilla people do warn that if you are a add-on user there may be some issues with your add-ons, but with the Add-on Compatability Reporter you can assist the add-on developers as well.
-- Rick Wanner - rwanner at isc dot sans dot org - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
3 Comments
Thunderbolt Security Speculations
Today, Apple release a new set of Macbook Pros, sporting the first implementation of "Thunderbolt", a new interconnect technology based on what Intel so far called "Lightpeek". It promisses 10 GBit/sec duplex connectivity to everything from storage to video devices. The technology is similar to Firewire (aka i.Link, IEEE 1394) in some ways. Like for Firewire, multiple devices may be daisy chained. However, if a display port display is used as part of the chain, the display has to be the last device in the chain.
One speculation put forward in an article in the register [1] is that devices connected via Thunderbolt are not authenticated and like for firewire, have full bus access. This speculation is supported by the so far available material form Intel and Apple. Like with Firewire, this bus would provide direct access to RAM and possibly disks. As a result, a malicious device may be able to read RAM and disks without authentication.
These attacks have been shown to work for Firewire, and have been used for example in memory forensics to extract memory content from live systems. However, with the larger variety of devices expected for thunderbolt, it may be more of a threat. In particular, the scenario put forward in the article: Connecting a laptop to a projector at a conference via display port. There is no telling if inside the projector a second device sits in line waiting to extract memory from the attached laptop.
As mentioned in the title: At this point, I don't think anybody has had a chance to experiment with this yet, and I am not aware of any display link projectors. Actually almost all of the time at conferences I find good old VGA (not DVI or HDMI). But this may of course change in the future.
[1] http://www.theregister.co.uk/2011/02/24/thunderbolt_mac_threat/
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
Windows 7 / 2008 R2 Service Pack 1 Problems
I will use this post to collect some of the problems we are hearing about with Windows 7 SP1 and Windows 2008 R2 SP1. Right now, there is no urgent reason to install this service pack and it should be tested first.
A few areas to watch:
- Whitelisting / Blocklisting: Whitelisting software may not have checksums yet to verify all the files that are modified by the service pack. Same for anti-virus: Some anti virus products monitor system files for changes and may sound an alert or block the installation of SP 1
- Firewalls: Third party firewalls may find that some of the low level hooks they use have changed.
- Disk Encryption: In particular full disk encryption that modifies the boot process may find that some of the changes it did are undone by the SP install
- Custom hardware: If you are using drivers other then those that are included in Windows 7 (or 2008 R2), be careful.
Specific examples. Consider them anecdotal but if you run any software mentioned here, or similar software, this list should give you a guide to test.
- Users with old versions of Microsoft Security Essentials may not be able to install SP1. Upgrade first.
- Samsung Galaxy S phone drivers may have problems with SP1
- some users reported very long install times (> 1hr. but not all that unusual for a service pack)
- Chrome 10 and 11 have issues according to some tweets
- Word 2003 VBA
- slower boot times with SP1 then without
- some reports of download issues due to overloaded servers
- Lenovo's Thinkvantage System Update may not work (update it before applying the SP)
- EVGA Precision Utility 2.0.2 (Graphics card stats program liked by gamers)
- MSI Afterburner
- some issues with Bitlocker are reported. But no confirmation at this point and it may also be due to entering the wrong password on reboot (you have to reboot a couple times in certain situations)
Link to a technet page with reports of install issues:
http://technet.microsoft.com/en-us/library/ff817622%28WS.10%29.aspx
If all fails, here a link with an uninstall procedure for SP1:
http://windows.microsoft.com/en-US/windows7/uninstall-sp1
To temporarily block installation of the service pack:
http://www.microsoft.com/downloads/en/details.aspx?FamilyID=d7c9a07a-5267-4bd6-87d0-e2a72099edb7&displaylang=en
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
28 Comments
Bind DOS vulnerability (CVE-2011-0414)
Internet Software Consortium published today an advisory for the BIND software. For versions 9.7.1-9.7.2-P3, when a server that is authoritative for a domain (i.e. owns the SOA record) process a successful domain transfer operation (IXFR) or a dynamic update, there is a small window of time where this processing combined with a high amount of queries can cause a deadlock, which makes the DNS server stop processing further requests.
Bind is one of the preferred targets for attackers on the Internet. If you have bind installed in your company, please remember the following basic security measures:
- Only allow IXFR transfers from known secondary servers of your domain. You don't want to let people know all the list of public ip address associated with your domain
- Keep separated your internal DNS information from your external DNS information. Some DNS provides information about private addresses used inside the corporate network.
- Allow recursive requests only from your internal DNS. If you allow recursive requests from the Internet, you are exposed to a distributed denial of service.
To solve the problem, upgrade to BIND 9.7.3. More information at http://www.isc.org/software/bind/advisories/cve-2011-0414
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
Windows 7 Service Pack 1 out
Microsoft made the first service pack for Windows 7 and 2008 R2 available for public download. This service pack is essentially a "roll up patch" including most security patches and hot fixes released so far.
Aside from patches, service packs typically include some improvements and new features. From a security point of view, RemoteFX may be of interest. RemoteFX extends RDP to allow a more "complete" remote desktop access including access to USB drives from example, more in line with virtual machine desktop clients that can use a local drive to load data on a remote virtual machine.
DirectAccess has been improved as well. DirectAccess requires the use of IPv6, and with SP 1, 6to4 as well as ISATAP are supported.
The RemoteFX and DirectAccess enhancements only affect Windows 2008 R2, not Windows 7.
Some twitter reports suggest that the service pack install may fail if bitlocker is used. If you experience any issues: Please let us know.
http://technet.microsoft.com/en-us/library/ff817622%28WS.10%29.aspx
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
4 Comments
ISC/DShield Website Update
We will be moving some servers to a new datacenter tomorrow (Wednesday Feb 23rd). As a result, you may not receive the daily summary e-mail for your DShield submissions tomorrow. We will work to keep the outage to the reports as brief as possible. The web site, and report submissions will not be affected.
Thanks.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
HBGary hack: lessons learned
Unless you’ve been living under a stone for last couple of weeks, you will have heard about the HBGary Federal hack. Seeing everything published about this probably makes every security professional think for at least a second, 'Could this happen to me too?'.
As most details about how the attack was carried have been published already (for example, see http://arstechnica.com/tech-policy/news/2011/02/anonymous-speaks-the-inside-story-of-the-hbgary-hack.ars) we can now look at all exploited vulnerabilities.
SQL injection on a public web site
I’m sure anyone who has done at least a little bit about security of web applications have heard about SQL injection. SQL injection vulnerabilities (or general injection vulnerabilities) are at the #1 place of OWASP top ten vulnerabilities for 2010.
A lot of web applications are vulnerable to SQL injection so one must be very careful when picking a web application for your web site. HBGary unfortunately had a vulnerable web application which allowed attackers to retrieve information directly from the back-end database – this information included MD5 hashes of passwords of users, that had access to the administration web interface.
I’ll get back to MD5 later, let’s focus on the web application for now. Successfully cracking one of the passwords would allow attackers to modify the web page (since it was a CMS). While this is bad (especially given it was a security company), it is still not as bad as what happened next.
According to the information that posted, the SQL injection in the application was really simple – I wouldn’t be surprised if the attackers used a powerful tool such as sqlmap, which should be able to exploit this.
Using same (weak) password for multiple applications
This turned out to be a major issue. After the attackers cracked the password, they (logically) tried it on all other applications/sites. Turns out that the same password was valid for e-mail & other applications, such as Twitter and Linkedin.
Since we all depend on e-mail for daily communication, it is obvious how the attackers took over the initiative at this point – they were able to read HBGary’s CEO’s e-mails and even send e-mail purporting to be him.
After carefully checking individuals that he was sending e-mails to, the attackers used social engineering to attack a system administrator of another system (rootkit.com) – an obvious weak spot since he/she holds “all the keys to the kingdom”.
It was this social engineering attack which impressed me the most (given the SQL injection was really simple) – the attackers sent a carefully crafted e-mail, asking the administrator to open SSH on a weird port and set the root password to something he knows (he allegedly being Greg Hoglund).
Could this happen in your company? I hope not – all of us - while doing various consulting gigs, such as ISO 27001 and similar, always stress, "that all changes must be approved and documented". However, when another person, or even a CEO asks an administrator to do something, ignoring all processes, would he/she that? Something to think about.
When the administrator opened SSH and changed the password, it was game over. The attackers had full access to the system and they downloaded e-mail backups and all other things we’ve been reading about over the last couple of weeks.
So what can we learn from this hack?
A lot of things that we already preach (or should be preaching):
- Do not use same passwords for multiple applications/sites. A lot of free, good utilities, such as Password Safe exist that will allow you to automatically generate strong passwords and store them in an encrypted key chain.
- No matter the size of your company, you should have change management processes that require all changes to be approved by appropriate personnel. While a CEO can request to open a port on the firewall, a security person in charge should approve any such request. If you don’t have multiple roles for this then make sure that appropriate authentication is in place – i.e. verifying such critical requests through other channels.
- You should regularly test your web applications – not only external, but also internal. While this does not guarantee that you will identify and eliminate all security vulnerabilities, it will certainly raise the overall security.
- Encrypt your backups and think twice if you need all those e-mails at one place. Gmail is certainly attractive for storing years of e-mails and searching through them quickly, but imagine what would happen if someone gets access to all your e-mail.
- While we’re on encryption – encrypt sensitive e-mails too - it may seem a nuisance, but it could save the day. PGP Encryption is not difficult to use, there are downsides, of course, so you should balance between usability and security.
- If you are a web-application developer, and have a need to store (hashed) user passwords remember that algorithms such as MD5 were built for speed! By using today’s GPUs, it is possible to crack hundreds of millions of MD5 passwords per second. Remember to use passwords salts to make rainbow tables useless (otherwise it’s usually a matter of seconds before a password is cracked).
Finally on storing hashed passwords, try to use multiple algorithms to store passwords – something like - sha1(sha1(sha1(password))) will be unnoticeable for the end user, but will make rainbow tables useless and increase the time needed to crack a password (and increase the likelihood an attacker will have to make a custom cracking module for their purpose).
And thanks to Sauj for fixing my grammar :)
Update: fixed some errors - I didn't try to go over what happened in every detail, I wanted us to think about "vulnerabilities" that have been exploited here.
--
Bojan
INFIGO IS
10 Comments
Kaspersky update servers unreachable
In a forum Kaspersky users discussed being unable to update their anti-virus product. The posting entitled 'Problem with the bases, Cannot update databases with 2011' is here: http://forum.kaspersky.com/index.php?showtopic=201405. It appears as though the issue has not yet been fully resolved. Thanks Bill for letting us know.
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
2 Comments
What’s New, it's Python 3.2
Python 3.2 has been released, with a plethora of newness. Check out the 'What’s New In Python 3.2' page: http://docs.python.org/dev/whatsnew/3.2.html or from their release announcement: "Python 3.2 is a continuation of the efforts to improve and stabilize the Python 3.x line. Since the final release of Python 2.7, the 2.x line will only receive bugfixes, and new features are developed for 3.x only." at http://www.python.org/download/releases/3.2/
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
0 Comments
Winamp forums compromised
Winamp have confirmed in a post to their own forums that email addresses used for the forums have been compromised. Users are recommended to change their passwords as a precautionary measure, and advised that the level of spam they receive may go up. Forum users may have also received an email from Winamp advising them of the compromise. The advisory is here: http://forums.winamp.com/showthread.php?t=327374. Thanks Evan for letting us know.
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
0 Comments
Snort Data Acquisition Library
With Snort 2.9 came the introduction of the Data Acquisition (DAQ) library to replace direct calls to PCAP functions."DAQ supports PCAP, AFPACKET, NFQ, IPQ, IPFW, and DUMP which is used for testing."[1]
After I upgraded from 2.8.6 to 2.9.0.2 (current version is 2.9.0.4), my Snort rules and in particular my Snort rule to detect Windows binary download (sid:15306) no longer detected Windows binary download via a browser. It was also affecting my Snort statistics that were constantly showing a small amount of packet loss.
In order to fix these various issues, I discovered after multiple tests that starting Snort in IDS mode with --daq afpacket and --daq-var buffer_size_mb=256 (default is 128MB and DAQ afpacket is recommended with an inline configuration) and my events were reporting correctly and the packet loss went away. If no options are specified, the default DAQ in Snort is PCAP DAQ and operates as it always did. Using the AFPACKET DAQ for me provided much better performance on various links (10 to more than 100 MB).
To find out which DAQ modules are already compiled in Snort, execute the following Snort command:
snort --daq-list
Available DAQ modules:
pcap(v3): readback live multi unpriv
ipq(v4): live inline multi
ipfw(v2): live inline multi unpriv
dump(v1): readback live inline multi unpriv
afpacket(v4): live inline multi unpriv
[1] http://vrt-blog.snort.org/2010/08/snort-29-essentials-daq.html
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
0 Comments
Windows 0-day SMB mrxsmb.dll vulnerability
A new vulnerability has been discovered exploiting SMB component of Windows. The attack involves sending of malformed Browser Election requests leading the heap overflow within the mrxsmb.dll driver. The vulnerability is known to be able to cause DoS and fully control of vulnerable machines. Proof of concept code for DoS had been released. There are reports that this exploit only work on local network segment (this hasn't been verified).
The general practice of block port 138, 139 and 445 should be observed especially with this 0-day.
More information on this exploit
http://www.vupen.com/english/advisories/2011/0394
9 Comments
HTTP headers fun
Not sure if you have seen our latest pet project - HTTP Headers. This is ISC's effort to track HTTP response headers by major sites on the Internet. Our main goal at this point is to monitor the use of security related headers. However, we are collecting all headers in part to monitor changes over time in the way administrators configure web servers.
Browsers have been somewhat ignored in the past when it came to web application defense. In part, because an application can't count on the user using any particular browser (or any browser for that matter). However, attacks on the other hand increasingly use the browser as an offensive tool to reflect attacks via cross site scripting, cross site request forging or click jacking. In all these attacks the browser is playing a major role.
The different attention to browsers is understandable. An attacker can be perfectly happy if an attack only works for a small percent of the population. If only users with Internet Explorer 6 on Windows XP are affected: Still a successful attack. For the defender on the other hand, the picture is different: If a particular browser protection is only enabled in 90% of browsers: One out of 10 visitors will still be affected by the attack.
This changes however if one is willing to accept browser defenses as an added defensive layer instead of a replacement for good application security. In addition, standards are emerging to make it easier for browser to provide meaningful protection. But none of this will work if it is not used.
We periodically reach out to the sites listed in the Alexa Top sites and track the HTTP headers returned by the web servers. We intend to track the changes over time and see how security related HTTP headers are used in real-world sites.
Some of the preliminary findings are as follows,
- Only very few sites use the X-FRAME-OPTIONS header. This is a reliable way to deal with Clickjacking attacks in newer browsers, but it will also block framing of web sites by friendly sites. The option allows for very little adjustment as it is currently implemented.
- X-XSS-Protection is used rarely by top sites (about 450 of the top sites). This is a IE 8+ supported header to enable/disable XSS protection feature on the browser. Only a few sites out of the hundreds turn off XSS protection by setting the value of this header to 0. Vast majority of the sites using this header enable the protect by setting value to 1 and mode=block, which makes the page blocked from the browser instead of browser sanitizing the content of the page.
- Set-Cookie2 is only used by two sites that we query. This is a largely ignored way of setting cookie, as specified in RFC 2965.
- X-Hacker caught our eyes. This is actually a job ad from the guys who developed Wordpress blogging software.
If you spot any interesting security related headers on our list and want to share with us. Please write in using the ISC contact form.
0 Comments
Oracle Java 6 Update 24
Oracle has released a new update for Java environment, it contains fixes for security issues. Time to get your Java environment up to date again.
The details on this update can be found at http://blogs.oracle.com/
Happy Java Patching!
1 Comments
Anonymous Damage Control Anybody?
One of our readers sent in this link:
hxxp://dazzlepod.com/rootkit/
It has a publicly disclosed list of accounts exposed from the attack on HBGary. As always follow the link at your own risk but it has been checked. It is regarding the site rootkit dot com. Their site seems to be unreachable at the moment but the article from Dazzlepod indicates that some passwords match Gmail and Twitter. 2 Factor Auth cannot come fast enough?
If you would like an offline copy email me at richard at isc dot sans dot edu
Richard Porter
--- ISC Handler on Duty
10 Comments
Network Visualization
One area of interest that I have is network visualization. What I'm referring to is being able to visually see the traffic flows and patterns to determine anomolies or events of interest. We have so much information with our networks today, that it is difficult to process all of it. The trend seems to be getting worse and reverting back to my good ole Army days of "Do more with less". With the economic times we live it, it always seems that security is one area that takes a hit. So, we have to work smarter and network visualization is one area that I think has great potential, but seems to be very under developed.
I haven't explored what's out there in a couple of years. What was out there that I experimented with it were tools such as:
- Time-based Network Traffic Visualizer (TNV)
- NVisionIP
- Spinning Cube of Potential Doom
- VisFlowConnect
- FlowTag
- InetVis
However, these tools had a long ways to go before they could really be effective on a large scale. Some were java based and SLOW (others were just slow) when processing any significant amount of data. However, what they did do, was pretty impressive for being able to visually make sense of a pcap file or your netflow data. They work great for looking at small chunks of traffic and helping immediately see anomolies. If this could just be channeled into a near real-time scenario for monitoring networks, that would be fantastic.
I did some quick google searches and didn't turn up any thing new in this arena. If anyone has any experience with network visualization or knows of any tools or work being done, please let us know.
17 Comments
DDoS Analysis Process
Introduction:
We sometimes get requests from people who are undergoing Denial of Service attacks. These days that usually means a Distributed Denial of Service attack. In our role at the Internet Storm Center, we're often limited to consultation roles and and can only recommend possible courses of action for the client. We don't have a canned response or top-three recommendations that will work in all cases; instead we have a process. Hopefully it can keep pace with the evolution of attacks.
Process Overview:
- Gather Information
- Get a list of attacking IPs from the client
- whois/geoip profiling
- description of the attack traffic
- SYN only
- complete session
- special request or execution
- pcaps are nice
- allow additional fingerprinting
- spoofed or not?
- Get a list of attacking IPs from the client
- attack analysis
- identify the weakness in the target
- identify the weakness in the attack
- formulate recommendations
- remiediate target weakness
- exploit attack weakness
An Example:
In the initial report we got a sample of source IPs and a description of the type of attack (e.g. SYN only.) Our initial response is to request a pcap sample of the attack. While that is underway we take look at the IP addresses from the first report. First there's a random sampling of IPs that we put through whois or geolocate to get an initial feel. In my random choice, it was Kazakhstan. A simple country code distribution of the full list had a heavy bias in Russia and the Ukraine.
Looking at the attack style, it was reported as SYNs-only. That kind of attack is easy to spoof, so I'm not so confident that the source IP addresses are accurate. I await the pcap.
Once it arrives we take a look at it in wireshark or other equivalent just to get a feel for the data. Just by eyeballing it we confirm that the SYN-only report was accurate. Next we begin a more in-depth analysis explore any theories that we may have. In my case, I'm interested in the validity of the source IPs. My approach is to build netflow data from the pcap and use that to filter out attackers from any legitimate customers that may have got through. I rely on argus to build the flow data and use a horrible combination of ra and awk to pull out the source IPs with flows that timed-out or had 0 bytes returned from the target. I can then feed that list of IPs into the geo-locator to get a distribution of the attackers. Another data-source is to passively fingerprint the attacking IPs and examine that distribution. I'm still using p0f for lack of a better alternative (although I did take Satori for a spin while writing this up.)
Is it uniform? Or does it have the feel of a exponential distribution? I admit that this process is far from rigorous (my apologies to all who have real statistics backgrounds.) The pcap itself is only a sample, so we're just looking to see if it's too random. In this case the distribution doesn't appear to be either uniform, nor clumped. So these IP addresses may be valid. Next we perform a similar plot of OS fingerprints.
Based on these observations we can get a feel if the source IPs are accurate or obviously-spoofed. In this case it still appears that these are legitimate IP addresses.
In addition to analyzing the source IPs, we give a similar treatment to the destination addresses. In this case, the stand-out is that it's only one IP that is targeted. This will play a factor in our recommendations below.
What does the attack look like? We've noted the SYN-only behavior, but are there other factors that could be leveraged? Things like TTL, and Byte-size? Perhaps the source port of the attacks has a pattern? In this case the source port had a uniformly random distribution. The estimated distance of the attackers ranged from 6 to 30 hops with most between 20 and 24 hops.
Now we have enough information to begin recommendations. Given that the attack is SYN-only, there are a number of SYN-flood defenses available at the server and the ISP-level. Additionally, if there is evidence that the attack is coordinated by IP address, we can exploit this weakness in the attack by moving the service over to a new IP and seeing how the attacker reacts.
Additional intelligence may be gained by paying extra attention to the outliers identified in the fingerprinting stage (for example the lone OpenBSD system or the handful of Linux systems.) These could be the systems that are monitoring the effect of the attack.
6 Comments
Two-Factor Auth: Can we just Google the response?
Google announced earlier that they are now offering two-factor authentication to all of their users. More information is available at the Google Blog. This is an extension to the service offered to their Apps customers last month. While normally I would think that “advertising” a service wouldn’t fit in this diary, this is a little more then the regular new feature. In mind opinion, it’s a big change in how people think about two-factor authentication.
We have known for years that passwords are one of the weakest points in our security controls. Users pick weak ones or share them with anyone who asks nicely. Even security consulting firms will fall for simple social engineering attacks and reveal them. One answer that has been proposed often, but is shot down almost as often. Clients often tell me that the cost is to high to roll out a solution, which I have always felt was the wrong answer. Of course, I am the paranoid security nerd. When this happens, I propose one of two solutions that try to help lower the cost.
The first is where the site or organization passes on the cost to the user. Blizzard does this for their Battle.net accounts. If the user feels that they should use two-factor authentication, they can either pay for a fob (the token generator) or install a smart-phone application. Of course I always laugh that my virtual gold in my World of Warcraft account is safer then my real “gold” in my bank account.
The second route is the one Google has chosen. When a user activates the system, their log on process has an extra step. After entering their password, they receive a phone call or an SMS that has the token. They enter this into the form and if it’s correct, they gain access to their account. This lowers the cost of deployment because it removes the needs for a fob to be sent to every user.
So the questions are pretty simple. First, how do you think two-factor authentication should be implemented and how do you deal with the cost? Second, alliance or horde? ;-)
Kevin Johnson
23 Comments
Befriending Windows Security Log Events
- Do you review or monitor them?
- How big are the log files?
- What happens when the log file are full?
- Do you know if security audit policies in place?
- Do you have different audit policies for certain systems?
- Are all your machines using the same time reference?
- Can you recognize the event ID that could mean trouble?
Chris Mohan --- ISC Handler on Duty
8 Comments
Linksys WAP610N has Unauthenticated Root Console issue
Passed to the Internet Storm Center from Jim.
Linksys wireless access point (WAP610N) has an unauthenticated root console issue
Taken from the actual advisory
*** SUMMARY ***
Linksys WAP610N is a SOHO wireless access point supporting 802.11n draft.
Unauthenticated remote textual administration console has been found that allow an attacker to run system command as root user.
Full details can be found here: http://www.securenetwork.it/ricerca/advisory/download/SN-2010-08.txt
This issue was also posted to the Full Disclosure mailing list http://seclists.org/fulldisclosure/2011/Feb/228
Chris Mohan --- ISC Handler on Duty
1 Comments
Java Floating point issue (CVE-2010-4476)
Oracle release a security bulletin yesterday relating to the binary floating point issue when converting 2.2250738585072012e-308" to a binary floating-point number. (http://www.oracle.com/technetwork/topics/security/alert-cve-2010-4476-305811.html)
The problem affects both JRE and JDK 6 update 23 and earlier. 4.0 Update 27 and earlier, as well as, yes people still use it, SDK & JRE 1.4.2_29.
Applications utilising these versions will be vulnerable to denial of service attacks. Servlet managers such as tomcat and others are likely affected as these often run older versions of java.
No patch available just yet.
- Mark -
2 Comments
Adobe Patches (shockwave, Flash, Reader & Coldfusion)
Just to add to the list of patches released: (thanks Frank, Ric, Jack):
- APSB11-01 Security update available for Shockwave Player
- APSB11-02 Security update available for Adobe Flash Player
- APSB11-03 Security updates available for Adobe Reader and Acrobat
- APSB11-04 Security update: Hotfix available for ColdFusion
Make sure you update these products as well please.
Mark
3 Comments
WordPress 3.0.5 (and 3.1 RC4) are out
The patching fun for the week continues with WordPress releasing an update.
This release is shown as a security release and contains a number of fixes for security issues. WordPress is one of the favourite targets, so all are encouraged to upgrade and get the benefits of the security fixes included (make sure you test before throwing it into production).
More information is here: http://wordpress.org/news/2011/02/wordpress-3-0-5/
M
0 Comments
Tippingpoint Releases Details on Unpatched Bugs
Tippingpoint, which operated the "Zero Day Initiative" bug bounty program released 22 vulnerabilities for which no patch is available [1]. Last year, Tippingpoint announced that they will release details 180 days after they are aware of a bug, even if the vendor has not yet released a patch.
The details released include a one paragraph description of the vulnerability, which in itself is usually not enough to come up with an exploit, but it may provide a pointer to re-discover the vulnerability.
[1] http://www.zerodayinitiative.com/advisories/published/
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
Snort 2.9.0.4 is coming out Thursday, ClamAV 0.97 update released
While this post may be a bit self-serving, as Snort is made by the company that I work for (Sourcefire. In the interest of full disclosure). Since Snort is rather large piece of security software, I thought I'd point to a blog post that I put up on the Snort.org blog about the release of Snort 2.9.0.4 that is being release this Thursday.
Check out the Snort 2.9.0.4 blog post here.
ClamAV was also updated this week to version 0.97, and since this a rather large piece of security software as well, I thought I'd point to the blog post that I wrote about ClamAV 0.97 update the other day.
Thanks all.
-- Joel Esler | http://blog.snort.org | http://blog.joelesler.net
0 Comments
Adobe Reader 9.4.2 and 10.0.1 Updates are out
Adobe released updates for Reader for 9.4.2 and 10.0.1. While this page on Adobe's site doesn't actually list them correctly, if you drill down into the actual product and OS, you'll see the updates listed for 2/8/2011.
Happy Patching.
-- Joel Esler | http://blog.snort.org | http://blog.joelesler.net
2 Comments
Feburary 2011 Microsoft Black Tuesday Summary
Here are the February 2011 Black Tuesday patches. Enjoy!
Overview of the February 2011 Microsoft Patches and their status.
| # | Affected | Contra Indications | Known Exploits | Microsoft rating | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS10-003 | Cumulative Security Update for Internet Explorer (Replaces MS10-090 ) | |||||
| Internet Explorer CVE-2010-3971 CVE-2011-0035 CVE-2011-0036 CVE-2011-0038 |
KB 2482017 | ACTIVELY EXPLOITED. | Severity:Critical Exploitability: 1,1,1 |
PATCH NOW! | Critical | |
| MS11-004 | Vulnerability in Internet Information Services (IIS) FTP Service Could Allow Remote Code Execution | |||||
| IIS CVE-2010-3972 |
KB 2489256 | POC Available. | Severity:Important Exploitability: 1 |
PATCH NOW! | Critical | |
| MS11-005 | DoS Vulnerability in Active Directory (Replaces MS10-068 MS10-101 ) | |||||
| Active Directory CVE-2011-0040 |
KB 2478953 | . | Severity:Important Exploitability: 3 |
Important | Important | |
| MS11-006 | Remote Code Execution Vulnerability in Windows Shell Graphics Processing (Replaces MS10-046 ) | |||||
| Windows Shell CVE-2010-3970 |
KB 2483185 | Exploit Available!. | Severity:Critical Exploitability: 1 |
PATCH NOW! | Critical | |
| MS11-007 | Remote Code Execution Vulnerability in the OpenType Compact Font Format (CFF) Driver (Replaces MS10-091 ) | |||||
| Open Type Compact Font Format Driver CVE-2011-0033 |
KB 2485376 | no exploit available. | Severity:Critical Exploitability: 1 |
Critical | Critical | |
| MS11-008 | Remote Code Execution Vulnerabilities in Microsoft Visio (Replaces MS10-028 MS10-036 ) | |||||
| Visio CVE-2011-0092 CVE-2011-0093 |
KB 2451879 | no exploit available. | Severity:Important Exploitability: 1,1 |
Critical | Important | |
| MS11-009 | Information Disclosure Vulnerability in JScript and VBScript Scripting Engines (Replaces MS10-022 ) | |||||
| VBScript/JScript CVE-2011-0031 |
KB 2475792 | no exploit available. | Severity:Important Exploitability: 3 |
Important | Important | |
| MS11-010 | Privilege Elevation Vulnerability in Windows Client/Server Run-time Subsystem (Replaces MS10-011 ) | |||||
| Client/Server Runtime CVE-2011-0030 |
KB 2476687 | no exploit available. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS11-011 | Privilege Elevation Vulnerabilities in Windows Kernel (Replaces MS10-021 MS10-047 ) | |||||
| Windows Kernel CVE-2010-4398 CVE-2011-0045 |
KB 2393802 | no exploit available. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS11-012 | Privilege Elevation Vulnerabilities in Windows Kernel-Mode Drivers (Replaces MS10-098 ) | |||||
| Windows Kernel-Mode Drivers CVE-2011-0086 CVE2011-0087 CVE2011-0088 CVE2011-0089 CVE-2011-0090 |
KB 2479628 | no exploit available. | Severity:Important Exploitability: 1,1,1,1,1 |
Important | Important | |
| MS11-013 | Privilege Elevation Vulnerabilities in Kerberos (Replaces MS10-014 ) | |||||
| Kerberos CVE-2011-0043 CVE-2011-0091 |
KB 2496930 | Publically Disclosed. | Severity:Important Exploitability: 1,1 |
Important | Important | |
| MS11-014 | Privilege Elevation Vulnerability in Local Security Authority Subsystem Service (Replaces MS08-002 ) | |||||
| LSASS 2011-0039 |
KB 2478960 | . | Severity:Important Exploitability: 1 |
Important | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them
-- Joel Esler | http://blog.snort.org | http://blog.joelesler.net
16 Comments
VMWare Security Advisory
Cisco Nexus 1000V VEM updates address denial of service in VMware ESX/ESXi
VMWare released a Security Advisory at this URL:
http://www.vmware.com/security/advisories/VMSA-2011-0002.html
Here's the issue summary right off their website:
1. Summary
Updated versions of the Cisco Nexus 1000V virtual switch address a denial
of service in VMware ESX/ESXi.
The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CVE-2011-0355 to this issue.
Thanks to VMWare for this one.
Chris Mohan
0 Comments
Crime is still Crime! Pt 2
There is an interesting piece running on several web news outlets and twitter is abuzz with HBGary Federal being hacked by Anonymous. HBGary was in the news less than 3 days ago stating they were tracking down members of Anonymous and aiding the FBI.
Last month we ran a piece Crime is still Crime and were assessing the risks of non-security firms "attacking back."
http://www.isc.sans.org/diary.html?storyid=10300
With today's events and HBGary having an incident it re-enforces the advice for of assess your risk and posture before attacking back. Esspecially for those that are not in the Information Security field. If your revenue driver is making baby bottles then ask yourself is this the right move and do I have the skill set on staff.
Less than 3 days ago:
http://uk.finance.yahoo.com/news/Cyberactivists-warned-arrest-ftimes-3487898538.html?x=0
Today:
http://nakedsecurity.sophos.com/2011/02/07/hbgary-federal-hacked-and-exposed-by-anonymous/
I have been following these events (And will continue to follow) from the start as they cross government lines and this could set legal precedent for the future. Let's stay tuned as this takes shape.
And remember a paraphrase/quote from Cliff Stoll's The Cuckoo's Egg "Professionals don't make big mistakes, they make little ones!"
Richard Porter
--- ISC Handler on Duty
3 Comments
The Good , the Bad and the Unknown Online Scanners
1 Comments
OpenSSH Legacy Certificate Information Disclosure Vulnerability
If generating a legacy certificate using the "-t" option, a vulnerability could be exploited by attackers to gain knowledge of sensitive information. If legacy certificates have been issued using OpenSSH version 5.6/5.7, consider rotating any CA key used. OpenSSH recommend upgrading to version 5.8 available here or apply this patch.
[1] http://www.openssh.com/txt/legacy-cert.adv
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
0 Comments
Busy patch tuesday ahead
Come Tuesday, Adobe is apparently planning to issue critical updates for Adobe Reader. Microsoft's advance notification indicates that we'll be getting a plethora of patches, most prominently a critical one ("remote code execution") for Internet Explorer. Further, Firefox 3.6.14 is also tentatively scheduled for a release on same Tuesday. Looks like we're in for a busy patch week.
0 Comments
Oh, just click "yes"
Java and Java Applets are featuring prominently on my "annoyances list" this year. There are vulnerabilities aplenty, and incompatibilities keep many a firm or university from applying the patches. We've covered these to some extent.
The latest incarnation of annoyance though is commercial software applets that are signed with an expired certificate. Dear vendors, if your "release" is supported until 2013, it is a bad idea to sign the code of said release with a cert that expires in December 2010. And it is an even worse idea to suggest to clients who open a ticket that they should just tell their users to "click yes" on the certificate warning until a patch can be provided.
The Original Sin of certificate handling in Java and Web Browsers alike?
The "oh, connect anyway" button.
I sure wish it simply weren't there.
5 Comments
Egyptian networks are being announced on BGP
Egyptian networks are now being announced on BGP which has lead to a number of Egyptian web sites being available again.
Reported at the web site BGPmon[1], over 2800 BGP announcements for Egyptian networks have returned.
Whether full internet services to and from Egypt will return and stay accessable remains to be seen over the coming days and weeks.
[1] http://www.bgpmon.com/blog/?p=480
Chris Mohan --- ISC Handler on Duty
1 Comments
Default Credentials for Root Account on Cisco Personal Video units
Tandberg C Series Endpoints and E/EX Personal Video units that are running software versions prior to TC4.0.0 ship with a root administrator account that is enabled by default with no password.
Cisco advise that all customers set the password on these devices to secure them.
Cisco advisory is posted at http://www.cisco.com/warp/public/707/cisco-sa-20110202-tandberg.shtml.
Chris Mohan --- ISC Handler on Duty
0 Comments
Having Phish on Friday
We have gotten reports of a phish group which may reside in Indonesia compromising large numbers of web servers. There isn't a lot of detail so far. One interesting facet is that the phish usually goes "live" on a Friday, probably in an attempt to maximize response time.
Each compromised site typically hosts phishing pages for multiple banks.
Many of the sites appear to have outdated versions of OS Commerce installed which is a likely source of the compromise.
If you have any logs willing to share: Please send them in via our contact form. We are trying to determine the exact entry vector (is it OS Commerce or something else?), maybe any tools used to achieve the compromise and anything else left behind besides the phishing pages.
https://isc.sans.edu/contact.html
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
1 Comments
The End Of IP As We Know It
Today, IANA announced that it had handed out two more /8 IPv4 assignments to APNIC. As a result, IANA is down to 5 /8s, triggering its special policy to hand out one address to each regional registrar (RIR). The 5 RIRs are AFRNIC (Africa), APNIC (Asia Pacific), ARIN (North America), LACNIC (Latin America) and RIPE (Europe). [1]
IANA hands IP address space to the RIRs in chunks of /8s, who then pass it on to ISPs, who then pass it on to end users. Some large end users may approach their RIR directly, and some "legacy assignments" are managed by IANA directly.
But in the end, what does this all mean?
A Quick FAQ To IPv4 Exhaustion
1 - Will the Internet stop working?
No. As a matter of fact, it is unlikely that the IPv4 internet will stop any time soon. It will likely happily exist next to the IPv6 internet. There are some transition mechanisms set up. While not pretty, the two "internets" can talk to each other via proxies and tunnels.
2 - Why do we run out of addresses?
IPv4 allows for about 4 billion addresses. There are about 6 billion people on the world... how many addresses do you need (phone, home, work...)? Its a simple math issue compounded by the fact that for efficient routing sake, we can't assign all addresses.
3 - A lot of IPv4 space is still unused. Why don't we use it more effectively?
The problem is not just that we are running out of addresses, even though that is the killer issue here. Assigning addresses more effectively would mean that assignments would become smaller and routing tables would become more complex. In order to make this work, we would have to essentially "renumber" the internet, and still be out of addresses at some point.
4 - What about legacy space? Does Apple really need a /8?
In the beginning of the Internet, IPv4 address space was handed out very liberally. Remember it was just an experiment? Some of the original participants still have large IPv4 assignments which they don't use efficiently. However, even if all of them are handed back, it would delay the problem only by 1-2 years at great expense to the effected companies (and they have contracts giving them the rights to use the address space). Some "legacy allocations" have been returned in the past
5 - What do I need to do today?
Relax. Nothing is going to happen fast. the RIRs still have space left, depending on the region a few month to a year. After that, it will get tricky. You may already find it harder to get IP address space. Eventually, your ISP may ask for some space back as they can't get new addresses from the RIR. Over time, IPv4 will get more expensive than IPv6.
6 - So I can just wait and do nothing?
No. What you should do tomorrow (maybe today?) is setup a test lab to familiarize yourself with IPv6. It is easy to get going. Ask your ISP if they support it (or when), or setup a tunnel with a free tunnel provider like Hurricane Electric [2] or Sixxs [3] (there are others). You need a plan on how to deal with it. Even if you don't need IPv6, maybe your business partners start using it and you need to connect to them via IPv6.
7 - Can't I just ignore it?
Remember why you are using IP in the first place? It allows you to connect to customers, suppliers, branch offices. In short: It keeps you in business. Once these people expect IPv6 connectivity, you will likely have to move along with it. It is like any technology in that it ultimately has to support the business (and well... it is fun too!).
8 - What will change from a security point of view?
Everything and nothing. The most important change is probably the fact that NAT will become less important. Endpoint protection and carefully configured firewalls will become more important. Passive asset detection will become more important compared to active scanning. There is a lot of security gear you own that probably does a lousy job dealing with IPv6. Did I mention it requires a plan and testing?
[1] http://www.iana.org/assignments/ipv4-address-space/ipv4-address-space.xml
[2] http://www.tunnelbroker.net
[3] http://www.sixxs.net
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
11 Comments
How Not to Respond to a Security Incident
Finding out that your organization's computer defenses has been breached is a stressful experience. Many are unprepared to deal with such situations, and some have a false sense of security as the result of impractical incident response plans.
Having read about the recent PlentyofFish.com security incident, as described by its founder and a more measured perspective from Brian Krebs, I was inspired to create this short list of what not to do when responding to a security incident:
- Don't drive the incident response (IR) team to work for several days without sleep. People's ability to conduct cognitive tasks is severely diminished when they are sleep-deprived. You may need to pull a one-nighter initially, but after that, stagger people's response tasks so they can get some rest.
- Don't make rush decisions when deciding upon the initial incident response steps. It is OK to take some time to assess the situation before taking action to avoid making mistakes. Of course, you need to balance this with waiting too long before making decisions regarding the next steps.
- Don't immediately attribute the source of the breach to people, companies or countries without conducting a thorough investigation. In particular, don't assume that the entity who notified you of the breach of a vulnerable condition is the entity responsible for the incident.
- Don't attempt to hire the entity who notified you of the breach to assist with incident response, unless there's truly no one else qualified for the job. They might not be responsible for the breach, but it's best to control the situation where you might accuse them of extortion. Also, there's no reason to encourage ambulance-chasing practices.
For more recommendations on what not to do when someone reports an incident, as well as for tips on what to avoid doing when reporting an incident, see our earlier diary Incident Reporting - Liston's "How-To" Guide.
In addition, here are a few Emergency Incident Response steps from Mandiant, which are a good starting point for responding to a security incident. I also put together a few incident response cheat sheets:
- Initial Security Incident Questionnaire for Responders
- Network DDoS Incident Response Cheat Sheet
- Security Incident Survey Cheat Sheet for Server Administrators
- Critical Log Review Checklist for Security Incidents
-- Lenny Zeltser
Lenny Zeltser leads a security consulting team and teaches how to analyze and combat malware. He is active on Twitter and recently launched a security blog.
3 Comments
The Importance of HTTP Headers When Investigating Malicious Sites
Incident responders sometimes need to investigate the nature of a website reported as being malicious. They do this by connecting to the remote site, while taking care not to infect themselves, perhaps by using a laboratory machine that isn't connected to the production network. They also take care to conceal their origin, perhaps by connecting using a non-corporate DSL line or by using an anonymizing proxy, such as Tor. There are a few other connection elements they need to account for.
When connecting to malicious websites to investigate them, take care to set your User-Agent and Referer headers according to the attacker's expectations.
The Referer Field of the HTTP Header
For instance, Websense documented a recent Kookface variant whose website looked at the Referer field of the HTTP request. If the victim visited the malicious website directly by typing the URL into the browser, the website would redirect to an apparently benign page that looked like Google news search results.
HTTP request headers when visiting the malicious page directly, without a referrer:
GET http://url-redacted HTTP/1.1
Accept-Language: en-us
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1)
Proxy-Connection: Keep-Alive
Host: hostname-redacted.com
Benign response from the website looked like this when rendered by the browser:
.png)
In contrast, when the victim clicked on a link embedded in some page, the "Referrer" field was set:
GET http://url-redacted HTTP/1.1
Referer: http://example.com
Accept-Language: en-us
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1)
Proxy-Connection: Keep-Alive
Host: hostname-redacted.com
As the result, the website redirected the visitor to another page. This one attempted to social-engineer the person into downloading and installing malware under the guise of a Flash player update:
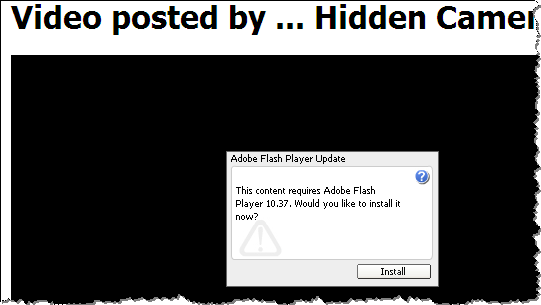
This particular site didn't seem to care about the specific contents of the Referer field, as long as it was set. However, many websites will only attempt to attack the visitor if the Referer field is set to a particular value, such as the one corresponding to Google. This is a defensive strategy to make it harder for security analysts to investigate the
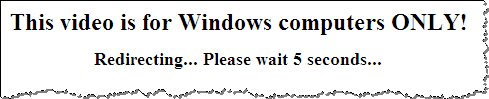
The User-Agent Field of the HTTP Header
The Koobface website above also paid attention to the User-Agent field of the HTTP header, attacking only visitors coming from the Windows platform. For instance, this request made the site think the person is connecting from a Linux platform:
GET http://url-redacted HTTP/1.1
Referer: http://example.com
Accept-Language: en-us
User-Agent: Mozilla/5.0 (X11; U; Linux i686; en-US) Gecko Ubuntu/9.10 (karmic) Firefox/3.5.1
Proxy-Connection: Keep-Alive
Host: hostname-redacted.com
The website responded by displaying the following message before redirecting to a non-malicious website http://rolly.com.
Tools for Controlling HTTP Headers
When investigating malicious websites using Firefox, you can control your Referer header by using the RefControl add-on. You can control your User-Agent header using the User Agent Switcher add-on.
Another option is to use command-line page retrieval tools, such as wget and curl. We discussed ways of controlling the headers sent by these tools in an earlier diary.
For more control over your browser's interactions with the malicious website, consider proxying your lab's browser through a local proxy tool, such as Paros Proxy, Fiddler, WebScarab, etc.
-- Lenny Zeltser
Lenny Zeltser leads a security consulting team and teaches how to analyze and combat malware. He is active on Twitter and recently launched a security blog.
0 Comments



6 Comments