Uberscammers
E-mail scams, phishing and social engineering is something that we (security people) became really used to. Even from the penetration testing engagements I do, when we utilize social engineering, it’s almost always extremely successful showing that, unfortunately, people still do not pay enough attention to validity of e-mails they received.
That being said, sometimes we do encounter really good (or bad for us defenders :/) phishing attempts. Couple of weeks ago, one of our readers, Matthew Henry sent in an example of a scam against Uber users (and we know that those count in millions).
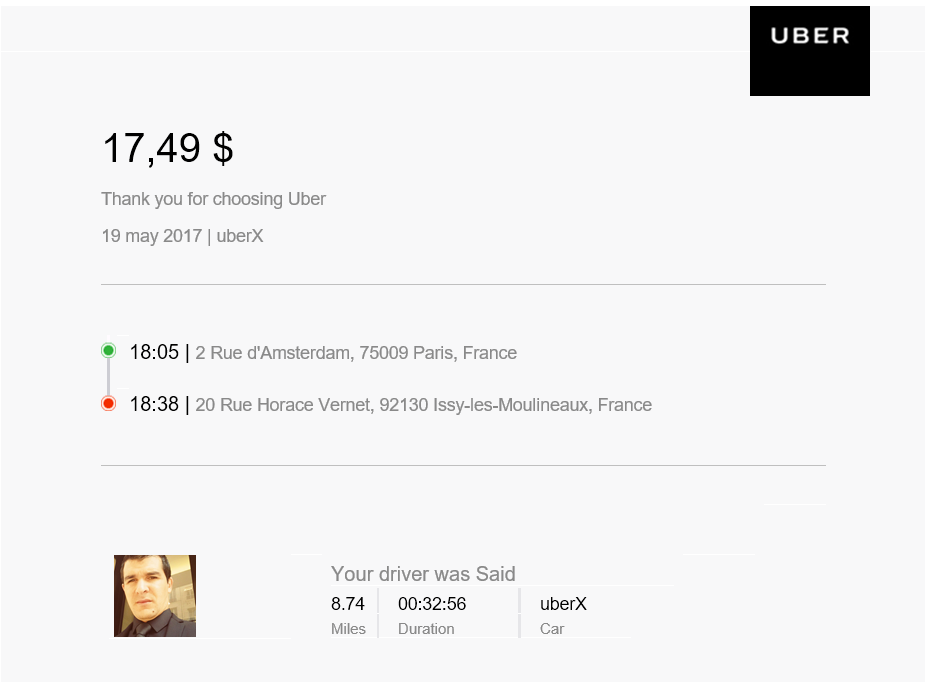
The e-mail appeared as a typical Uber receipt where it looked as the recipient was charged for a ride in France. The e-mail is shown below:
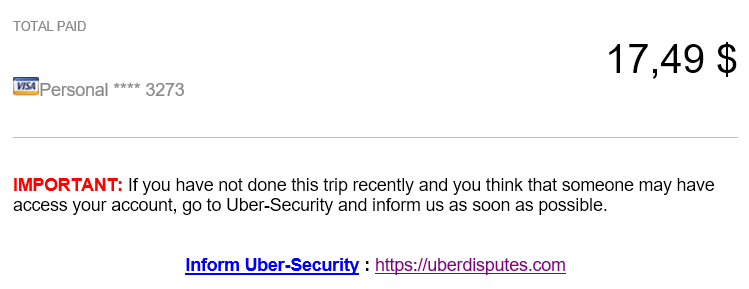
The bait was at the bottom, and you can see it here:
Of course, none of the users that receive this e-mail would have taken this trip so the phisher in this case is trying to get people to click on the link to dispute the received receipt.
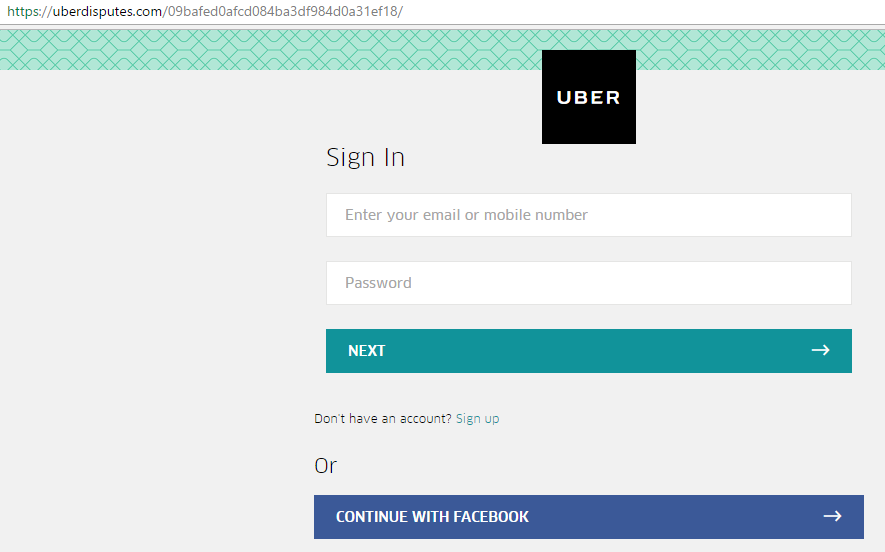
See the domain? uberdisputes.com is not an Uber’s domain. At the time of the phishing e-mail circulating around, the domain was only a day old. If you visited the link shown above while it was still up, you would be asked to log in:
After logging in, in order to dispute the receipt, the site would ask for the credit card number, of course, so the victim can be reimbursed. You can probably guess what happened with the credit card after submission …
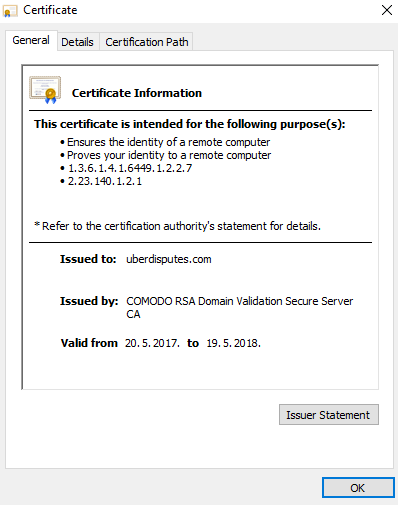
While all this is nothing particularly amazing, what I do find unbelievable is how easy it is for the bad guys to get certificates for such web sites. Although there has been a lot of discussion about how Let’s Encrypt can be used now for all sorts of certificates, in this example we can see that another CA, this time COMODO, happily issued a certificate for domain uberdisputes.com:
(Small rage: I wonder who was the GENIUS in Google that decided to remove SSL/TLS certificate information from the lock icon in Google Chrome. Yeah, it was a great idea to make users open Developer Tools to see it grrrr).
Such cases are very common and always make me wonder why both CA’s and big companies do not do the following:
- For CA’s, they should have a list of critical keywords of big players that are commonly used in attacks. For example, I would not let automatic systems issue a certificate for a domain such as microsoft-software.com (it belongs to Microsoft luckily),
- For big(ger) companies, I would try to register/buy most domains that are similar to the company’s name, and especially those that can be potentially used for phishing.


Comments