50 years of malware? Not really. 50 years of computer worms? That's a different story...
If you have any interest in the history of malicious code, chances are you’ve heard or read somewhere that the first piece of malware ever created was a computer worm called Creeper and that spread itself through the ARPANET in 1971. Some sources even mention that it might have been on this very date, i.e. exactly 50 years ago[1].
So does malware really turn 50 today?
Not likely. Even leaving aside that according to some sources[2], there may have been a fork bomb[3] program created all the way back in 1969, and therefore the oldest malware might already be over 50 years old, the simple fact is that Creeper wasn’t malware in any sense of the word... Alhough it was probably the first example of a (benign) computer worm ever created.
In the multiple retellings of its legend that may be found both online and in print, we have, however, a prime example of something which is unfortunately relatively common (not just) in infosec. That is repeating of interesting-looking information without checking for any original sources, which might provide context to it. I don’t mind admitting that this is a pet peeve of mine[4] and so I thought that on this day, which may or may not mark the 50th anniversary of the original “run” of Creeper, it might be a good idea to take a look at what we really know about it.
According to the few trustworthy articles on the subject, which cite their sources[5,6], and explanations provided by Ray Tomlinson, who played a significant part in the story of Creeper[7,8], the program was created at BBN technologies at some point in 1971. At that time, BBN was developing the TENEX an operating system for the PDP-10 computer. One of the developers of TENEX was Robert Thomas, who, among other projects, worked on what was called a Resource Sharing Executive, or RSEXEC – an experiment with what was thought of as a “mobile application” concept. RSEXEC was basically supposed to enable a program to “jump” between computers in order for it to always be executed by a machine with unutilized computational resources or with data, which the program needed. As you’ve probably guessed, Creeper was the demonstration program, which resulted from Thomas’s work.
The original application was tested using (at most) 28 computers connected to the ARPANET and running the TENEX OS. Creeper migrated from one system to another, always "removing" itself from the machine, when it was leaving it. What is important to note is that this was done with full agreement and cooperation of operators of all those computers and that the test had no negative effects on them.
All that the Creeper supposedly did on “visited” computers was printing the famous message “I’M THE CREEPER : CATCH ME IF YOU CAN” on a teletype.
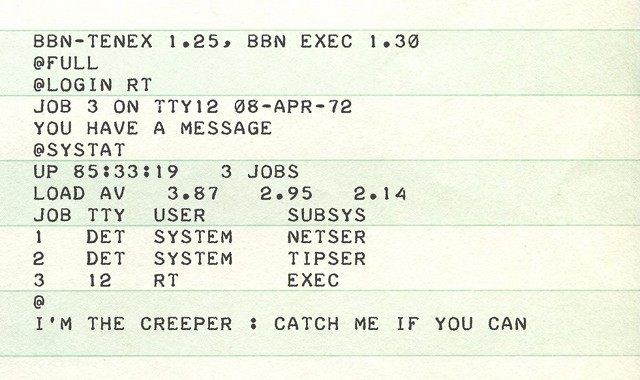
Message printed by Creeper[5]
An indeterminate amount of time later, Ray Tomlinson, who worked at BBN Technologies at the same time as Bob Thomas, created a modified version Creeper. The program originally jumped from one machine to another, which meant that there was always only one copy of it on the entire network (computer worms which behave in this way are sometimes called “rabbits”). The new version, which was created by Tomlinson, had the ability to replicate itself, i.e. create multiple copies of itself, which might exist at the same time on different machines (meaning it behaved more like a usual computer worm). This updated version was - once again - not malicious in any way and one may think of it as a demonstration of the concept of distributed computation more than anything else.
Since it was able to replicate itself and it was necessary to make sure it didn’t cause any problems even in case of bugs which might make it hang, Tomlinson also created a program called Reaper. This was a simple piece of code, which visited each of the approximately 28 computers, which might have hosted Creeper, and terminated any instances of Creeper it found running on them.
Due to this behavior, Reaper is sometimes called “the first anti-virus”[9]. Since neither version of Creeper was malicious in any way, depending on your definition of "anti-virus" this title may or may not be applicable. Reaper however almost certainly may be called the first “nematode” (a worm or virus, which removes another worm or virus from a system, on which it is present).
So, based on the history ve'we recounted, what may we say with any sort of certainty regarding the age of malware? Not much. In terms of the age of computer worms, however, chances are good that they really are really turning 50 this year, whether it is today or not. It is a little bit sad that one tends to think of every computer worm as being malicious “by default”, since, as this little trip down the memory lane shows us, it doesn’t necessarily have to be true...
In any case, if you’d like to learn a bit more about the origins of modern malware (and don’t mind low-quality video editing), the following video might be worth your time.
[1] https://www.cybersecurity-insiders.com/a-brief-history-of-cybersecurity/
[2] http://catb.org/~esr/jargon/html/W/wabbit.html
[3] https://en.wikipedia.org/wiki/Fork_bomb
[4] https://untrustednetwork.net/en/2019/10/19/do-automated-tools-really-detect-only-45-of-all-vulnerabilities/
[5] https://corewar.co.uk/creeper.htm
[6] http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.137.9511&rep=rep1&type=pdf
[7] https://history-computer.com/the-first-computer-virus-of-bob-thomas-complete-history/
[8] https://nerdology.org/2014/11/qa-with-ray-tomlinson-on-creeper/
[9] https://en.wikipedia.org/wiki/Reaper_(program)


Comments