Domain Name Used as Password Captured by DShield Sensor
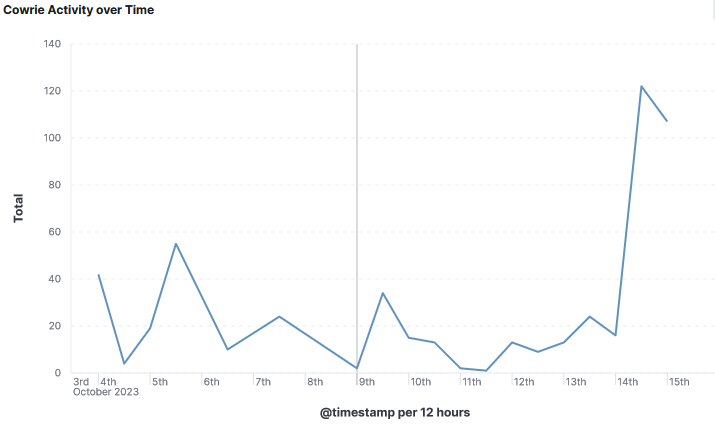
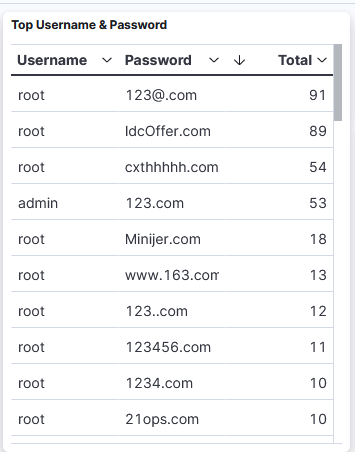
While reviewing my DShield honeypot logs, I noticed for the first time something strange in my list of Top Username & Password where several domain name were use as password. Initially, I was under the impression this might be a parsing error by Logstash and decided to review the raw logs to make sure it was parsed correctly to confirm data integrity. Since username and passwords isn't something submitted to DShield, I reviewed my own raw logs to confirm the data was accurate and reviewed the capture rate of username/password combination for the past few weeks:
2023-10-15T00:06:32.836953Z [HoneyPotSSHTransport,491,43.134.105.200] login return, expect: [b'root'/b'123@.com']
2023-10-15T00:11:39.103160Z [HoneyPotSSHTransport,594,43.134.105.200] login return, expect: [b'root'/b'123@.com']
2023-10-15T00:13:08.464557Z [HoneyPotSSHTransport,664,43.134.105.200] login return, expect: [b'root'/b'123@.com']
The logs also showed that only two usernames were used for this activity: root & admin.
I tried resolving some of the domain, some resolve and some don't. Here are a few examples of domain name (password) that resolve:
- cxthhhhh.com → Addresses: 2606:4700:3033::ac43:9280, 2606:4700:3031::6815:2f65, 172.67.146.128, 104.21.47.101
- minijer.com → Address: 106.52.55.138
- 123456.com → Addresses: 3.33.130.190, 15.197.148.33
Top 10 IPs Indicator
62.3.42.85
185.116.194.231
138.197.102.26
221.133.12.6
180.101.88.239
180.101.88.240
51.68.121.67
43.153.108.66
52.140.61.101
122.114.155.20
Have you seen similar activity in your logs? Let us know via our contact page.
[1] https://isc.sans.edu/ipinfo.html?ip=43.134.105.200
[2] https://isc.sans.edu/diary/Install+Configure+Filebeat+on+Raspberry+Pi+ARM64+to+Parse+DShield+Sensor+Logs/30056
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu



Comments
dec0der
Oct 18th 2023
1 year ago