Generating PCAP Files from YAML
The PCAP[1] file format is everywhere. Many applications generate PCAP files based on information collected on the network. Then, they can be used as evidence, as another data source for investigations and much more. There exist plenty of tools[2] to work with PCAP files. Common operations are to anonymize captured traffic and replay it against another tool for testing purposes (demos, lab, PoC).
When you anonymize PCAP files, the goal is to replace IP addresses by other ones (The classic operation is to replace the first byte with a ’10’ value to make the IP address non-routable). However, the payload may contain sensitive data that are more difficult to sanitize. Last week, I attended the hack.lu[3] conference in Luxembourg and, during the lightning talks session, an interesting tool was demonstrated: pCraft. It can be described as a “PCAP file generator from a scenario described in YAML[4]”. The idea behind this tool is to create a scenario of network actions that will be translated into a fully-working PCAP file.
Here is a quick example to demonstrate how to test an IDS rule:
start: GenerateNewDomain
GenerateNewDomain:
_plugin: GenerateNewDomain
_next: DNSConnection
DNSConnection:
_plugin: DNSConnection
sleep: {"once-finished": 1}
_next: HTTPConnection
HTTPConnection:
_plugin: HTTPConnection
method: GET
uri: "/shell?busybox"
user-agent: "Mozilla/5.0"
_next: done
The script is easy to understand: We generate a random domain name, we resolve it then we generate an HTTP request to the servers with a suspicious URI.
Let's generate the PCAP file:
# ./pcraft.py test.yaml test.pcap ['PCraft/plugins/HTTPConnection.py', 'PCraft/plugins/DNSConnection.py', 'PCraft/plugins/TcpRst.py', 'PCraft/plugins/HTTPPostConnection.py', 'PCraft/plugins/PcapImport.py', 'PCraft/plugins/Ping.py', 'PCraft/plugins/GenerateNewDomain.py', 'PCraft/plugins/Cheat.py', 'PCraft/plugins/SMTPReceive.py'] All plugins loaded! Opening Script File test.yaml [2019-10-28 18:01:35.324952] Executing: Generate_a_new_domain [2019-10-28 18:01:35.367461] Executing: DNSConnection [2019-10-28 18:01:35.368882] Executing: HTTPConnection [2019-10-28 18:01:36.984010] Executing: done
The PCAP file can now be used to test our IDS or any other application.
Let's open it in a Wireshark and inspect the HTTP request:
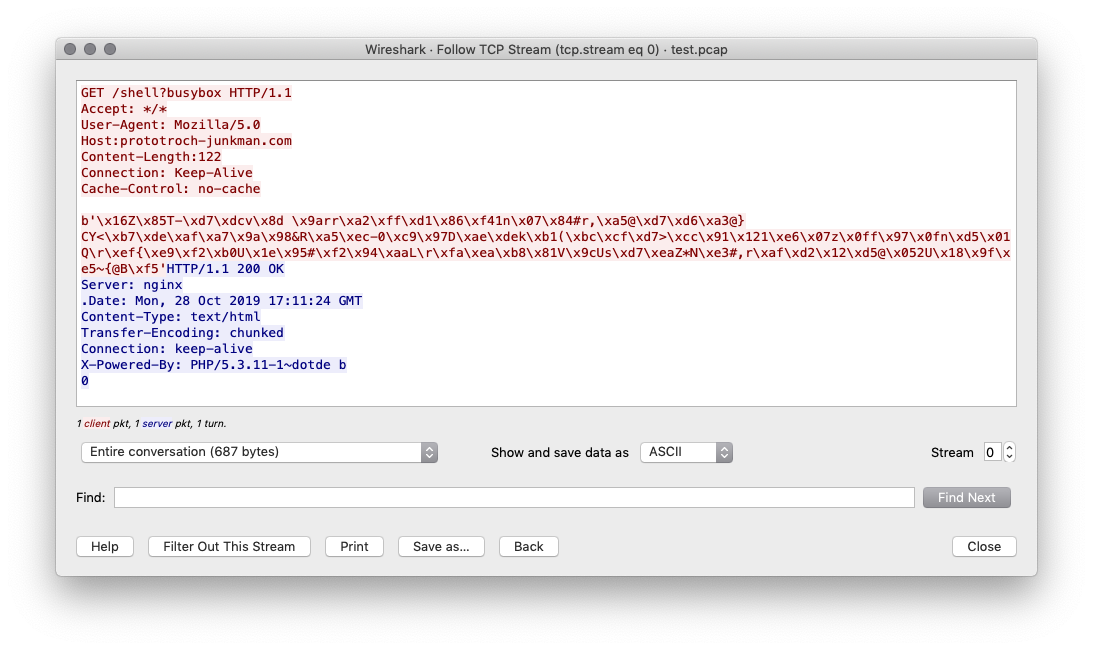
pCraft is written in Python and, if you check the required modules, you see it relies on scapy[5] to generate packets and the PCAP file. Not many types of traffic are supported at the moment but, being based in plugins, it's easy to expand it. The current list of plugins is:
- DNSConnection
- GenerateNewDomain
- HTTPConnection
- HTTPPostConnection
- PCAPImport
- Ping
- TcpRst
pCraft has been developed by Sébastien Tricaud and is available on github[6]. Great tool!
[1] https://wiki.wireshark.org/Development/LibpcapFileFormat
[2] https://n0where.net/best-pcap-tools
[3] https://2019.hack.lu/
[4] https://en.wikipedia.org/wiki/YAML
[5] https://scapy.net/
[6] https://github.com/DevoInc/pCraft
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | British Summer Time | Jul 28th - Aug 1st 2025 |



Comments