Analyzing an HTA file: Update
A reader asked what the &H?? strings were in the malware I analyzed in my last diary entry. These are numbers in VBA written in hexadecimal.
For analysis, these numbers can be easily extracted with my re-search.py tool and then converted to binary with hex-to-bin.py.
With regular expression "&H..", we can extract all strings starting with &H followed by 2 characters:
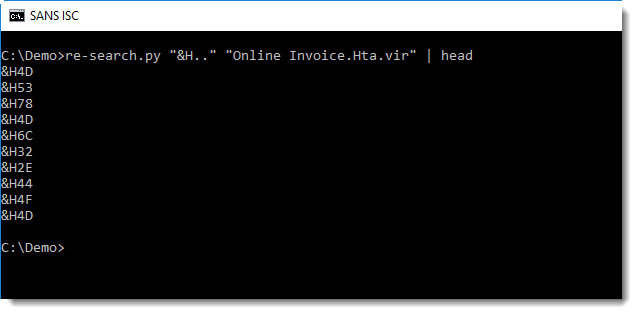
When we use a capture group (), re-search will output the capture group in stead of the full matched string:
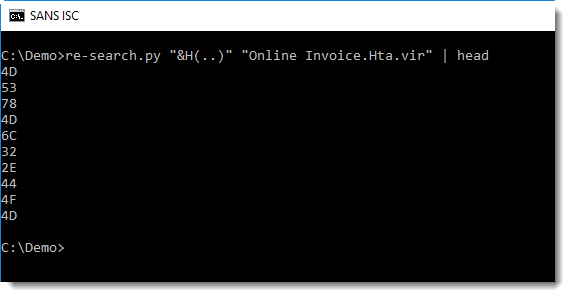
And then we can convert the hexadecimal digits to their binary values:
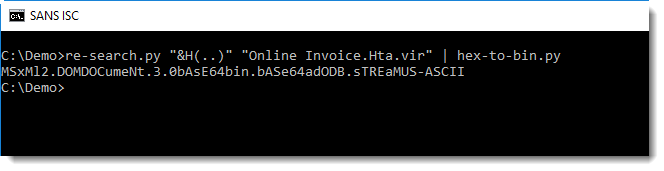
In this HTA document, the malware authors tried to obfuscated strings like MSXML2.DOMDocument.3.0 that are used in AV signatures and other detection tools.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com



Comments