Analyzing (malicious) SWF file actions
Couple of days ago, Steve P. reported a web page that, when viewed, somehow redirected his browser to another, phishing web site. I initially thought that the original web page just used simple redirection (with or without help from JavaScript), but after analyzing the original site I found out that phishers used something different.
(I’ll use this opportunity to ask developers of legitimate web sites to try to make their code a bit more readable – stripping all spaces and tabs from your code and using cryptic names for variables doesn’t help analysts at all)
So, the web site that had the redirection had the following HTML code embedded:
…
<P><embed src="http://mauke.globat.com/~traderonline-ltd.com/images/a8/cocino.swf"
height="4" width="3"></P>
As you can see above, the web site (which is still live, but the target phishing site has been removed) is actually pulling an SWF (Macromedia Adobe Flash) file. In other words, the redirection was caused by the malicious SWF file, which also means that this will work only if you have Flash installed. While this was obvious, I got interested into how to analyze actions embedded in SWF files so I found two nice (and free!) utilities that you might want to bookmark, in case you need to do the same thing in the future.
SWFTools
The first utility is actually a collection called SWFTools (http://www.swftools.org/). This utility is for all you guys that prefer to analyze malware under Linux. The collection consists of various command line utilities for various manipulations of SWF files. The most useful one for our analysis is called swfdump. This small utility can disassemble action tags in SWF files and that’s exactly what we need in this case:
$ swfdump -a cocino.swf
[HEADER] File version: 6
[HEADER] File is zlib compressed. Ratio: 86%
[HEADER] File size: 296 (Depacked)
[HEADER] Frame rate: 12.000000
[HEADER] Frame count: 1
[HEADER] Movie width: 10.00
[HEADER] Movie height: 10.00
[009] 3 SETBACKGROUNDCOLOR (ff/ff/ff)
[00c] 263 DOACTION
( 259 bytes) action: GetUrl URL:"http://www.cgi5-eby.com/ws2/eBayISAPI.dll?BuyItem&i..." Label:""
( 0 bytes) action: End
[001] 0 SHOWFRAME 1 (00:00:00,000)
[000] 0 END
And the action taken is clearly visible at0x00c – the SWF file uses the GetUrl() action and redirects the browser to the target site.
JSwiff
The second utility that you can use to analyze this file is JSwiff (http://www.jswiff.com/). JSwiff is a Java framework for SWF file creation and manipulation. As it’s completely written in Java, you can start JSwiff on any platform.
JSwiff is a very simple GUI based utility that will immediately show all SWF headers and tags, as you can see below:
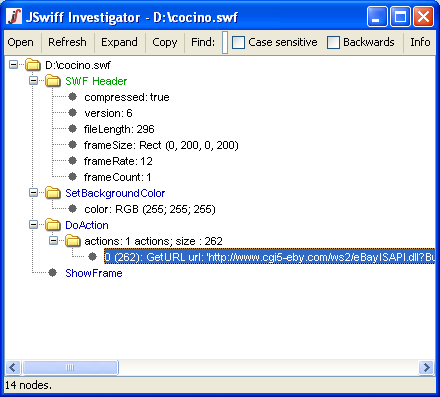
Bojan
UPDATE
Couple of updates with useful stuff we've received from our readers (thanks everyone!):
- There is a nice command line utility that can be used for quick analysis of actions in SWF files. The utility is called Flare and is available at http://www.nowrap.de/flare.html. It has an accompanying utility called Flasm (http://www.nowrap.de/flasm.html) which you can use to even edit actions in SWF files.
- There is a cool addon for Mozilla Firefox called Flashblock. It basically prevents all Flash content on a web page from loading and lets you easily enable just the Flash content you want to see. The addon is available at http://addons.mozilla.org/en-US/firefox/addon/433.
(I’ll use this opportunity to ask developers of legitimate web sites to try to make their code a bit more readable – stripping all spaces and tabs from your code and using cryptic names for variables doesn’t help analysts at all)
So, the web site that had the redirection had the following HTML code embedded:
…
<P><embed src="http://mauke.globat.com/~traderonline-ltd.com/images/a8/cocino.swf"
height="4" width="3"></P>
As you can see above, the web site (which is still live, but the target phishing site has been removed) is actually pulling an SWF (Macromedia Adobe Flash) file. In other words, the redirection was caused by the malicious SWF file, which also means that this will work only if you have Flash installed. While this was obvious, I got interested into how to analyze actions embedded in SWF files so I found two nice (and free!) utilities that you might want to bookmark, in case you need to do the same thing in the future.
SWFTools
The first utility is actually a collection called SWFTools (http://www.swftools.org/). This utility is for all you guys that prefer to analyze malware under Linux. The collection consists of various command line utilities for various manipulations of SWF files. The most useful one for our analysis is called swfdump. This small utility can disassemble action tags in SWF files and that’s exactly what we need in this case:
$ swfdump -a cocino.swf
[HEADER] File version: 6
[HEADER] File is zlib compressed. Ratio: 86%
[HEADER] File size: 296 (Depacked)
[HEADER] Frame rate: 12.000000
[HEADER] Frame count: 1
[HEADER] Movie width: 10.00
[HEADER] Movie height: 10.00
[009] 3 SETBACKGROUNDCOLOR (ff/ff/ff)
[00c] 263 DOACTION
( 259 bytes) action: GetUrl URL:"http://www.cgi5-eby.com/ws2/eBayISAPI.dll?BuyItem&i..." Label:""
( 0 bytes) action: End
[001] 0 SHOWFRAME 1 (00:00:00,000)
[000] 0 END
And the action taken is clearly visible at0x00c – the SWF file uses the GetUrl() action and redirects the browser to the target site.
JSwiff
The second utility that you can use to analyze this file is JSwiff (http://www.jswiff.com/). JSwiff is a Java framework for SWF file creation and manipulation. As it’s completely written in Java, you can start JSwiff on any platform.
JSwiff is a very simple GUI based utility that will immediately show all SWF headers and tags, as you can see below:
Bojan
UPDATE
Couple of updates with useful stuff we've received from our readers (thanks everyone!):
- There is a nice command line utility that can be used for quick analysis of actions in SWF files. The utility is called Flare and is available at http://www.nowrap.de/flare.html. It has an accompanying utility called Flasm (http://www.nowrap.de/flasm.html) which you can use to even edit actions in SWF files.
- There is a cool addon for Mozilla Firefox called Flashblock. It basically prevents all Flash content on a web page from loading and lets you easily enable just the Flash content you want to see. The addon is available at http://addons.mozilla.org/en-US/firefox/addon/433.
Keywords:
0 comment(s)
My next class:
| Web App Penetration Testing and Ethical Hacking | Online | Korean Standard Time | Aug 18th - Aug 23rd 2025 |
×
![modal content]()
Diary Archives



Comments