Emotet Returns
Introduction
Back in January 2021, law enforcement and judicial authorities worldwide took down the Emotet botnet. Although some Emotet emails still went out in the weeks after that, those were remnants from the inactive botnet infrastructure. We hadn't seen any new Emotet since then.
But on Monday 2021-11-15, we saw indicators that Emotet has returned. This diary reviews activity from a recent Emotet infection.
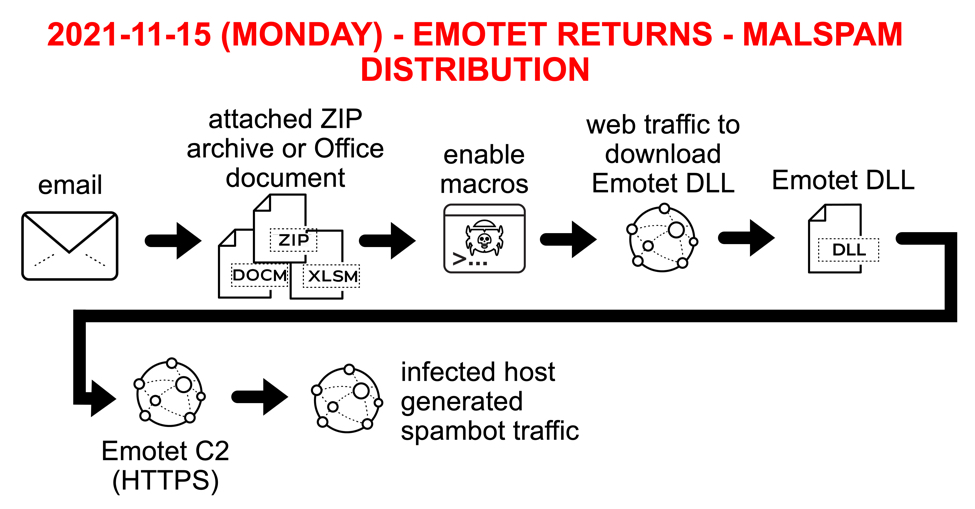
Shown above: Chain of events for Emotet infection on Monday 2021-11-15.
Emails
We found some emails from a newly-revived Emotet botnet on Monday 2021-11-15 that have one of three types of attachments:
- Microsoft Excel spreadsheet
- Microsoft Word document
- Password-protected zip archive (password: BMIIVYHZ) containing a Word document
These emails were all spoofed replies that used data from stolen email chains, presumably gathered from previously infected Windows hosts.
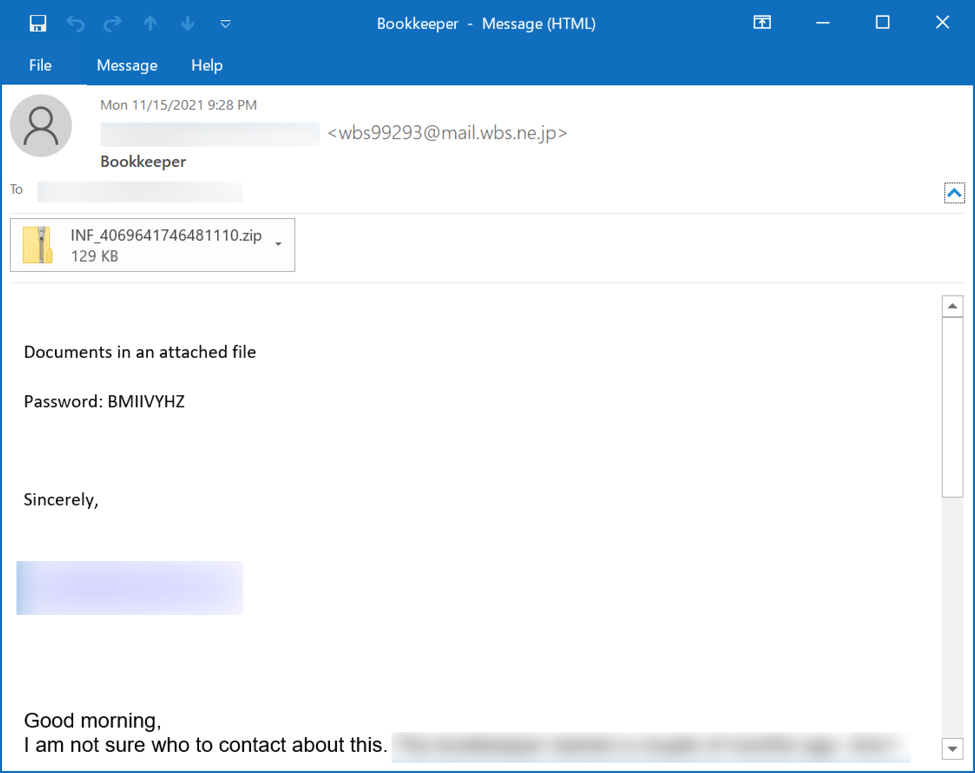
Shown above: Example of Emotet malspam with password protected zip attachment.
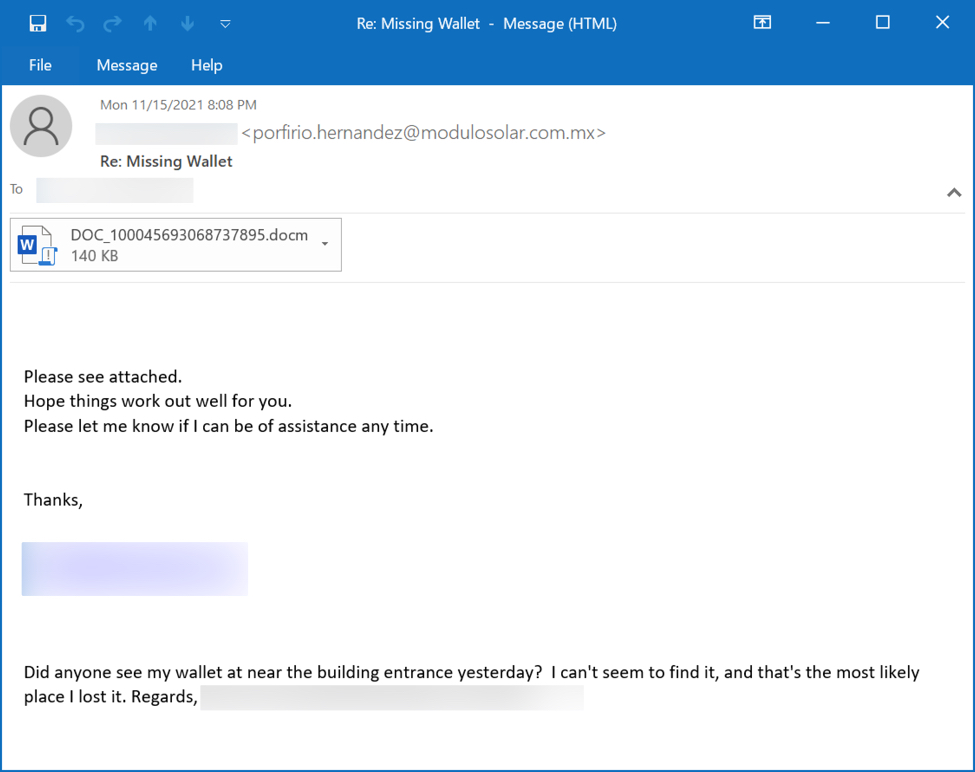
Shown above: Example of Emotet malspam with attached Word document.
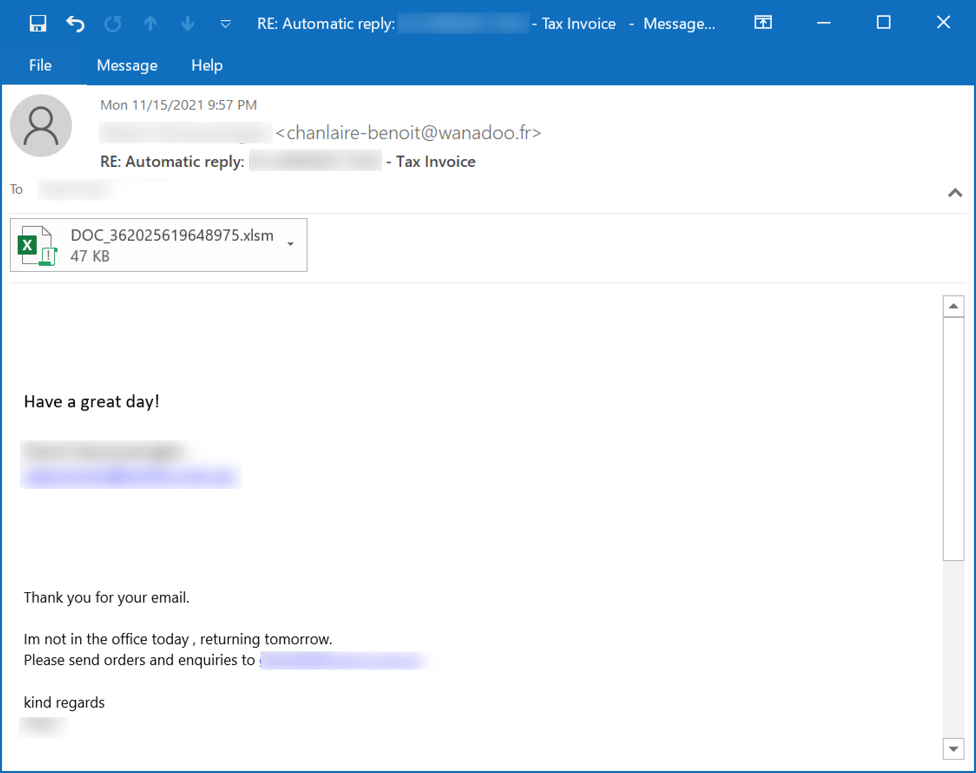
Shown above: Example of Emotet malspam with attached Excel file.
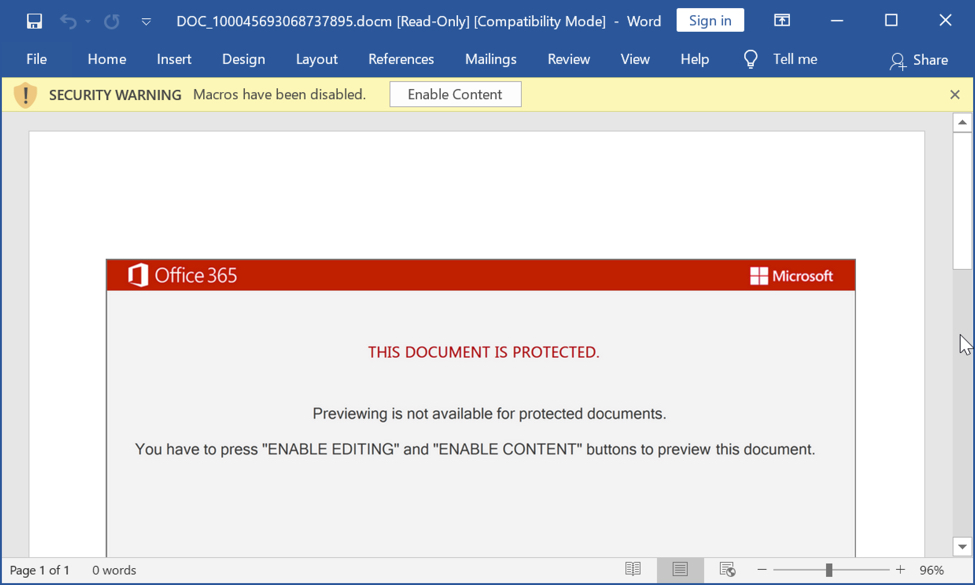
Shown above: Screenshot of Word document for Emotet.
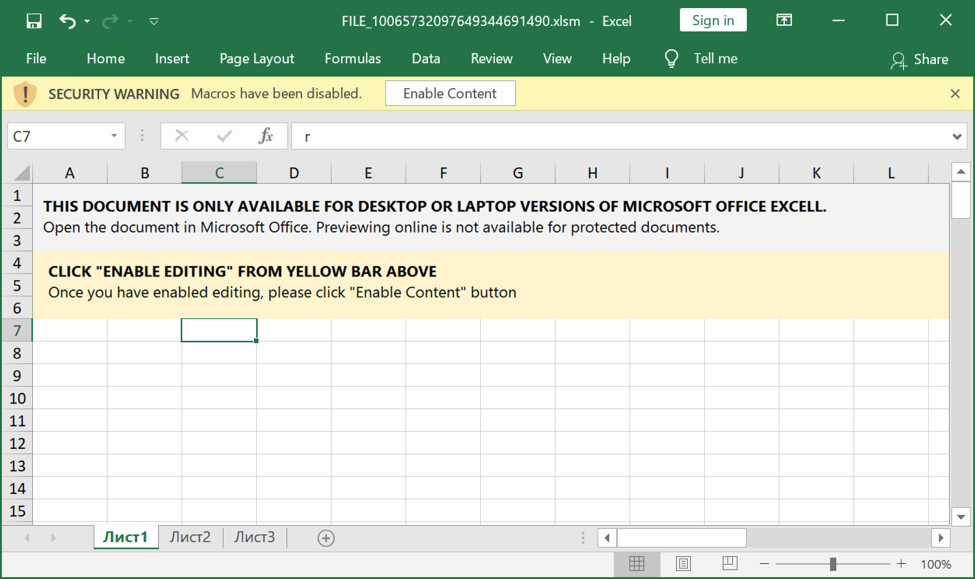
Shown above: Screenshot of Excel spreadsheet for Emotet.
Infection traffic
Infection traffic for Emotet is similar to what we saw before the takedown in January 2021. The only real difference is Emotet post-infection C2 is now encrypted HTTPS instead of unencrypted HTTP. My infected lab host turned into a spambot trying to push out more Emotet malspam.
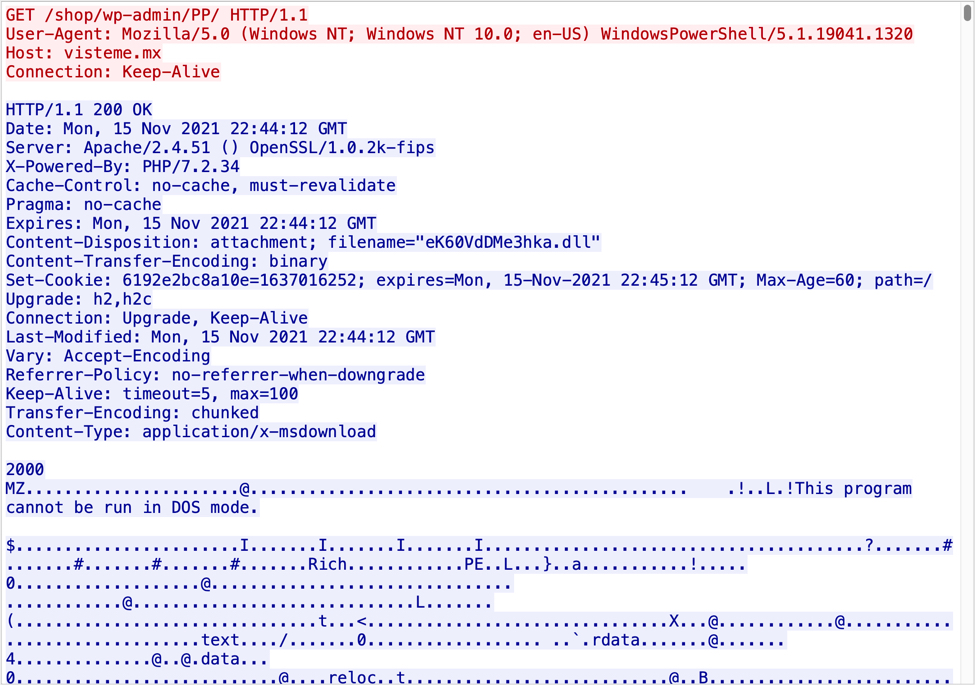
Shown above: Example of traffic generated by Excel or Word macros for an Emotet DLL.
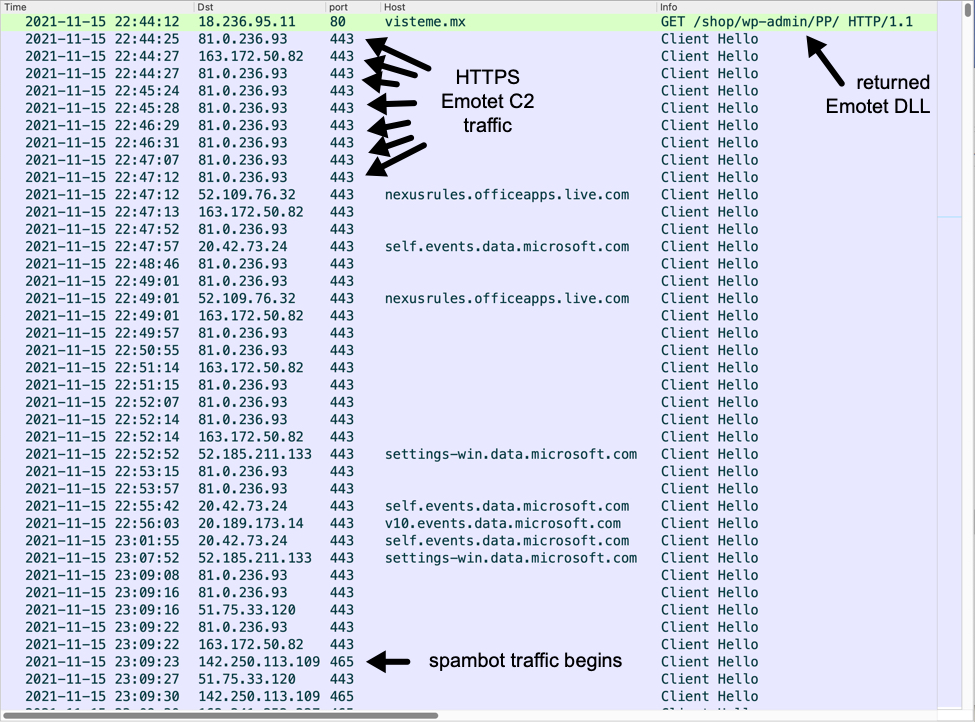
Shown above: Traffic from an infection filtered in Wireshark.
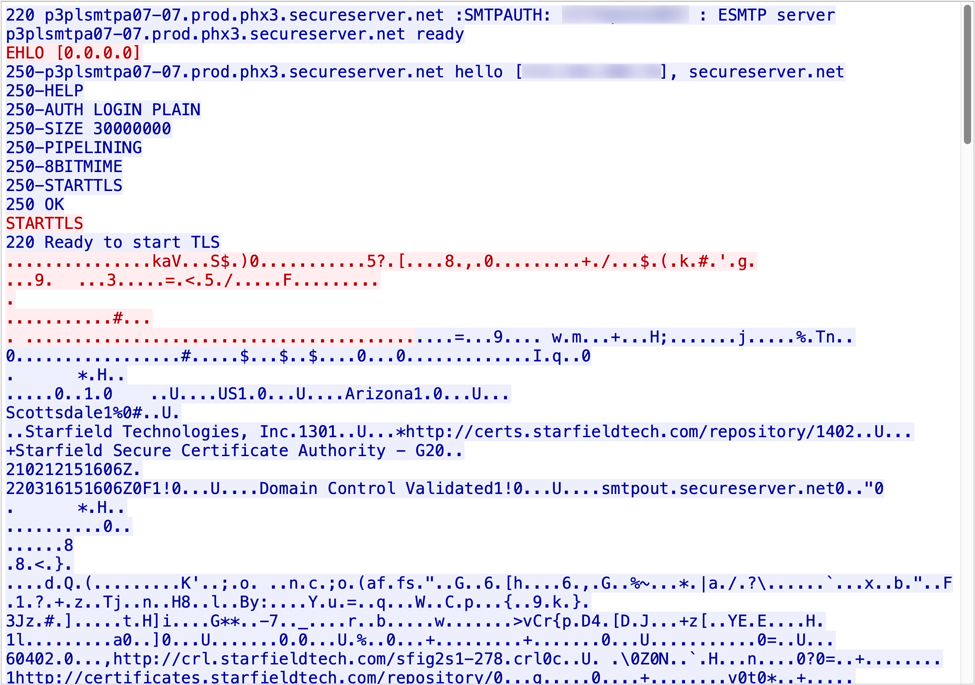
Shown above: TCP stream of encrypted SMTP traffic from my infected Windows host.
Indicators of Compromise (IOCs)
The following are Word documents, Excel files, and a password-protected zip archive I saw from Emotet on Monday 2021-11-15.
SHA256 hash: 7c5690577a49105db766faa999354e0e4128e902dd4b5337741e00e1305ced24
- File size: 143,401 bytes
- File name: DOC_100045693068737895.docm
- File name: DOC_10010148844855817699830.docm
- File name: INF_10043023764772507433030.docm
SHA256 hash: bd9b8fe173935ad51f14abc16ed6a5bf6ee92ec4f45fd2ae1154dd2f727fb245
- File size: 143,121 bytes
- File name: FILE_24561806179285605525.docm
SHA256 hash: f7a4da96129e9c9708a005ee28e4a46af092275af36e3afd63ff201633c70285
- File size: 132,317 bytes
- File name: INF_4069641746481110.zip
SHA256 hash: d95125b9b82df0734b6bc27c426d42dea895c642f2f6516132c80f896be6cf32
- File size: 143,108 bytes
- File name: INF_4069641746481110.docm
SHA256 hash: 88b225f9e803e2509cc2b83c57ccd6ca8b6660448a75b125e02f0ac32f6aadb9
- File size: 47,664 bytes
- File name: FILE_10065732097649344691490.xlsm
SHA256 hash: 1abd14d498605654e20feb59b5927aa835e5c021cada80e8614e9438ac323601
- File size: 47,660 bytes
- File name: SCAN_1002996108727260055496.xlsm
The following are URLs generated by macros from the above files for an Emotet DLL file:
- hxxp://av-quiz[.]tk/wp-content/k6K/
- hxxp://devanture[.]com[.]sg/wp-includes/XBByNUNWvIEvawb68/
- hxxp://ranvipclub[.]net/pvhko/a/
- hxxp://visteme[.]mx/shop/wp-admin/PP/
- hxxps://goodtech.cetxlabs[.]com/content/5MfZPgP06/
- hxxps://newsmag.danielolayinkas[.]com/content/nVgyRFrTE68Yd9s6/
- hxxps://team.stagingapps[.]xyz/wp-content/aPIm2GsjA/
The Emotet DLL was first stored as a random file name with a .dll extension under the C:\ProgramData directory. Then it was moved to a randomly-named directory under the infected user's AppData\Local folder. The DLL is then made persistent through a Windows registry update as shown below.
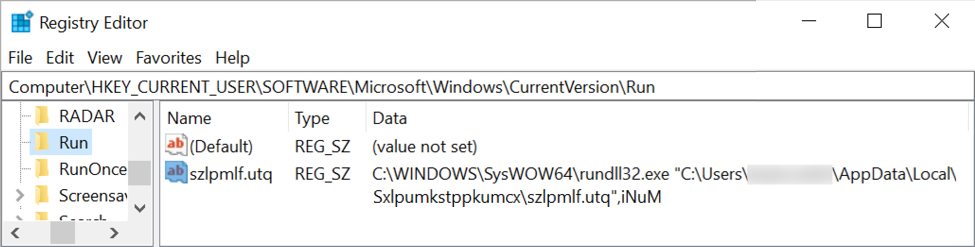
Shown above: Example of registry update to keep Emotet persistent.
SHA256 hashes for 7 examples of Emotet DLL files:
- 0b132c7214b87082ed1fc2427ba078c3b97cbbf217ca258e21638cab28824bfa
- 373398e4ae50ecb20840e6f8a458501437cfa8f7b75ad8a62a84d5c0d14d3e59
- 29de2e527f736d4be12b272fd8b246c96290c7379b6bc2d62c7c86ebf7f33cd4
- 632447a94c590b3733e2e6ed135a516428b0bd1e57a7d254d5357b52668b41f1
- 69efec4196d8a903de785ed404300b0bf9fce67b87746c0f3fc44a2bb9a638fc
- 9c345ee65032ec38e1a29bf6b645cde468e3ded2e87b0c9c4a93c517d465e70d
- b95a6218777e110578fa017ac14b33bf968ca9c57af7e99bd5843b78813f46e0
HTTPS Emotet C2 traffic:
- 51.75.33[.]120 port 443
- 51.159.35[.]157 port 443
- 81.0.236[.]93 port 443
- 94.177.248[.]64 port 443
- 92.207.181[.]106 port 8080
- 109.75.64[.]100 port 8080
- 163.172.50[.]82 port 443
Final words
The emails examples and malware samples from Monday's Emotet activity on 2021-11-15 can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments
And I always remind them, "We would rather spend a few minutes investigating a message you feel uneasy about rather than open an attachment and spend hours or days rebuilding a system or systems."
Thanks and keep up the good work.
Anonymous
Nov 16th 2021
3 years ago
Emotet will abuse established trust between people as well as the "known good" / "accepted domains" configurations that have been implemented to improve communications with customers, partners etc.
A strong defense is to simply block macro-enabled Office documents via anti-malware policies, do not forget that this even works for docm/xlsm/pptm files inside password protected ZIP files as the file names are not encrypted.
Blocking of macro-enabled documents should not affect users at all because they will be notified that this has been blocked and can find ways around this for legitimate use. Did you mean to send a PDF version, could you share via our collaboration tool etc.
docs.microsoft[.]com/en-us/microsoft-365/security/office-365-security/configure-anti-malware-policies?view=o365-worldwide#use-the-microsoft-365-defender-portal-to-create-anti-malware-policies
Enable the common attachments filter: If you select this option, messages with the specified attachments are treated as malware and are automatically quarantined. You can modify the default list by selecting Customize file types.
THANKS from a long time reader.
Tor
PS: Yes, old macros come in .XLSX or .XLS files.. But, finally, Microsoft has published techcommunity.microsoft[.]com/t5/excel-blog/restrict-usage-of-excel-4-0-xlm-macros-with-new-macro-settings/ba-p/2528450 and promise that "XLM macros will soon be disabled by default"
Users can expect this coming change in default behavior to occur in the following M365 updates:
2021 October Current Channel
2021 December Monthly Enterprise Channel
2022 January Semi-Annual Enterprise Channel (Preview)
2022 July Semi-Annual Enterprise Channel
Anonymous
Nov 17th 2021
3 years ago