Flashback on CVE-2019-19781
First of all, did you know that the Flame[1] malware turned 8 years today! Happy Birthday! This famous malware discovered was announced on May 28th, 2012. The malware was used for targeted cyber espionage activities in the Middle East area. If this malware was probably developed by a nation-state organization. It infected a limited amount of hosts (~1000 computers[3]) making it a targeted attack.
At the opposite, we see very broad attacks that try to abuse vulnerabilities present in very common products. Almost every day, new CVEs ("Common Vulnerability Exposure") are released or updated. Yesterday, I indexed 141 new CVEs:
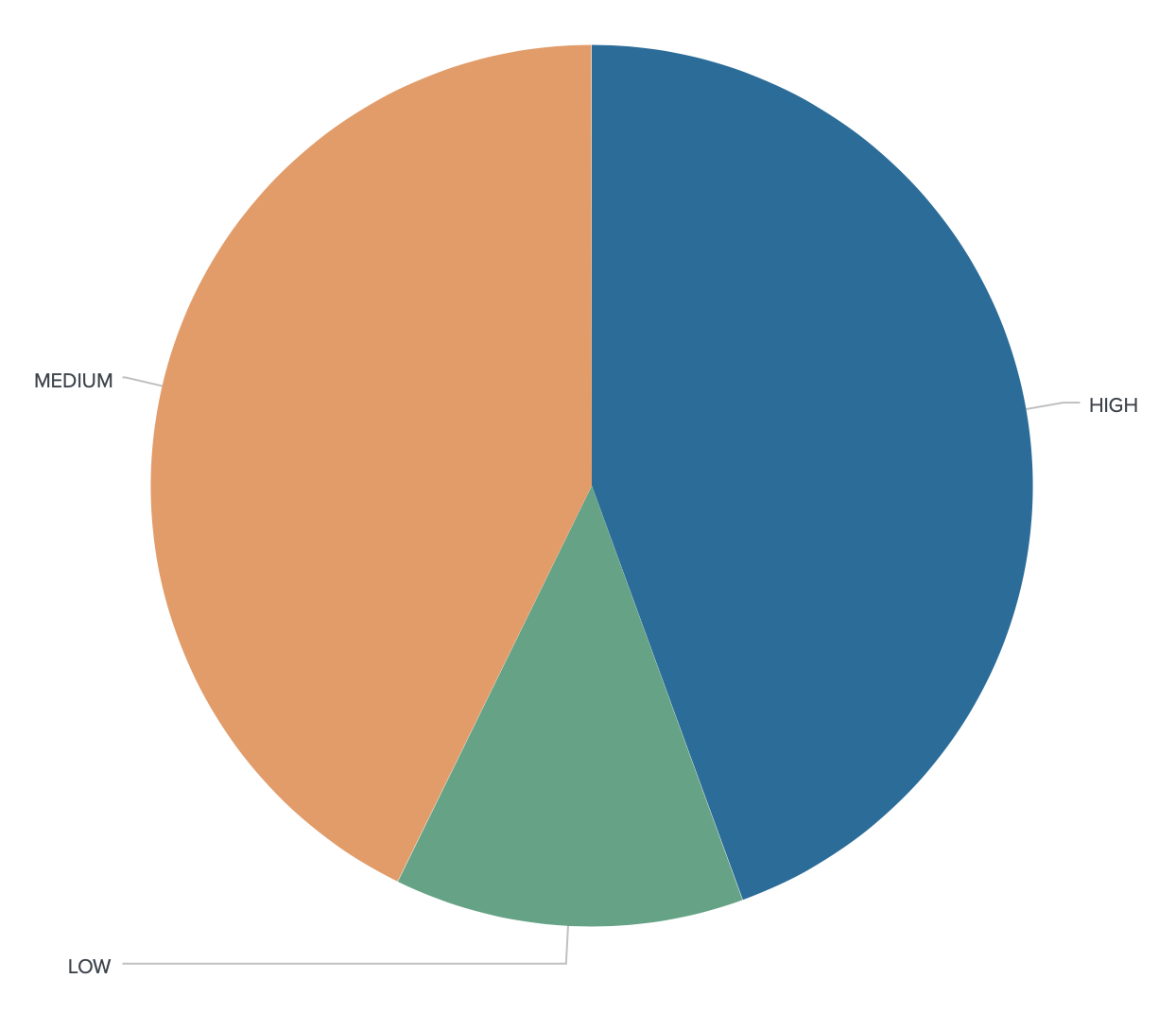
In a perfect world, a CVE is followed by a patch released by the vendor or the developer, followed by the deployment of this patch by the end-user. Case closed! But, it’s not always as simple, for multiple reasons. Recently, an interesting article was released about the top-10 most exploited vulnerabilities[3]. It’s interesting to discover how very old vulnerabilities are still exploited in the wild, by example: CVE-2017-11882 (from 2017!)
Amongst others, let’s have a look at CVE-2019-19781 also know as “Shitrix”[4]. We searched for the population of ‘Citrix NetScaler’ hosts in SHODAN, then we search for the ones tagged with the CVE. Results are interesting (starting from the beginning of the year).
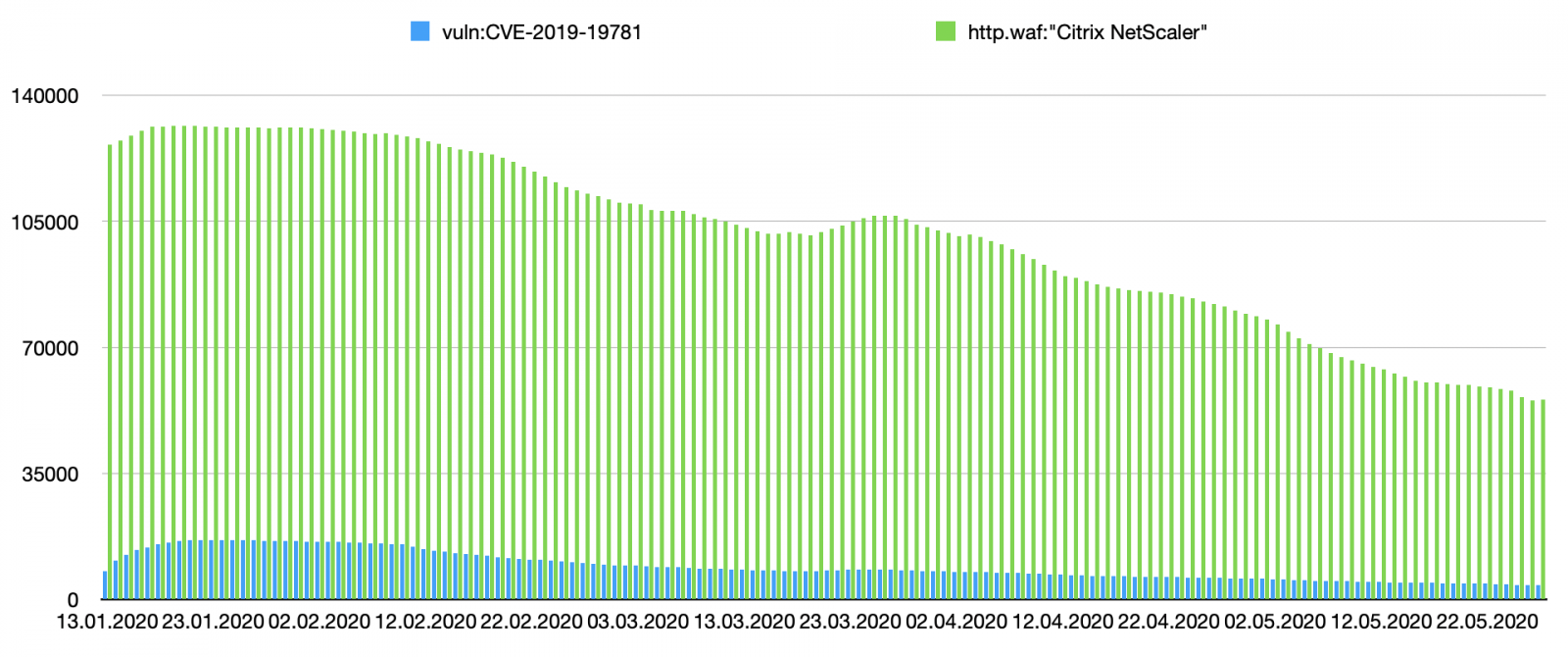
In blue, you see the number of devices identified as vulnerable. The green data represent the entire population of Citrix devices seen online. Let's focus on the two first months:
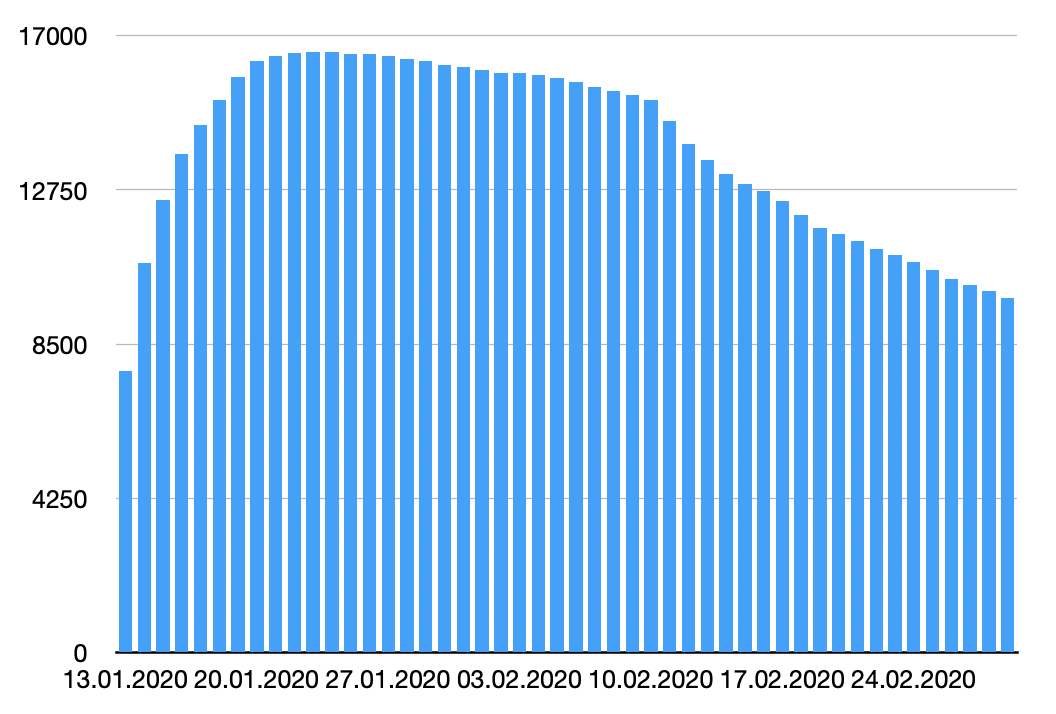
We see that SHODAN is scanning the web and found more and more vulnerable devices, then organizations started to patch then but we remain for a while to a stable amount of devices (around ~4000 detected daily). But we see also a decrease in detected NetScaler devices. How to interpret this?
- Some organizations got rid of their Citrix device and replaced it with another solution? (it could happen)
- Devices were hardened and do not disclose the version/model (footprint not possible)
- Devices facing the Internet are now protected by filters/firewalls
- SHODAN IP addresses are blocklisted (which is bad and does NOT secure your infrastructure)
Anyway, the best advice remains patch, patch, and patch again!
[1] https://isc.sans.edu/forums/diary/Why+Flame+is+Lame/13342
[2] https://www.wired.com/2012/05/flame/
[3] https://nakedsecurity.sophos.com/2020/05/15/top-10-most-exploited-vulnerabilities-list-released-by-fbi-dhs-cisa/
[4] https://krebsonsecurity.com/2020/02/hackers-were-inside-citrix-for-five-months/#more-50556
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | British Summer Time | Jul 28th - Aug 1st 2025 |



Comments
https://radar.securitywizardry.com
Anonymous
May 28th 2020
5 years ago