Good Cop; Bad Cop; Domain Cop?
When investigating events, like malware or spam hitting our systems, we often send notifications to parties from which the malicious traffic originates. One the other hand, it isn't terribly unusual, for us to receive malware notifications if some of the snippets of code we post match anti-virus patterns.
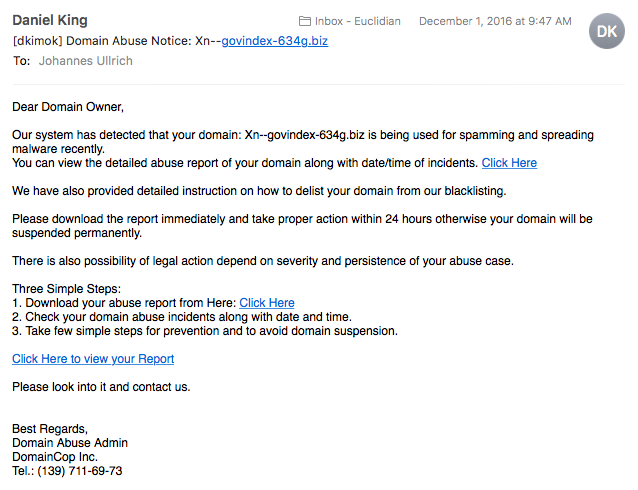
So I was not terribly surprised when I got an e-mail recently regarding one of my more "interesting" domains that I keep around for our web application security classes: xn--govindex-634g.biz . The e-mail claimed to come from an organization that calls itself "Domaincops.net":
As far as malicious e-mails go, I would consider this one of the better once. Obviously, they harvested whois information. It would not be terribly odd to find a link in a message like that (we try to avoid them, but I have seen them used in abuse notifications for tracking). But with any link, it is better to be careful, so I pulled it in from my sacrificial machine / malware lab.
What I got was an RTF document called Abuse_report_HSQ393.doc. Virustotal had some history for the file and identified it as a generic downloader, exploiting an older (CVE-2012-0158) vulnerability. It is kind of sad that this group wasted a pretty nice scheme with a plausible domain name and only had a 2012 vulnerability to deliver with it.
First time I tried to download the file, the site was down (it was however protected by Cloudflare). A day or so later, the site was up again, and I finally was able to download my report. It is interesting that the e-mail was signed with DKIM (my mail server adds the "[dkimok]" flag to all e-mails that have a valid signature). This should make it less likely for e-mails like this to pass spam filters.
Currently, domaincops.net has been suspended by its registrar.
| Application Security: Securing Web Apps, APIs, and Microservices | Washington | Jul 14th - Jul 19th 2025 |



Comments
Joe Loughry
University of Denver
Anonymous
Dec 8th 2016
8 years ago
Anonymous
Dec 8th 2016
8 years ago
Anonymous
Dec 8th 2016
8 years ago
Name Server: BLOCKEDDUETOSPAM.PLEASECONTACTSUPPORT.COM
Name Server: DUMMYSECONDARY.PLEASECONTACTSUPPORT.COM
It's too bad that you did not record the ID of the DNS-servers that they were using/abusing, and the IP-address (and, thus, the hosting-provider) of their web-server, so that the hosting-provider could also be informed about the misdeeds of their customer. Hopefully, that provider, if informed, would [permanently] block the offender from ever getting hosting services in the future.
Anonymous
Dec 9th 2016
8 years ago