Noticing command and control channels by reviewing DNS protocols
Last Updated: 2023-11-14 00:01:25 UTC
by Manuel Humberto Santander Pelaez (Version: 1)
Malicious software pieces installed in computers call home. Some of them can be noticed because they perform DNS lookup and some of them initiates connection without DNS lookup. For this last option, this is abnormal and can be noticed by any Network Detection and Response (NDR) tool that reviews the network traffic by at least two weeks.
Most companies do not have money to afford a NDR, so I'm going to show you today an interesting tip that have worked for me to notice APT calling home when they perform DNS lookup.
- Perform a DNS capture for an extended period of time. 12 hours at least have worked for me. I'm recommending this amount of time because the malicious artifact can call once every specific time. This can be 6 hours, 12 hours or longer. This is a single packet on millions inside the network, so the longer the capture the better.
- I'm using a small capture for this diary about 4 hours long and about 8 million packets:
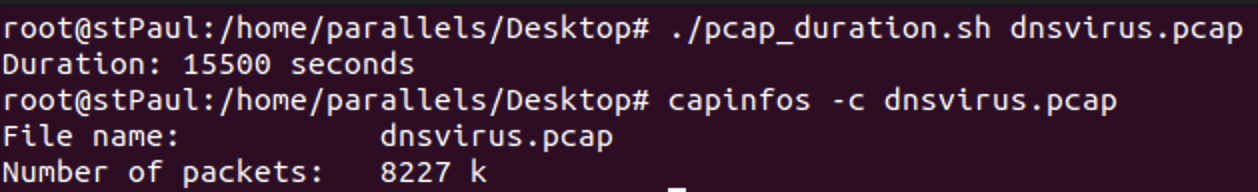
- Now let's transform the traffic into something we can parse. Let's take the source IP address to understand who is performing the call and the DNS query name:
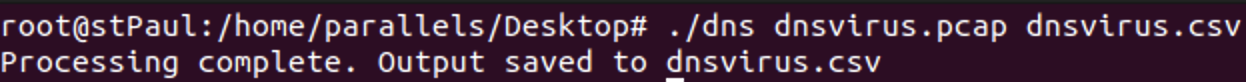
- Let's see the content to understand it worked:
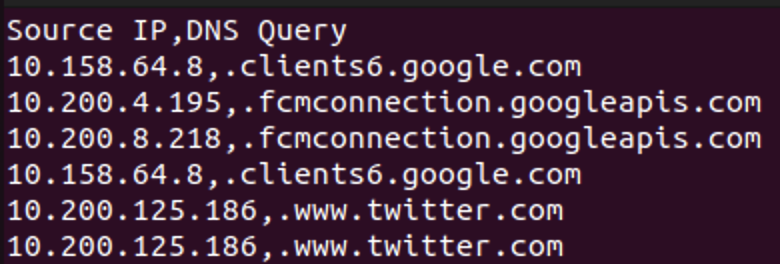
- Where can we see the abnormalities? They will be with the least amount of repetitions. Let's calculate a frequency histogram for the CSV:
- Let's tail the CSV file. We will find some DNS with random DNS char names consistent with malware domains:
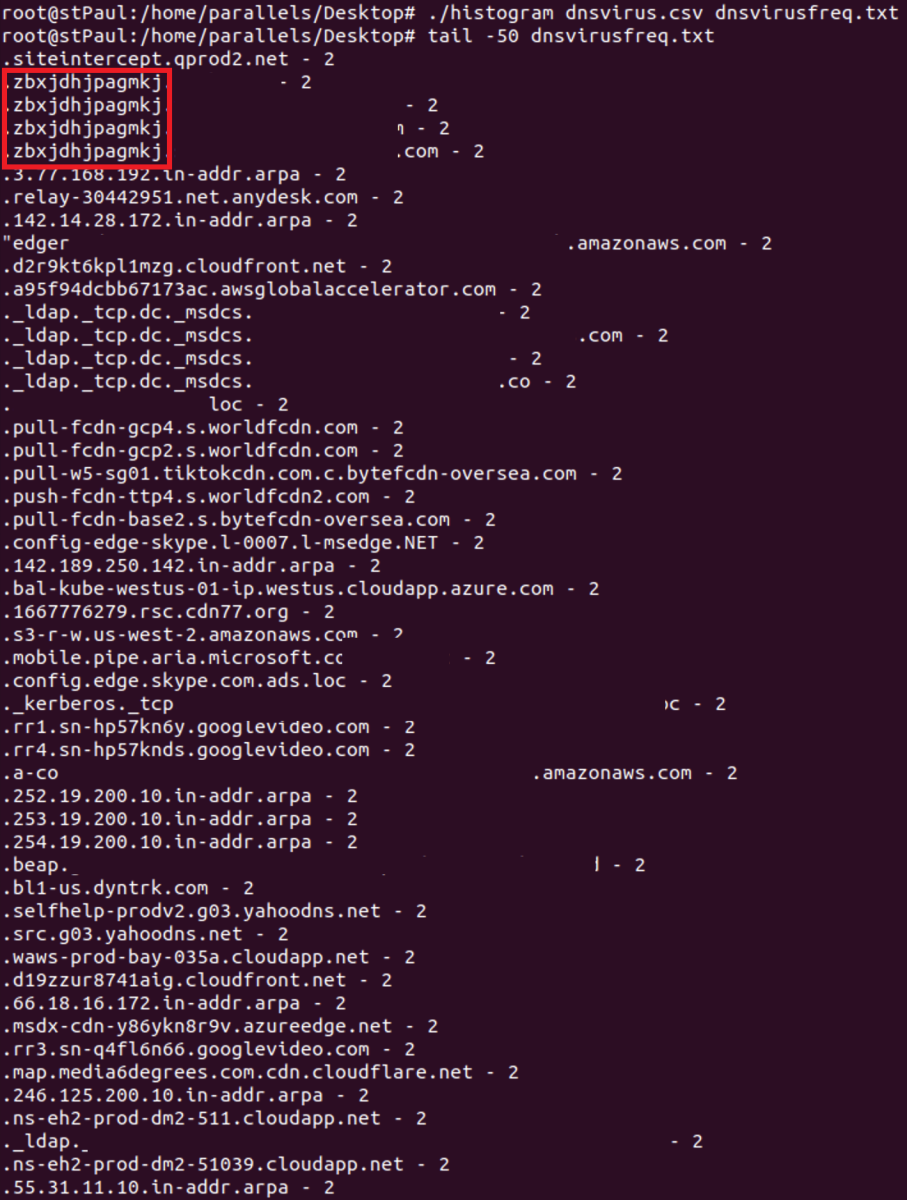
- Correlate the CSV with the dns query name and you will get the name of the compromised computer.
Packet captures are great to understand what's happening on the network. You still can perform threat hunting and incident response without commercial tools and appliances.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Mastodon:manuelsantander@infosec.exchange
email: msantand@isc.sans.org

Comments
Jack
Nov 13th 2023
5 months ago