RedHunt Linux - Adversary Emulation, Threat Hunting & Intelligence
Based on Lubuntu-18.04 x64, the RedHunt Linux virtual machine for adversary emulation and threat hunting is a “one stop shop for all your threat emulation and threat hunting needs. It integrates an attacker’s arsenal as well as defender’s toolkit to actively identify the threats in your environment.”
RedHunt Linux is available as an OVA virtual machine file from http://bit.ly/RedHUNTv1. I imported it with ease via VirtualBox and was up and running in minutes. This distribution includes tools for attack emulation, logging and monitoring, open source intelligence (OSINT) gathering and threat intelligence. As such, I’m going focus on one each from attack emulation, OSINT, and threat intelligence. The virtual machine username and password are hunter. The menu is simple and laid out categorically, you’ll have no trouble navigating accordingly. I’ll follow the same sequence for continuity.
Attack Emulation
Of the attack emulation tool list, there are a few I’ve been meaning to test prior to spotting RedHunt, this is a nice opportunity to do so on a ready made platform. There are a few that may be new to you so allow me to break them down a bit. You’ll notice the Mitre ATT&CK framework leveraged throughout.
- CALDERA “is an automated adversary emulation system that performs post-compromise adversarial behavior within Windows Enterprise networks. It generates plans during operation using a planning system and a pre-configured adversary model based on the Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) project.”
- Atomic Red Team “allows every security team to test their controls by executing simple “atomic tests” that exercise the same techniques used by adversaries (all mapped to Mitre’s ATT&CK).“
- Metta is an “information security preparedness tool that uses Redis/Celery, python, and vagrant with virtualbox to do adversarial simulation. This allows you to test (mostly) your host based instrumentation but may also allow you to test any network based detection and controls depending on how you set up your vagrants. The various actions live in the MITRE folder sorted by MITRE ATT&CK phases.”
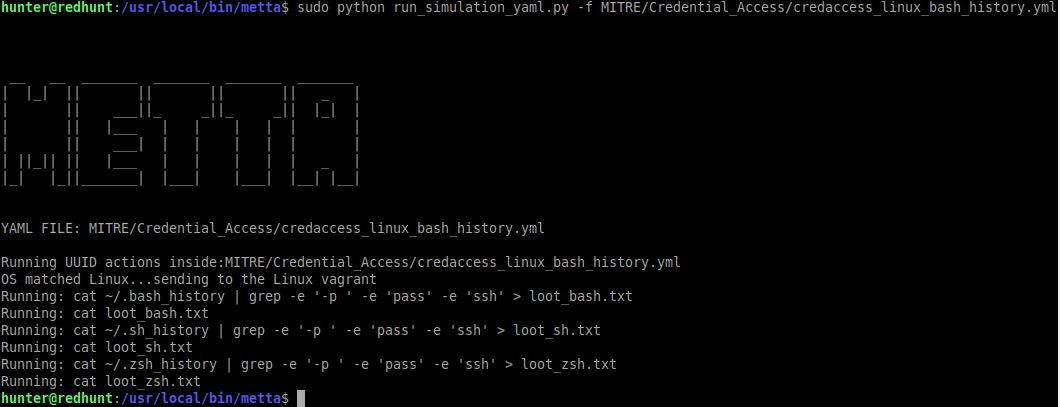
I’ll focus specifically on Metta. I used the RedHunt Linux VM instance itself as my targert and ran the following OS-appropriate scenario, resulting in output as noted in Figure 1.
sudo python run_simulation_yaml.py -f MITRE/Credential_Access/credaccess_linux_bash_history.yml
Figure 1: Metta Linux credential access bash history results
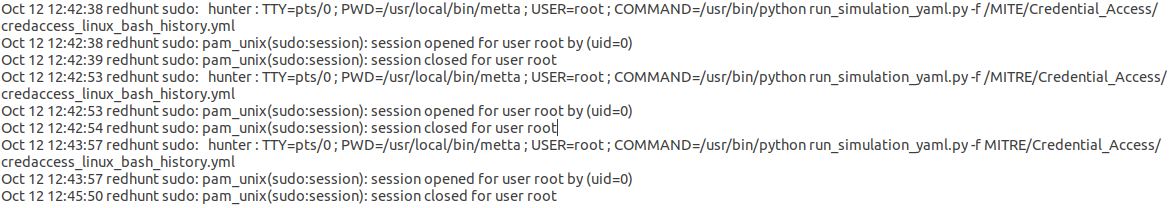
As expected, when I reviewed /var/log/auth.log, Metta’s activity was immediately evident, as seen in Figure 2.
Figure 2: /var/log/auth.log Metta entries
One can imagine that a properly configured detection and alerting scenario should have effictively triggered and fired if tuned to react to such behaviors.
OSINT
The OSINT selection includes Maltego, Recon-ng, and Datasploit, all of which I’ve covered in earlier toolsmith articles, as far back as December 2009 for Maltego.
The one remaining offering I’ve not already discussed is the theHarvester, “a tool for gathering subdomain names, e-mail addresses, virtual hosts, open ports/ banners, and employee names from different public sources (search engines, pgp key servers).” As described, it is indeed a simple tool, and effective for the early stages of a penetration test, as well assessing your target’s Internet exposure. Select theHarvester from the OSINT menu, a shell will open and dump the menu for you.
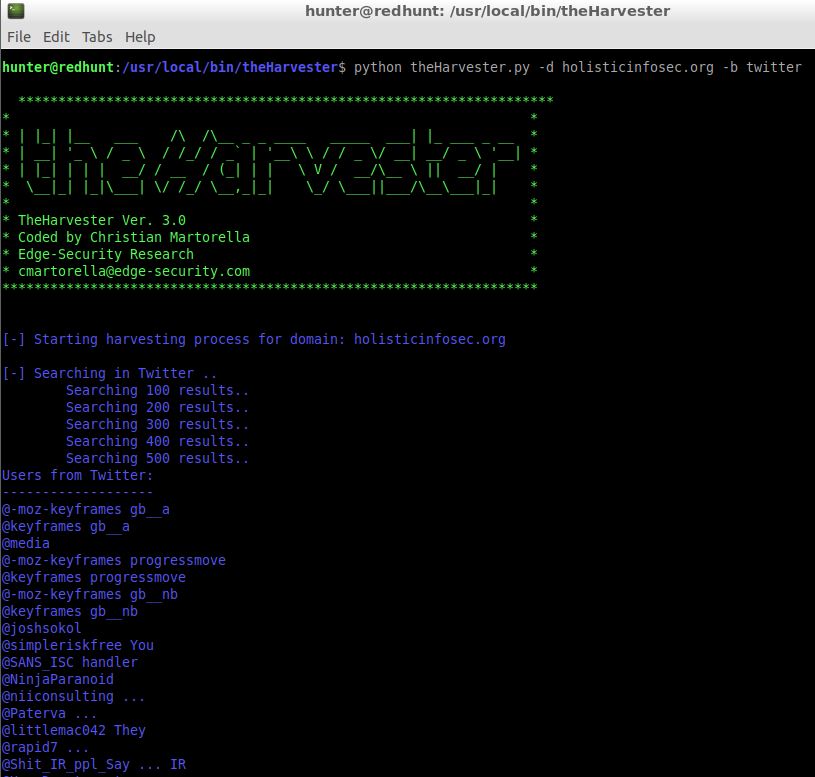
I ran
python theHarverster.py -d holisticinfosec.org -b twitter
and received results as seen in Figure 3.
Figure 3: theHarverster Twitter search results
Threat Intelligence
Finally, in the threat intelligence offerings you’ll find Yeti and Harpoon. I’ll focus on Yeti for our purposes here. Yeti is “a platform meant to organize observables, indicators of compromise, TTPs, and knowledge on threats in a single, unified repository. Yeti will also automatically enrich observables (e.g. resolve domains, geolocate IPs) so that you don’t have to.” Yeti is really where the rubber hits the road for me with the RedHunt OS. I’ll set up a real world scenario for you with Yeti, using it in what could be considered a production manner. Do add your API keys under the user profile so you can take advantage of analytics functionality.
I decided to use IOCs (observables) from GCHQ’s National Cyber Security Centre Indicators of Compromise for Malware used by APT28 report (also known as Fancy Bear, Pawn Storm, the Sednit Gang and Sofacy), released 4 OCT 2018. These include IOCs for X-AGENT (also known as CHOPSTICK), “a second-stage modular remote access trojan (RAT). It can run on Windows, iOS and Unix-based operating systems.” These IOCs include IPs, domains, and hashes.
Additionally there are CompuTrace IP and hash-based IOCs. “CompuTrace/Lojack is a legitimate piece of software, which can track and assist in the recovery of lost or stolen laptops as well as remotely locking and deleting files.”
Also available are IP, domain, and hash X-TUNNEL IOCs. X-TUNNEL is a “network tunnelling tool used for network traversal and pivoting. It provides a secure tunnel to an external command and control server, through which the actors can operate using a variety of standard networking tools and protocols to connect to internal services.”
Finally, there are ZEBROCY IOCs. ZEBROCY is a tool observed since late 2015. “The communications module used by ZEBROCY transmits using HTTP. The implant has key logging and file exfiltration functionality and utilises a file collection capability that identifies files with particular extensions.”
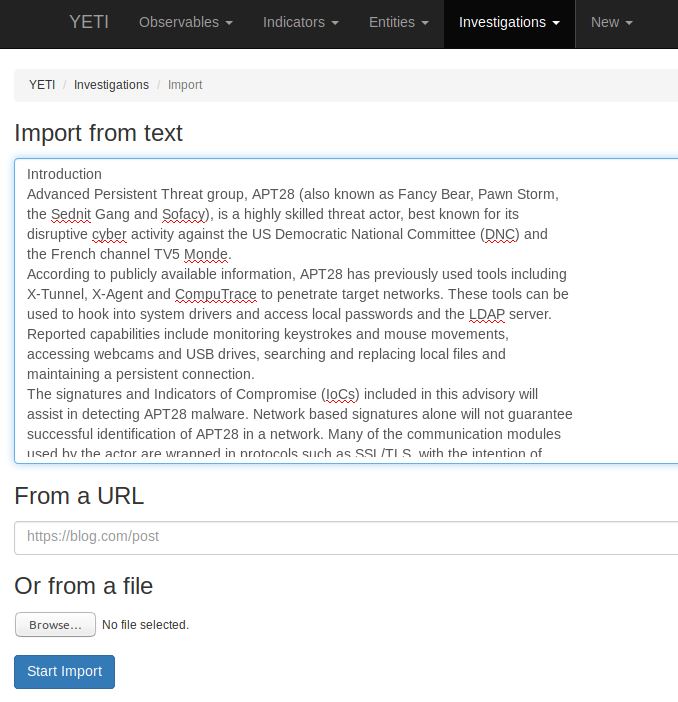
Yeti allows you to add observables manually, and does include excellent guessing functionality if you tag IOCs as unknown. But by now you’re likely saying “Russ, STFU, you had me at Fancy Bear.” Right on, so let me give you that “Dude, that’s awesome” moment. Above all else, read Yeti’s documentation, there’s much to learn here as well as features and capabilities I won’t explore. Yeti can import an Investigation from text, a URL, or a file. Choose Investigations then Import. I literally copied the text I wanted to import from GCHQ’s report (pages 2 through 6) into the Import from text window and clicked Start Import. Figure 4 is the result.
Figure 4: Yeti import function
Yeti then presents you with what it determines are the observables by categories, IP, hostname, and hash in this scenario. Scroll down the list and then choose Import. If you then go to Observables, then Browse, you’ll see all the IOCs you just imported. Organizationally, you can/should tag the entities as they’re associated (xagent, computrace, xtunnel, zebrocy) in the report. You’ll also want to go to Investigations, then List, and select Unnamed. Choose the Investigation you just imported and tagged, name it and save it accordingly. I used APT28 NCSC for mine. You can add a new Actor via the New menu. Again, APT28 makes sense here, and you can mark this Actor entity with your above created tags. Similarly, you can bind to entities with the same tags. I did the same thing again with a Campaign, also calling it APT28 NSCS. I then drilled to Entities and selected this campaign. I created a new Investigation then selected Go To Graph.
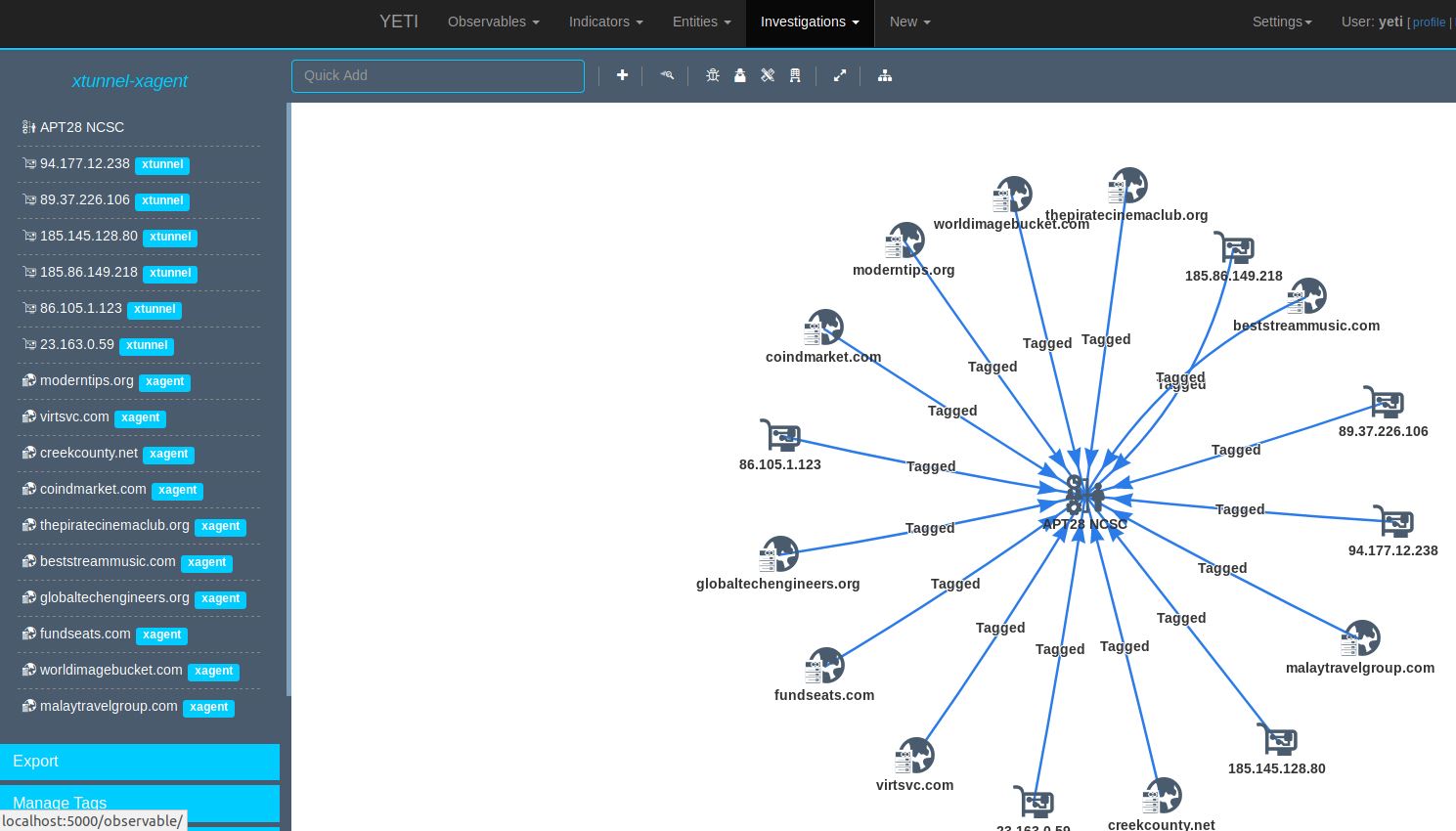
Now for the magic. You’re presented with a node map that for you Maltego users may look conceptually familiar as noted in Figure 5..
Figure 5: Yeti Graph
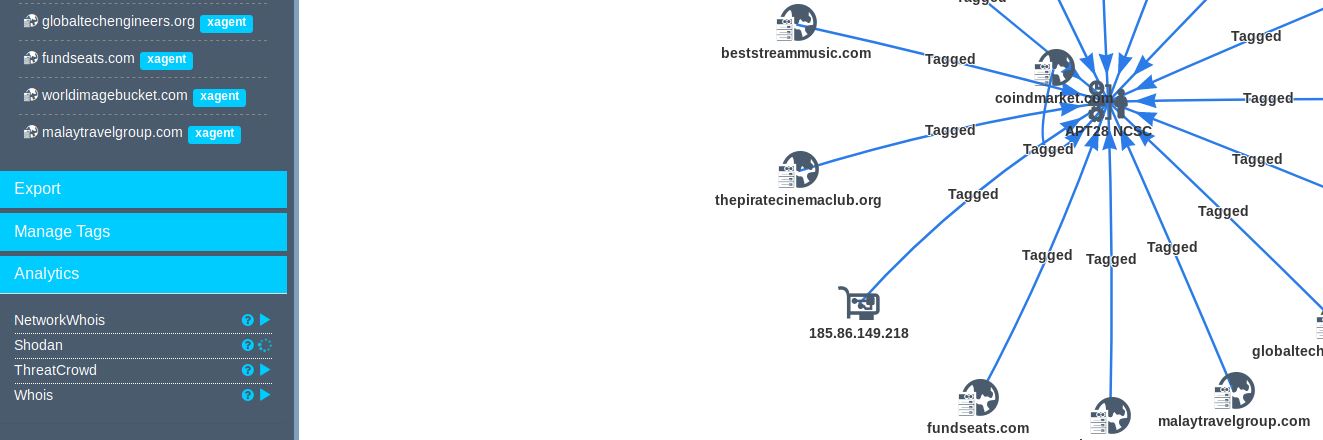
Select an individual node or all nodes then run a variety of analytics (Figure 6). These depend on the API keys you set in your profile as discussed earlier.
Figure 6: Yeti Analytics
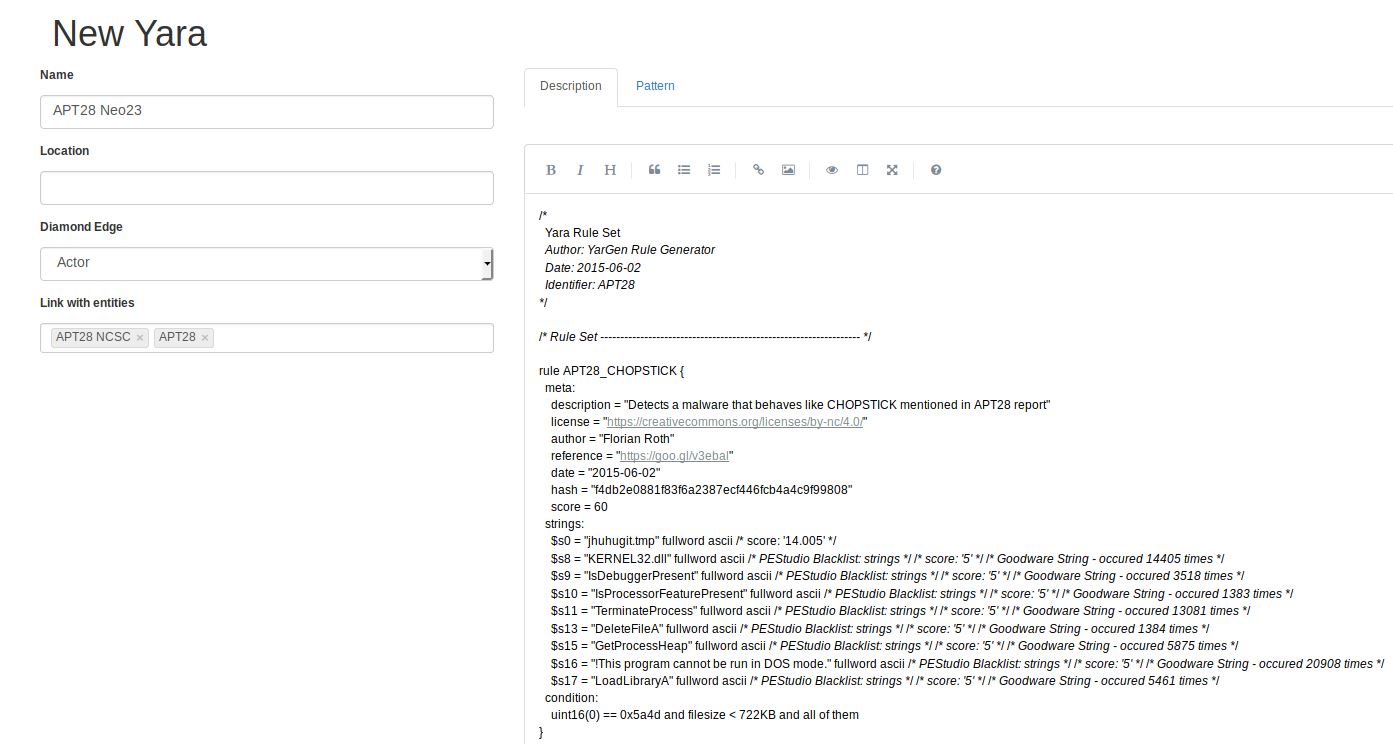
You can import Yara rules too (Figure 7). I opted for Florian Roth’s,@cyb3rops, APT28 rule.
Figure 7: Yeti Yara import
I intend to continue using RedHunt Linux beyond simply testing it for toolsmith. I’m particularly invested in Yeti and recognize of only touched on the basics of its use here. I plan to dig into the API and export, there are numerous interesting features yeti to explore. :-) Yeti is definitely a truly viable option for managing your threat intelligence practice.
I strongly suggest you dig in to RedHunt and Yeti, I’d love to hear more about your experience. Ping me via email (russ at holisticinfosec dot io) or Twitter @holisticinfosec.
Cheers…until next time.



Comments