Russian language malspam pushing Shade (Troldesh) ransomware
Introduction
Shade ransomware was spotted in the wild as early as 2014, and it was first called Troldesh. I previously wrote an ISC diary on malicious spam (malspam) pushing Troldesh ransomware two years ago in November 2016, and I also documented a later example in March 2017.
However, Shade/Troldesh ransomware has been spotted in the wild since then. I searched Twitter and found a handful of sightings in the past few weeks. Today's diary reviews recent examples from a campaign using Russian-language malspam to push Shade/Troldesh, and it also examines an infection from Wednesday 2018-11-28.
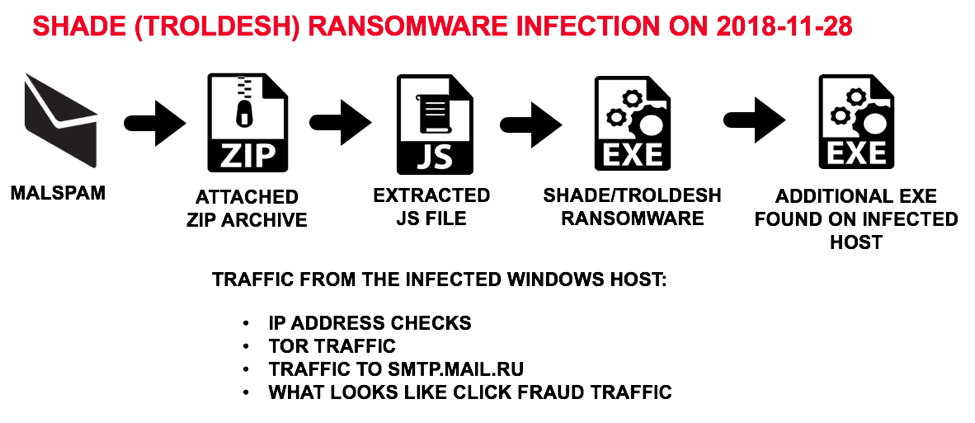
Shown above: Flow chart for the Shade/Troldesh infection I saw in my lab.
Recent campaign since October 2018
This investigation started after I ran across a Russian language email with an attachment that caused a Shade/Troldesh ransomware infection after I checked it in my lab environment. I hadn't paid much attention to this ransomware family in a while, so I decided to look into it.
My first step in the investigation was checking URLhaus. There I found approximately 50 URLs reported as an executable and tagged either Shade or Troldesh (or both) since October 2018. Many of these URLs ended with sserv.jpg, and a search on that revealed 71 URLs reported since 2018-11-01. I added more URLs after my investigation. Not all of these URLs reported to URLhaus were tagged Shade or Troldesh, but they fit the same general pattern that I'd seen from my infection traffic.
Searching through VirusTotal Intelligence, I found Russian language malspam with attached zip archives pushing Shade/Troldesh ransomware since at least 2018-10-30. I collected 12 examples to investigate for this diary.
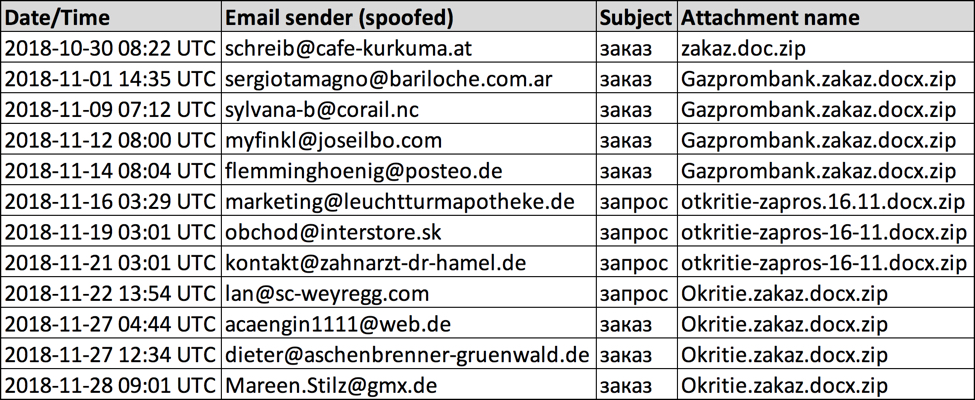
Shown above: Data from 12 malspam examples I collected.
The malspam
The emails are in Russian, and they claim an order or a request from a bank.
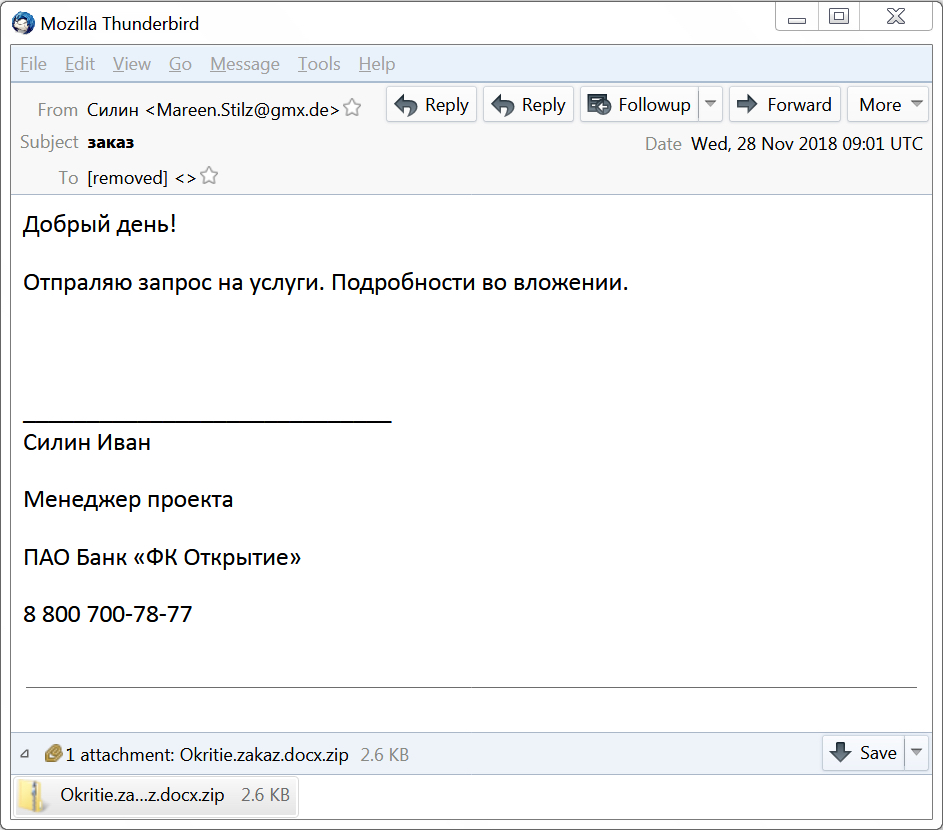
Shown above: Screenshot from one of the emails.
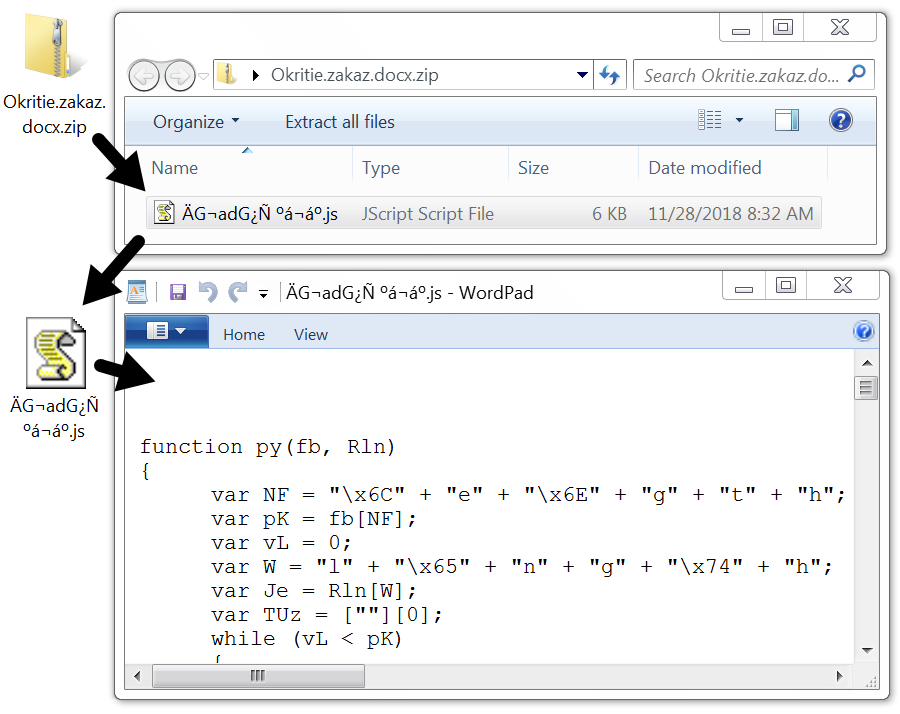
Shown above: The attached zip archive contains a .js file.
An infected Windows host
Potential victims would need to be on a vulnerable Windows host with poor security measures. Victims would open the attached zip archive, then they would need to double-click the JavaScript (.js) file contained in the archive. This causes their Windows computer to retrieve Shade/Troldesh ransomware and become infected. The ransomware infection quickly becomes obvious.
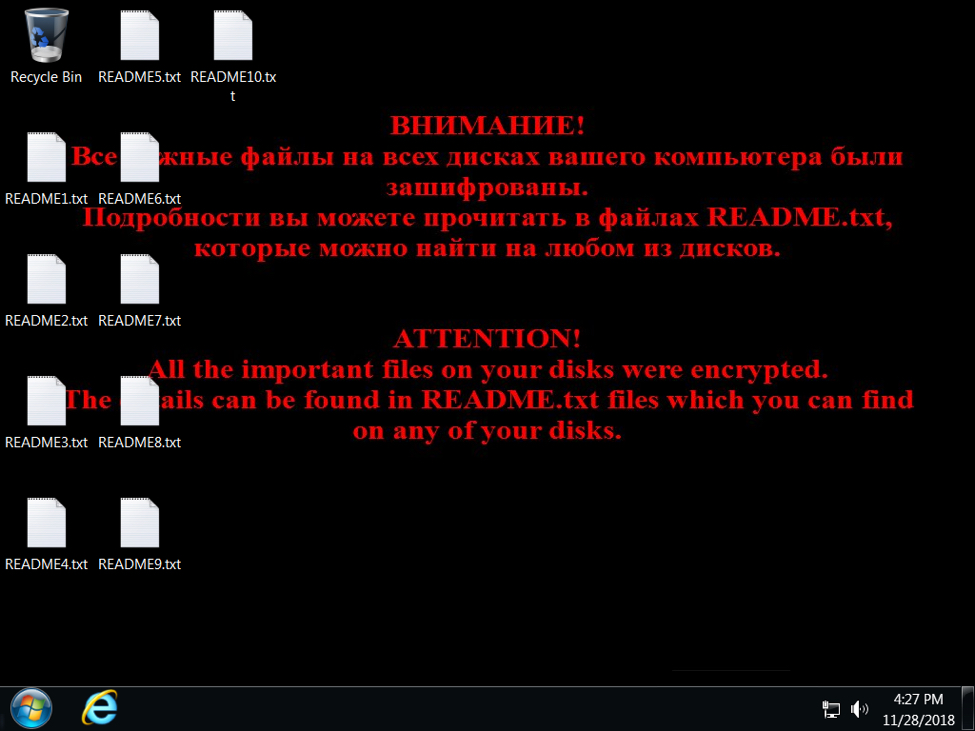
Shown above: Desktop of an infected Windows host.
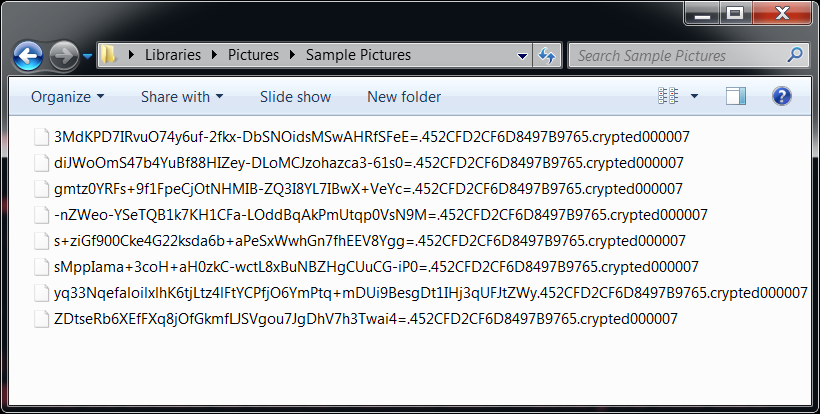
Shown above: All encrypted file named end with .crypted000007
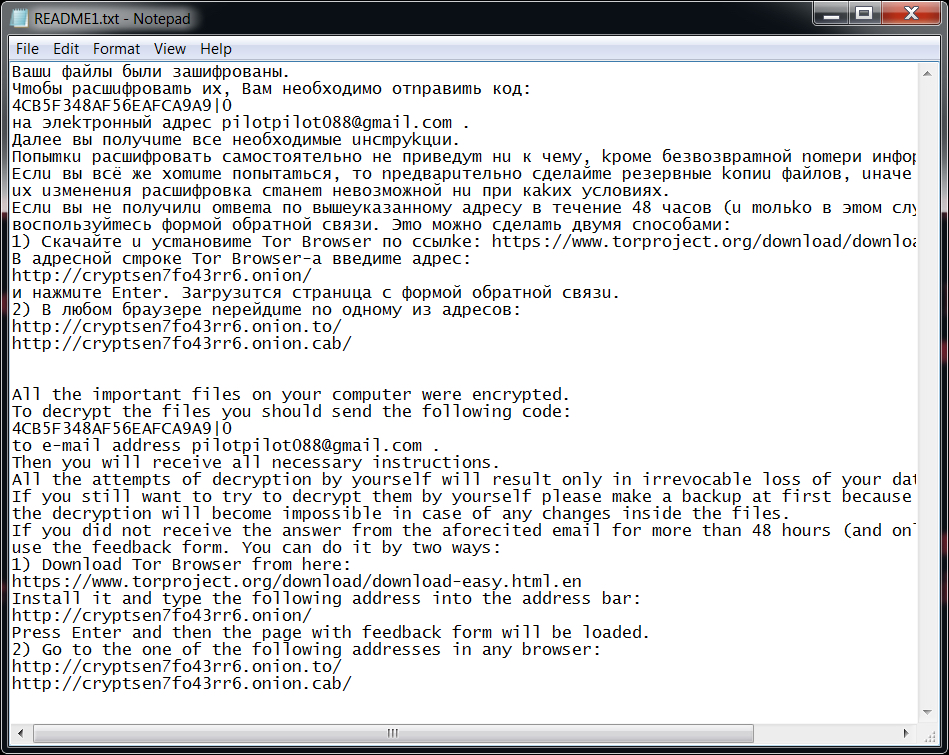
Shown above: The ransom payment instructions are written in both Russian and English.
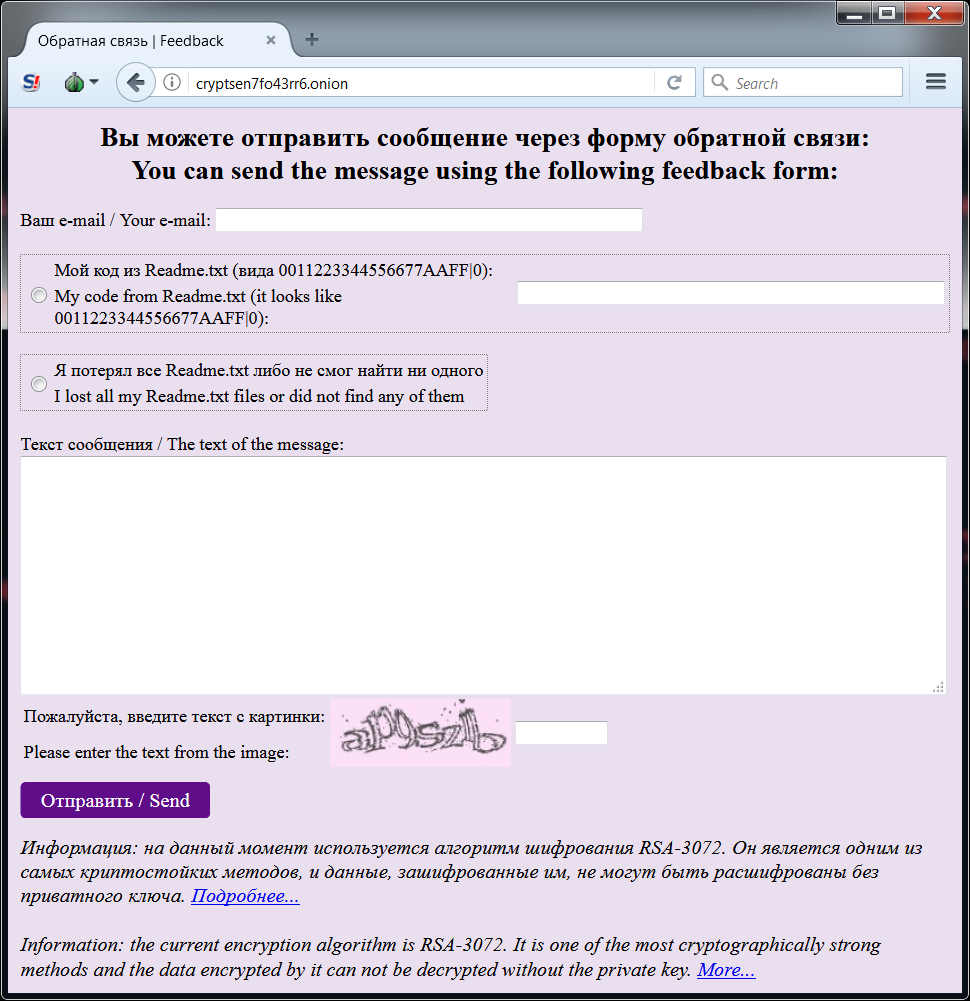
Shown above: Tor page where victims would start a discussion about the ransom payment.
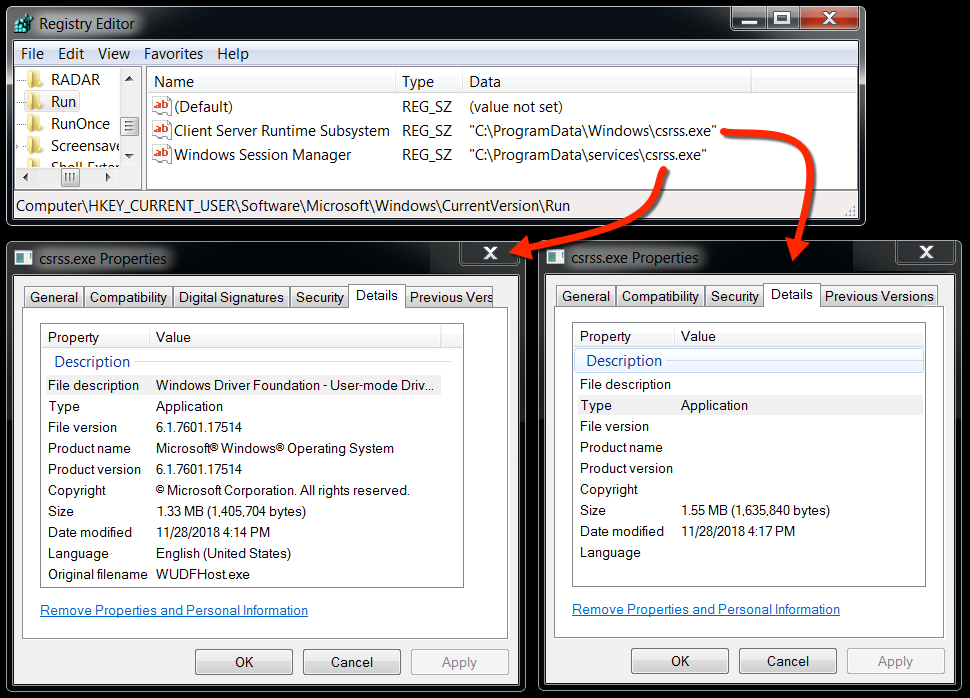
Shown above: Malware from the infection persistent on the infected Windows host.
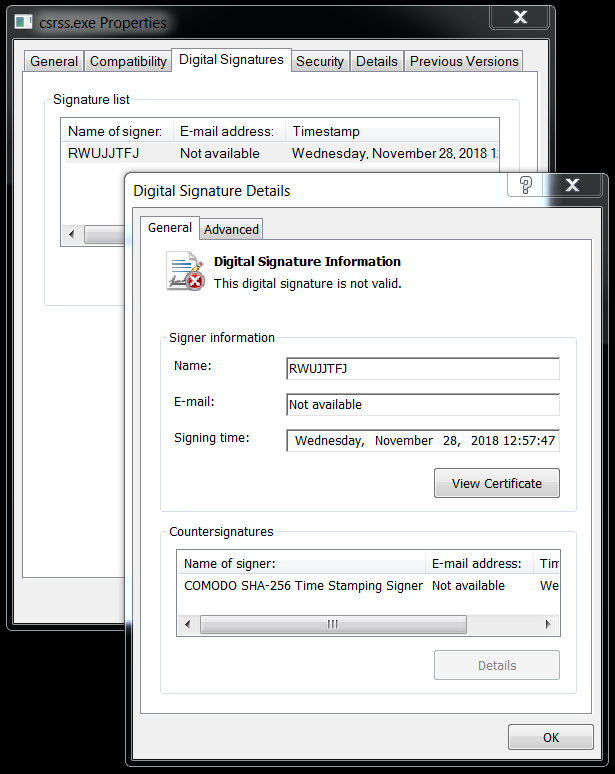
Shown above: Certificate data from one of the malware executable files.
Infection traffic
Almost immediately after the initial Shade/Troldesh malware binary is retrieved, the infected host generated Tor traffic. Then the infected host checked it's IP address and generated encrypted SMTP traffic to smtp.mail.ru.
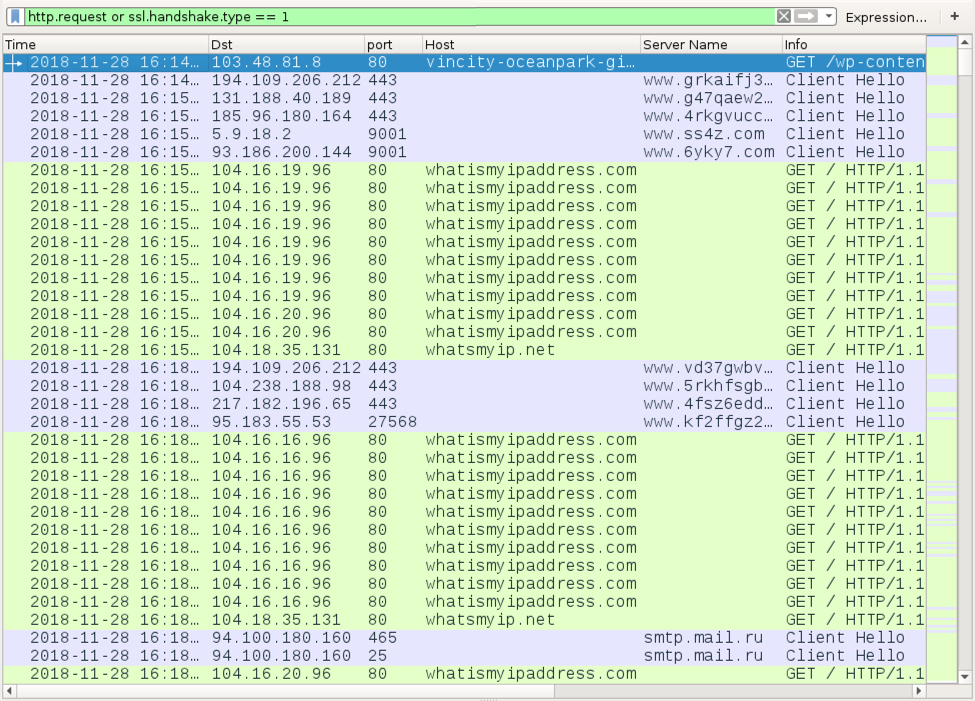
Shown above: Filtered in Wireshark, the initial infection traffic after a .js file was executed.
After four cycles of IP address checks and SMTP traffic, the infected Windows host generated a great deal of web traffic. This reminded me of click-fraud traffic.
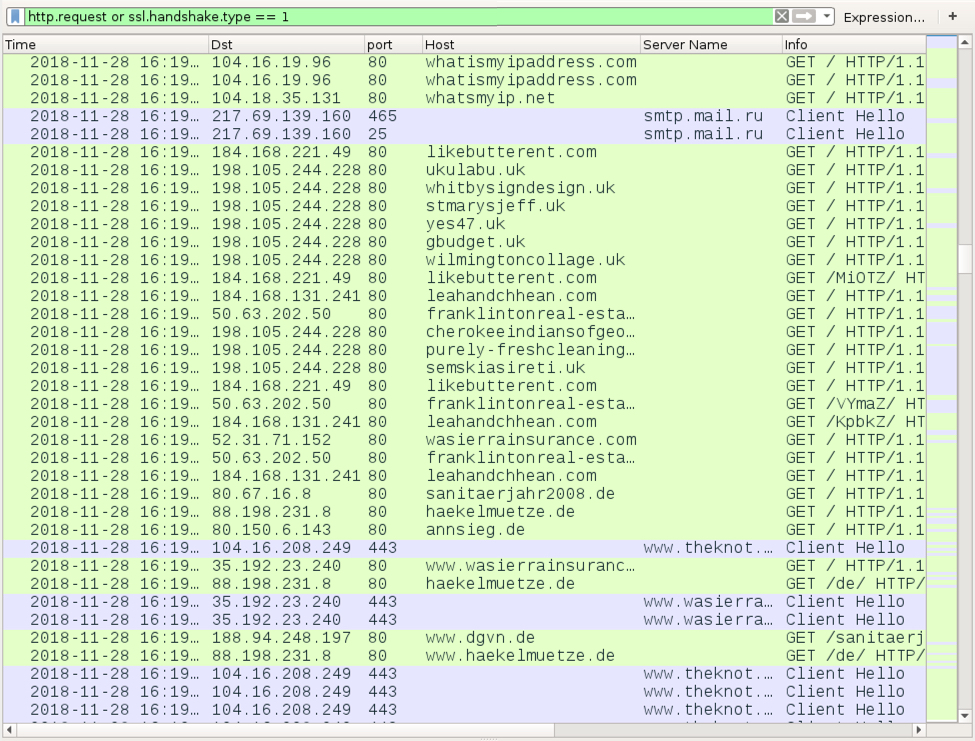
Shown above: Possible click-fraud traffic approximately 5 minutes later.
Indicators
The following are indicators from this malspam campaign and the associated infections:
- Examples found dated as early as 2018-10-30
- Various spoofed sending email addresses
Attachment names noted so far:
- zakaz.doc.zip
- Gazprombank.zakaz.docx.zip
- otkritie-zapros-16-11.docx.zip
- Okritie.zakaz.docx.zip
Some SHA256 hashes for attached zip archives:
- 249b86cc2bd5b28f77b9a61b1b66ed704aefe0be27e44e4e620c65b61b089b92
- ff87a5ca1ee240be8f788c3c3affeee46dea2a63c8cd9963130dcb223388dc6f
- b339aa8060210319472e5fcf935e509c95224c6933fc16e9468d8b48773a5950
- c70163783d5ce1307802a551b8ef0c080a3881ed90c41685e2624135ea5fd6e2
- 4179695f015fb1c8337be67a2e974fcf5dc4fa4b116f6223763b10e67d76b1a1
- 1f5de330ceef0c53799c53d54b47531656d9a1b8b271be59dc99cf90aafd12a9
- b3cfdcd6ffd0e08a55fb9d27a02883e7a7eaecf6fd14a4613984b3ed67feb166
- 3dc38475216d694062172bdc78ae4204755b026b544737ed5891c744acc49eca
- 0b72cc16d752ef266bcc655075c53658ecc05d28c57b9bc73806f15a03f5ab4a
- 1dff4e9d17948095a247edeb23c38e940ea163d6b103869e4abc8aa597a630cb
- 4cd6e03e7ce7e808e8c8c1f3f21bbecdc7b385f156bcc7ee2390c8c6316fd60c
- 5f50dcf06dd5fb51b26f815fd8ff6d4a5afa7301e9c7923ea8f75b2b1e224f82
Some SHA256 hashes for extracted JS files:
- db5fa717b638d86af42cb1db96002d7e264f9b474bbd34bf3a229bbea0fcc3fc
- ca3becff92c6fae2434e57cdc34f1a1ed96d4bf64bb6c0806dd220c71197faa0
- 2dbdd1d06b37835efeb029ce06ad4d8b6eb334e7702f62e8b1572c2b9c0f0983
- 4183405b950db6a04d762bb97d27e144a98419755afa7b02a2e353ac2eb2cb08
- 79cf9a53a96bd9aa7c9f04a90bd3b29f6b48eeb35ac41adba03de143578f60a1
- 6d0205bca14df731a4aae8a7d8b0e9b5bbc3599a70c89dd2d2ffc4f6290df588
- c5c0d0ee70e9e9a25263bca43009061dce8758f839d265ed154d6d064bc31280
- 592fb4fea1d8c9a9a12e55cf4c2817f0f6467d344460c711d4192dd9ebda32e9
- 8a4863db3d778387f9d2809481a08a585f20a31022de603c50b9b07f2f4c2860
- 29feff2c97027661301e2baa1b83bdf40ffb1a56afcfec6ba7811ceaf7bb0c87
- 13d674b64e66a97d40fb6f38237b450a3af95310d7ed008954c8ab2760361165
- e51f36811056d71c970791223da17c3f5b4d84394063a42eb8f2c432e97dba7a
URLs generated by the above extracted JS files:
- hxxp://bosnasport[.]info/wp-content/plugins/ad-inserter/css/images/chrome.jpg
- hxxp://deepakasso[.]com/wp-content/themes/advisor/fonts/chrome.jpg
- hxxp://www.mrtaotao[.]com/wp-content/themes/pacify/images/sserv.jpg
- hxxp://azhub[.]us/.well-known/pki-validation/sserv.jpg
- hxxp://yueltoursandtreks[.]com/components/com_ajax/sserv.jpg
- hxxp://fnbadventure[.]com/components/com_ajax/sserv.jpg
- hxxp://xn--e1adigbdjz5k[.]xn--p1ai/includes/sserv.jpg
- hxxps://inspierasibunda[.]win/wp-content/themes/superfast/images/sserv.jpg
- hxxp://www.izmirlipilavciadnan[.]com/wp-content/themes/twentyseventeen/assets/css/sserv.jpg
- hxxp://conseil-btp[.]fr/wp-snapshots/sserv.jpg
- hxxp://nexusonedegoogle[.]com/wp-includes/ID3/sserv.jpg
- hxxp://tuhoctiengduc[.]asia/wp-includes/ID3/sserv.jpg
- hxxp://immergasteknikservisibursa[.]com/js/views/sserv.jpg
- hxxps://chasehematite[.]com/wp-content/themes/rara-business/sections/sserv.jpg
- hxxp://ansaigon[.]com/templates/tm_parallaite/features/sserv.jpg
- hxxp://buivanhuy[.]com/templates/boker/css/fontawesome/css/sserv.jpg
- hxxp://grandholidayvacations[.]in/AdminEmail/admin/css/sserv.jpg
- hxxp://rhinoarabia[.]site/code.jquery.com/sserv.jpg
- hxxp://tiesmedia[.]com/sserv.jpg
- hxxp://lilaafit[.]xyz/wp-content/themes/twentyseventeen/template-parts/footer/sserv.jpg
- hxxp://marosprint[.]hu/templates/siteground-j15-138/css/sserv.jpg
- hxxp://test.kalaakart[.]in/sserv.jpg
- hxxp://vincity-oceanpark-gialam[.]com/wp-content/cache/blogs/sserv.jpg
- hxxp://mysmilekart[.]com/journal/cache/sserv.jpg
SHA256 hashes of Shade/Troldesh ransomware retrieved from any of the above URLs on still active on 2018-11-28:
- 0b5ed93a5da40cec20f414028fab9ada951745455c8e982ff67ac39590b9768a
- 1e01f8ef1610dce5983c628f55d187757af14e3f0ee1bd94e63435bf647177cf
- 94e39e9710ab725aefe4d7dffe3b93e447210e3b322666b9c8d42b3622094878
- 981e0d084f78e268294fe3c0a5ecc4869bb189aff927a6b6a5da0cad61b4fca4
- a39dc4dc4e01a6c0c819c1fa9faa63811dd2978af85d4474cdc4dfa3dd0601a2
- af02d3501fc954f435a0569fd727af9377d54891b4690ccbf7e3e10bf1f6c0dc
- d5fe31471af8abcd884108fbbfe776c3df6c988a865e401fc83ccbdfe030ed4e
- f140cab283c35c92dc74db53b6d9964706538554d4151a637a406b093746692b
- fec5824e87550fc4981606030d7b74f6d00b001de536916b95f7c1d24a8113d8
Malware from an infected Windows host:
SHA256 hash: 5f50dcf06dd5fb51b26f815fd8ff6d4a5afa7301e9c7923ea8f75b2b1e224f82
- File size: 2,645 bytes
- File name: Okritie.zakaz.docx.zip
- File description: Attached zip archive from one of the emails
SHA256 hash: e51f36811056d71c970791223da17c3f5b4d84394063a42eb8f2c432e97dba7a
- File size: 5,317 bytes
- File name: [garbled characters].js
- File description: Extracted JS file from the attached zip archive
SHA256 hash: d5fe31471af8abcd884108fbbfe776c3df6c988a865e401fc83ccbdfe030ed4e
- File size: 1,405,704 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\rad012AB.tmp (random hex digits)
- File location: C:\ProgramData\services\csrss.exe
- File description: Initial Shade/Troldesh executable retrieved by the JS file
SHA256 hash: 2824a8ce0e65bb185a88ff1fe5f1df202405c42b6705a420dbc07c565a44b240
- File size: 1,635,840 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\0123ABCD.exe (random hex digits)
- File location: C:\ProgramData\Windows\csrss.exe
- File description: Additional malware found on the same infected Windows host
Tor domains from the decryption instructions:
- cryptsen7fo43rr6.onion.to
- cryptsen7fo43rr6.onion.cab
Email address from the decryption instructions:
- pilotpilot088@gmail.com
Final words
12 email examples, a pcap of network traffic traffic from an infection, and the associated malware/artifacts are available here.
I checked the 28 URLs I found ending in .jpg for delivering the initial Shade/Troldesh malware binary. 17 of them still returned the ransomware executable. All URLs have been submitted to URLhaus, so hopefully they'll all get taken off-line soon. These URLs will not work if you copy/paste them into a browser, because the servers hosting this malware are looking for the right User-Agent string. You'd have to use a tool like curl to spoof the correct User-Agent string and get the malware.
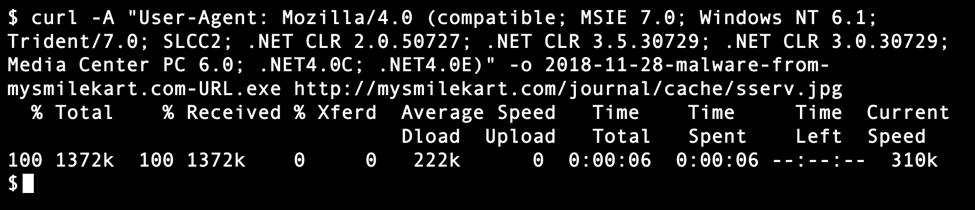
Shown above: An example of using curl to retrieve these ransomware binaries.
Russian language malspam pushing Shade/Troldesh ransomware is not anything new. As mentioned earlier, I posted a diary about it back in 2016 and I doubt it ever really disappeared for long. Nor is this malspam limited to Russian malspam. The example I documented in 2017 was from English language malspam. This diary is yet another reminder that the criminals behind this malware remain active and are still trying to infect vulnerable Windows hosts.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments
Maybe now people will stop calling every malicious email "phishing".
Anonymous
Nov 29th 2018
6 years ago