Sextortion Spam and the Infinite Monkey Theorem
As early as 2018-09-05, I've seen daily waves of sextortion spam that have spoofed yahoo.jp in the message headers and sending addresses. Subject lines include a password the recipient allegedly uses. Extortion prices range from $1,000 to $7,000 US dollars.
Back in July 2018, Johannes Ullrich wrote about an example here. Brian Krebs also documented a wave earlier that month. But recent sextortion emails appear to be mass-distributed without any real or current passwords. Krebs indicated these criminals were using password lists from older data breaches. However, these most recent waves don't seem particularly targeted.
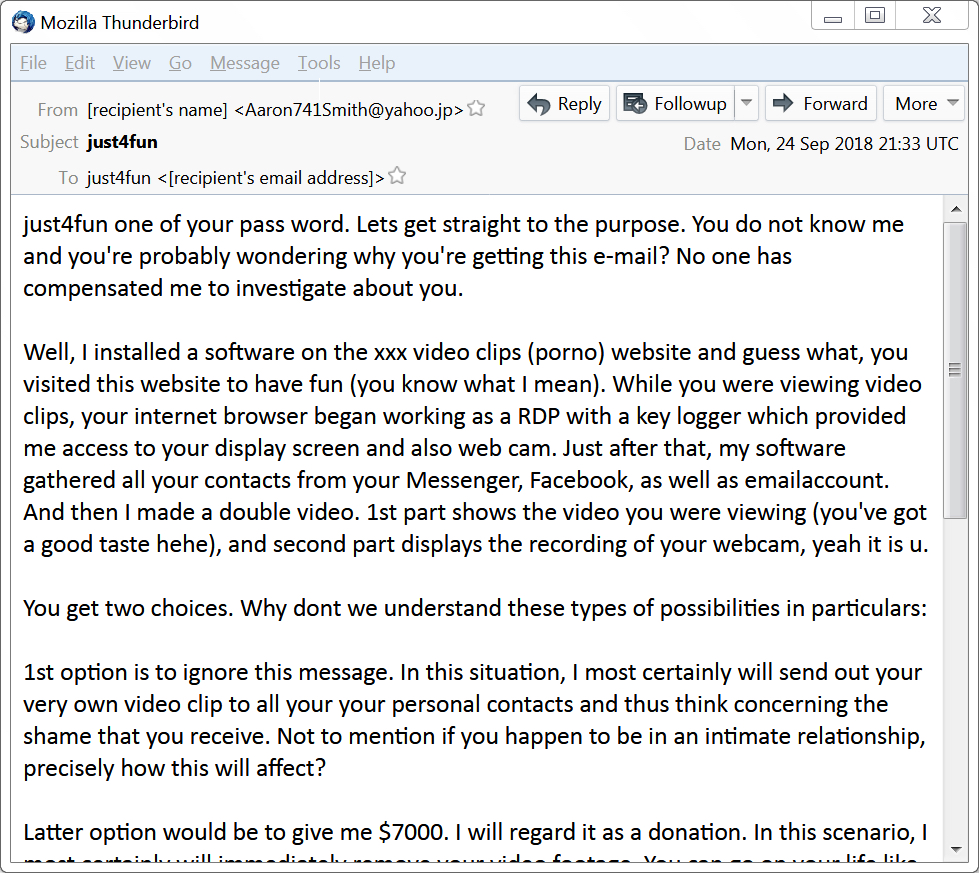
Shown above: An example of sextortion spam from Monday, 2018-09-24.
By now, many of us have probably seen or heard about these sextortion emails. They are botnet-based spam, and emails from this latest campaign follow noticeably distinct patterns. A different Bitcoin address is used for each message I've reviewed. 50 examples of this sextortion spam from Monday 2018-09-24 are available here.
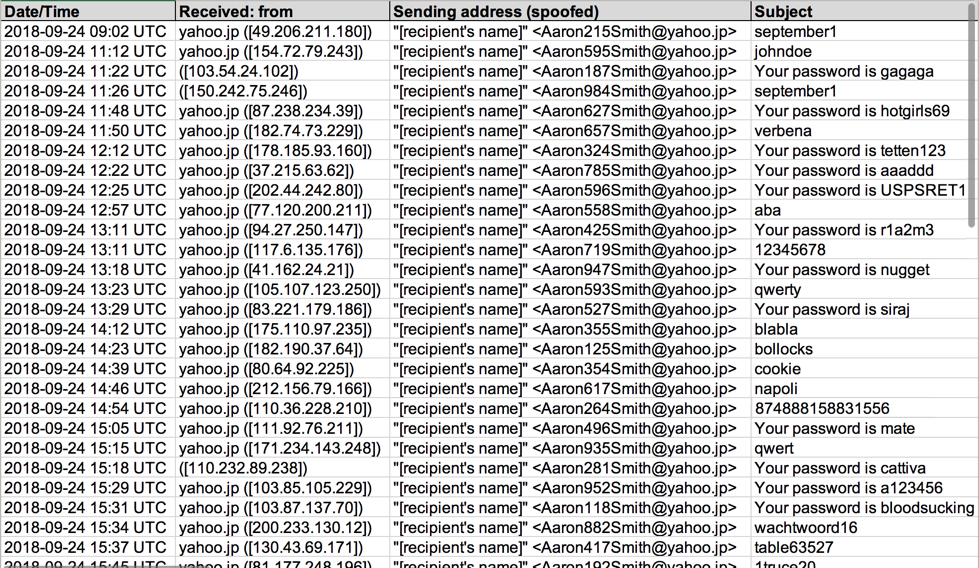
Shown above: Some metadata from my spreadsheet tracker for Monday, 2018-09-24.
These messages have different passwords for each recipient and different Bitcoin addresses for each message. It's done on a massive scale of distribution, and I've only found English-speaking recipients. I run across this type of spam at least every weekday. I suppose criminals must find it cost-effective.
But does this actually work?
Criminals behind the campaign assume most people view pornography on their computers. But the majority of passwords from this spam don't follow lists of most common passwords I've seen published. The passwords in these messages appear to be somewhat random, even if they are based on information from data breaches.
I feel like this campaign is attempting to prove the infinite monkey theorem. It states that a monkey hitting keys at random on a typewriter keyboard for an infinite amount of time will almost surely type a given text, such as the complete works of William Shakespeare. The infinite monkey theorem has been referenced several times in popular culture over the years. My favorite reference is this Simpsons cartoon scene.

Shown above: "This is a thousand monkeys working at a thousand typewriters.
Soon they'll have written the greatest novel known to man."
The idea may not be so far-fetched. Given the amount of sextortion spam I run across in my day-to-day work, it might hit on someone's actual current password. I doubt it, but it's possible.
An example of the sextortion spam follows.
Well, I installed a software on the xxx video clips (porno) website and guess what, you visited this website to have fun (you know what I mean). While you were viewing video clips, your internet browser began working as a RDP with a key logger which provided me access to your display screen and also web cam. Just after that, my software gathered all your contacts from your Messenger, Facebook, as well as emailaccount. And then I made a double video. 1st part shows the video you were viewing (you've got a good taste hehe), and second part displays the recording of your webcam, yeah it is u.
You get two choices. Why dont we understand these types of possibilities in particulars:
1st option is to ignore this message. In this situation, I most certainly will send out your very own video clip to all your your personal contacts and thus think concerning the shame that you receive. Not to mention if you happen to be in an intimate relationship, precisely how this will affect?
Latter option would be to give me $7000. I will regard it as a donation. In this scenario, I most certainly will immediately remove your video footage. You can go on your life like this never took place and you surely will never hear back again from me.
You will make the payment by Bitcoin (if you don't know this, search "how to buy bitcoin" in Google).
BTC Address to send to: 13Uw4tqt31ar8RauE8AEtdTxYe52wD9Y3Z
[CASE-sensitive, copy & paste it]
Should you are wondering about going to the cops, very well, this email cannot be traced back to me. I have covered my moves. I am also not trying to demand much, I simply prefer to be rewarded.
You now have one day in order to pay. I have a special pixel within this email message, and now I know that you have read this email. If I do not get the BitCoins, I will, no doubt send out your video to all of your contacts including relatives, colleagues, etc. However, if I do get paid, I will erase the video immediately. If you need proof, reply Yup and I will send out your video to your 6 contacts. It's a nonnegotiable offer and so please do not waste my time and yours by replying to this email message.
Final words
I'm not sure how effective this sextortion campaign really is. But due to poor security practices of potential victims, and based on how vulnerable some people are to suggestion, I suppose someone might be tricked into paying the criminals.
If countless variations of the Nigerian Prince scam have convinced people to share their bank account information, this sextortion scam might also be viable.
50 email examples and a spreadsheet tracker associated with today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments
I received those for info@ and for two aliases I use; info@ was addressed three times. My best guess is that these addresses were "harvested" from the address books of infected machines I have corresponded with. The SPAM were sent from Australia, Montenegro, Saudi-Arabia and Vietnam. The German text body was definitely not written by a native speaker. I have documented it in my blog (German): <https://www.pc-fluesterer.info/wordpress/2018/09/11/es-geht-um-ihre-sicherheit/>
Anonymous
Sep 25th 2018
6 years ago
--------------------------------------------------------------------------------------------------------------------------
Return-Path: <xxxxxx@xxxxxx.net>
Received: from [105.0.1.66] ([105.0.1.66])
by www.xxxxxx.net (8.15.2/8.15.2) with ESMTP id w8PERXBa007878
for <xxxxxx@xxxxxx.net>; Tue, 25 Sep 2018 10:27:34 -0400 (EDT)
(envelope-from xxxxxx@xxxxxx.net)
Authentication-Results: xxxxxx.net; dmarc=fail (p=reject dis=none) header.from=xxxxxx.net
Message-ID: <001801d454ec$06835a2b$602978b2@gqows>
From: <xxxxxx@xxxxxx.net>
To: "123456" <xxxxxx@xxxxxx.net>
Subject: Security Warning
Date: 25 Sep 2018 17:00:27 +0100
MIME-Version: 1.0
Content-Type: text/plain;
charset="cp-850"
Content-Transfer-Encoding: 8bit
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Outlook Express 6.00.2600.3712
X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2600.3712
X-Spam-Status: No, score=-92.3 required=6.6 tests=RCVD_IN_CBL,RCVD_IN_PBL,
RCVD_IN_SBL_XBL,RCVD_IN_WSFF,RCVD_IN_XBL,SHORTCIRCUIT,USER_IN_WHITELIST
shortcircuit=ham autolearn=disabled version=3.4.1
X-Spam-Checker-Version: SpamAssassin 3.4.1 (2015-04-28) on www.xxxxxx.net
X-UIDL: 5Q;"!7m@"!Xf8"!F:O!!
Hello!
I'm a member of an international hacker group.
As you could probably have guessed, your account xxxxxx@xxxxxx.net was hacked, I sent message you from it.
Now I have access to you accounts! You still do not believe it?
So, this is your password: 123456 , right?
Within a period from July 5, 2018 to September 21, 2018, you were infected by the virus we've created, through an adult website you've visited.
So far, we have access to your messages, social media accounts, and messengers.
Moreover, we've gotten full damps of these data.
We are aware of your little and big secrets...yeah, you do have them. We saw and recorded your doings on porn websites. Your tastes are so weird, you know..
But the key thing is that sometimes we recorded you with your webcam, syncing the recordings with what you watched!
I think you are not interested show this video to your friends, relatives, and your intimate one...
Transfer $700 to our Bitcoin wallet: 1DzM9y4fRgWqpZZCsvf5Rx4HupbE5Q5r4y
I guarantee that after that, we'll erase all your "data" :D
A timer will start once you read this message. You have 48 hours to pay the above-mentioned amount.
Your data will be erased once the money are transferred.
If they are not, all your messages and videos recorded will be automatically sent to all your contacts found on your devices at the moment of infection.
You should always think about your security. We hope this case will teach you to keep secrets.
Take care of yourself.
Anonymous
Sep 26th 2018
6 years ago
The password is *real* and *connected* to the recipient email. Probably leaked during the SSH vulnerability havoc, few years ago.
The leaked mail and passwords, once verified they no longer work for stealing identities were probably put on a list and sold or given away for free. The attacker does not show if he knows from what site the password comes from (doing that would ruin his trick).
The scam requires a target that:
- reuses the same password (there is plenty)
- has some sort of "private" online life (who hasn't?) using the same credentials (as most do)
- be somehow ashamed of getting exposed (plenty of)
- falls into the trick (and the trick is ... tricky)
The trick is:
The attacker contacts you directly, and shows off all the information he has on you, information you wouldn't expect him to have (your supersecret password and email), that surprises you, because passwords are supposed to be secret, and he tells you that is only a sample of the *real* information he has (full websites activity, videos, etc..) on you. You might believe it because, well, he even knows your supersecret password.
I presume a lot of people would fall into this, some would doubt and risk but still feel uncomfortable, some would unfortunately pay, maintaining this kind of scum profitable for some time (until novelty expires).
Anonymous
Sep 28th 2018
6 years ago
The password was complex and it does not seems to me to be easily guessable. It also does not seems to me to be a created randomly by the monkey army.
It seems that the database of username / password was analyzed .
Since the username of the professional social network is the e-mail address, then it is kinda easy to reach the human behind the login and then pretend to have access to your computer and so on.
Anonymous
Sep 29th 2018
6 years ago
Hello! I'm a member of an international hacker group. As you could probably have guessed, your account monster.....@.... was hacked, because I sent message you from your account. Now I have access to all your accounts! For example, your password for monster.....@...: ...... Within a period from July 31, 2018 to October 3, 2018, you were infected by the virus we've created, through an adult website you've visited. So far, we have access to your messages, social media accounts, and messengers. Moreover, we've gotten full damps of these data. We are aware of your little and big secrets...yeah, you do have them. We saw and recorded your doings on porn websites. Your tastes are so weird, you know.. But the key thing is that sometimes we recorded you with your webcam, syncing the recordings with what you watched! I think you are not interested show this video to your friends, relatives, and your intimate one... Transfer $800 to our Bitcoin wallet: 1PwENLsmQ2Z6b4EJfXDeeXKBj9v878uHRf If you don't know about Bitcoin please input in Google "buy BTC". It's really easy. I guarantee that after that, we'll erase all your "data" A timer will start once you read this message. You have 48 hours to pay the above-mentioned amount. Your data will be erased once the money are transferred. If they are not, all your messages and videos recorded will be automatically sent to all your contacts found on your devices at the moment of infection. You should always think about your security. We hope this case will teach you to keep secrets. Take care of yourself.
Regardless of the fact that this is bogus, any laptop I have has a piece of paper taped over the webcam - a good practice for anyone though most webcams also have an associated light that comes on to let you know when they are in use. I am wondering why the bitcoin address can't be cancelled or locked for this criminal.
Anonymous
Oct 6th 2018
6 years ago